Linux permissions
1. The concept of Linux permissions
There are two types of users under Linux : super user (root) and ordinary user.
Super user: can do anything under Linux
system without restrictions; ordinary user: can do limited things under Linux .
The command prompt of the super user is "#" , and the command prompt of the ordinary user is "$"
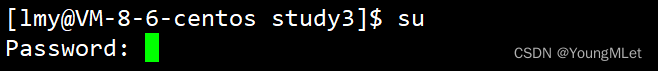
Command: su [username]
Function: switch users.
For example, to switch from the root user to the normal user user , use su user . To switch from the ordinary user user to the root user, use su root (root can be omitted) . At this time, the system will prompt you to enter the password of the root user, as shown below:
2. Linux permission management
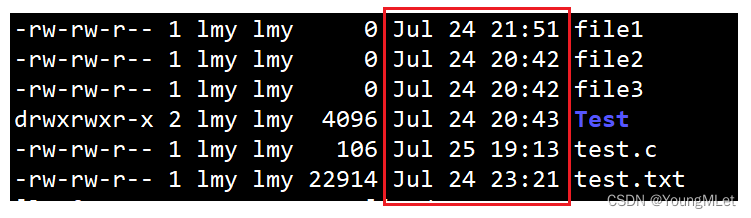
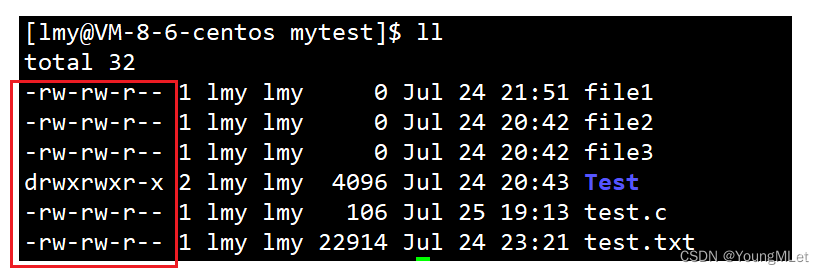
When we use the ll command, we usually see a string of data in front of the file or directory name. So what do they mean? For example, in the red box in the picture below:

First of all, we know that the following three columns are the time, to be precise, the time when the file or directory was last modified:
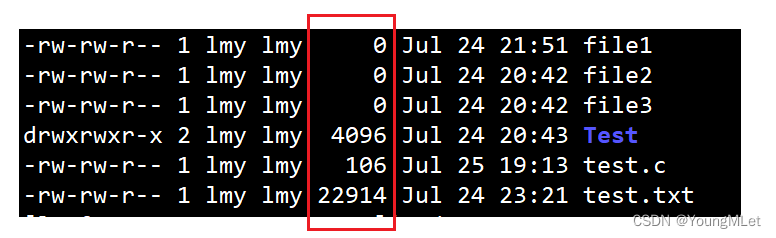
Then there are the numbers in the following column, which represent the size of the file or directory:
Next, we will understand what the two columns of lmy represent.
1. Classification of file visitors
First of all, we need to understand that file visitors are divided into three categories:
- Owner of files and file directories: u—User
- Users of the group to which the file and file directory owners belong: g—Group
- Other users: o—Others
In the two columns lmy in the figure below , the first column lmy represents user , and the second column represents group , as shown below:
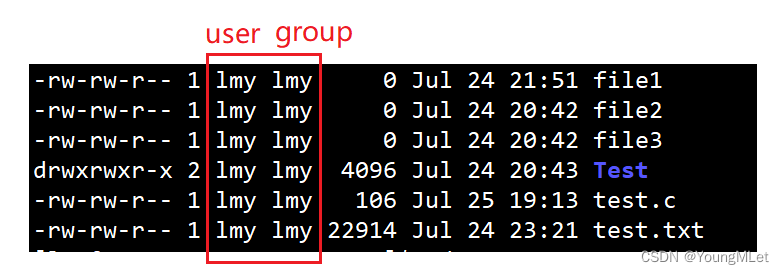
In addition to user and group , it belongs to the other group. Users belonging to the other group do not have permission to access this file or directory.
2. File type and access permissions (thing attributes)
The first character is as shown below:
What does this character mean? The meaning of this character is as follows:
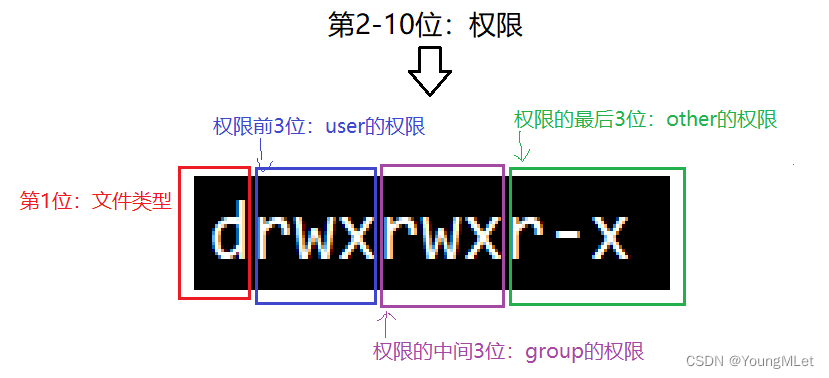
The meaning of the file type is as follows:
d:文件夹
-:普通文件
l:软链接(类似Windows的快捷方式)
b:块设备文件(例如硬盘、光驱等)
p:管道文件
c:字符设备文件(例如屏幕等串口设备)
s:套接口文件
The basic representation of visitor permissions is as follows:
- Read (r): Read , for files, has the permission to read the file content; for directories, has the permission to browse the directory information
- Write (w): Write , for files, has the permission to modify the file content; for directories, has the permission to delete files in the moved directory
- Execute (x): execute , for files, has the permission to execute the file; for directories, has the permission to enter the directory
- - Indicates that you do not have this permission
For example, in the Test directory as shown below :
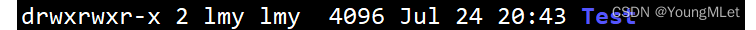
The d in the first digit means that the file type is a directory; the 2-4 digits are the permissions owned by the user , which are respectively read and write execution; the 5-7 digits are the permissions owned by the group , which are also read and write execution; the last three digits are The permissions of other only have read and execute permissions, but no write permissions.
3. Related setting methods for file access permissions
Command: chmod
Function: Set file access permissions
Format: chmod [parameter] permission file name
Note: Only the owner of the file and root can change the permissions of the file.
Modify permission characters:
+: Add the authority indicated by the authority code to the scope of authority
-: Cancel the authority indicated by the authority code to the scope of authority
=: Grant the authority indicated by the authority code to the scope of authority
User symbols:
u: owner
g: owner in the same group
o: other users
a: all users
For example, if we touch a file, its default permissions are as follows:
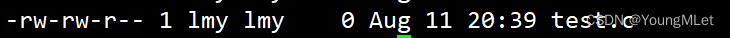
We add x permissions to user:
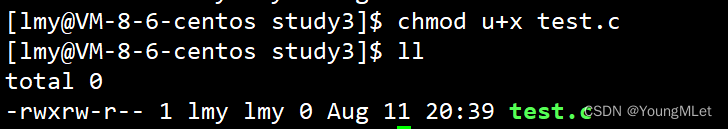
At this time, the user user of test.c has x permissions; we then add rwx permissions to other users, as shown below:
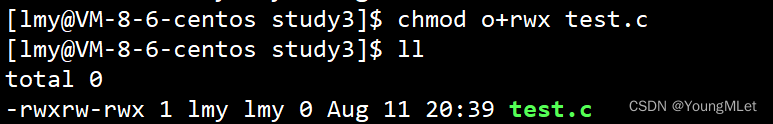
Finally, we remove all the permissions of the group group, as shown below:
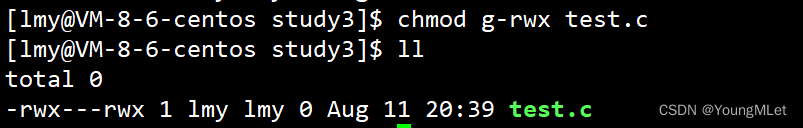
The operation of modifying permissions is as shown above. In fact, we have another way to modify permissions, which is to use the binary method;
For example, rwx is a three-digit letter, we can use 0 or 1 to indicate the presence or absence of its authority; so we can regard these three digits as a whole and form an octal number to judge the existence of its user authority, for example rx, you can use Binary 101 is represented, its octal is 5 ; –x can be represented by binary 001 , its octal is 1 ; rwx can be represented by binary 111 , its octal is 7 .
Therefore, when modifying permissions, we can also use three-digit octal numbers to modify them. For example, we want to remove all other permissions, and add all user and group permissions, as shown in the following figure:
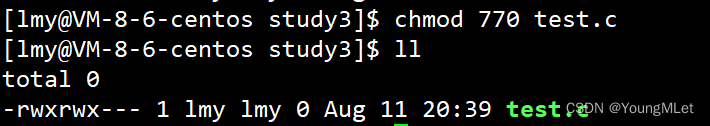
For another example, we remove the permissions of all groups, as shown in the figure:
The above is the relevant content of modifying permissions.
3. Default permissions
1. Permissions required to operate files and directories
Before learning about default permissions, we need to understand the permissions we need to operate on files or directories.
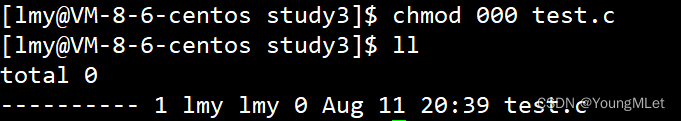
First, let's first understand what kind of permissions are needed to enter a directory? Let’s try them one by one. First, let’s reserve the read(r) permission:
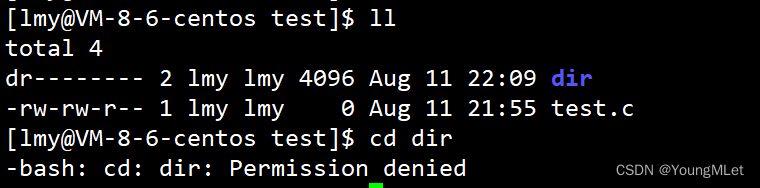
Read (r) permission cannot enter a directory, and then we only retain write (w) and execute (x) permissions respectively:
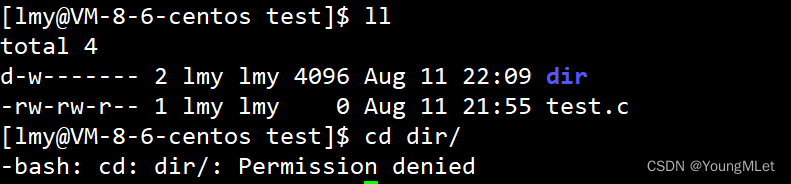
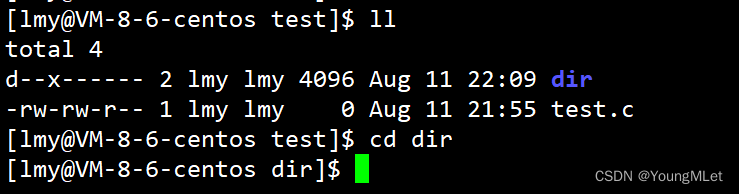
We can observe that entering a directory only requires execute (x) permissions.
Then we release the permissions of dir and create some new files in it, as follows:
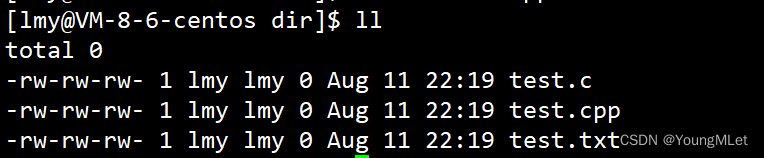
Then we remove the read (r) and write (w) of dir . We enter this directory and find that viewing and creating files are no longer possible, as shown in the figure:
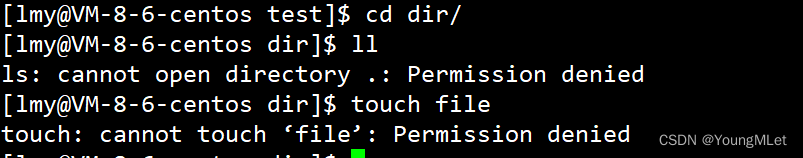
The reason is very simple, because the dir directory only has execute (x) permission, and the ll command needs read (r) permission to view file attributes; while creating a new file requires write (w) permission, you can verify it yourself.
So to summarize:
- Whether a specified user is allowed to view the directory's file listing requires read (r) permission.
- Whether to allow a specified user to create new files or delete files in the current directory requires write (w) permission.
- Entering a directory requires execute (x) permissions.
- A file must belong to a directory. Whether a file can be viewed is determined by the permissions of the directory.
- A file must belong to a directory. Whether a file can be deleted is determined not by the file itself, but by whether the directory to which it belongs and the corresponding account have write (w) permissions!
2. Default permissions for files and directories
We need to know that the default permission of a new file is 666 ; the default permission of a new directory is 777 ; but in fact, when we create a new file and directory, their default permissions are not what we said, as shown in the figure below:
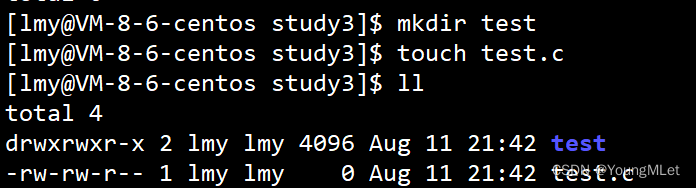
As shown in the figure, we can observe that the default permission of the newly created test directory is 776 ; the default permission of the newly created test.c file is 664 ; the reason is that when creating a file or directory, it is also affected by the umask permission mask. umask function: View or modify file mask.
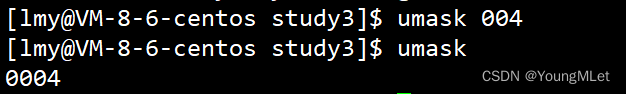
We can view the permission mask by entering umask on the command line, as shown below:
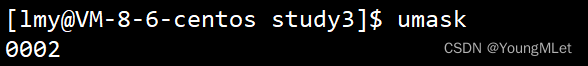
To modify the permission mask, just follow the permission mask after umask :
So why does permission mask exist? What is the permission mask? What is it used for? Let’s analyze it below.
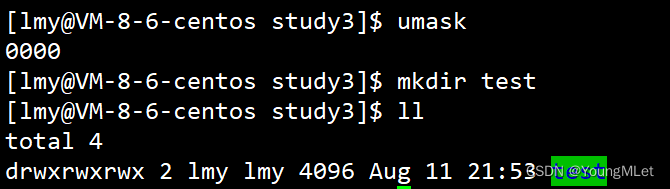
Assuming that we are not restricted by the permission mask, we change the permission mask to 000 and then create a directory, as shown in the figure:
Then we go into this directory and create a file:
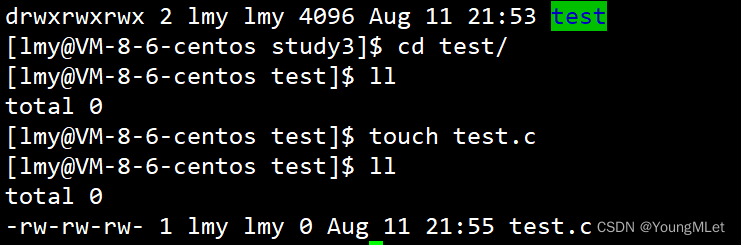
Now the default permission of this file is 666 , because our permission mask has been changed to 000 ; now in this file, the other group has the permission to write (w) , so it means that everyone can modify this file, which means This makes this file unsafe; therefore we should remove the write (w) permission of the other group in this file, as shown below:
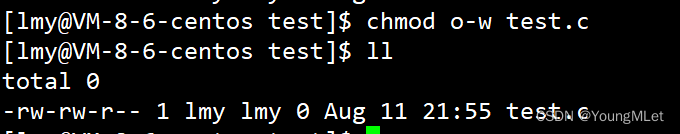
Is this file now safe? no! Although in this file, the other group does not have the permission to write (w) , but as we said earlier, whether a file can be deleted is not determined by the file itself, but by whether the directory to which it belongs and the corresponding account have the permission to write (w). ) Authority decision! We need to know that this directory releases all permissions to the other group, because the permission mask is 000 , so it means that everyone can enter this directory and delete this file, which means that if you don’t let me see it, I will destroy it. Lose! This means this entire directory is unsafe!
So when we look back, we should be able to guess why there is a permission mask by now. It is to protect the security of directories and files. Specifically, it is to prevent the other group from posing a threat to our directories and files.
So how does the permission mask work? The reason is that all permissions that appear in the permission mask will eventually be removed from the starting permissions. For example, the following picture:
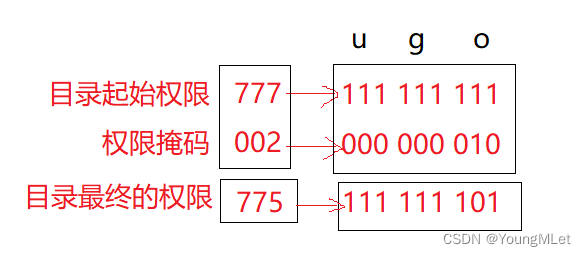
Therefore, the permission mask removes the write (w) permission of the other group , effectively protecting the security of the directory and the files in the directory. The specific implementation in the above picture is: final permission = starting permission& (~umask) .
So this explains why the actual default permission of a new directory is 775 ; why the actual default permission of a new file is 664 .
3. Sticky bit
Generally speaking, the situation we mentioned above is unlikely to occur, because different accounts will not be in the same directory; but if there are special circumstances, our multiple accounts want to cooperate with each other and share some data, but Don't want others to modify our data?
At this time, we need to use the sticky bit . The sticky bit is used chmod +t 目录名. The sticky bit can only be set for directories. The usage is as follows:
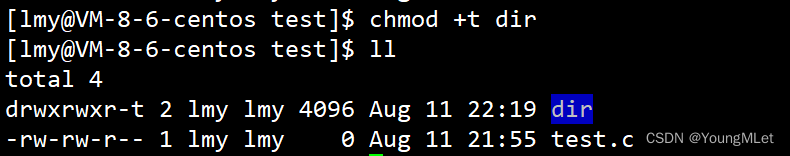
When a directory is set to the sticky bit , files in the directory can only be accessed by
- Delete by super administrator (root)
- The owner of the directory is deleted
- The owner of the file deletes