Encryption and Encryption Principles
Use XOR operation to realize image encryption and decryption functions.
XOR operation rules (0 for the same, 1 for different)
- If the operands are the same, the result is 0; if the operands are different, the result is 1
- XOR any number (0/1) with 0, the result is still itself
- XOR any number (0/1) with 1, the result is another number, that is, 0 becomes 1, 1 becomes 0
- XOR any number with itself, the result is 0
The same goes for image encryption and decryption
- Encryption process: XOR operation of plaintext a and key b to obtain ciphertext c
- Decryption process: XOR operation of ciphertext c and key b to obtain plaintext a
run a code
import cv2 as cv
import numpy as np
lena = cv.imread("lena.jpg")
row, colm,count = lena.shape
print(row)
print(colm)
key = np.random.randint(0, 256, size=[row, colm,count], dtype=np.uint8)
encryption = cv.bitwise_xor(lena, key)
decryption = cv.bitwise_xor(encryption, key)
cv.imshow("lena", lena)
cv.imshow("key", key)
cv.imshow("encryption",encryption)
cv.imshow("decryption",decryption)
cv.waitKey()
cv.destroyAllWindows()Run as follows:

Face encryption and decryption
Face encryption and decryption is actually the process of encrypting and decrypting some areas of the image.
The function of face coding is more like a combination of mask + np XOR operation. There are two ways of face coding, one is through the mask method, and the other is through the ROI method.
mask method
Encryption process:
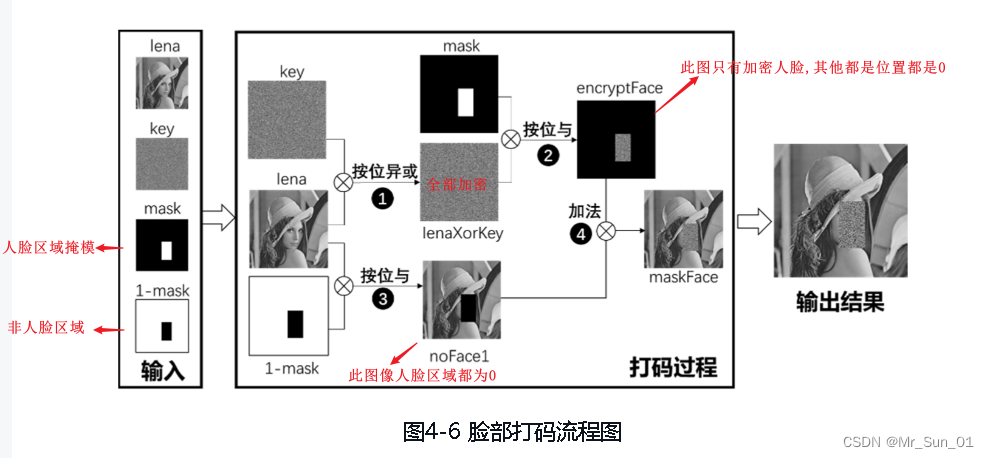
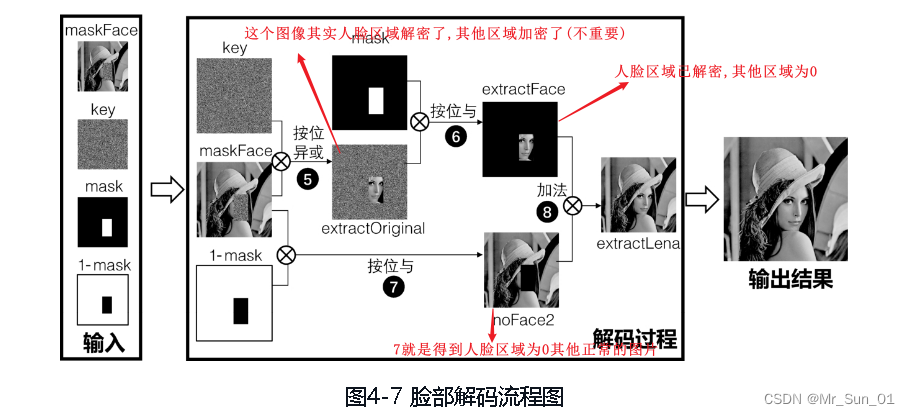
Decryption process:
The specific code is implemented as follows:
import cv2 as cv
import numpy as np
# 读取原始图
lena = cv.imread("lena.png", 0)
cv.imshow("lena", lena)
r, c = lena.shape
# 得到掩码模板
mask = np.zeros((r, c), dtype=np.uint8)
mask[220:400, 250:350] = 1
# 得到加密解密的密钥图像
key = np.random.randint(0, 256, size=[r, c], dtype=np.uint8)
# ========================获取加密的脸===================
# step1 使用密钥key对原始图片lena进行加密
lenaXorKey = cv.bitwise_xor(lena, key)
# step2 获取已经加密的脸部位置信息(整个加密图像与mask做与运算)
encryptFace = cv.bitwise_and(lenaXorKey, mask * 255)
# step3 另外再对lena图像进行处理 通过使用 反mask,得到没有人脸信息的lena图像
noFace = cv.bitwise_and(lena, (1 - mask) * 255)
# step4 把获取的已经加密的只有人脸的图像加到被扣掉人脸信息的lena图像上,得到人脸加密的lena图像
maskFace = encryptFace + noFace
cv.imshow("maskFace", maskFace)
# ========================开始人脸解密===================
# step5 将脸部加密的lena与密钥key进行异或,这样人脸区域会解密,其他区域会被加密(不重要)
extractOriginal = cv.bitwise_xor(maskFace, key)
# step6 提取解密后的人脸,其他区域是0
extractFace = cv.bitwise_and(extractOriginal, mask * 255)
# step7 从打码的lena图像中提取没有人脸信息的lena图像(人脸区域为0)
noface2 = cv.bitwise_and(maskFace, (1 - mask) * 255)
cv.imshow("nofaceee", noface2)
# step8 在扣掉人脸的lena图像中加入已经解密后的人脸
extractLena = noface2 + extractFace
cv.imshow("extractLena", extractLena)
cv.waitKey()
cv.destroyAllWindows()The program runs as follows:

ROI method
The ROI method is more about processing the face area.
The face encryption process is as follows:
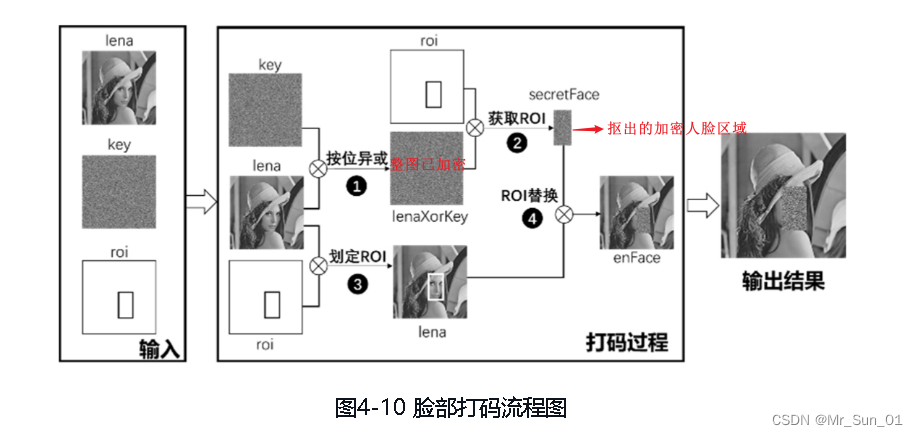
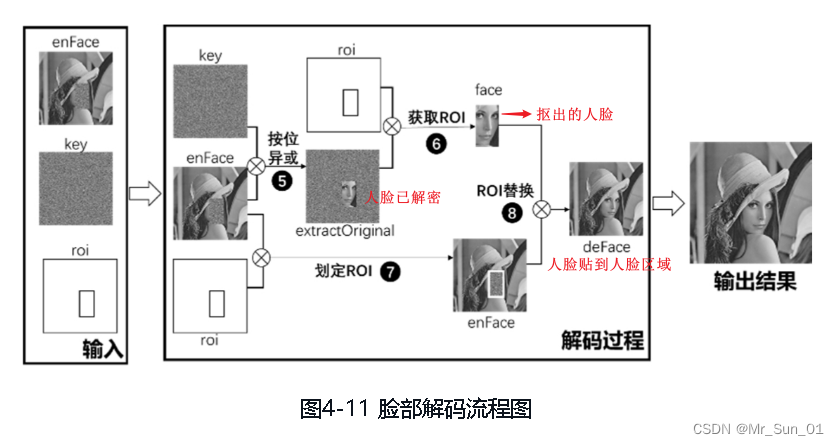
The face decryption process is as follows:
The process of encrypting and decrypting the face in the ROI method feels like a cheating process.
code show as below:
import cv2 as cv
import numpy as np
# 读取原始图
lena = cv.imread("lena.png", 0)
cv.imshow("lena", lena)
r, c = lena.shape
# 得到掩码模板
mask = np.zeros((r, c), dtype=np.uint8)
mask[220:400, 250:350] = 1
# 得到加密解密的密钥图像
key = np.random.randint(0, 256, size=[r, c], dtype=np.uint8)
# ========================获取加密的脸===================
# step1 使用密钥key对原始图片lena进行加密
lenaXorKey = cv.bitwise_xor(lena, key)
# step2 得到加密的人脸区域
secretFace = lenaXorKey[220:400, 250:350]
# step3 把加密的人脸区域贴到lena原始图上
lena[220:400, 250:350] = secretFace
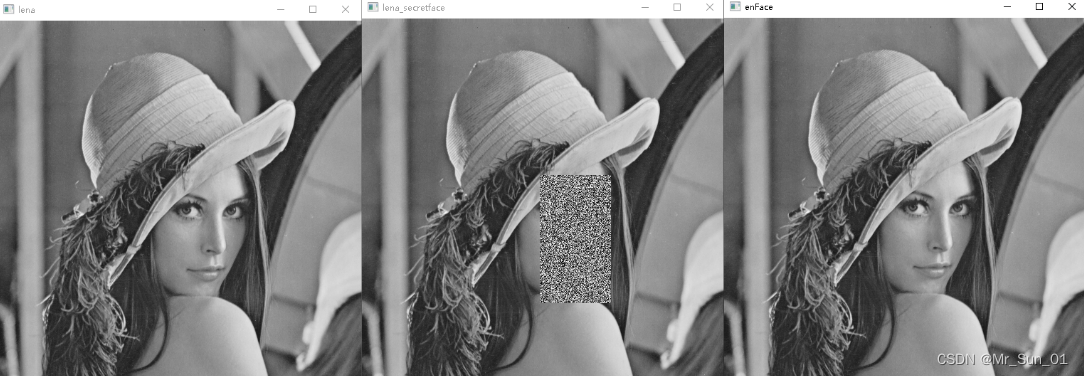
cv.imshow("lena_secretface", lena)
# ========================开始人脸解密===================
# step4 将脸部加密的lena与密钥key进行异或,这样人脸区域会解密,其他区域会被加密(不重要)
extractOriginal = cv.bitwise_xor(lena, key)
# step5 扣下已经解密的人脸图像
face = extractOriginal[220:400, 250:350]
# step6 把扣下的人脸贴到加密的lena上,这样,解密后的脸就把加密的人的区域覆盖了
lena[220:400, 250:350] = face
cv.imshow("enFace", lena)
cv.waitKey()
cv.destroyAllWindows()
The program runs as follows:
Summary: The encryption and decryption of images is more like XOR operations and masks, and the comprehensive use of ROI is not difficult overall.