The Difference Between Penetration Testing and Intrusion
Penetration testing: Taking security as the basic principle, analyzing the potential security risks and vulnerabilities of the target from the perspective of attackers and defenders, with the ultimate goal of protecting system security.
Intrusion: Obtain system permissions and various sensitive information through various methods, even destructive operations.
General penetration testing process

1. Define your goals
l Determine the scope: the scope of the test target, ip, domain name, internal and external network, and test account.
l Determining the rules: how far it can penetrate, the time required, whether it can be modified and uploaded, whether it can be elevated, and so on.
l Determine requirements: web application vulnerabilities, business logic vulnerabilities , personnel authority management vulnerabilities, and so on.
2. Information collection,
l Method: active scanning, open search, etc.
l Open search: Use search engines to obtain: background, unauthorized pages, sensitive URLs, etc.
l Basic information: IP, network segment, domain name, port.
l Application information: the application of each port. Such as web applications, mail applications, and so on.
l System information: operating system version
l Version information: the version of all these detected things.
l Service information: various information of middleware, plug-in information.
l Personnel information: domain name registrant information, the id of the person who posted in the web application, the name of the administrator, etc.
l Protection information: Try to see if the protection equipment can be detected.
3. Vulnerability detection
Use the corresponding vulnerabilities for various systems, applications, etc. listed in the previous step.
method:
(1) Missing scan, awvs, IBM appscan, etc.
(2) Combined with the vulnerability, go to exploit-db and other locations to find the exploit.
(3) Look for the verification poc on the Internet.
content:
l System vulnerabilities: the system has not been patched in time
l WebSever vulnerability: WebSever configuration problem
l Web application vulnerabilities: Web application development issues
l Other port service vulnerabilities: various 21/8080(st2)/7001/22/3389
l Communication security: clear text transmission, token transmission in cookies, etc.
4. Vulnerability verification
Verify all the vulnerabilities found in the previous step that may be successfully exploited. Combined with the actual situation, build a simulated environment for testing. Successfully applied to the target.
l Automated verification: combined with the results provided by automated scanning tools
l Manual verification, based on public resources
l Test verification: build your own simulation environment for verification
l Login guessing: Sometimes you can try to guess the account password and other information of the login port
l Business vulnerability verification: If a business vulnerability is found, it must be verified
Use of public resources
l exploit-db/wooyun/
l google hacking
l Penetration code website
l Common and default passwords
l Vulnerability warnings from vendors, etc.
5. Information analysis
Prepare for the next step of penetration.
l Precise strike: Prepare the exploit of the vulnerability detected in the previous step for precise strike
l Bypass defense mechanism: whether there is a firewall and other equipment, how to bypass
l Customized attack path: the best tool path, based on weak entrances, high intranet authority locations, and final goals
l Bypass the detection mechanism: whether there is a detection mechanism, traffic monitoring, anti-virus software, malicious code detection, etc. (anti-kill)
l Attack code: code obtained through experiments, including but not limited to xss code, sql injection statement, etc.
6. Get what you need
Implement the attack: according to the results of the previous steps, carry out the attack
l Obtain internal information: infrastructure (network connection, vpn, routing, topology, etc.)
l Further penetration: intranet intrusion, sensitive targets
l Persistent existence: Generally, we do not need to infiltrate customers. Rookit, backdoor, add management account, stationing methods, etc.
l Clean up traces: clean up related logs (access, operation), upload files, etc.
7. Information collation
l Organize infiltration tools: organize the code, poc, exp, etc. used in the infiltration process
l Organize and collect information: organize all the information collected during the infiltration process
l Organize vulnerability information: sort out various vulnerabilities encountered in the penetration process, and various vulnerable location information
8. Create a report
l Arrange on demand: organize the data according to the scope and needs determined with the customer in the first step, and form the data into a report
l Supplementary introduction: analyze the cause of the vulnerability, the verification process and the harm it brings
l Repair suggestions: Of course, reasonable, efficient and safe solutions should be put forward for all the problems that arise
Process summary

Learning resource sharing
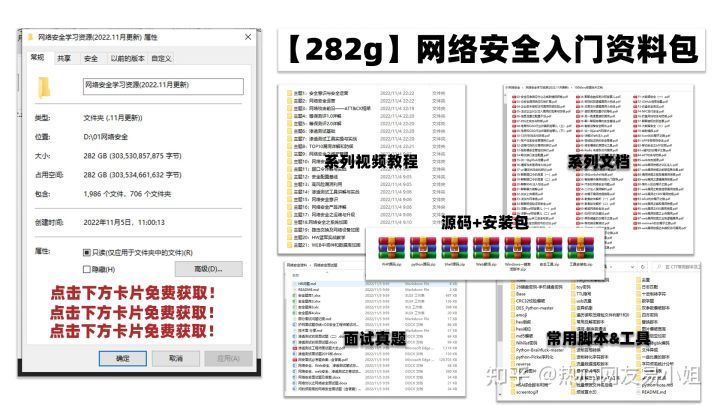
Many small partners want to have a glimpse of the entire system of network security. Here I share a " Learning Roadmap for Network Security Engineers with an Average Salary of 40w" that has been polished for 4 years and has been successfully revised to version 4.0.

Some video tutorials that are not available on other platforms
Network Security Super Practical Tutorial Documentation Toolkit

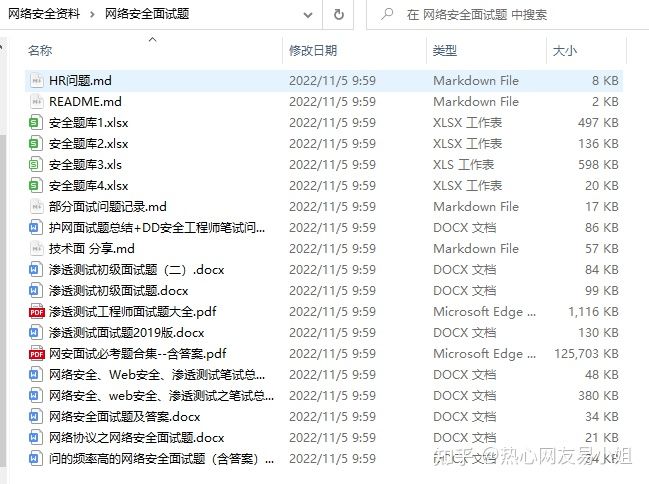
Leak-checking and fill-in-vacancy interview question bank
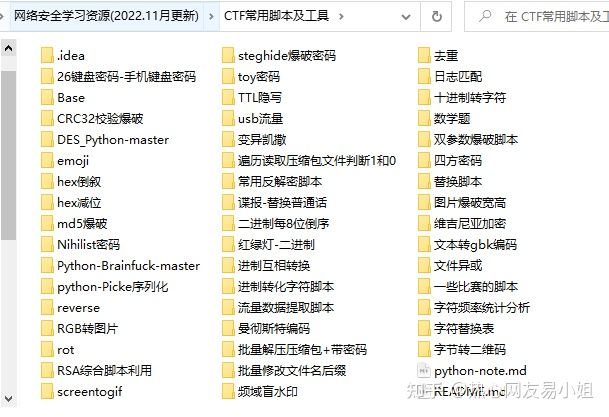
List of common tools
The Difference Between Penetration Testing and Intrusion
Penetration testing: Taking security as the basic principle, analyzing the potential security risks and vulnerabilities of the target from the perspective of attackers and defenders, with the ultimate goal of protecting system security.
Intrusion: Obtain system permissions and various sensitive information through various methods, even destructive operations.
General penetration testing process

1. Define your goals
l Determine the scope: the scope of the test target, ip, domain name, internal and external network, and test account.
l Determining the rules: how far it can penetrate, the time required, whether it can be modified and uploaded, whether it can be elevated, and so on.
l Determine requirements: web application vulnerabilities, business logic vulnerabilities , personnel authority management vulnerabilities, and so on.
2. Information collection,
l Method: active scanning, open search, etc.
l Open search: Use search engines to obtain: background, unauthorized pages, sensitive URLs, etc.
l Basic information: IP, network segment, domain name, port.
l Application information: the application of each port. Such as web applications, mail applications, and so on.
l System information: operating system version
l Version information: the version of all these detected things.
l Service information: various information of middleware, plug-in information.
l Personnel information: domain name registrant information, the id of the person who posted in the web application, the name of the administrator, etc.
l Protection information: Try to see if the protection equipment can be detected.
3. Vulnerability detection
Use the corresponding vulnerabilities for various systems, applications, etc. listed in the previous step.
method:
(1) Missing scan, awvs, IBM appscan, etc.
(2) Combined with the vulnerability, go to exploit-db and other locations to find the exploit.
(3) Look for the verification poc on the Internet.
content:
l System vulnerabilities: the system has not been patched in time
l WebSever vulnerability: WebSever configuration problem
l Web application vulnerabilities: Web application development issues
l Other port service vulnerabilities: various 21/8080(st2)/7001/22/3389
l Communication security: clear text transmission, token transmission in cookies, etc.
4. Vulnerability verification
Verify all the vulnerabilities found in the previous step that may be successfully exploited. Combined with the actual situation, build a simulated environment for testing. Successfully applied to the target.
l Automated verification: combined with the results provided by automated scanning tools
l Manual verification, based on public resources
l Test verification: build your own simulation environment for verification
l Login guessing: Sometimes you can try to guess the account password and other information of the login port
l Business vulnerability verification: If a business vulnerability is found, it must be verified
Use of public resources
l exploit-db/wooyun/
l google hacking
l Penetration code website
l Common and default passwords
l Vulnerability warnings from vendors, etc.
5. Information analysis
Prepare for the next step of penetration.
l Precise strike: Prepare the exploit of the vulnerability detected in the previous step for precise strike
l Bypass defense mechanism: whether there is a firewall and other equipment, how to bypass
l Customized attack path: the best tool path, based on weak entrances, high intranet authority locations, and final goals
l Bypass the detection mechanism: whether there is a detection mechanism, traffic monitoring, anti-virus software, malicious code detection, etc. (anti-kill)
l Attack code: code obtained through experiments, including but not limited to xss code, sql injection statement, etc.
6. Get what you need
Implement the attack: according to the results of the previous steps, carry out the attack
l Obtain internal information: infrastructure (network connection, vpn, routing, topology, etc.)
l Further penetration: intranet intrusion, sensitive targets
l Persistent existence: Generally, we do not need to infiltrate customers. Rookit, backdoor, add management account, stationing methods, etc.
l Clean up traces: clean up related logs (access, operation), upload files, etc.
7. Information collation
l Organize infiltration tools: organize the code, poc, exp, etc. used in the infiltration process
l Organize and collect information: organize all the information collected during the infiltration process
l Organize vulnerability information: sort out various vulnerabilities encountered in the penetration process, and various vulnerable location information
8. Create a report
l Arrange on demand: organize the data according to the scope and needs determined with the customer in the first step, and form the data into a report
l Supplementary introduction: analyze the cause of the vulnerability, the verification process and the harm it brings
l Repair suggestions: Of course, reasonable, efficient and safe solutions should be put forward for all the problems that arise
Process summary

Learning resource sharing
Many small partners want to have a glimpse of the entire system of network security. Here I share a " Learning Roadmap for Network Security Engineers with an Average Salary of 40w" that has been polished for 4 years and has been successfully revised to version 4.0.

Some video tutorials that are not available on other platforms

Network Security Super Practical Tutorial Documentation Toolkit


Leak-checking and fill-in-vacancy interview question bank

List of common tools
