Recently, AudioCodes desk phones and Zoom's Zero Touch Provisioning (ZTP) have been exposed to multiple security vulnerabilities, malicious attackers may exploit these vulnerabilities for remote attacks.
SySS security researcher Moritz Abrell mentioned in an analysis report published on Friday (August 11) that external attackers can use vulnerabilities found in AudioCodes' desk phone and Zoom's Zero Touch Provisioning feature to remotely control these devices. equipment.
This unfettered access can see through devices and attack corporate networks to eavesdrop on rooms or phones, or even build a botnet of infected devices. The research was presented at the Black Hat US security conference earlier this week.
The root of this problem actually lies with Zoom's ZTP, which allows IT administrators to configure VoIP equipment in a centralized manner, allowing businesses to easily monitor, troubleshoot, and update equipment when needed. This is accomplished by providing configuration and firmware updates to devices through a web server deployed in the local network.
Specifically, it was found to lack a client-side authentication mechanism when retrieving configuration files from the ZTP service, making it possible for an attacker to trigger the download of malicious firmware from a malicious server.
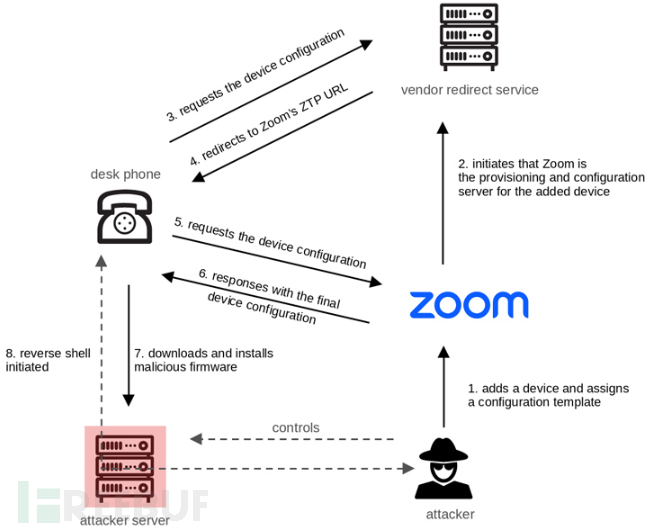
The research further revealed improper authentication issues in the encryption routines of the AudioCodes VoIP desk phone (which supports Zoom ZTP) that allowed decryption of sensitive information, such as passwords and configuration files, through a redirection server used by the phone Transfer to get the configuration.
These two weaknesses, unverified ownership errors and flaws in certified hardware, could be fashioned into a chain of vulnerabilities that deliver malicious firmware by abusing Zoom's ZTP and triggering arbitrary devices to install it.
When combined, these vulnerabilities can be used to remotely take over arbitrary devices. Since this attack is highly scalable, it can pose a significant security risk.
About a year ago, the German cybersecurity firm discovered a security issue in Microsoft's Teams Direct Routing feature that could have left the installation vulnerable to toll fraud.
Abrell said at the time that an external unauthenticated attacker could send specially crafted SIP messages and pretend they were from Microsoft. This way the victim's session border controller will correctly classify these messages. This allows unauthorized external calls to be made through the victim's phone.