Overview of National Secret Algorithms, and Integrated Applications of Algorithms (sm2, sm3, sm4)
I. Overview
Due to the needs of the project, it is necessary to integrate the encryption and decryption of the national secret, so I reviewed the old secret of the national secret again. At the same time, I sorted out some algorithms of national secrets.
This article mainly starts with the introduction of national secret related algorithms, the integration of application systems, the packaging of tools, etc., and conducts in-depth study of national secrets.
-
In order to ensure the security of commercial ciphers, the State Cryptography Administration has formulated a series of cipher standards, including: SM1 (SCB2), SM2, SM3, SM4, SM7, SM9, Zu Chongzhi cipher algorithm (ZUC) and so on.
-
SM1, SM4, SM7, Zu Chong's cryptographic algorithm (ZUC): Symmetrical algorithm.
-
SM2, SM9: Asymmetric algorithm.
-
SM3: Hash algorithm.
-
The SM1 and SM7 algorithms are not public. When calling the algorithm, it needs to be called through the interface of the encryption chip.
2. Classification Overview
3.1, SM1 symmetric password
- The SM1 algorithm is a block cipher algorithm with a block length of 128 bits and a key length of 128 bits. The security strength of the algorithm and the performance of related hardware and software are equivalent to those of AES. The algorithm is not disclosed and only exists in the chip in the form of an IP core.
- Using this algorithm, a series of security products such as chips, smart IC cards, smart password keys, encryption cards, and encryption machines have been developed, which are widely used in various application fields of e-government, e-commerce and national economy (including national government affairs communication, police communication, etc.) and other important areas).
3.2. SM2 Elliptic Curve Public Key Cryptography Algorithm
- The SM2 algorithm is the ECC elliptic curve cryptography mechanism, but it is different from ECDSA, ECDH and other international standards in terms of signature and key exchange, but adopts a more secure mechanism. In addition, SM2 recommends a 256-bit curve as a standard curve.
- The SM2 standard includes four parts: General Principles, Digital Signature Algorithm, Key Exchange Protocol, and Public Key Encryption Algorithm, and the appendix of each part details the relevant details and examples of implementation.
- The SM2 algorithm mainly considers the elliptic curves on the prime fields Fp and F2m, and introduces the representation and operation of these two types of fields, as well as the representation and operation of the points on the elliptic curves on the fields, and the calculation algorithm for multiple points. Then it introduces data conversion in programming language, including data conversion rules between integer and byte string, byte string and bit string, field element and bit string, field element and integer, point and byte string.
- The generation and verification of the parameters of the elliptic curve on the finite field are explained in detail. The parameters of the elliptic curve include the selection of the finite field, the parameters of the elliptic curve equation, the selection of the base point of the elliptic curve group, etc., and the selection standard is given for verification. Finally, for the generation of the key pair on the elliptic curve and the verification of the public key, the user’s key pair is (s, sP), where s is the user’s private key, and sP is the user’s public key. Due to the discrete logarithm problem, from sP It is difficult to get s, and the details of key pair generation and verification methods are given for prime fields and binary extended fields. The knowledge in the general principles also applies to the SM9 algorithm.
- On the basis of general principles, digital signature algorithms (including digital signature generation algorithms and verification algorithms), key exchange protocols, and public key encryption algorithms (including encryption algorithms and decryption algorithms) are given, and algorithm descriptions are given in each part , algorithm flow and related examples.
- The digital signature algorithm, key exchange protocol and public key encryption algorithm all use the SM3 cryptographic hash algorithm and random number generator approved by the State Administration of Cryptography. Digital signature algorithm, key exchange protocol and public key encryption algorithm select finite fields and elliptic curves according to the general rules, and generate key pairs.
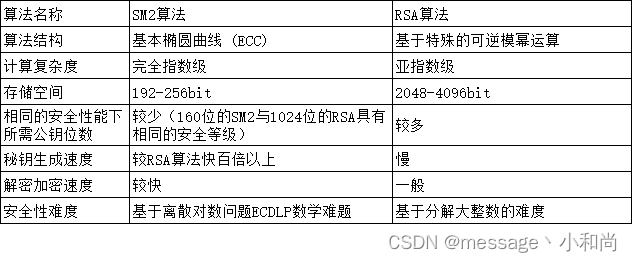
- The SM2 algorithm is superior to the RSA algorithm in many aspects (RSA was developed early and widely used, and it is natural for SM2 to lead). The security comparison with RSA is shown in the figure below.
3.3, SM3 hash algorithm
- SM3 cryptographic hash (hash, hash) algorithm gives the calculation method and calculation steps of the hash function algorithm, and gives operation examples. This algorithm is suitable for digital signature and verification in commercial cryptographic applications, generation and verification of message authentication codes, and random number generation, and can meet the security requirements of various cryptographic applications. Used in SM2, SM9 standards.
- This algorithm generates a hash value with a length of 256 bits for a bit message whose input length is less than 2 to the 64th power, after padding and iterative compression, using XOR, modulus, modulo addition, shift, AND, OR, NOT operations , consisting of padding, iterative process, message expansion and compression functions. See the SM3 standard for specific algorithms and operation examples.
3.4, SM4 symmetric algorithm
- This algorithm is a grouping algorithm and is used in wireless LAN products. The packet length of this algorithm is 128 bits, and the key length is 128 bits. Both the encryption algorithm and the key expansion algorithm adopt a 32-round nonlinear iterative structure. The structure of the decryption algorithm is the same as that of the encryption algorithm, except that the order in which the round keys are used is reversed, and the decryption round key is the reverse order of the encryption round key.
- This algorithm adopts a nonlinear iterative structure, and each iteration is given by a round function, where the round function is composed of a nonlinear transformation and a linear transformation, and the nonlinear transformation is given by an S-box. Where rki is the round key, and the synthetic permutation T constitutes the round function. The generation of the round key is similar to the process in the above figure, and the encryption key is used as the input to generate it. The linear transformation in the round function is different, and there are some differences in parameters. For a detailed description and examples of the SM4 algorithm, see the SM4 standard.
3.5, SM7 symmetric password
- The SM7 algorithm is a block cipher algorithm with a block length of 128 bits and a key length of 128 bits. SM7 is suitable for non-contact IC cards, and its applications include identification applications (access control cards, work permits, competition passes), ticketing applications (large-scale event tickets, exhibition tickets), payment and card applications (point consumption cards, campus cards) , corporate card, etc.).
3.6, SM9 identification password algorithm
- In order to reduce the complexity of key and certificate management in the public key system, Adi Shamir, an Israeli scientist and one of the inventors of the RSA algorithm, proposed the concept of Identity-Based Cryptography in 1984. The identification password uses the user's identification (such as email address, mobile phone number, QQ number, etc.) as the public key, omitting the process of exchanging digital certificates and public keys, making the security system easy to deploy and manage, and very suitable for end-to-end offline secure communication , Cloud data encryption, attribute-based encryption, policy-based encryption in various occasions. In 2008, the identification encryption algorithm officially obtained the commercial secret algorithm model: SM9 (Shangmi No. 9 algorithm) issued by the State Cryptography Administration, which laid a solid foundation for the application of identification encryption technology in my country.
- The SM9 algorithm does not need to apply for a digital certificate, and is suitable for the security guarantee of various emerging applications of Internet applications. Such as cloud-based password services, email security, smart terminal protection, Internet of Things security, cloud storage security, etc. These security applications can use mobile phone numbers or email addresses as public keys to implement security applications such as data encryption, identity authentication, call encryption, and channel encryption, and are easy to use and deploy, thus opening the door to the popularization of cryptographic algorithms.
3.7, ZUC Zu Chong's algorithm
- Zu Chongzhi sequence cipher algorithm is a stream cipher algorithm independently researched by China. It is an international standard cipher algorithm used in mobile communication 4G networks. The algorithm includes Zu Chongzhi algorithm (ZUC), encryption algorithm (128-EEA3) and integrity algorithm (128-EEA3) EIA3) Three parts. At present, there is an optimized implementation of the ZUC algorithm, and there are hardware implementations and optimizations specifically for 128-EEA3 and 128-EIA3
- As a national strategic resource, cryptographic algorithms are more critical than at any time in history. In the era of big data and cloud computing, key information is often obtained from massive data through data mining technology, so everyone's information protection is very important.
3. Integrated SM2 encryption and decryption
JAVA integrated national secret SM2: https://blog.csdn.net/qq_38254635/article/details/131810661
4. Integrated SM3 encryption and signature verification
JAVA integrated national secret SM3: https://blog.csdn.net/qq_38254635/article/details/131810696
5. Integrated SM4 encryption and decryption
JAVA integrated national secret SM4: https://blog.csdn.net/qq_38254635/article/details/131810715
6. Resource download
SpringBoot integrates SM2, SM3, SM4 code package download
CSDN download address: https://download.csdn.net/download/qq_38254635/88063758
Baidu network disk download address: https://pan.baidu.com/s/1oy0OqRSvYues-w_lbHe27A ?pwd=48i0
Extraction code: 48i0
The reference link of the national secret series of documents is as follows:
National secret algorithm overview: https://blog.csdn.net/wang_jing_jing/article/details/121493025
Java implements national secret encryption and decryption: https://blog.csdn.net/m0_37539286/article /details/127584892
JAVA – sm3 encrypted signature, and prevent repeated attacks: https://blog.csdn.net/DGH2430284817/article/details/131472103
Notes on national secret algorithms SM1, SM2, SM3, SM4: https:// www.cnblogs.com/zhangshitong/p/8057845.html
Java for JT/T808 national secret SM4 encryption and decryption processing: https://blog.51cto.com/u_12846753/4584586