introduction
With the continuous development of the Internet, network security issues have become increasingly important. On the Internet, malicious users can use IP proxies to hide their true identities and launch various network attacks or fraud. In order to ensure network security, IP proxy identification API has become an indispensable tool. This article will explore its role and application in depth.
The role of IP proxy identification API
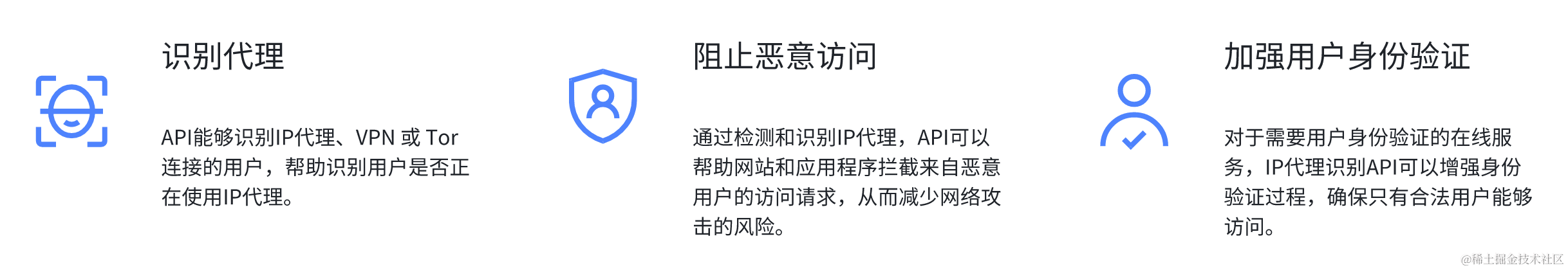
The IP proxy identification API can detect IP proxies, VPNs and Tor connections used on the network, revealing potential network security threats. Its main functions include:
Application of IP proxy identification API
1. Website security
The IP Proxy Identification API can be used to identify and restrict users using proxy, VPN or Tor connections. Some malicious users may use proxies or anonymous connections to bypass security measures, engage in abusive behavior, or launch network attacks. By using the IP Proxy Identification API, you can detect these connections and take appropriate security measures to protect your website or application.
2. Advertising fraud detection
In the advertising world, some people may use proxies or VPNs to spoof their location, hide their true identity, or commit fraud. The IP proxy identification API can help identify such fraud, thereby improving the accuracy and effectiveness of advertising.
3. Content access control
Some websites or services may wish to restrict or disable access to their content to users using proxies, VPNs, or the Tor network. By using the IP Proxy Identification API, you can check whether a user's connection uses these anonymizing services and decide whether to allow them to access specific content.
How to use IP proxy identification API?
1. Application interface
Log in to APISpace and enter the details page of [ IP Proxy Identification API ] to apply for the interface.
2. Online test interface
Enter the test page, enter the IP address to be identified, and click Send Quick Test.
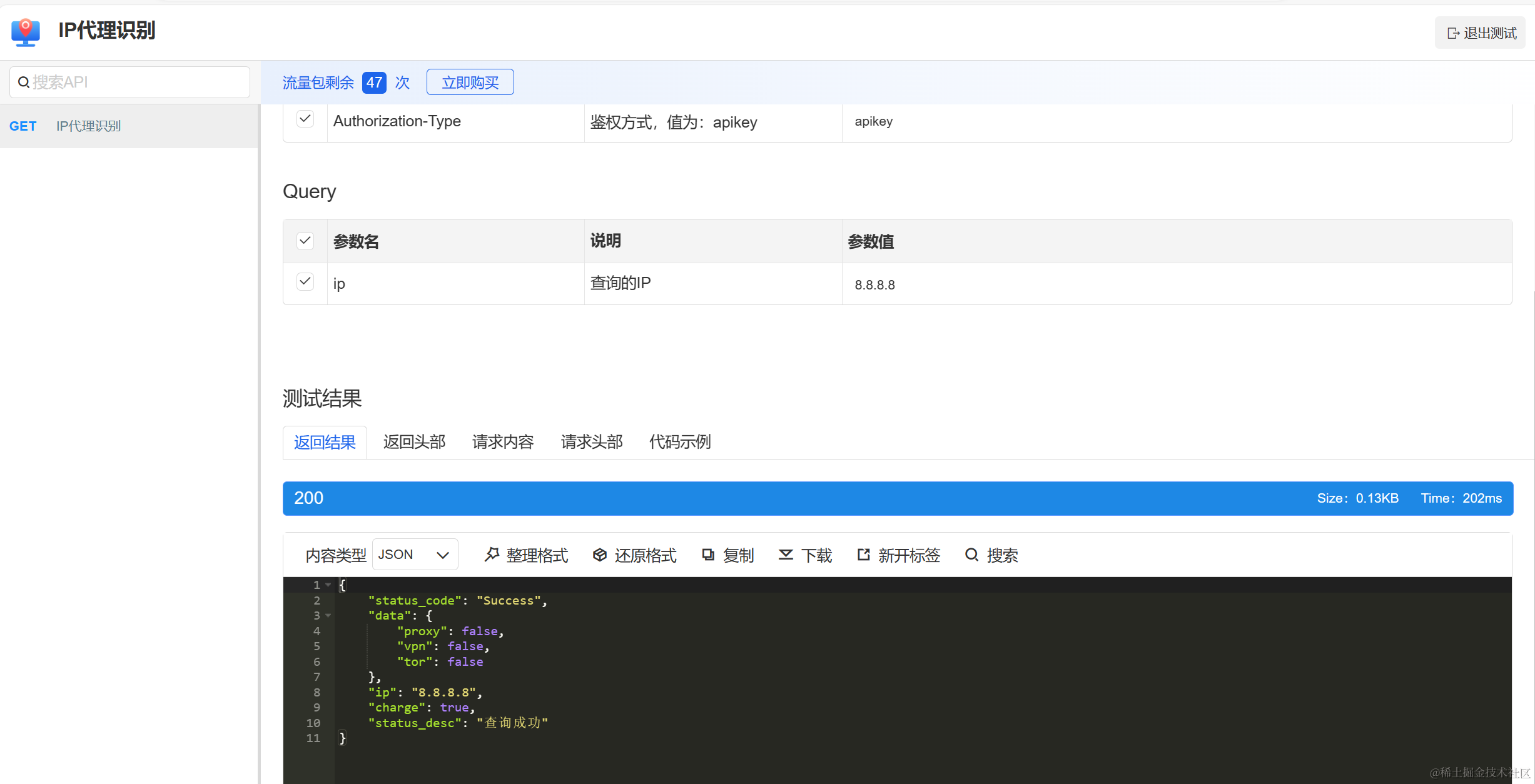
Return example:
{
"status_code": "Success",
"data": {
"proxy": false,
"vpn": false,
"tor": false
},
"ip": "8.8.8.8",
"charge": true,
"status_desc": "查询成功"
}
3. Interface access
After passing the test, you can connect the interface to your own program. The access code example is as follows:
OkHttpClient client = new OkHttpClient().newBuilder().build();
MediaType mediaType = MediaType.parse("application/x-www-form-urlencoded");
Request request = new Request.Builder()
.url("https://eolink.o.apispace.com/ipproxy/ip/info/v1?ip=8.8.8.8")
.method("GET",null)
.addHeader("X-APISpace-Token","登录APISpace即可获得")
.addHeader("Authorization-Type","apikey")
.build();
Response response = client.newCall(request).execute();
System.out.println(response.body().string());
in conclusion
IP proxy identification APIs play a critical role in network security in today's digital age. By identifying and blocking the abuse of IP proxies, they help ensure the security and health of the network environment. As cyber threats continue to evolve, the application prospects of IP proxy identification API will continue to expand to ensure that our online world is more secure, transparent and trustworthy.