
The login module is the first point of contact for users to contact the system. Especially for C-end business, if the registration process is too complicated, it will easily cause the loss of users; for B-end business, the registration process can be the first step It can also be ignored appropriately. It needs to be judged according to the coherence between the company's internal systems. If it is ignored, it can directly pull the verified account to log in, so as to reduce the waste of time.
01 Registration, login module
The login system can be divided into two login methods: registration login and pull third-party verification:
Pull third-party verification login:
Logging in does not require an account, but requires a unified verification logo to identify the account at a third party or account management office, such as the email suffix verification service provided by Microsoft. When logging in for the first time, you need to find the user in the background of the system and give the user access or other permissions. At this time, user identification information and permissions should be stored in the database to facilitate adding permissions and recording user operation records.
register log in:
The user needs to fill in the necessary information when registering and logging in for the first time. At this time, it is necessary to judge the need for third-party binding accounts such as email addresses and mobile phone numbers based on business needs.
In general, you can register directly through your mobile phone number, WeChat ID, QQ number, etc.
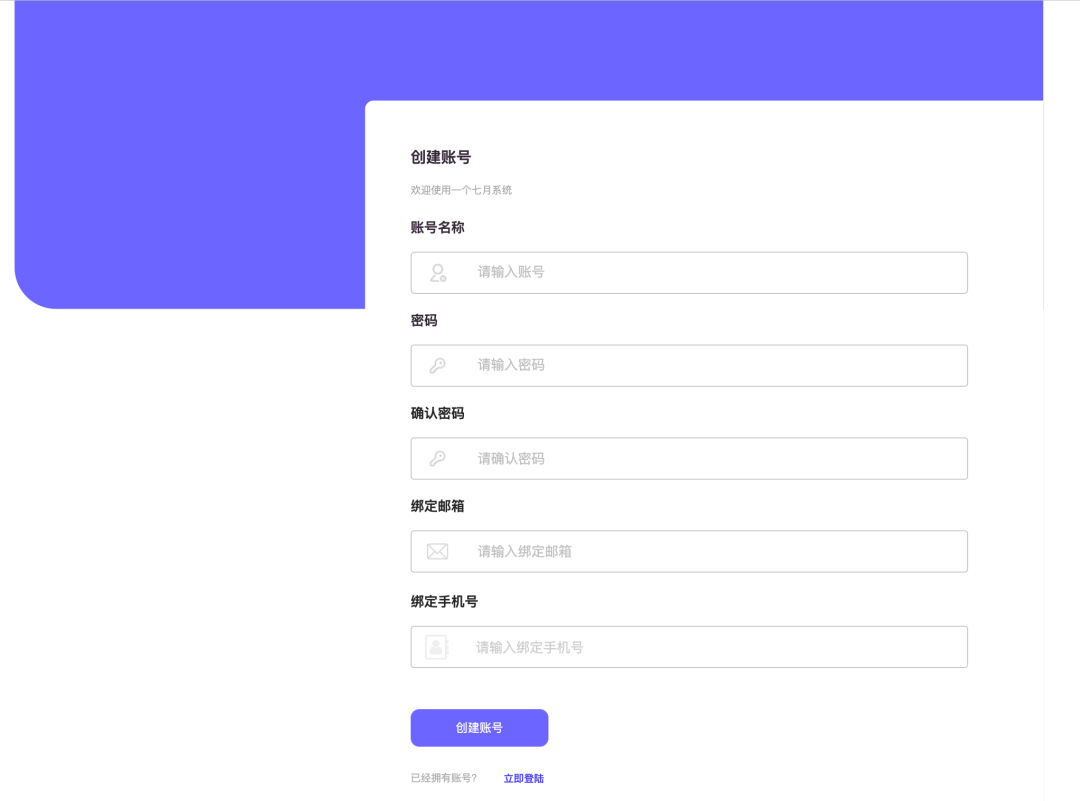
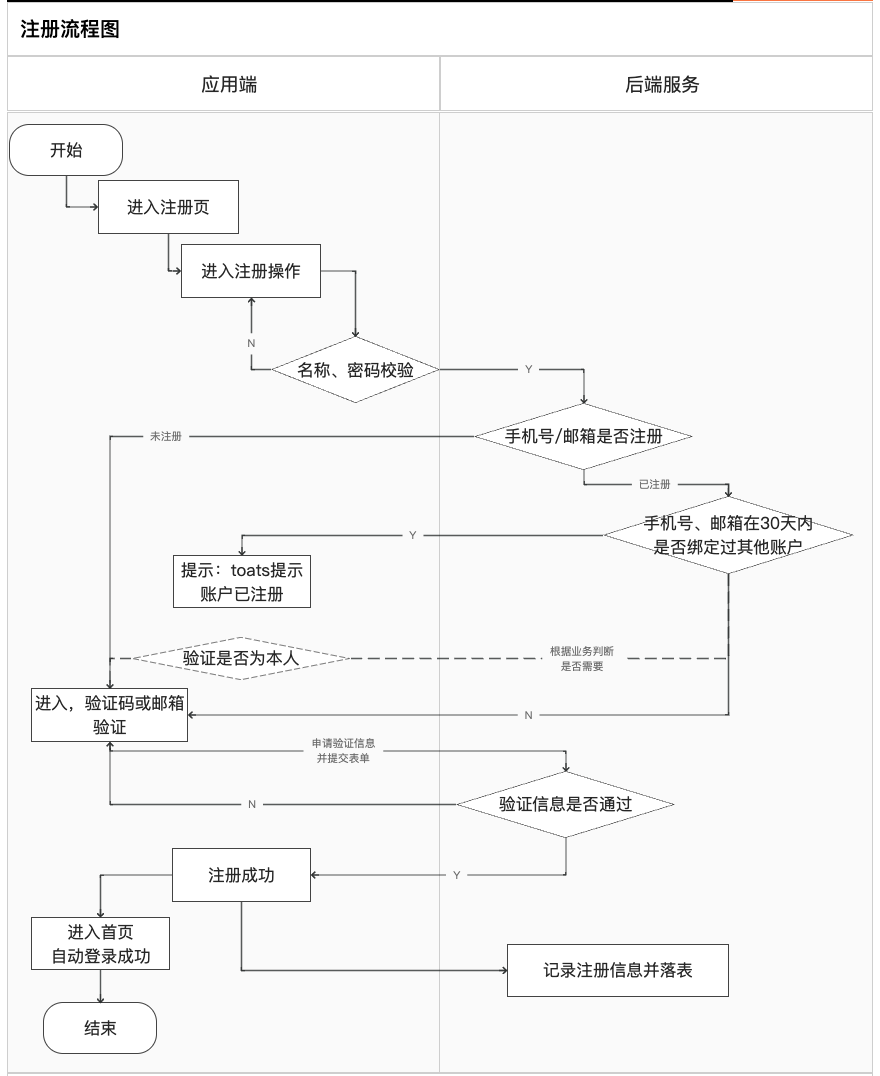
Registration flow chart:
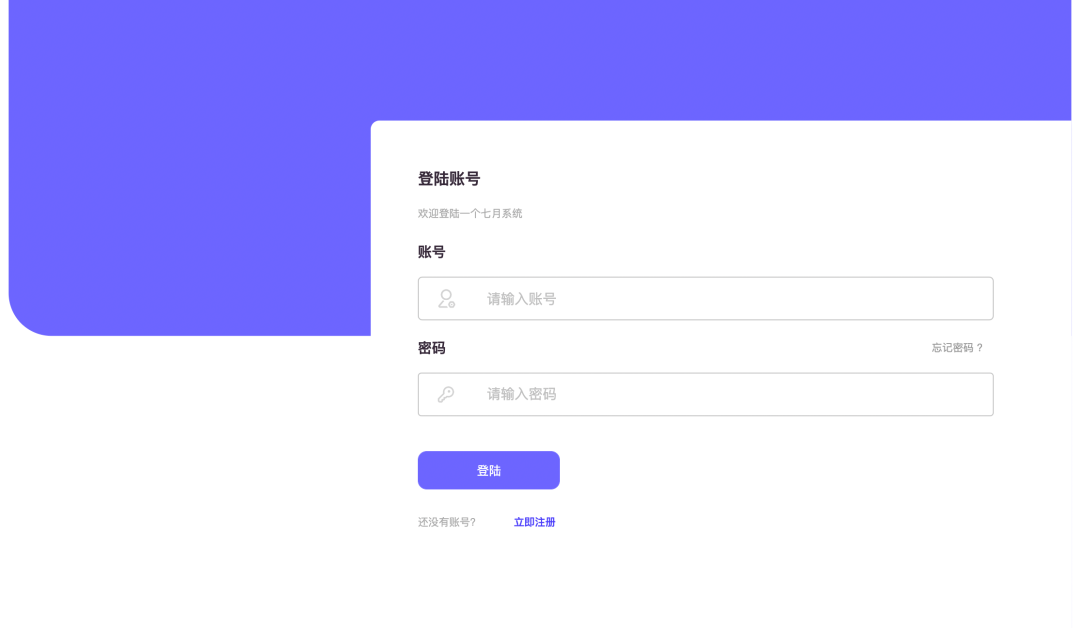
Login module: Login and registration are a coherent process, so the logic needs to be smooth and easy to operate and automatically jump during the connection process.
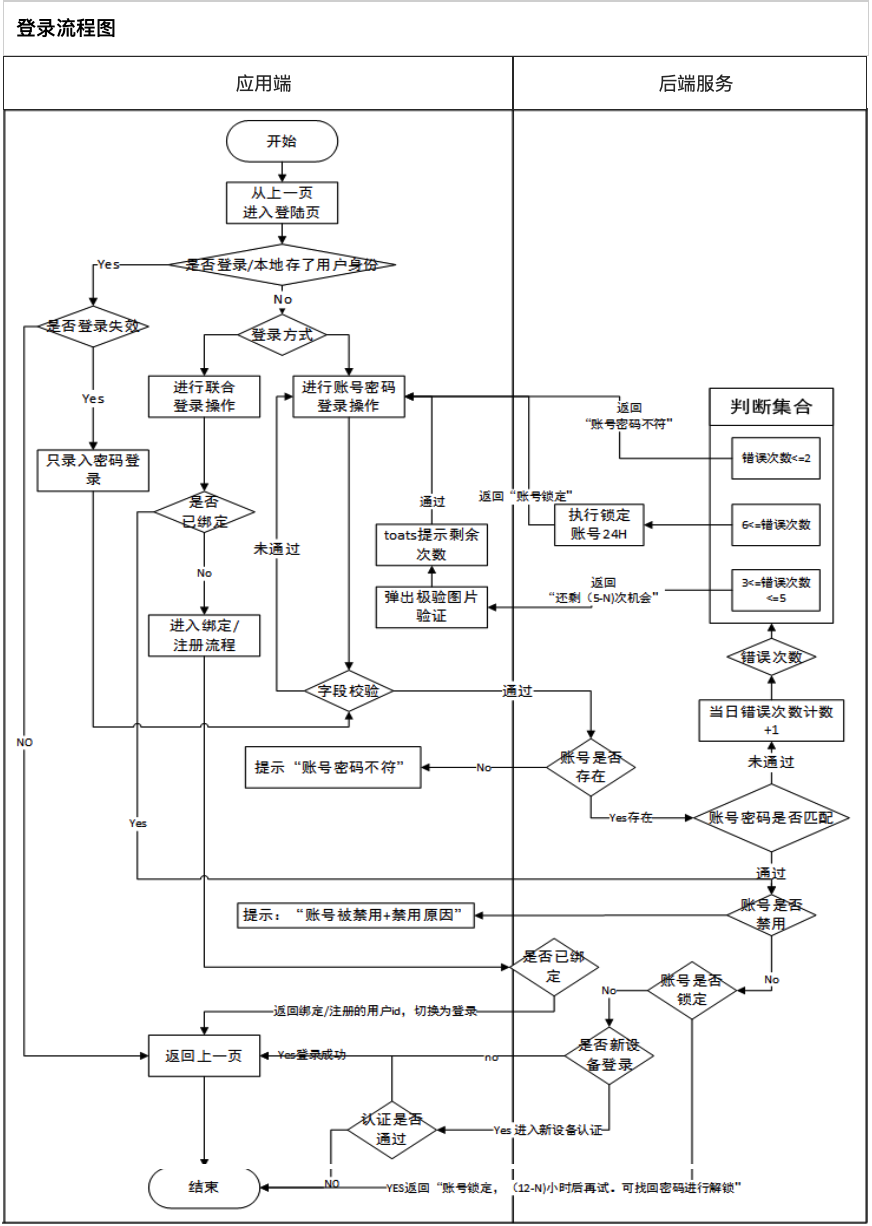
Login flow chart:
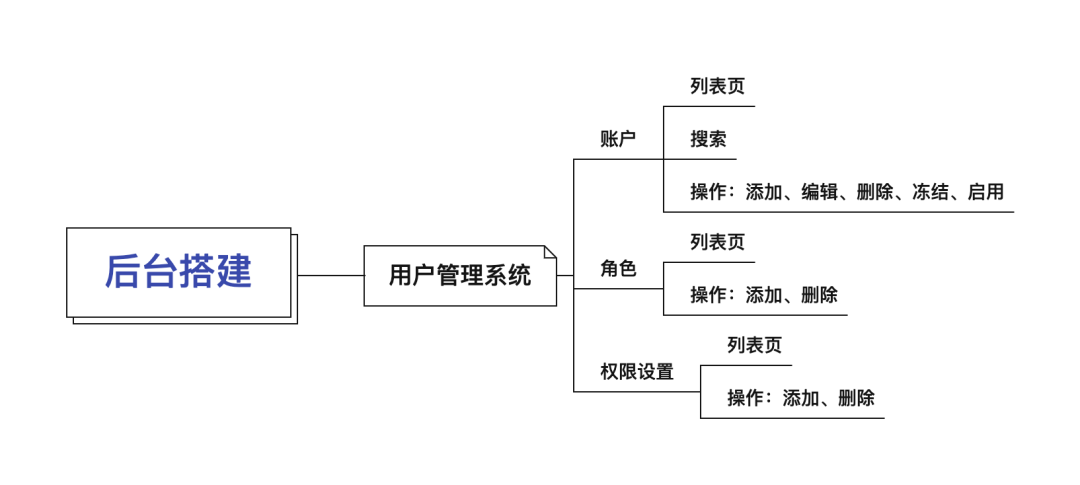
02 User management (roles, accounts and permissions) module
The user authority management system of the background product can be roughly divided into three modules: account, role and authority management;
Accounts are assigned roles, and roles are configured with permissions. An account can be assigned multiple roles, and a role can only have its corresponding permission restrictions; in this way, it is possible to avoid the situation where the coupling information is redundant.
1. Role Management
A role refers to the induction of a certain group of people with the same identity, but the role needs to have an inheritance and constraint relationship to show that the role has a distinction between superiors and subordinates.
In this module, we need to define different role names and corresponding role information according to the business. If the business permits, try not to set too many roles. If there are too many roles, you must clarify with the permissions granted by the roles. for example:
Inheritance & constraint relationship:
Roles need to satisfy the inheritance relationship to indicate the role's subordinate relationship. In this part, you can refer to the root leaf node of the decision tree to distinguish the parent-child relationship of the role.
Roles need to satisfy the existence of a constraint relationship, which shows that the differences between roles correspond to the differences in the permissions and services under the roles.
Prerequisite role: In this case, when the system is huge, whether the user needs to satisfy the sub-roles under the role when adding a role and permissions with a higher scope of influence;
Mutually exclusive roles: a user can only be assigned one of mutually exclusive role groups, for example, marketing specialist, operation personnel, and system management can be set as mutually exclusive groups, and a user can only belong to one of these groups; setting mutually exclusive groups is in the System and business security considerations, for example, if a user's role is the system administrator's role, if the permissions granted to the operation role are accidentally clicked, the online business may be affected. However, the specific mutually exclusive roles and corresponding permission settings need to be set according to the actual situation of the business. Mutual exclusion at runtime: A user can have multiple roles, but these two roles cannot be activated at the same time in actual business operations to achieve dynamic separation of duties.
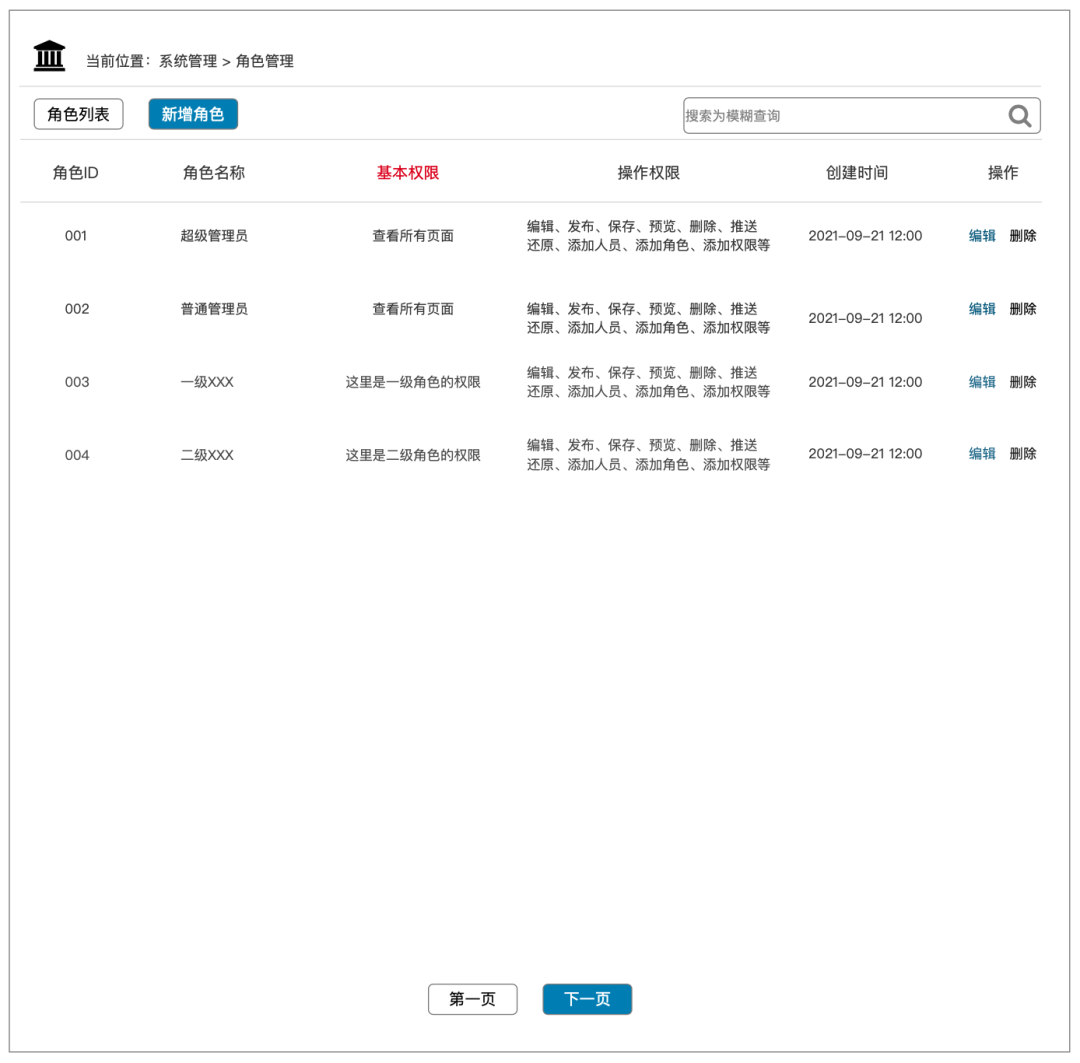
Role list page:
The role list page is more convenient for the system administrator to verify the corresponding roles and users. Besides the basic functions, you can add, delete, modify and check the roles. You can also consider whether to add custom role functions according to the actual business situation, so as to consider the scalability of the system. .
List page = display page + entry for some necessary operations; main information such as role ID, role name, permissions, creation time, and operations can be displayed on the list page; only a part can be displayed when there are many basic permissions and operation permissions , and the rest can be in the form of [display all when the cursor moves to this field or add a view operation under the operation field to perform a details page]
As shown below:
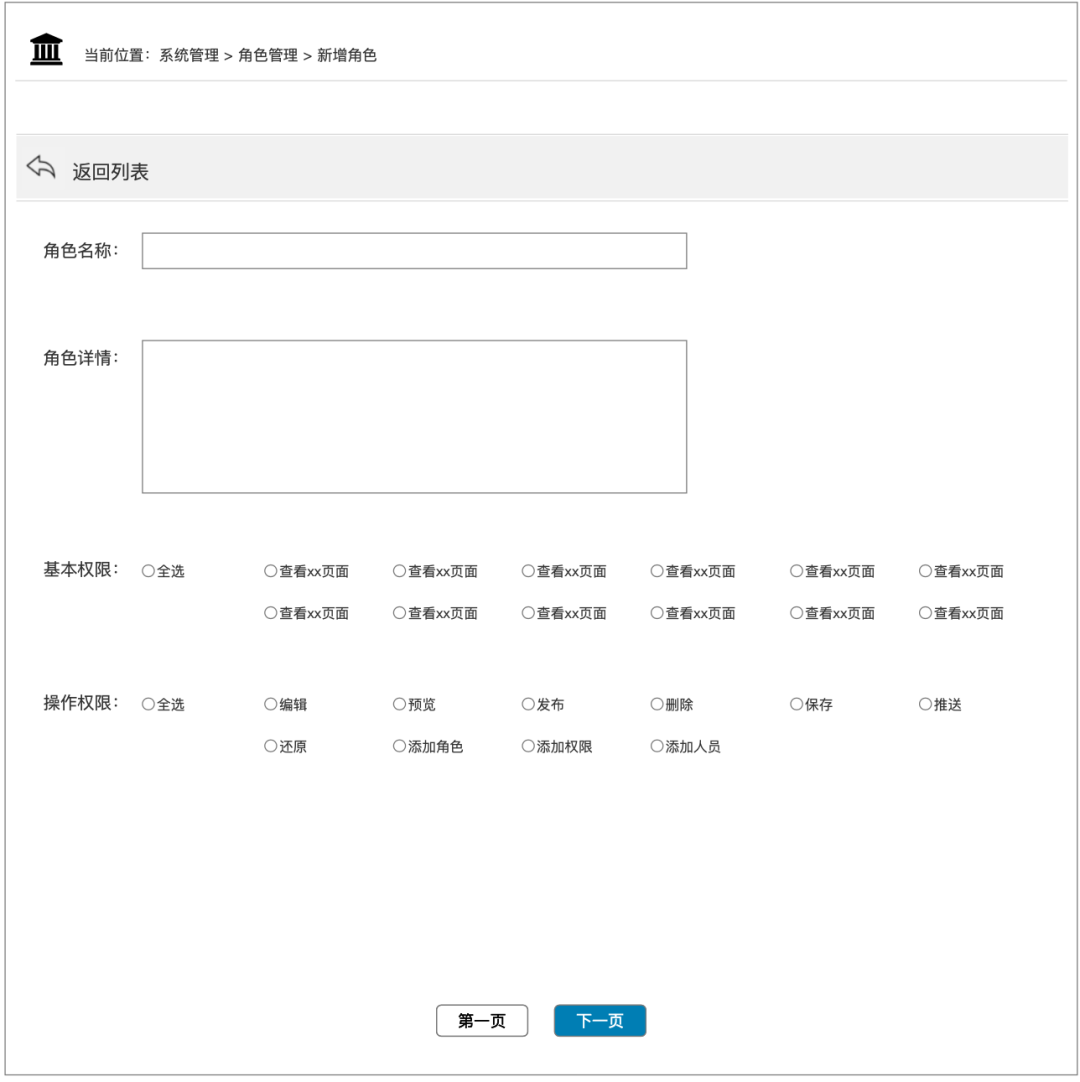
New role page:
Both "add role" and "edit role" give the corresponding definition to the role, but editing the role needs to consider the current use of the role, whether it already exists and runs in the existing system, and whether the modification will affect the line on the system. The authority given to the new role is to consider the scalability of the system from the perspective of long-term value. When adding business modules and permissions in the iterative business, there is no need to access new development, but at the same time, it is necessary to do a good job at the beginning. definition and new rules, so it is not recommended to provide the function of adding new roles during the initial construction period.
When the role has fewer permissions, it can be selected in the form of [drop-down box]; when it has more permissions, it can be selected in the form of [Privilege List].
2. Rights Management
The authority management part is the most logical and has the most extensive impact on the overall system. It is necessary to match the role with the corresponding authority in advance, and sort out the name, description, nature (basic/operation) and other information of the authority. Here It should be noted that you cannot give yourself permission. Although it will cause trouble in operation under certain circumstances, it will greatly reduce insecurity.
Related permission model can refer to RBAC: role-based access control
RBAC definition: When an operation satisfies a and b at the same time, the operation is allowed: a. Specify which resources the role can perform and which operations; b. Specify which roles the subject has
The idea of RBAC comes from the corporate structure in the real world.
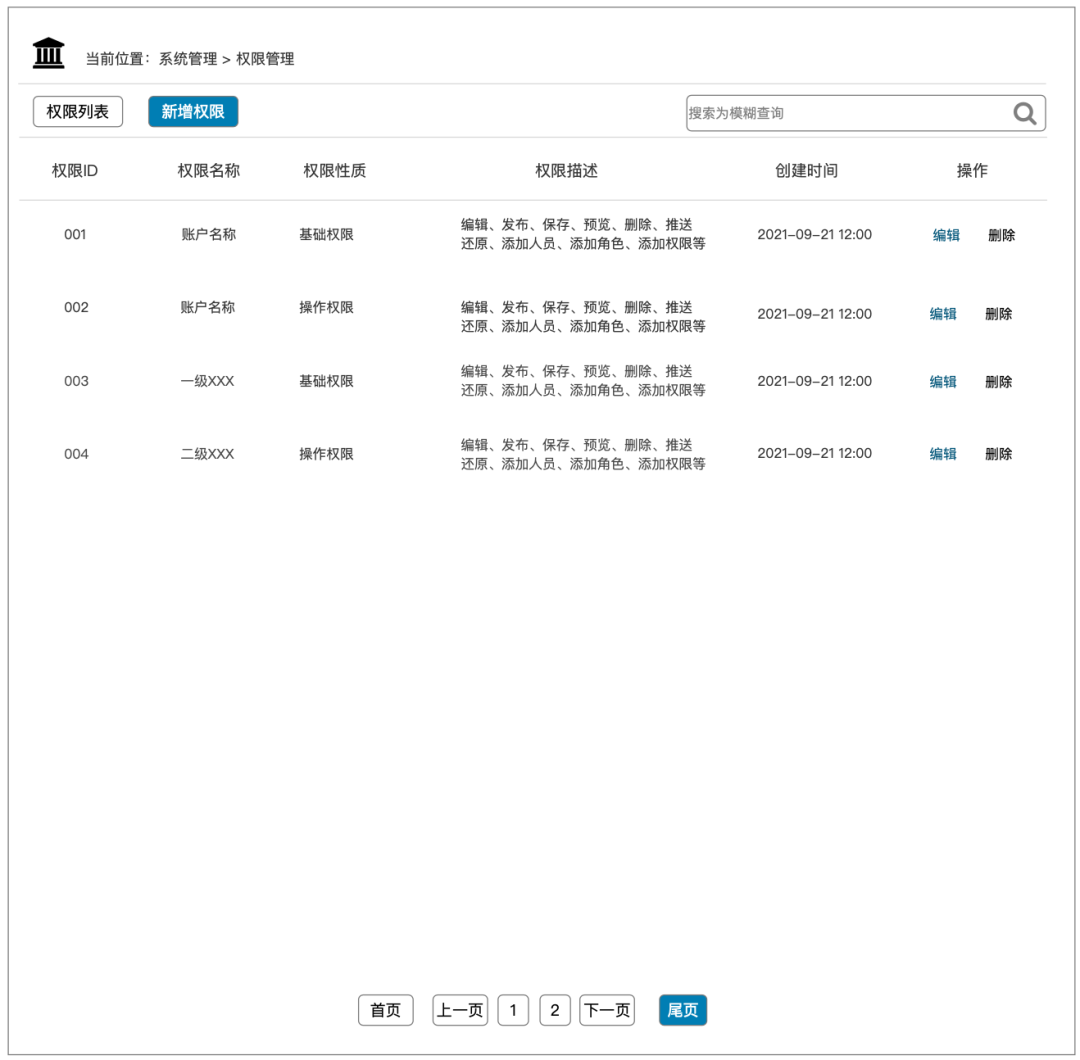
Permission list page:
A good permission system needs to be scalable, efficient and easy to maintain, hierarchical and traceable.
Before sorting out permissions, reach an agreement with business and development students to determine which permissions are of the same type and can be aggregated in the same group, and which business or function permissions must be set separately.
The [permission nature] part is based on the actual setting needs of the business situation and specifies the settings of roles and [view], [operation] and other permissions. In the logic as a whole, it needs to satisfy the correspondence between roles and permissions, so as to realize the business page viewing corresponding to different roles. Different operations of functions such as , editing, and deleting, and even functions such as viewing, editing, and deleting of certain elements on the same page can be set separately according to the corresponding relationship between roles and permissions.
The permission setting can also consider the parent-child relationship
3. Account Management
This function module is closely related to the function module of the registered account. Account management is a module that associates users with roles. One user corresponds to one account, and one account can correspond to different roles. Different roles are assigned different permissions to achieve [one account corresponds to multiple permissions] account management. In this module, corresponding fields need to be set to manage internal personnel information, which is also the most commonly used function by administrators.
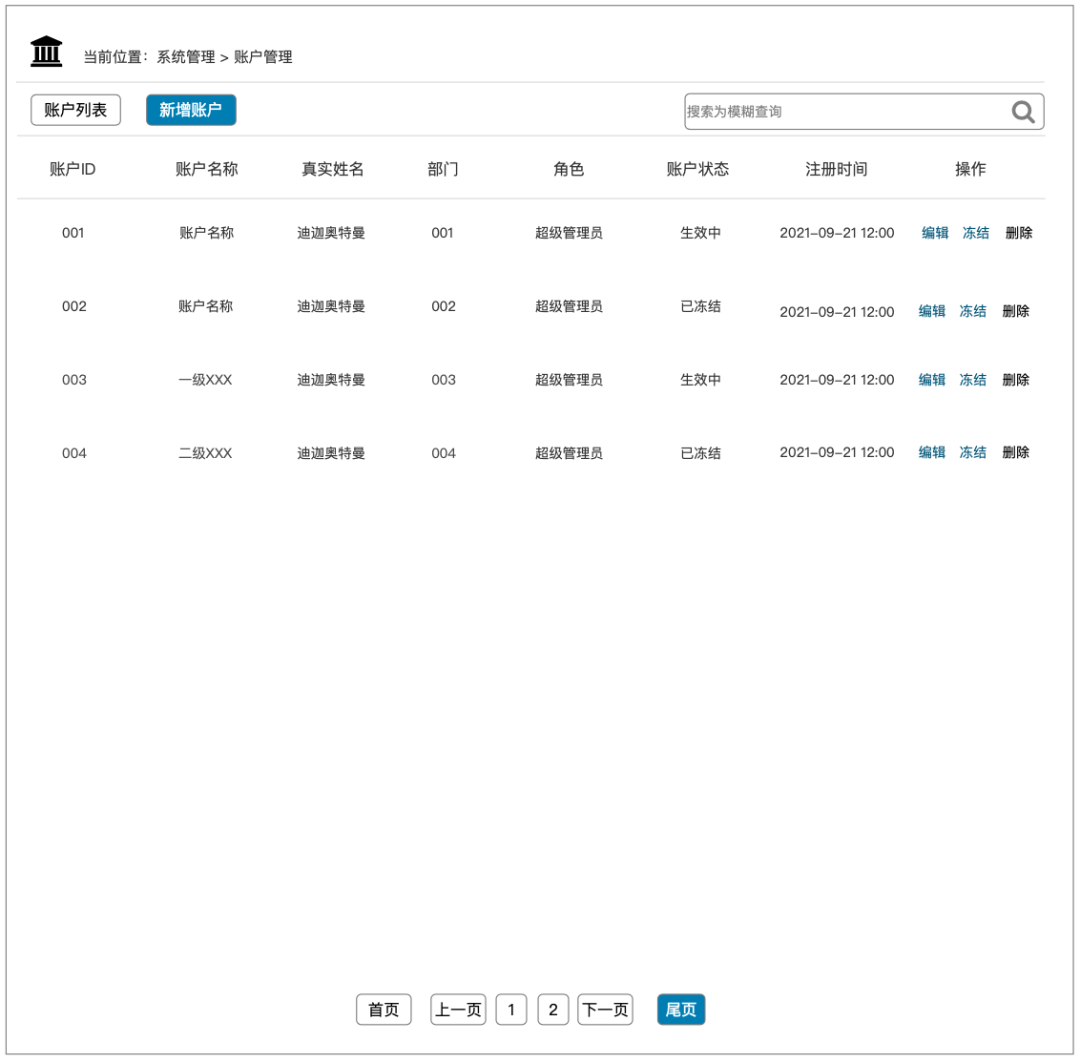
Account list page:
List page = display page + entry for some necessary operations. The main function of the list page is to allow users to clearly query the necessary information, such as user ID, user name, department, role, account status, registration time and operations (first in the operation It should have the basic operation functions of "edit" and "delete");
On the other hand, some accounts may be frozen (this situation is relatively common in some business scenarios with fewer levels of user management accounts), and based on this situation, it is necessary to add the functions of "freeze" and "enable" .
In addition, to facilitate subsequent data analysis and operation records, some simple data burying points can be done on the front end, such as the latest login time, login times, etc.
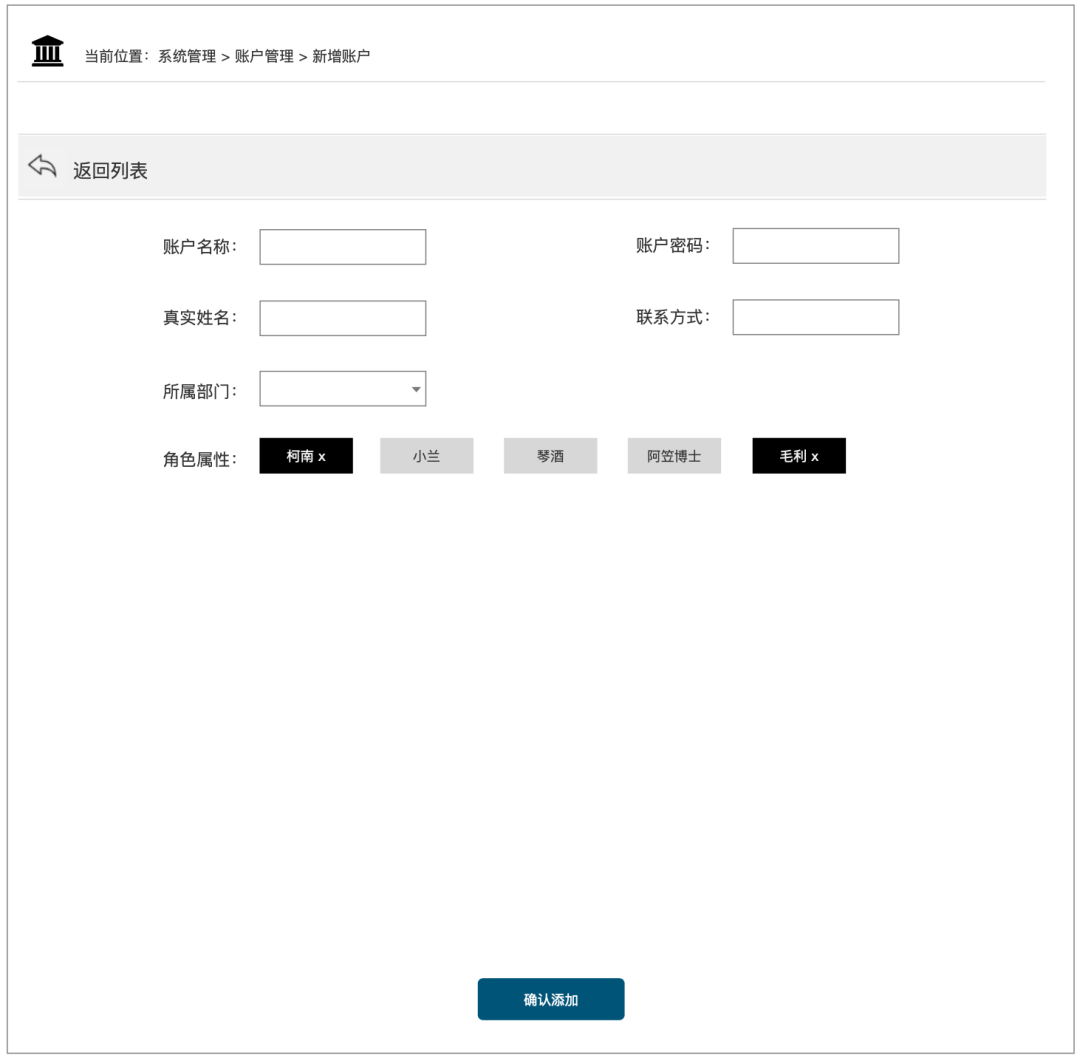
New account page:
When the "Add Account" button is clicked, the current page can jump to the page for filling in the account information. The fields on the [Add Account] page should list as much information as possible for the account and determine the corresponding account information. character of. Since the role itself has the nature of permissions, there is no need to match permissions. As shown below:
Summarize
The three modules of user management introduced above are mainly designed for the background system, and users are also internal personnel of the enterprise. A clear user management system can enhance the coherence of users in using the system and the stability of the business. The clear setting of permissions can enhance the security of the system. Too many roles and permissions will not only increase the pressure of iteration but also have permissions redundancy and waste. Therefore, at the beginning of product design, we must follow the MVP principle and take small steps.
Finally, I established communication groups in major cities. Those who want to join the group can add WeChat: chanpin628 and I will pull you into the group.

Recommended video number
Pay attention to the WeChat public account: Product Liu can receive a big gift package.

··················END··················

Today's report: HCR Huichen released " Research on Generative AI Cognition and Usage 2023 " , download the report and go to the official account: Hard Core Liu Da background reply " Generative AI Cognition ", you can download the complete PDF file.
Declaration: The copyright of the report belongs to HCR Huichen All, this is only for sharing and learning. If there is any infringement, please contact the editor to delete it.
RECOMMEND
recommended reading
B-end product manager workflow review
Interview one-on-one counseling
How to use and build user portraits and user tags

Click "Read the original text"
View more dry goods