Unknowingly, it has been almost 5 years since the first submission of Vulhub, the open source project I led, and Vulhub has become a daily routine in my life. Just like several other daily code audit planets and Sec-News in my life, they are not a task that I deliberately complete, but have become my "callback functions" in reality.
It sounds unique to use a callback function to describe this thing, but if you think about it carefully, it is true - I will make a Vulhub environment and submit it to Github after analyzing the latest vulnerability, and I will click on the browser after reading a good article Click the button to add it to Sec-News. When I have new ideas or learn knowledge, I will go to the planet to chat and share it.
These behaviors are like callback functions. They are triggered at a certain moment in my daily life. They may encounter "network delays", but they will always be produced and consumed like a queue, and finally settled in the code audit universe. .
Yes, someone used to tease me that the projects I led personally formed the "Code Audit Universe", and I readily accepted this name.
In the eyes of outsiders, these are some tools and sharing that I give back to the security community, but in fact they together form my own knowledge matrix. Whether they are made public does not actually affect my collection and recording of these contents.
Just like Vulhub, the first purpose of doing this project was just because I wanted to learn Java vulnerabilities at that time. However, in 2016 and 2017, when Java vulnerabilities were blowing out, there was no good way to learn. I didn’t even know how to build a Java Web development environment. Don't know any of them (except JSPStudy).
So Vulhub came into being, and it basically accompanied me when I was learning various vulnerabilities starting from Java vulnerabilities.
Interested students may find that there are not many PHP-related vulnerabilities in Vulhub, which is in sharp contrast to Exploit-Db. Although the reason has something to do with the decline of PHP's CMS in recent years, it is actually inseparable from my own learning trajectory. I pride myself on having a pretty good grasp of PHP security in 2016 (thinking about it now, it’s actually far behind), so when I choose to work on vulnerability environments in the future, I will tend to focus more on areas that I am not familiar with, especially Java. .
Nowadays, my knowledge system is very different, and I no longer treat vulnerabilities differently. When Vulhub chooses an environment, it still prefers factors such as vulnerability type, influence, and harm, rather than my own personal preferences.
It can be said that the development of Vulhub has entered a mature and systematic stage.
There has been a lot of buzz recently about Spring Framework vulnerabilities, and Vulhub has recently included three related vulnerabilities:
CVE-2022-22947 - Spring Cloud Gateway Actuator API SpEL Code Injection
CVE-2022-22963 - Spring Cloud Function SpEL Code Injection
CVE-2022-22965 - Spring Framework RCE via Data Binding on JDK 9+
Thanks to the recent increase in my Twitter followers, these environments have achieved outstanding results after being promoted on Twitter. On March 31 this year, I saw that the number of Stars of the Vulhub project was marked as 10k on the page, but in fact this was a rounded number. Unexpectedly, the number of Stars exceeded 10,000 on the day the Spring4Shell vulnerability environment was released. The trend is It’s obvious from the picture:
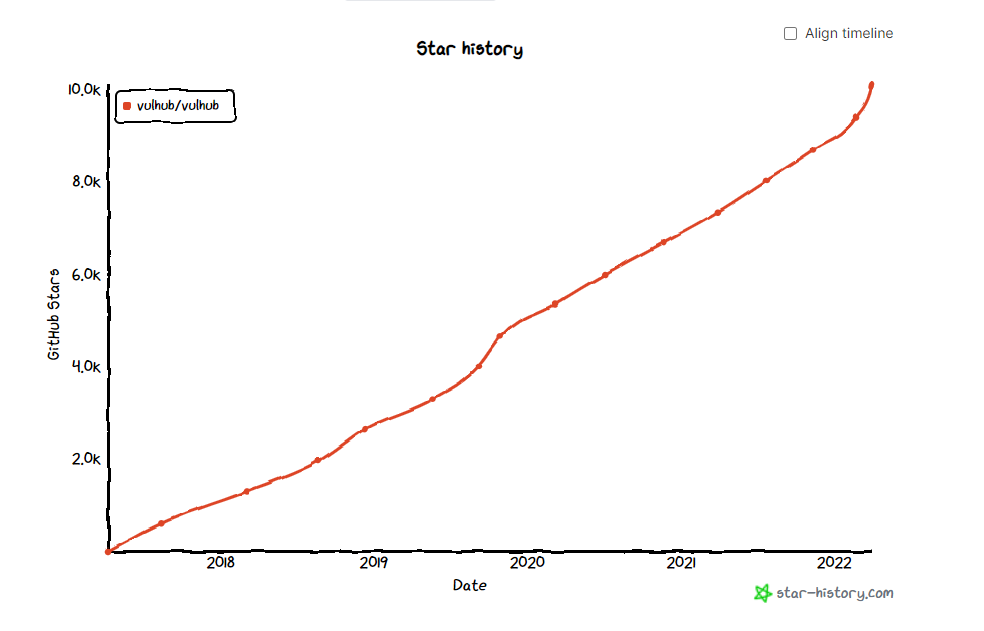
It also appeared on the Github Trending list this week (I didn’t capture the picture of the fastest rising day):
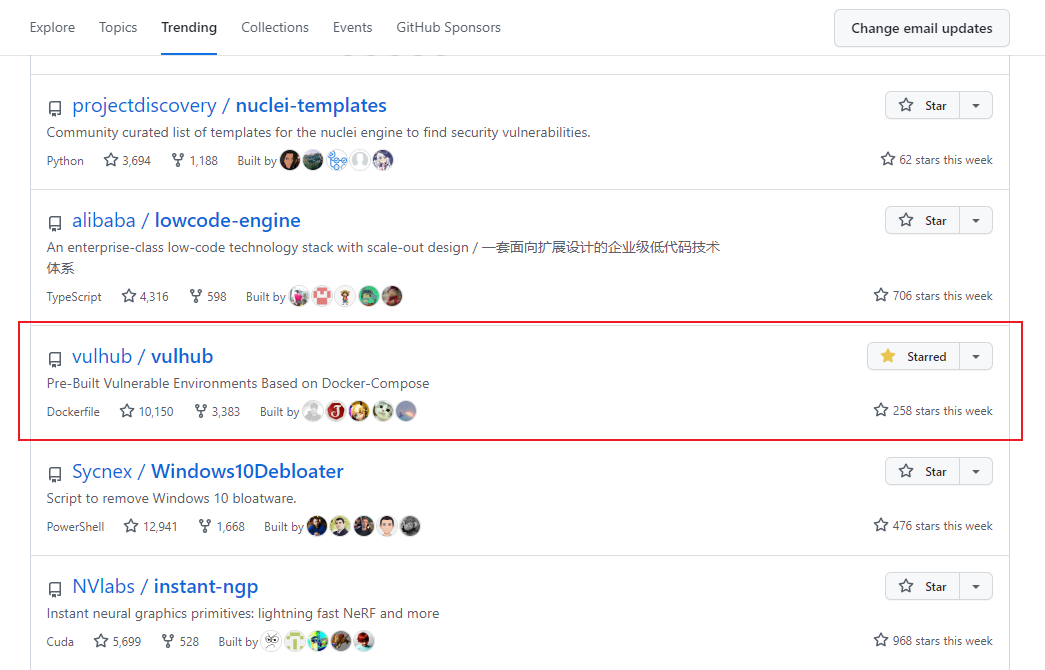
Vulhub is now also an open source project with “10,000 likes”, spread the flowers~
To commemorate this occasion, I decided to do a lottery and prepared two prizes:
First Prize: Geek Time Super Member Annual Card x 1
Second prize: Vulhub commemorative sticker x 2
Geek Time is the best company for computer-related column tutorials. I usually read a lot of related tutorials on it, so this time the first prize is set to be a Geek Time super membership annual card. This super member can learn most of the courses on the platform, which is a great value.
If you don’t know about the Geek Time super membership, or think that you have a non-Emirati physique and can’t win the prize, you can also directly scan the code to purchase, worth ¥498 a year:

Speaking of the lottery, our method of participating in this lottery is very simple. Click on the "Lottery Assistant" applet below and follow the instructions to participate in the lottery.