● Click the ↑ blue word to follow us and get more security risk notices
Vulnerability overview |
|||
Vulnerability name |
Linux Kernel Privilege Escalation Vulnerability |
||
Vulnerability number |
QVD-2023-15242、CVE-2023-3269 |
||
open time |
2023-07-05 |
Affected object magnitude |
10,000 level |
Qi Anxin Rating |
high risk |
CVSS 3.1 score |
7.8 |
threat type |
privilege escalation |
use possibility |
middle |
PoC status |
published |
state of use in the wild |
Not found |
EXP state |
published |
Technical Details Status |
published |
Conditions of use: Need local low-privilege trigger. |
|||
(Note: Qi Anxin CERT's in-depth vulnerability analysis report includes the POC and technical details of this vulnerability. See the end of the article for subscription methods.)
01
Vulnerability details
>>>>
affect components
The Linux kernel is the main component of the Linux operating system (OS) and the core interface between computer hardware and its processes. It is responsible for the communication between the two and also manages resources as efficiently as possible.
>>>>
Vulnerability description
Recently, Qi Anxin CERT detected a Linux Kernel privilege escalation vulnerability (CVE-2023-3269) , also known as "Stack Rot" . There is a reuse-after-free vulnerability in the memory management subsystem of the Linux kernel. Local low-privileged users can use this vulnerability to elevate to ROOT privileges. At present, the technical details, POC and EXP of this vulnerability have been made public on the Internet, and Qi Anxin CERT has successfully reproduced this vulnerability. In view of the rising threat of this vulnerability, customers are advised to do self-examination and protection as soon as possible.
02
Sphere of influence
>>>>
Affected version
v6.1-rc1 <= Linux Kernel <= v6.5-rc1
>>>>
unaffected version
RedHat Linux Kernel
>>>>
Other affected components
none
03
Recurrence
At present, Qi Anxin CERT has successfully reproduced the Linux Kernel privilege escalation vulnerability (CVE-2023-3269) , the screenshot is as follows:
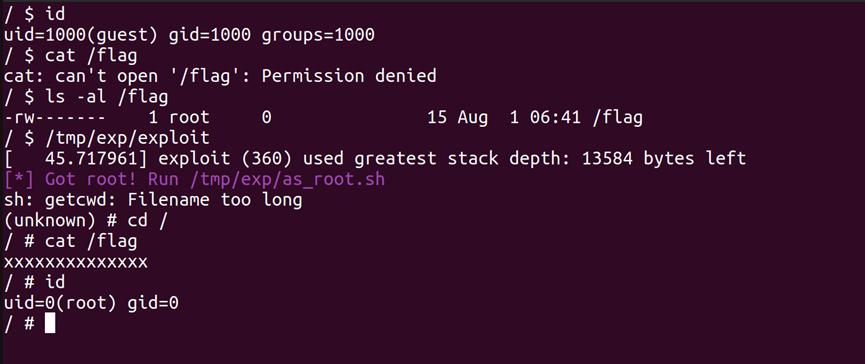
04
disposal advice
>>>>
security update
At present, the official version has been released, and affected users can update the kernel to a safe version:
Linux Kernel >= 6.1.37
Linux Kernel >= 6.3.11
Linux Kernel >= 6.4.1
05
References
[1]https://www.openwall.com/lists/oss-security/2023/07/05/1
[2]https://security-tracker.debian.org/tracker/CVE-2023-3269
[3]https://ubuntu.com/security/CVE-2023-3269
[4]https://access.redhat.com/security/cve/cve-2023-3269
06
timeline
On August 1, 2023, Qi Anxin CERT issued a security risk notice.
07
In-depth analysis report
The in-depth analysis report (including PoC and technical details) has been subscribed, scan the QR code below the picture to apply:

Please indicate "Reprinted from Qi Anxin Code Guard https://codesafe.qianxin.com".


Qi Anxin code guard (codesafe)
The first domestic product line focusing on software development security.
 If you feel good, just click "Looking" or "Like"~
If you feel good, just click "Looking" or "Like"~