Use of tools such as burpsuite
Gadget list:
 Go to view related commands
Go to view related commands

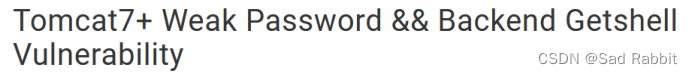
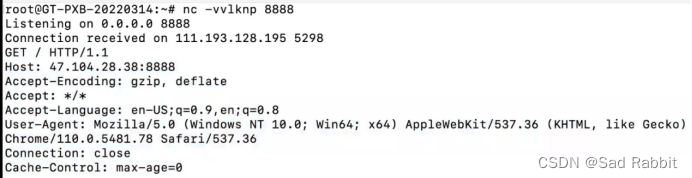
Directly check whether the port is successful.
If you only use it to verify whether the port is successful,
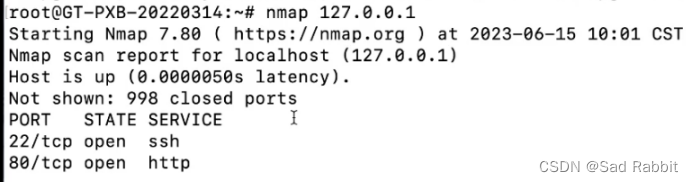 you will find that only scanning 1-1000
you will find that only scanning 1-1000
 Nmap is too slow! ! !
Nmap is too slow! ! !
 12 seconds
12 seconds
 is very fast, 65535 port 1 second
is very fast, 65535 port 1 second
Hping3 scan port
Nc verify port open
nmap study port details

 -A is to use all 600 scripts with
-A is to use all 600 scripts with
Windows2001
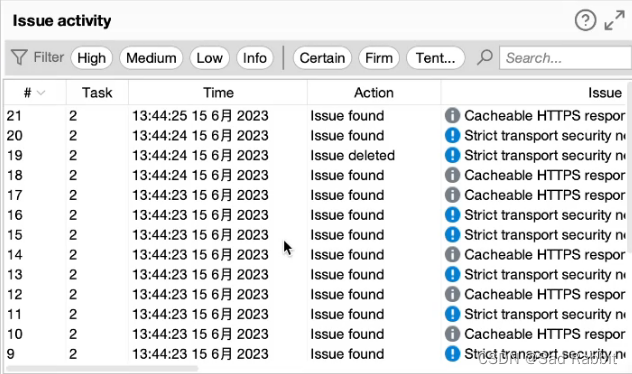
 Curl: verify whether the web page is accessed successfully, you can also upload and download files, you can also get and post
Curl: verify whether the web page is accessed successfully, you can also upload and download files, you can also get and post
out of the network: you can access the outside world Internet, but just a simple ping does not explain the problem. Curl is a tcp network that can be used.
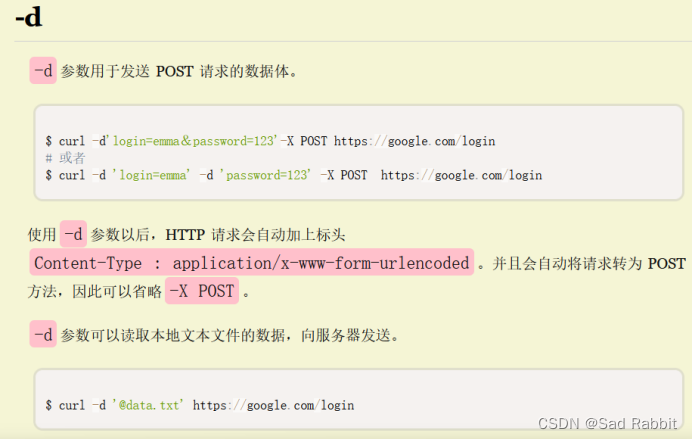
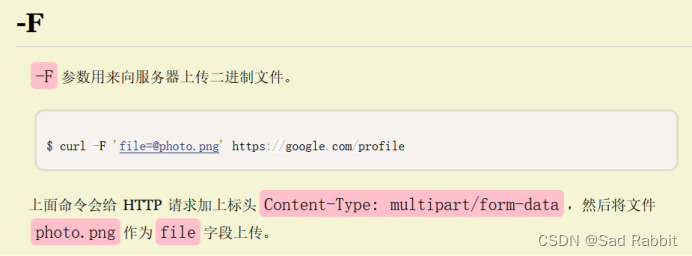
Personal tips:
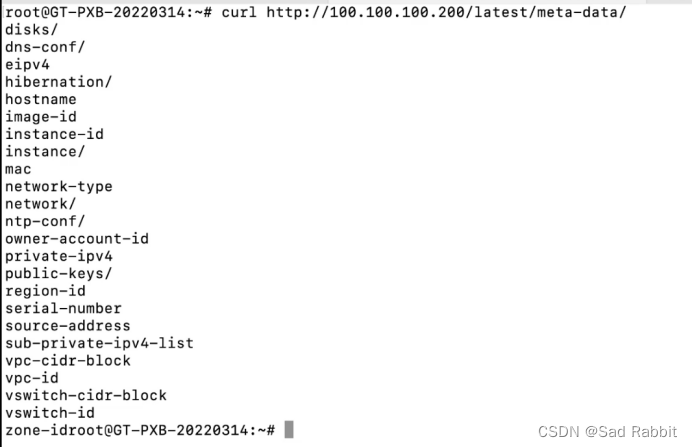
Cloud assets, there will be ram/ This path has k8s credentials to get permissions and ak/sk
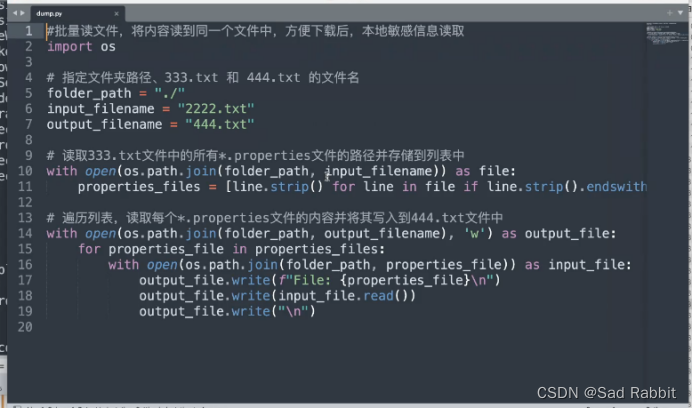
python
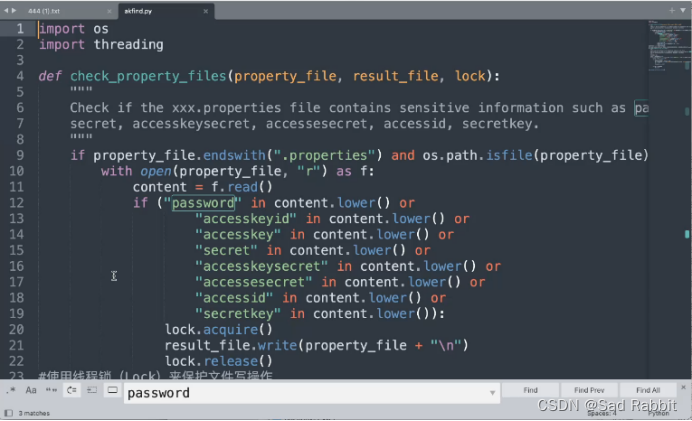
//Try to use the pro version
//Must be turned off, it will automatically crawl
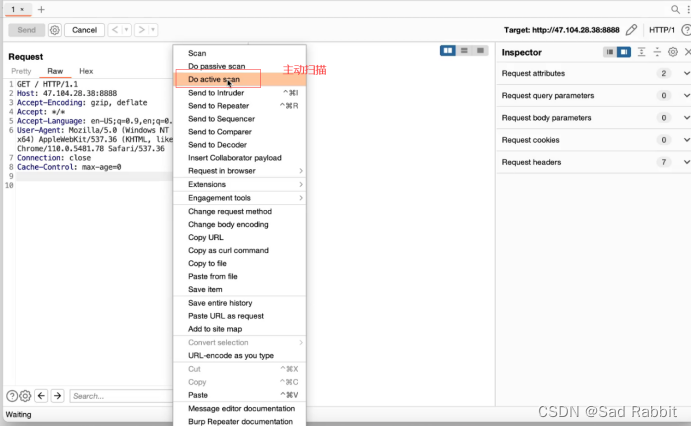
1. Passively crawl
2. Passively send attack payloads.
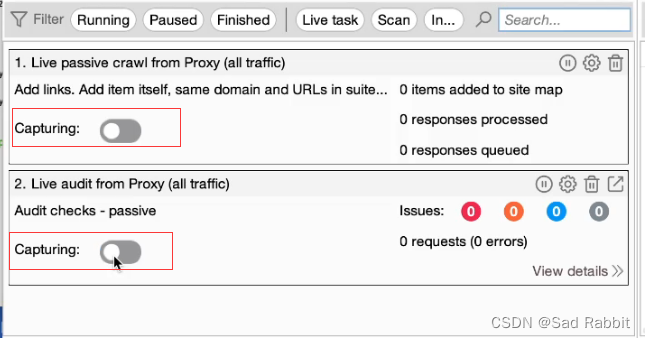
Crawling can only be done when the customer is fully authorized.
Scanning can only be performed without waf.
//Describe the problem.
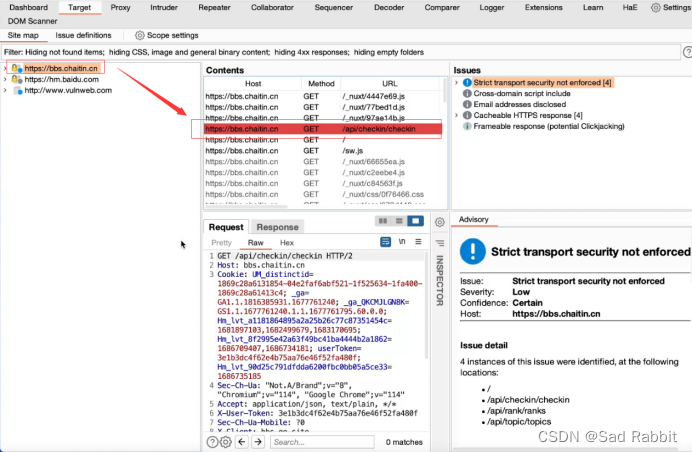
Not necessary
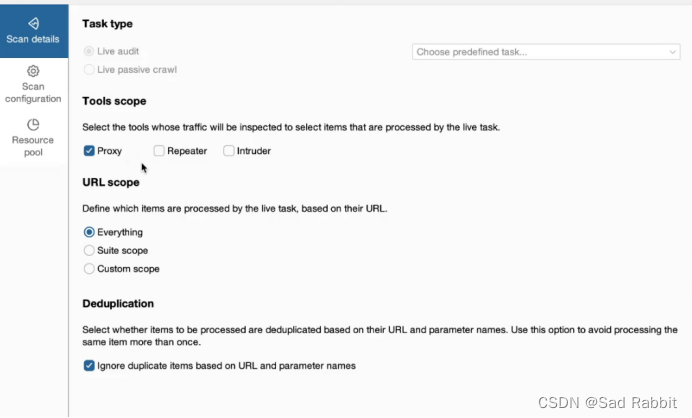
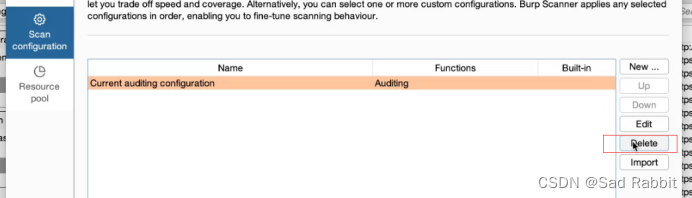
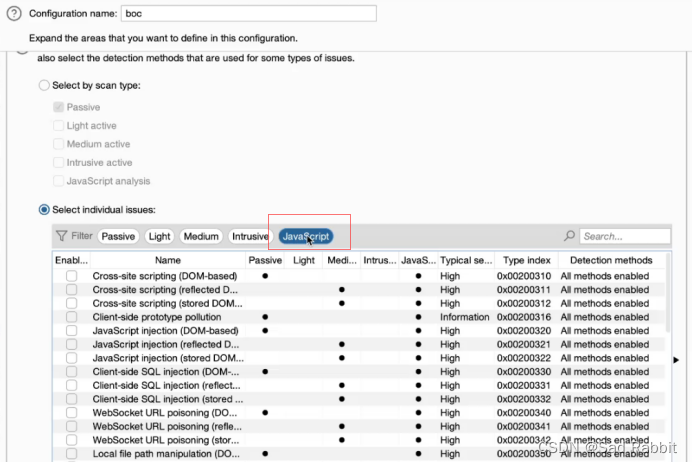
. Select the type of DOM.

Proxy module: related to the package. Bring your own browser
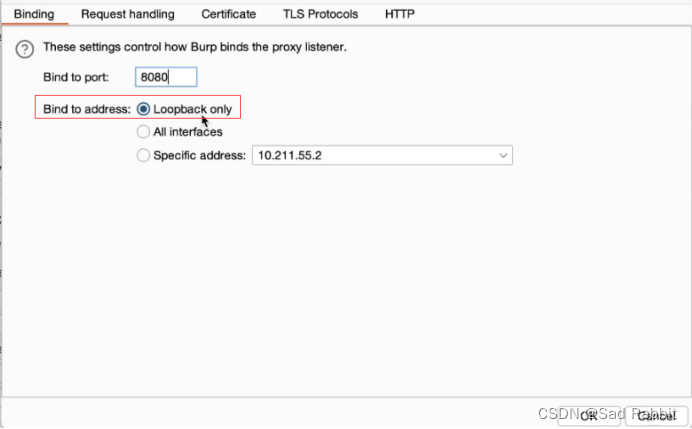
in the Google Store.

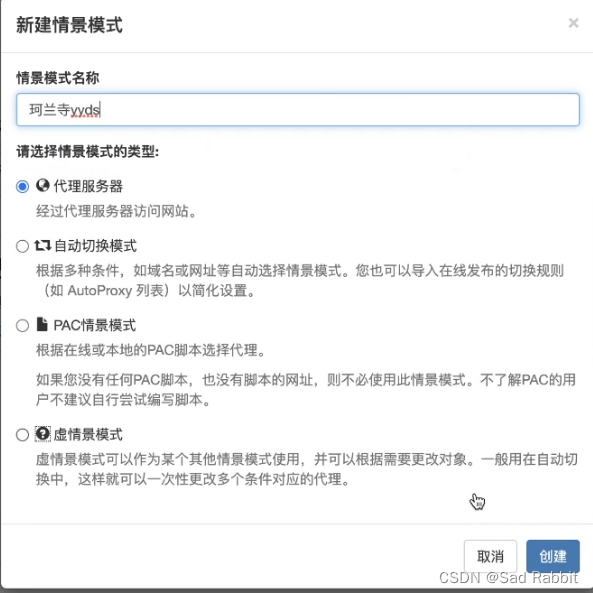
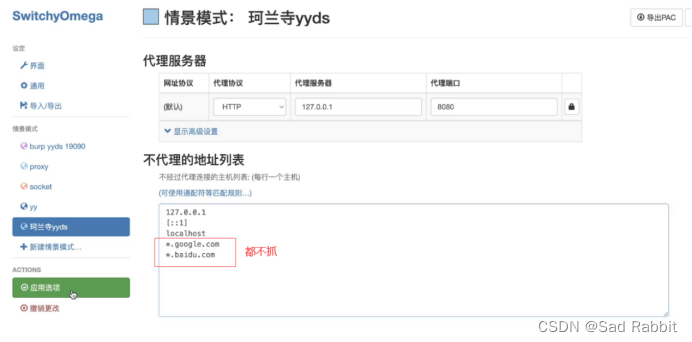

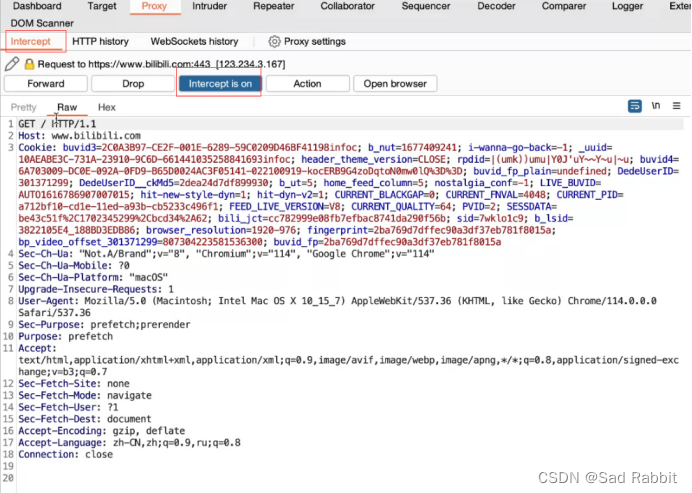
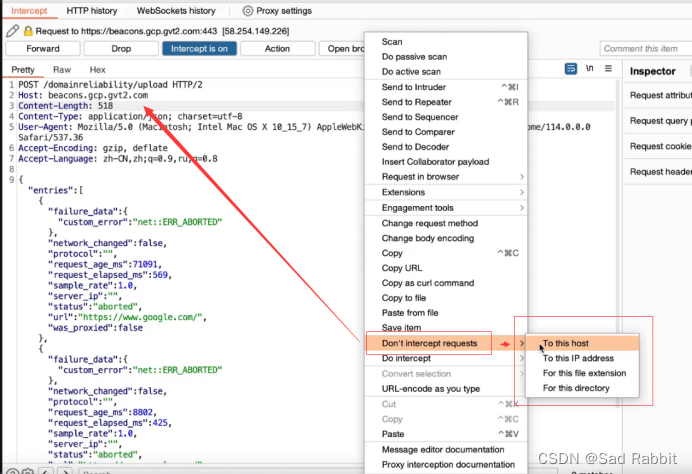
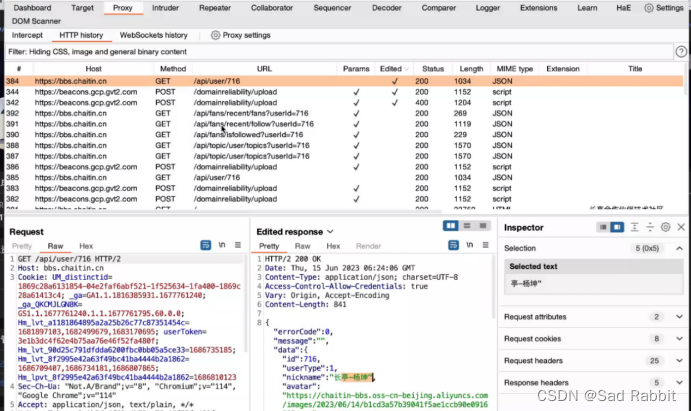
Firefox tool:

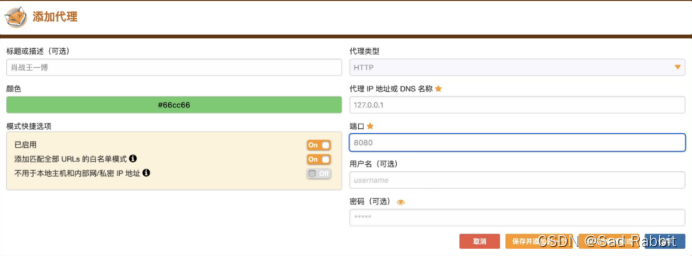
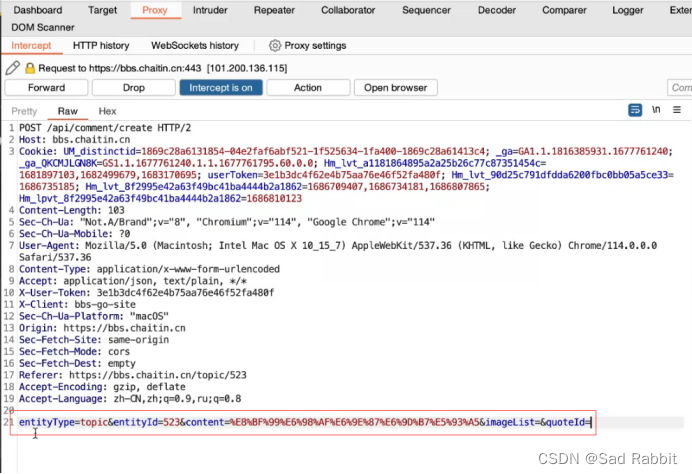
//Modify the package
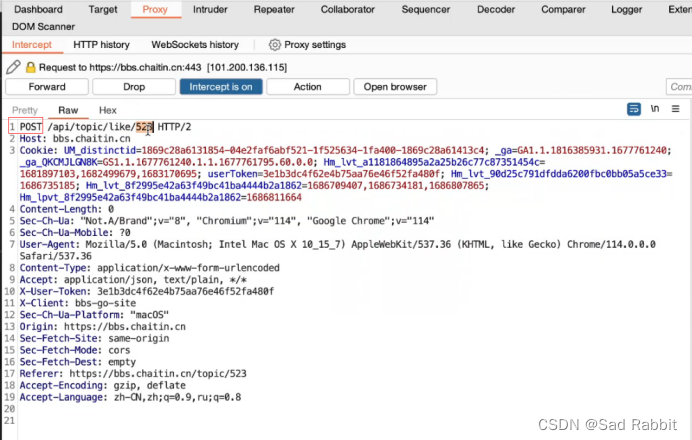
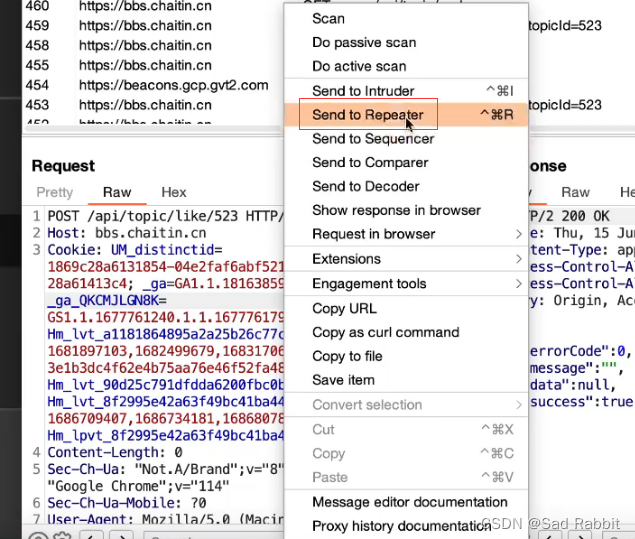
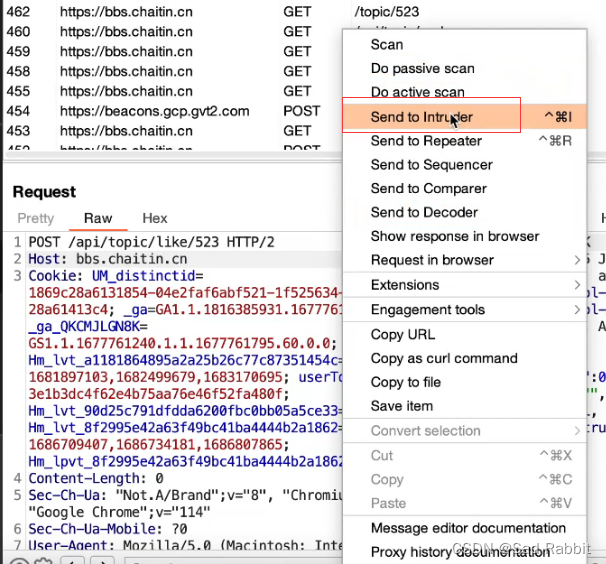
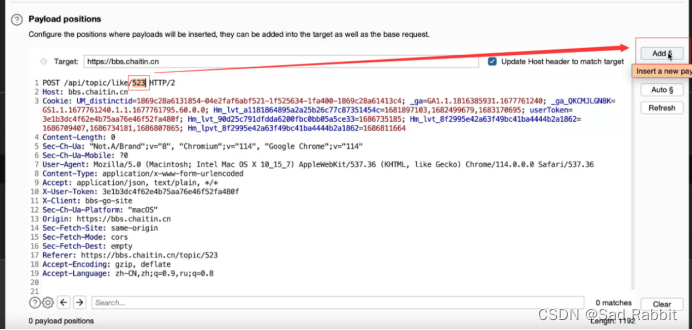
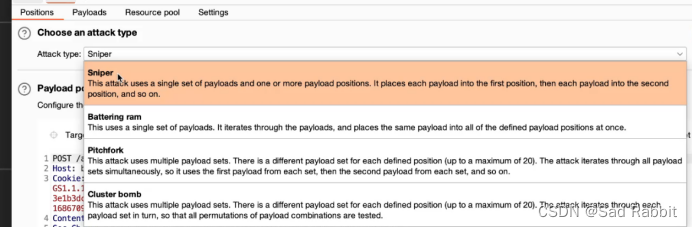
Sniper: hit it
/Note here that when blasting, conditional competition will occur under multi-threading, resulting in a 401 error
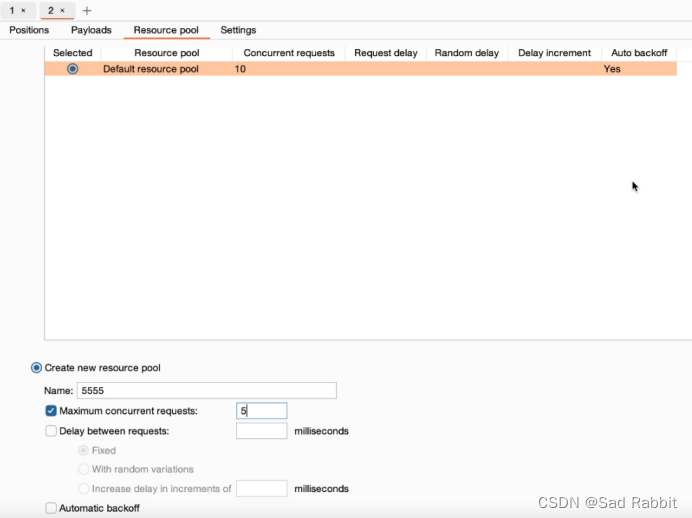

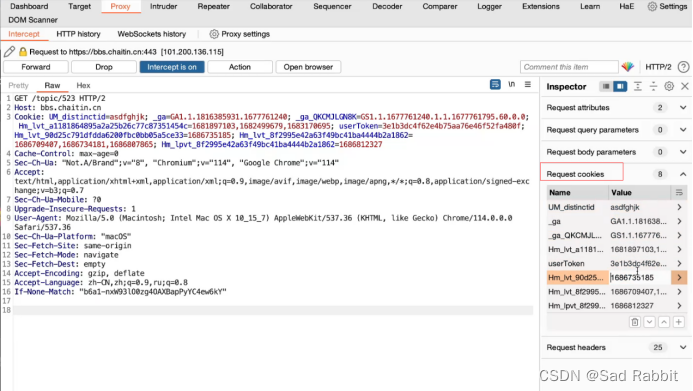
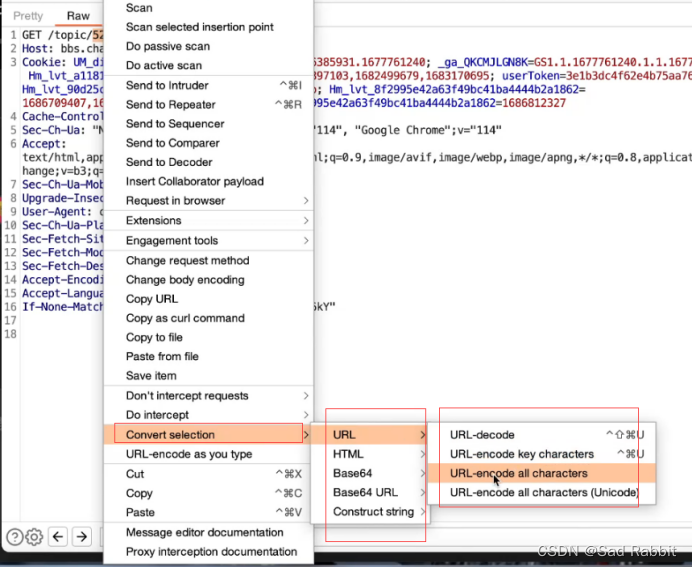
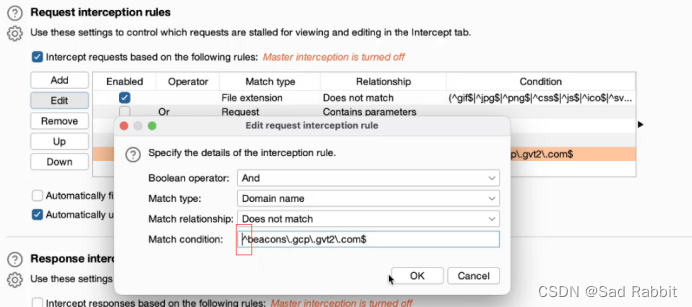
//Business logic vulnerability

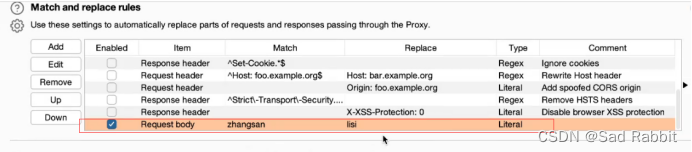
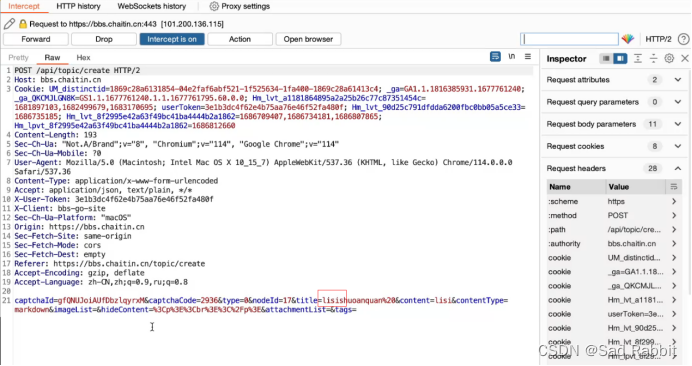
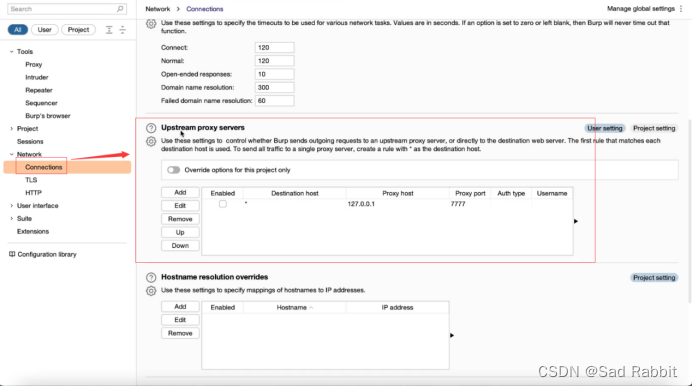
//You can configure the upper-layer agent

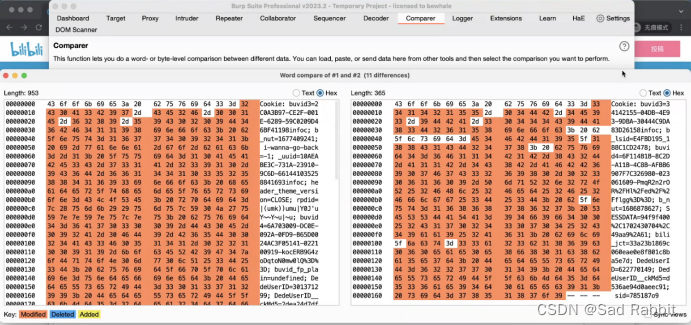
and you can dig out the highlighting of unauthorized vulnerabilities
HAE
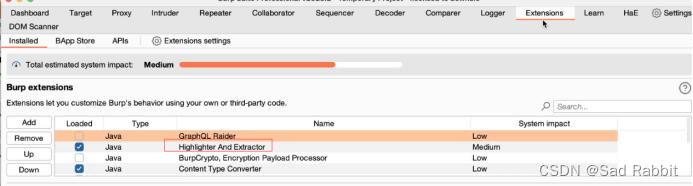
Operation