Introduction
Goby uses a new generation of network security technology to achieve rapid security emergency by establishing a complete asset database for the target.
What are the advantages of Goby?
The richest device rule set
Goby presets more than 100,000 rule recognition engines, which can automatically identify and classify hardware devices and software business systems, and comprehensively analyze the business systems existing in the network. Currently supports more than 100,000 devices and business systems. Hardware coverage: network equipment, Internet of Things equipment, network security products, office equipment, etc. Software coverage: CRM, CMS, EMAIL, OA system, etc.
The most lightweight protocol identification
Goby presets more than 200 protocol identification engines, covering network protocols, database protocols, IoT protocols, ICS protocols, etc., and quickly analyzes the protocol information corresponding to the port by sending packets very lightweight. The speed is fast and the impact on the target device is small.
Port grouping based on rich attack and defense experience
Our security designers have summed up port grouping in different scenarios through front-line security practices to ensure the most efficient result output. It is impossible for penetration testers to perform full-coverage scanning of ports 1-65535 on a large network, and it is particularly important to determine port groups. At present, we have screened more than 300 ports for scanning to ensure the highest input-output ratio.
Based on the vulnerability framework updated daily by the community,
Goby presets the most effective vulnerability engine, covering the most serious vulnerabilities such as Weblogic and Tomcat. A large amount of vulnerability information is generated from the Internet (such as CVE) every day, and we screen the vulnerabilities that will be used in real attacks for daily updates. Goby also provides a customizable vulnerability inspection framework, mobilizing a large number of security practitioners on the Internet to contribute POCs to ensure continuous emergency response capabilities. At the same time, we believe that the actual effect-based inspection will be more valuable than the version-based comparison method.
The most comprehensive preset password checking
Almost any device will have a default account or even a backdoor account, and the traditional brute force cracking method is not the best effect. Goby presets the preset account information of more than 1,000 devices for targeted checks to ensure the accuracy and efficiency of risk identification. Of course, Goby also has built-in brute force tests for custom dictionaries of various protocols.
Install
Goby is divided into free version and paid version, you can download it according to your own situation, and download it from the official website.
After downloading, just double-click to run it.
Then register on the official website, log in and copy the corresponding key, and log in in the software.
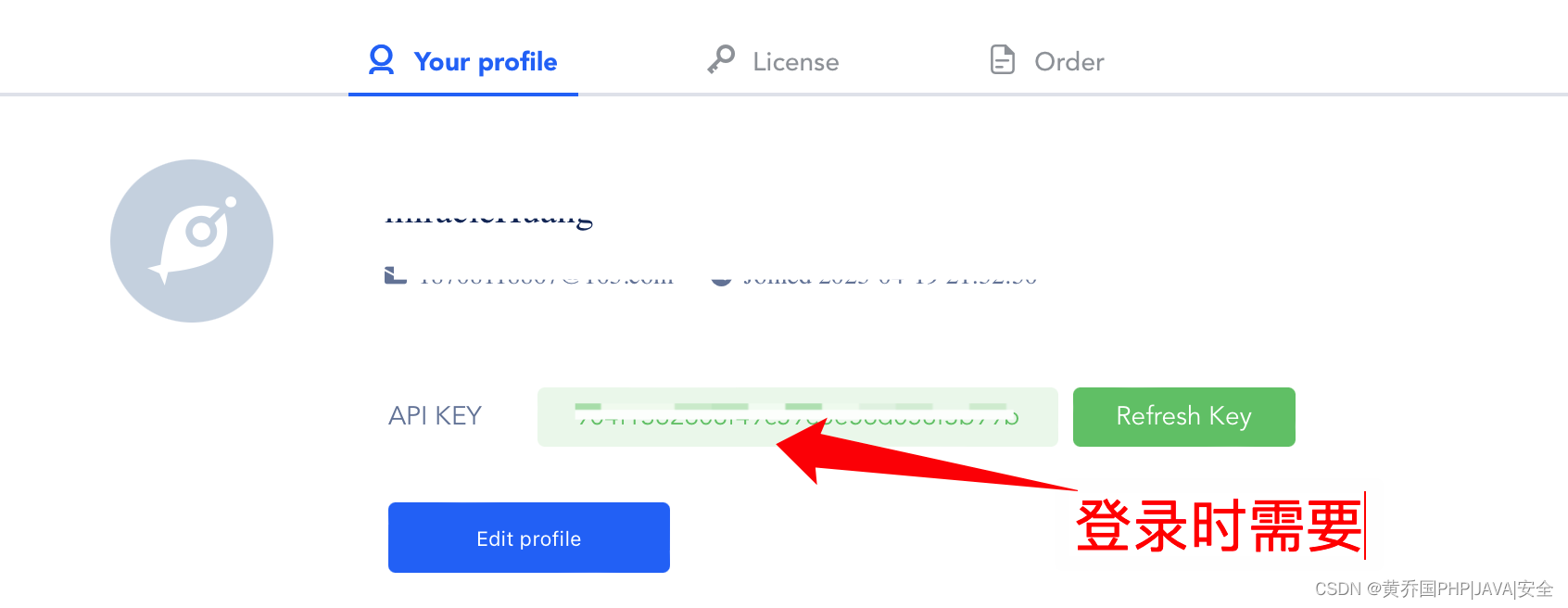
After successful login:
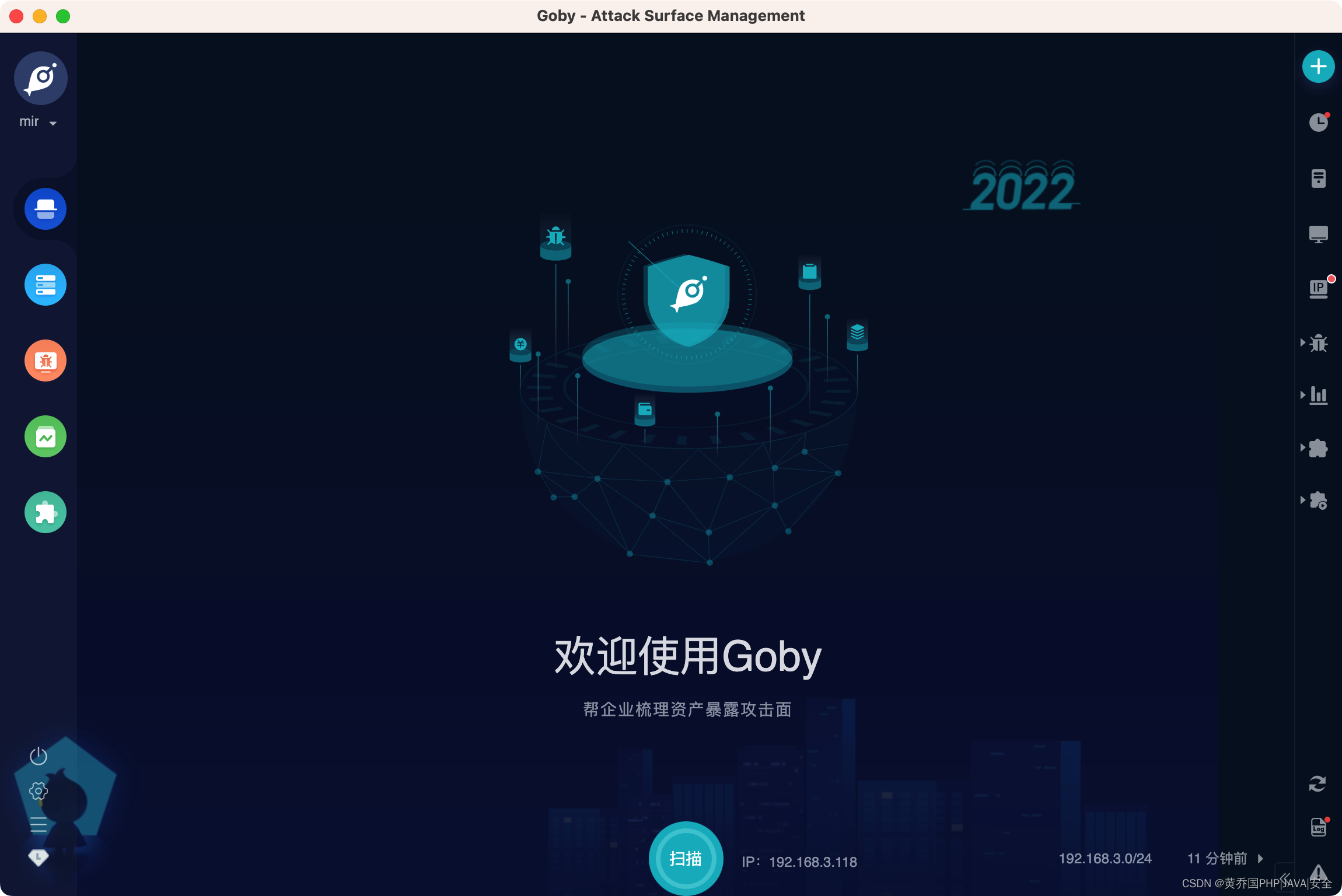
Function introduction
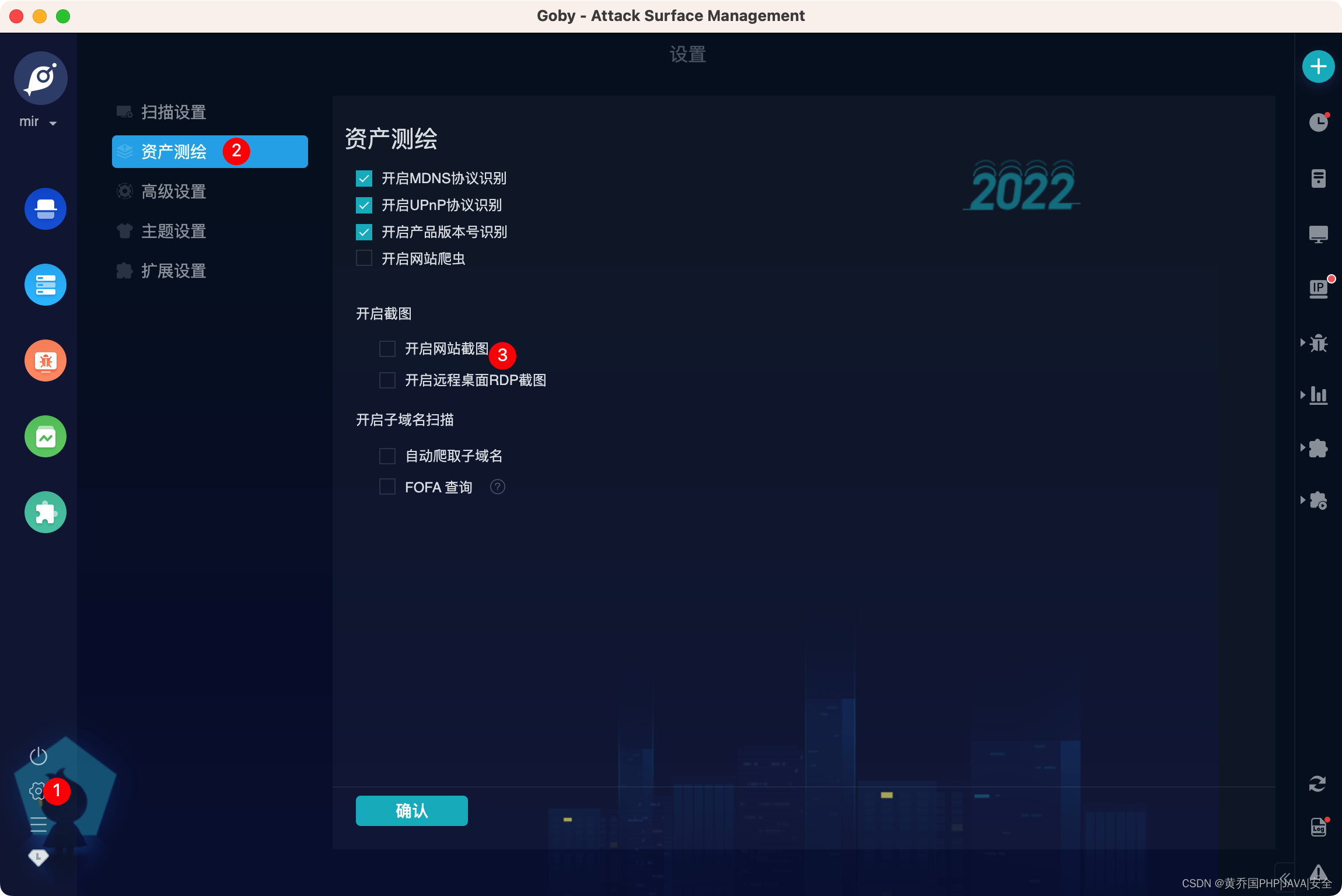
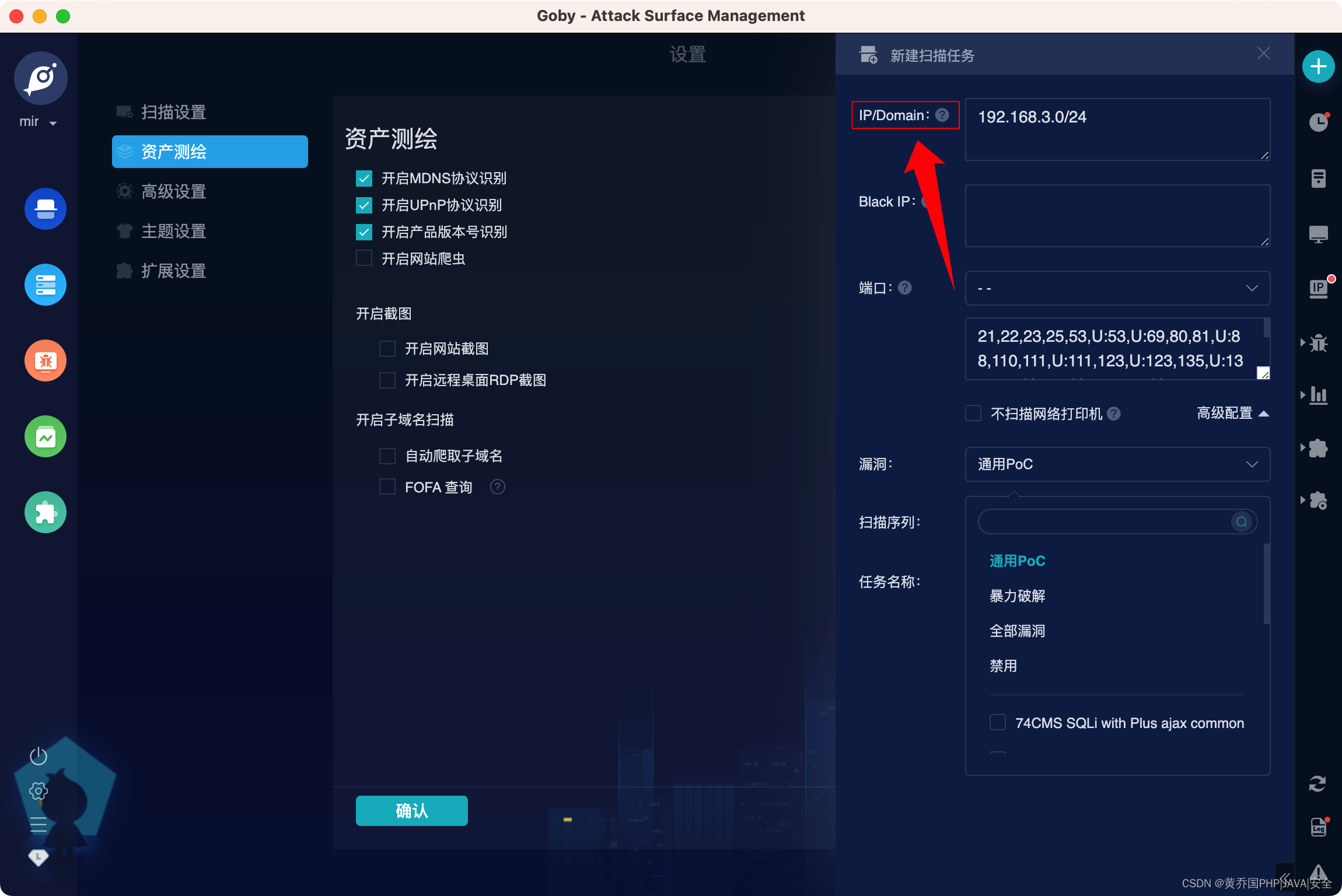
asset scan
Automatically detect the surviving IP in the current network space
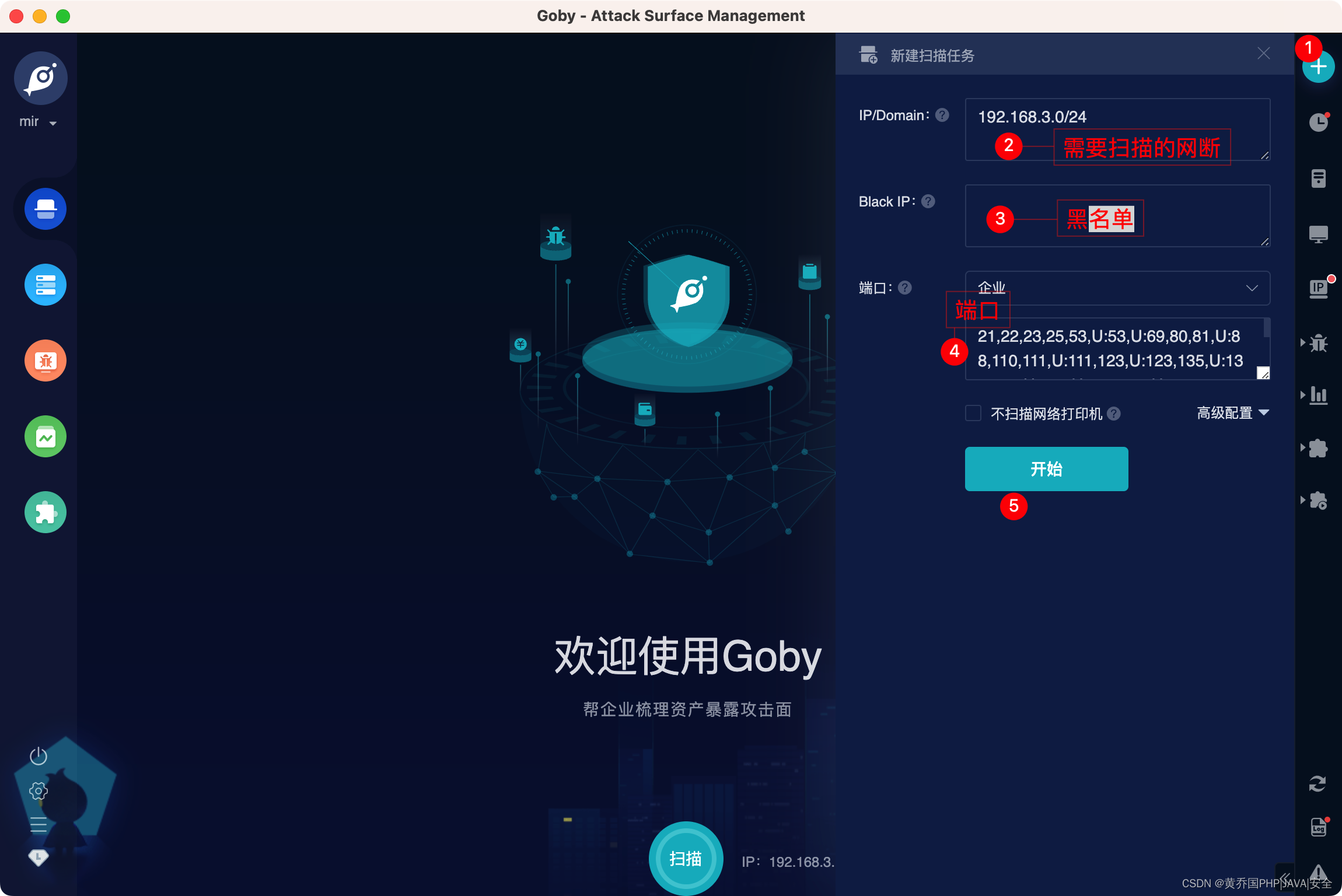 and start scanning:
and start scanning:
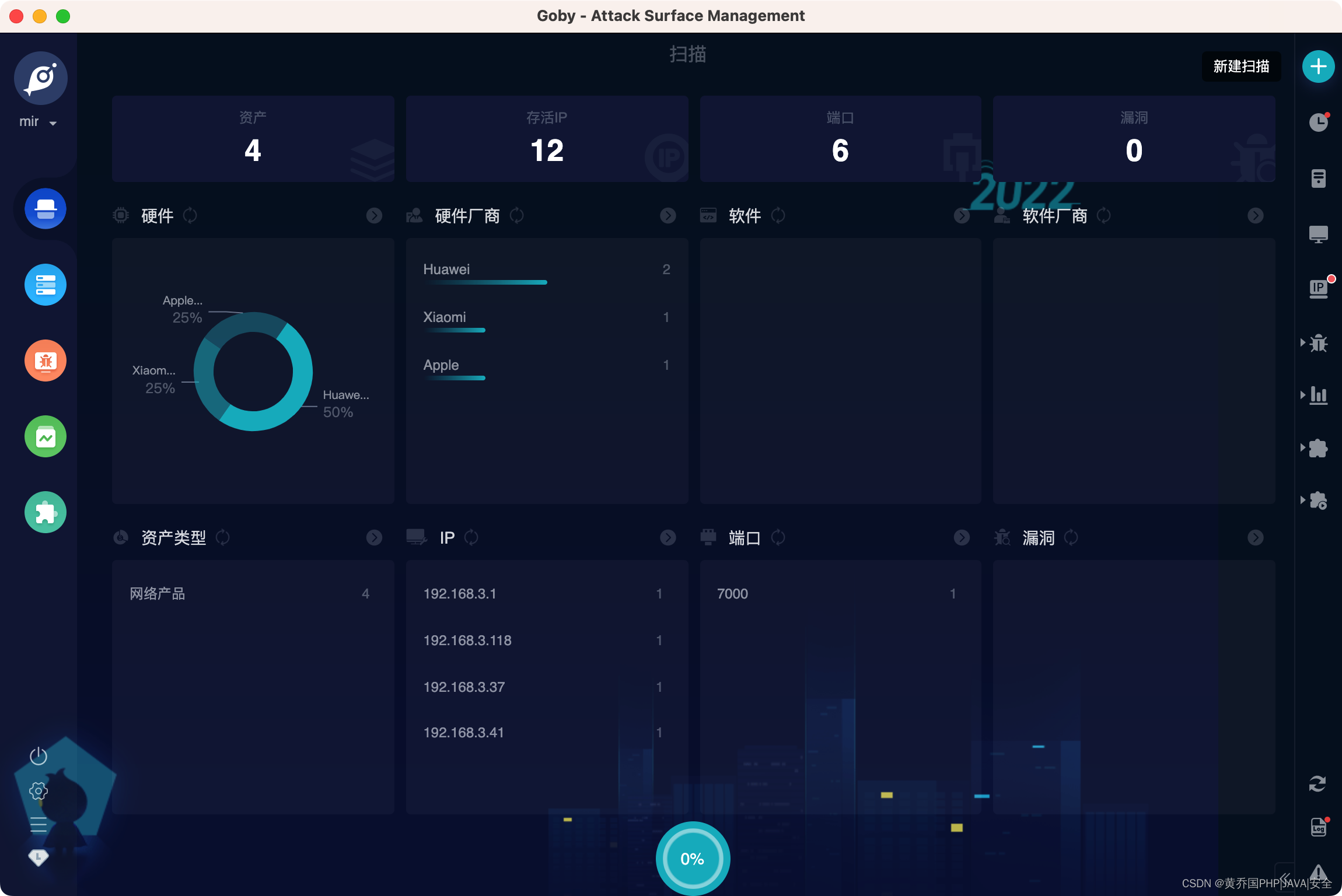
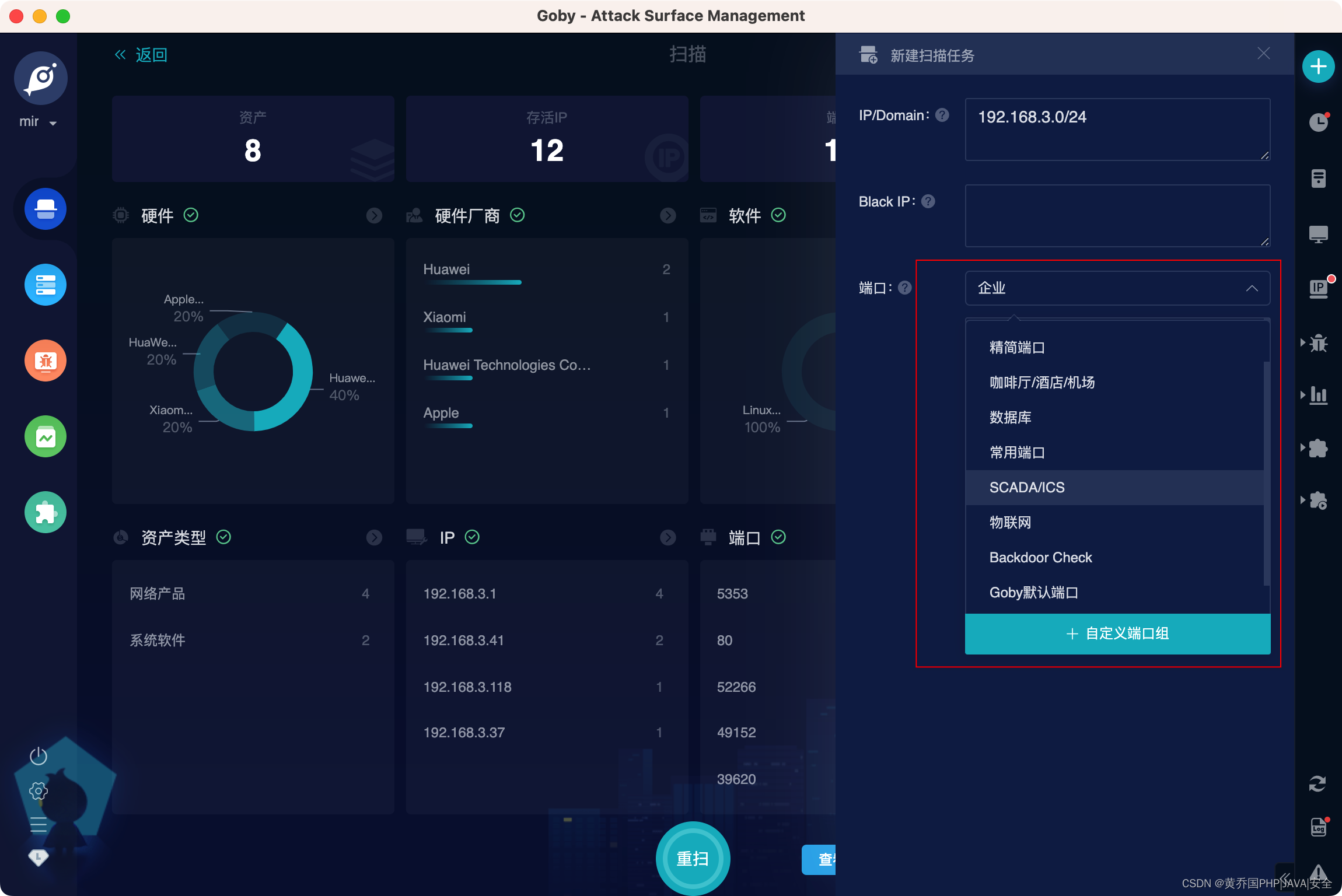
port scan
Covers nearly 300 mainstream ports and supports port grouping in different scenarios to ensure the most efficient output of results;
protocol identification
More than 200 protocol identification engines are preset, covering common network protocols, database protocols, IoT protocols, ICS protocols, etc., and can quickly analyze the protocol information corresponding to the port through very lightweight packet sending;
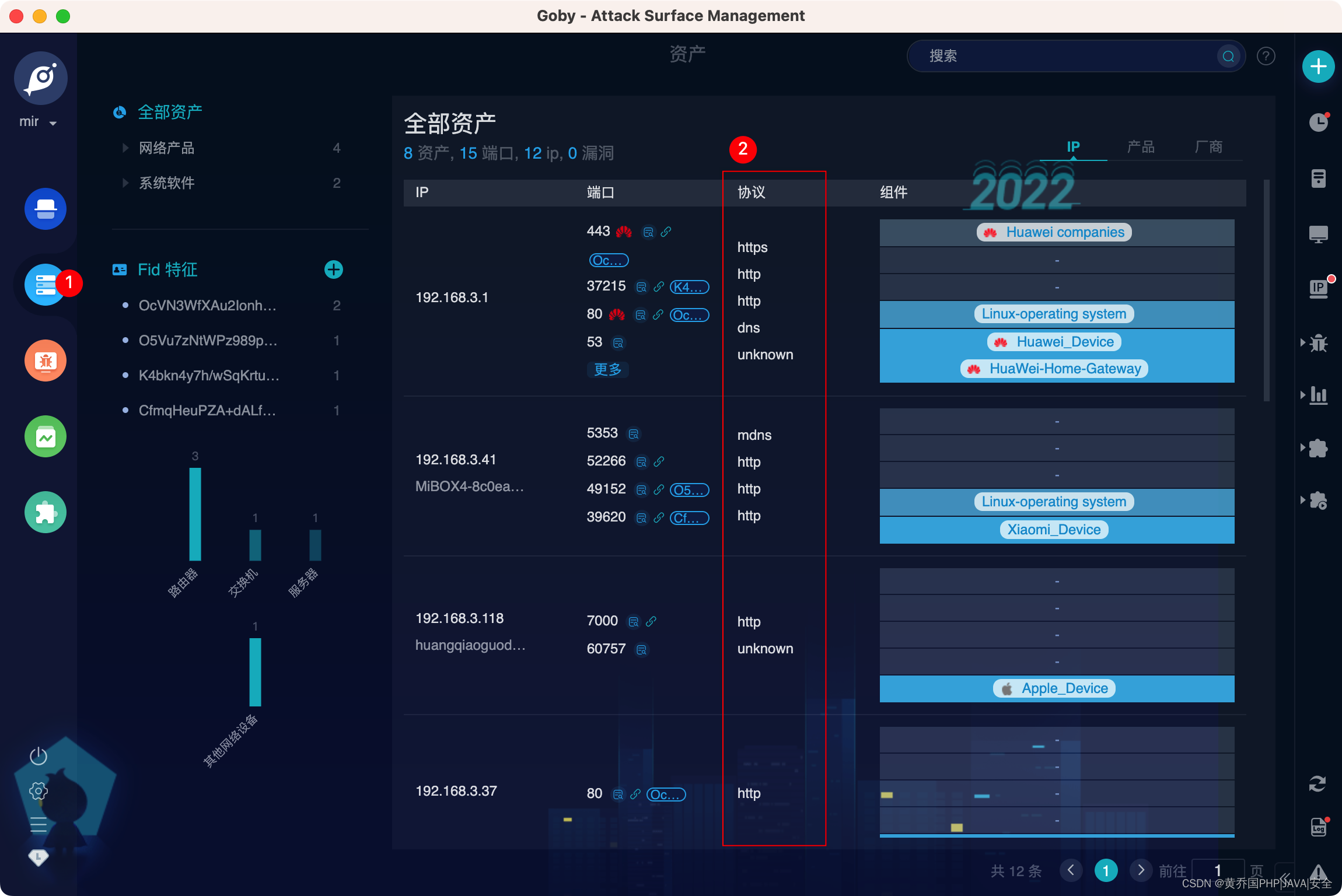
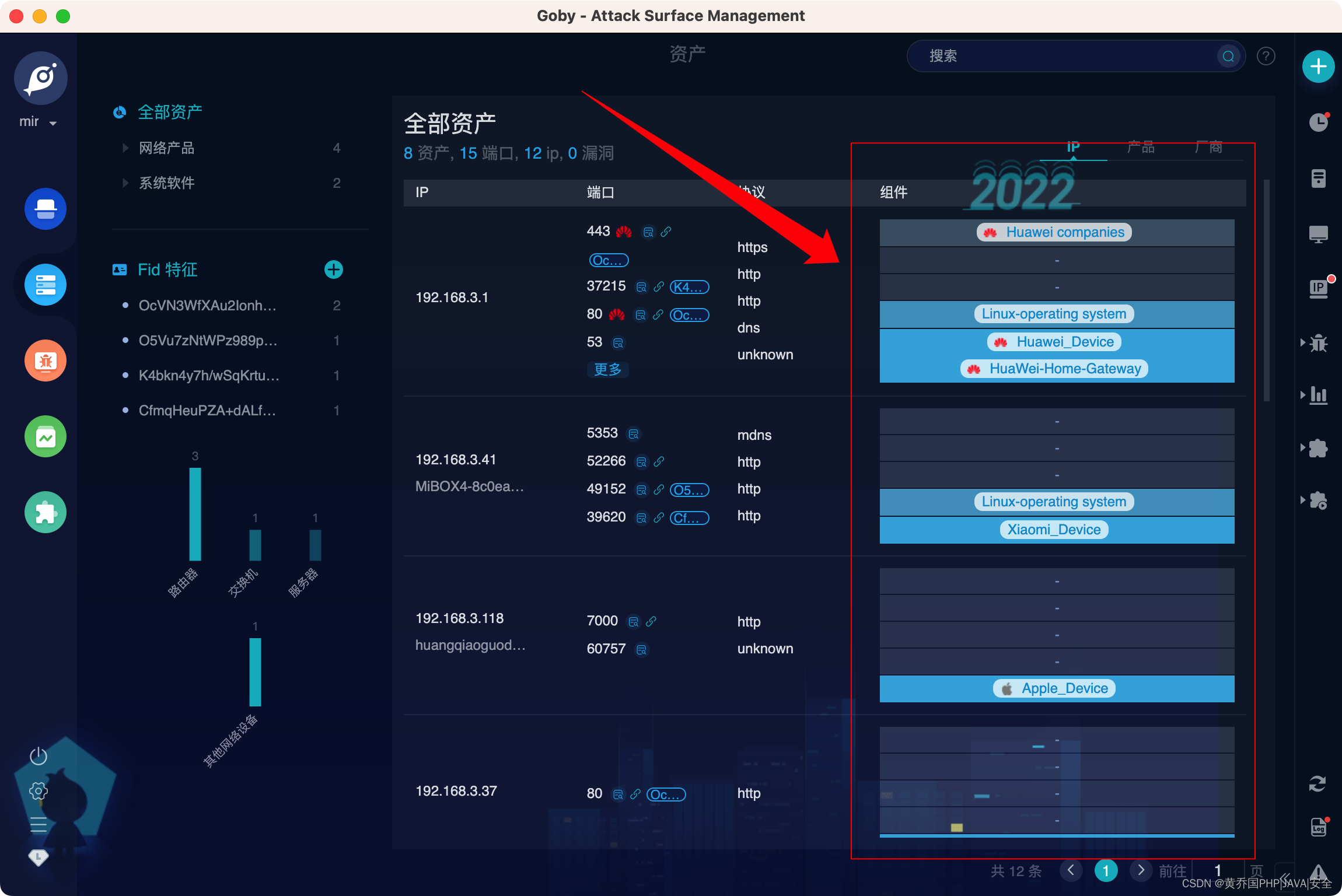
product identification
More than 100,000 rule recognition engines are preset to automatically identify and classify hardware devices and software business systems, and comprehensively analyze business systems existing in the network;
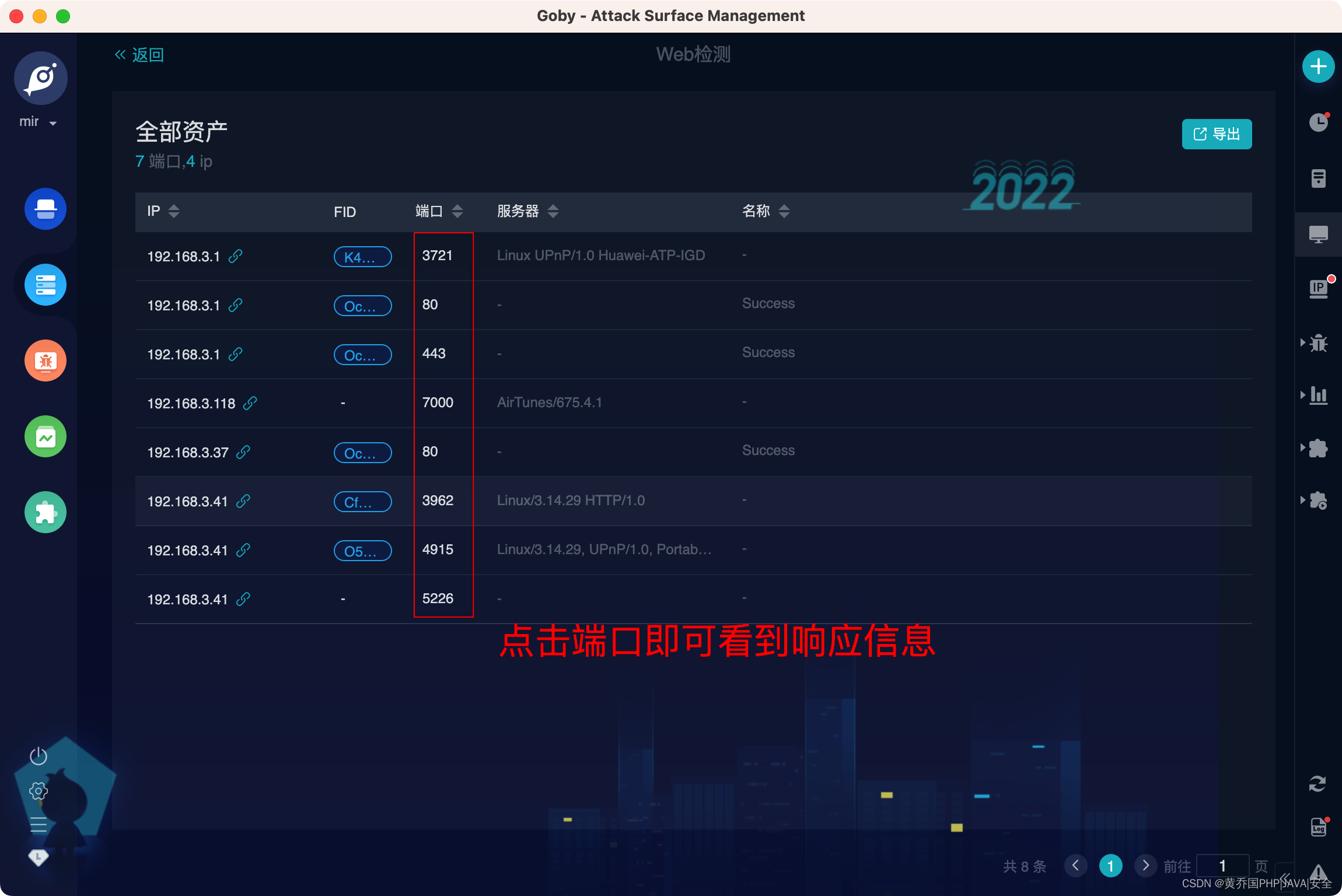
Web Finder
Important information needed to support website penetration: including IP, port, server, title, etc.;

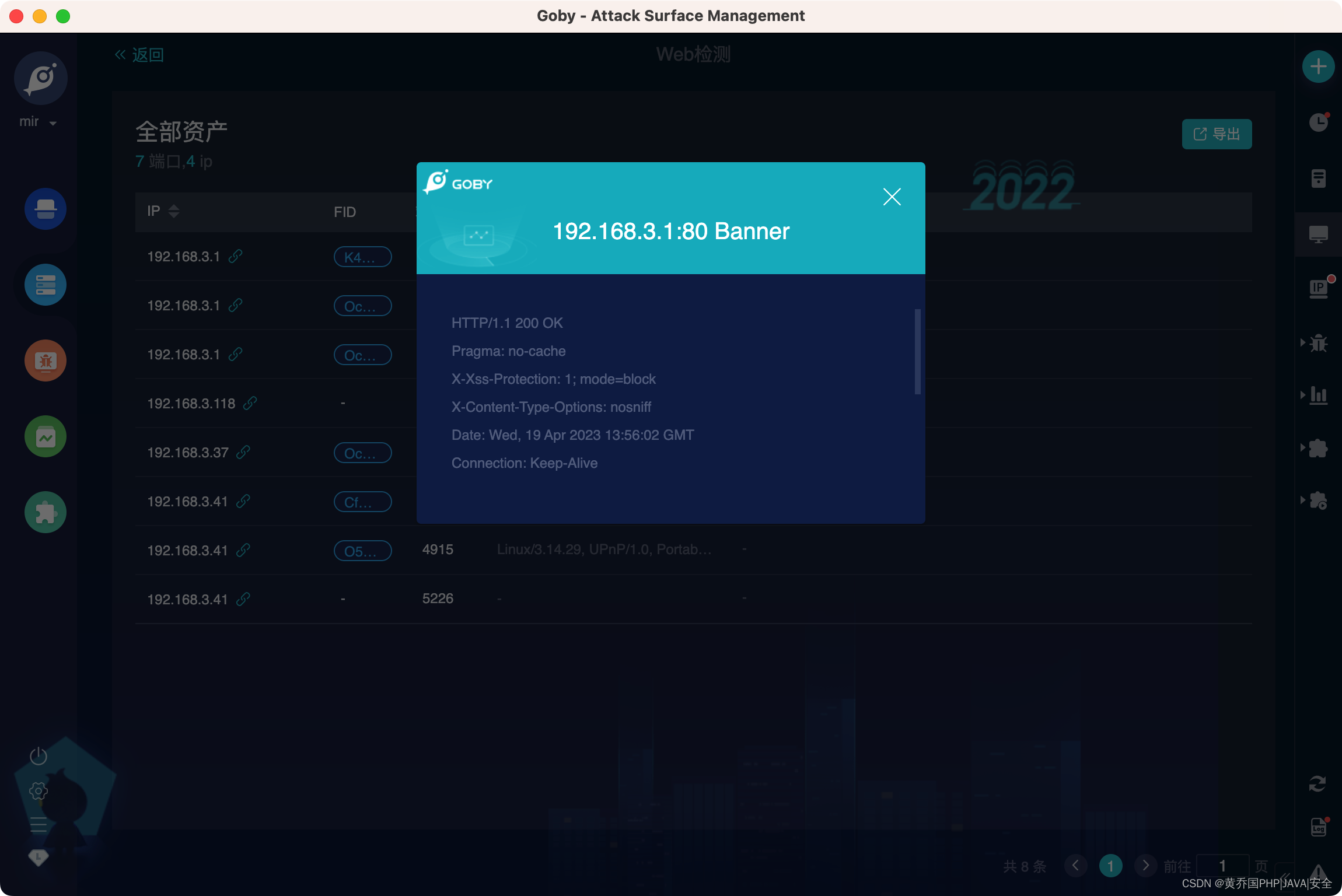
vulnerability scan
The vulnerability engine with the most attacking effect is preset, covering the most serious vulnerabilities such as Weblogic and Tomcat;
website screenshot
Supports obtaining website screenshots on the server, and you can see more screenshots on the details page.
proxy scan
Through the socket5 proxy, quickly enter the intranet and enable intranet penetration.
Note: Pcap and socket modes are supported, please switch dynamically according to different occasions.
pcap mode: supports protocol identification and vulnerability scanning, does not support port scanning;
Socket mode: Supports port scanning protocol identification and vulnerability scanning, but the scanning speed is slow.
domain scan
Customize the resolution of domain names to IPs, and automatically crawl sub-domain names. Including AXFR detection, secondary domain name dictionary blasting, associated domain name query.
Report
The report function is also quite powerful:
the above is the basic usage of Goby, please check the official website for more usage!