With the acceleration of informatization, enterprise networks are becoming more and more perfect. With the acceleration of enterprise digitalization, more and more key businesses are running on the basis of computer networks, more and more important information is transmitted through the network, and enterprise networks are facing increasingly serious security threats. These security threats are based on stealing information and collecting intelligence. It has the ability to work secretly for a long time, which poses a serious threat to the data security of the country and enterprises.
Especially after the new crown epidemic has swept the world, international relations are unpredictable, and the construction of national key information infrastructure is also facing invisible cyber security threats. We should plan ahead, make every effort, and turn passive into active. Aiming at the characteristics of random, scattered and massive network traffic, high-speed, flexible and comprehensive storage and retrieval technical support is an important feature to solve current network traffic problems. Therefore, mass storage, fast retrieval, flexible analysis and accurate traceability based on full-flow data An all-in-one solution is an urgent need in the current network security field .
Smart Eye full flow security analysis system
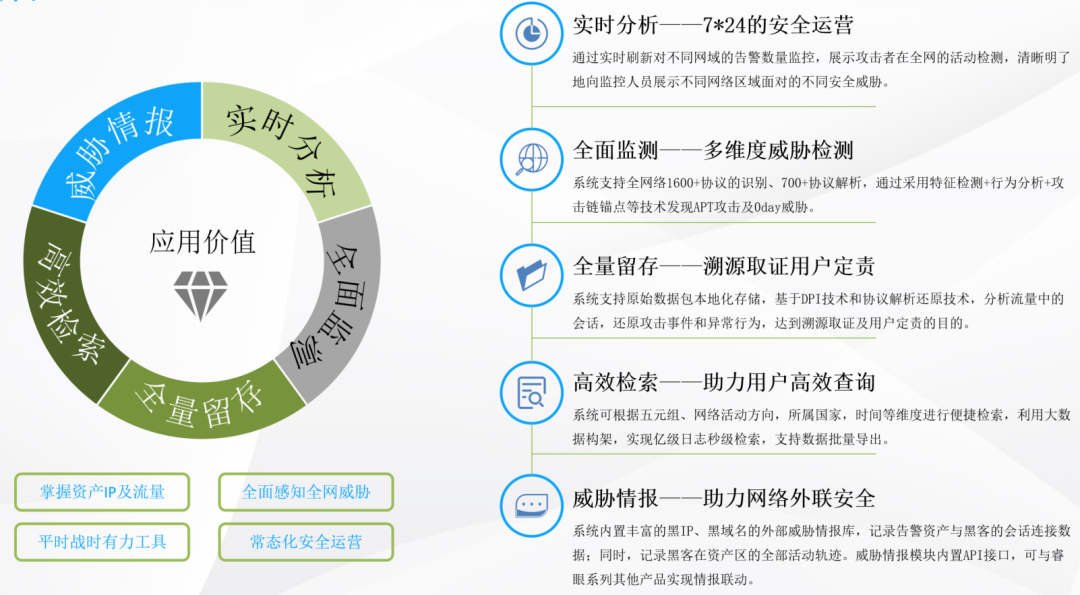
The system takes full-flow storage and backtracking technology as the core, and provides users with a threat detection platform that is handy in monitoring and early warning, threat detection, and traceability analysis . This system is independently developed by Zhongrui Tianxia , and it is a real-time monitoring and intelligent analysis platform that adapts to user business logic. The system takes attack and defense as the core concept, and uses data processing technology to deeply analyze and decode network protocol data, combined with network attack identification and traffic security analysis technology, to detect and analyze security events in network traffic, and convert the research and judgment of attack and defense technology into business risks result . The full-flow security analysis platform combines product capabilities such as asset structure, collection and storage, and analysis and retrieval. It has the capabilities of full-flow recording, full-log retention, full-data retrieval, and threat discovery . It provides a powerful solution for attack evidence collection and user accountability. data support.
Five core functions
0 1 Full flow storage detection
full storage
The system can store the full traffic in the local space in the form of session flow PCAP files, and adopts high-reliability storage technology to ensure that the stored data packets will not be lost or tampered with. It can quickly store and retrieve massive data packets, and supports distributed storage and multi-node storage at the same time, improving the efficiency of storage and retrieval.
real-time monitoring
The system can monitor the entire traffic of the enterprise network in real time, and find abnormal traffic and abnormal behavior in the network. This function can help enterprises discover network attacks in time and prevent data loss and property damage caused by attacks.
traffic backtracking
Through traffic traceability analysis, the system can find out the source and attack path of network attack events, as well as the attack target and method, analyze the sessions in the traffic, restore the attack events and abnormal behaviors, realize the complete restoration of the attack process, and achieve traceability and evidence collection and user accountability the goal of.
Insight
The system can conduct a comprehensive analysis of all communication flows within the enterprise, including internal communication and external communication. The analysis results can be displayed visually, so that users can understand the security situation more intuitively, and help enterprises identify internal communication relationships, external attack sources, malware and other potential threats to make quick decisions.
The full-flow storage detection function of the full-flow security analysis system can help enterprises realize full-flow storage and efficient retrieval, and provide efficient and accurate attack identification and prevention capabilities, effectively ensuring enterprise network security.
0 2Threat intelligence linkage
Threat intelligence data source integration
The system integrates a variety of threat intelligence data sources, including public intelligence data sources, industry intelligence data sources, enterprise internal intelligence data sources, etc., and can obtain the latest threat intelligence information in a timely manner.
Real-time threat matching
The system can detect network threats in a timely manner by matching threat intelligence and enterprise network traffic in real time, including new threats, advanced persistent threats, and APTs.
Intelligent alarm
According to the matching results of threat intelligence, the system can intelligently generate alarm events, including detailed information such as threat level, attack type, attack source, and attack target, to help enterprises quickly discover and respond to network threats.
Threat intelligence sharing
The system supports the sharing of threat intelligence information, which can exchange and share the threat intelligence information inside the enterprise with external threat intelligence data sources, and improve the threat intelligence acquisition and analysis capabilities of the enterprise.
The threat intelligence linkage function of the full-flow security analysis system can provide enterprises with comprehensive, real-time, and intelligent network threat analysis and defense services, help enterprises discover and respond to various network threats, improve enterprise network security defense and disposal capabilities, and ensure enterprise safe operation and business development.
0 3 Asset risk
asset discovery
The system can discover the network assets of enterprises in real time, and classify, mark and archive them. Through this function, enterprises can fully understand the situation of network assets, and evaluate and deal with new assets discovered in a timely manner.
Asset valuation
The system can conduct a comprehensive assessment of network assets, including asset vulnerabilities, weak passwords, and security policies. The assessment results can help enterprises understand the risk level of network assets and take corresponding security measures.
Risk Analysis
The system can analyze and rank the risks of network assets, allowing enterprises to understand the importance and impact of various risks. This function can help enterprises formulate more precise security policies and improve network security levels.
Risk Warning
The system can monitor and warn the risks of network assets in real time, and discover potential security threats in time. This function can help enterprises take measures to protect network security before security incidents occur.
The asset risk function of the full-flow security analysis system can help enterprises fully understand the situation and risks of network assets, provide scientific risk assessment and analysis, discover and respond to security threats in time, and escort the network security of enterprises.
0 4 All-Inclusive Forensic Analysis
Data stream real-time recording
The system can record all data flows in the enterprise network in real time, including traffic, protocol, source address, destination address, port and other information, helping enterprises to quickly obtain complete data information when network security incidents occur.
Data Stream Storage and Retrieval
The system can efficiently store and retrieve recorded data streams, support operations such as searching, filtering, sorting, and sorting stored data streams, and help enterprises quickly locate security incidents and attack behaviors.
Data Flow Analysis and Forensics
The system can conduct in-depth analysis and forensics on stored data streams, including traffic analysis, protocol analysis, behavior analysis, and security event restoration, to help enterprises quickly discover and locate security threats, and provide effective evidence to support the handling and tracking of security events. responsibility.
Intelligent analysis of data flow
The system can intelligently analyze the stored data flow through machine learning and artificial intelligence technology, helping enterprises discover hidden attacks and new security threats, and improving network security prevention and handling capabilities.
The all-inclusive forensic analysis function of the full-flow security analysis system can provide enterprises with comprehensive network data recording, storage, analysis and forensics services, help enterprises quickly locate and handle security incidents, improve network security prevention and disposal capabilities, and provide enterprise network security with More comprehensive and reliable protection.
0 5 all-round analysis function
Traffic Analysis
The system can conduct in-depth analysis and mining of all data flows in the enterprise network, including information such as flow size, flow protocol, and data packet content, helping enterprises quickly discover network threats and attack behaviors.
protocol analysis
The system can conduct in-depth analysis and identification of network protocols, including commonly used protocols such as HTTP, FTP, SMTP, and POP3, as well as unused protocols such as P2P, Tor, and VPN, helping enterprises discover abnormal protocols and attack behaviors in the network.
Behavior analysis
The system can conduct in-depth analysis and identification of various behaviors in the network, including user behavior, application behavior, device behavior, etc., to help enterprises discover abnormal behaviors and threats in the network.
Security Event Recovery
The system can comprehensively restore and analyze network security events, including the attacker's intrusion behavior, attack process, attack path, attack target, etc., helping enterprises quickly locate and deal with security events.
Threat Intelligence Analysis
The system can obtain the latest threat intelligence information through a variety of threat intelligence sources and analysis technologies, and perform real-time matching and analysis with enterprise network traffic to help enterprises discover and respond to new network threats.
The all-round analysis function of the full-flow security analysis system can provide enterprises with comprehensive and in-depth network threat analysis and defense services, help enterprises achieve comprehensive security protection and network security risk management, and improve the network security defense and anti-attack capabilities of enterprises. Effectively guarantee the safe operation and business development of enterprises. Comprehensive analysis.
feature of product

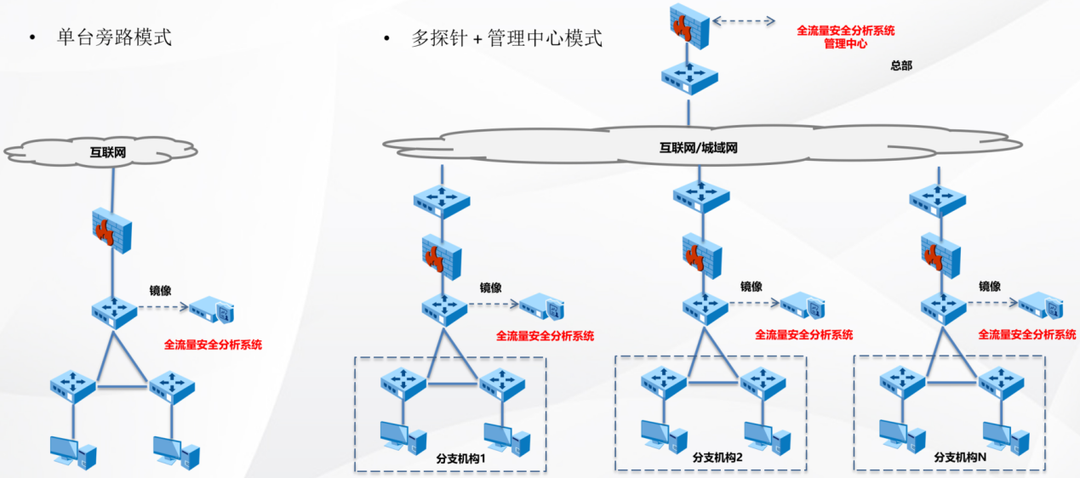
product deployment
product value