OAuth 2.0, JWT (JSON Web Token) and Spring Security are security-related concepts and technologies with different functions and uses.
OAuth 2.0 (Open Authorization):
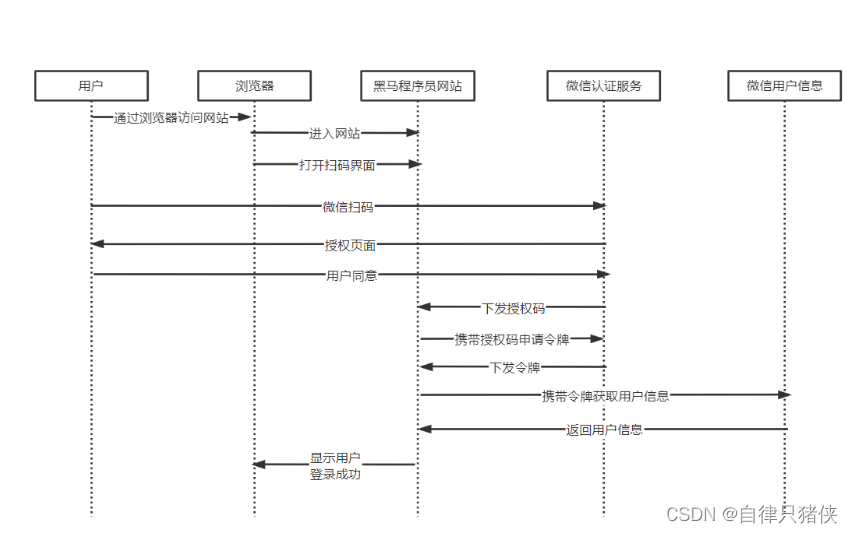
OAuth 2.0 is an authorization framework for authorizing third-party applications to access user resources without sharing the user's credentials. It provides users with better privacy and security, and allows users to have fine-grained control over authorization. The core concepts of OAuth 2.0 include resource owner (Resource Owner), client (Client), authorization server (Authorization Server) and resource server (Resource Server). OAuth 2.0 issues an access token (Access Token) through the authorization server, which is used to access resources on the protected resource server.
JWT (JSON Web Token):
JWT is a JSON-based open standard (RFC 7519) for securely transferring information between parties. A JWT contains a digitally signed or encrypted JSON object that can be securely passed between systems. The format of JWT consists of three parts: header (Header), payload (Payload) and signature (Signature). It can be used to verify and determine the identity of the sender and whether the transmitted data has been tampered with.
Spring Security:
Spring Security is a powerful framework for handling authentication and authorization in Java applications. It provides a comprehensive set of security features for protecting applications from various security threats and supports various authentication and authorization mechanisms. Spring Security can be integrated with technologies such as OAuth 2.0 and JWT for a more flexible and secure authentication and authorization process.
Summary:
They can have this inclusion relationship: JWT<OAuth 2.0<Spring Security, but it is not absolute!
OAuth 2.0 is a framework for authorization and access to protected resources.
JWT is a standard for securely transferring information between parties.
Spring Security is a framework for handling authentication and authorization.