Significance of PHP code audit
What is code auditing
What is code auditing? Code audit is to obtain the source code of the target. This target can be a website or a mobile app. As long as we get the source code of the target, we can dig out the loopholes of the target system. Code audit refers to the source code. Checking and finding bugs in the code is a technology that requires many skills, including mastery of programming, understanding of the principles of bug formation, and familiarity with systems and middleware. Code auditing is a necessary basic capability for enterprise security operators and security practitioners. Code auditing is needed in many scenarios, such as enterprise security operations, penetration testing, vulnerability research, etc.
The difference between black box testing and white box testing
In code auditing, the main difference between black-box testing and white-box testing is whether the source code can be obtained. Black-box testing cannot obtain the source code, but white-box testing can obtain the source code.
Should Code Auditing Be Mastered?
It is very important for penetration testers to master code auditing, because we often need to debug the payload of the target environment during penetration testing. In addition, if a source code backup package in the web directory is scanned by the directory scanning tool, usually the attacker will use the source code package to find some configuration files or sensitive information, because there are configurations such as databases and APIs in it. For those who have mastered code auditing and those who have not mastered code auditing, the results are completely different. For those who have not mastered code auditing, it may stop here. For those who have mastered code auditing, he can conduct security audits on source code packages , discover the loopholes in the code of the website, and then use the exploited loopholes to infiltrate. All in all, code auditing is an essential part of penetration testing
Programming Ability Requirements
Code audit has certain requirements on the basics of programming languages. At least you must be able to read and understand the code, understand what the code means and the logic of the code. Even if you encounter some functions that you have never seen before in the code audit, you can directly I went to Baidu to check, so as long as you have a preliminary grasp of the programming language, it should not be a problem to learn PHP code auditing
PHP code audit process
First of all, do code audit. The first method is to read through the full text method. As the most troublesome method, the full-text method is also the most comprehensive audit method, especially for large-scale projects. Reading through the full text is also the best way to understand the entire project, business logic, and the entire project. , so that more medium and high-risk vulnerabilities can be found, and the second is to check the parameters of sensitive functions, and then backtrack the variables to determine whether the variables are controllable and have not undergone strict filtering. This is a reverse tracing process, named It is the sensitive function parameter backtracking method. This method is the most effective and commonly used method. Most of the vulnerabilities are caused by improper use of functions. We can search some sensitive functions globally to see if there are unfiltered parameters. Pass it in, and you can dig out loopholes. The third method is called directional function analysis method. This method mainly conducts code audit based on the business logic of the program. Check the functions of the website, and roughly speculate that there may be functional vulnerabilities that are common to those vulnerabilities, such as initial installation of the program, file upload, database backup, Retrieve passwords, verification codes, etc. Another way is to first find out which files are accepting external parameters, and then track the variable transfer process to see if any variables are passed into high-risk functions, or whether there are code logic loopholes in the transfer process, This is a way of forward tracking, which is more comprehensive than reverse mining.
What software is required for code auditing
We often need to use the following software in the process of PHP code audit:
- PHPStorm
- SQLyog
- virtual machine
- Burpsuite
- PHPStudy
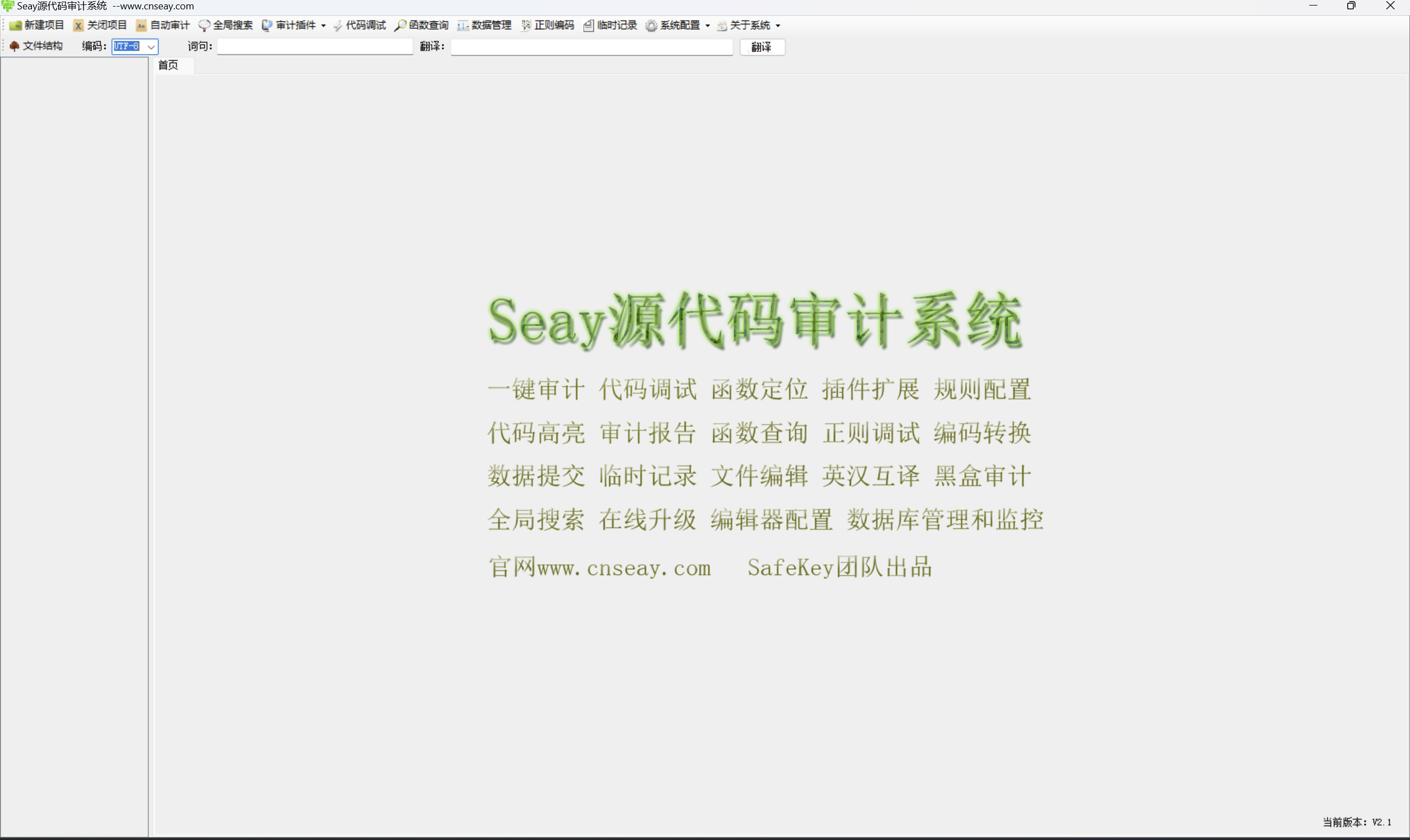
- Seay source code audit system
Code audit environment construction
The tools needed for code audit are provided here, and you can download them through the following link
链接:https://pan.baidu.com/s/1e-526vPdsDtSUoexZKZP8w?pwd=8888
提取码:8888
code audit tool
Code audit tools are a type of program that assists us in white-box testing. It can be divided into many categories, such as security audits and code normative audits. Seay source code audit is a system for PHP code security audit, mainly running on Windows system, this software can find SQL injection, code execution, command execution, file inclusion, file upload, bypass escape protection, Vulnerabilities such as denial of service, XSS cross-site, information leakage, and arbitrary URL jumping basically cover common PHP vulnerabilities. The system is configured with the following functions:
- One-click audit
- fast function positioning
- Customize multi-window search
- MySQL execution monitoring
- One-click debugging of selected code
- Document automatic query
- plug-in extension
- code highlighting
- Encoding Debug Conversion
- Database Execution Monitoring
The main interface is as shown in the figure:
Detailed PHP core configuration
The result of code execution in different environments will also be very different. It may be because of a configuration problem that a very high-risk vulnerability can be exploited, or a vulnerability you have found may be because of your configuration problem, so you cannot succeed. Construct the code for the exploit. In PHP, the configuration instructions in different versions are also different, so we need to be very familiar with the core instructions of the configuration files in each version of PHP before code audit, so as to find vulnerabilities more efficiently
The following only lists the configuration list and core configuration options that affect the security of PHP scripts:
- register_globals (global variable registration switch)
When this option is set to on, the parameters submitted by the user through GET, POST, etc. will be directly registered as global variables and the initialization value will be the value corresponding to the parameter, so that the submitted parameters can be directly entered in the script used in . register_globals is set to PHP_INI_ALL when the PHP version is less than or equal to 4.2.3. It is deprecated since PHP5.3.0 and is not recommended. This option is removed in PHP5.4.0 - allow_url_include (whether to allow the inclusion of remote files)
in the case of this configuration is on, it can directly include remote files, when there is include( var ) and var) and var) and var is controllable, you can directly control the $var variable to execute PHP code. allow_url_include is set to off by default after PHP5.2.0, and the configuration range is PHP_INI_ALL. A similar configuration is allow_url_fopen, whether the configuration allows opening remote files - magic_quotes_gpc (automatic filtering of magic quotes)
magic_quotes_gpc has made a great contribution to security, mainly when it is turned on, it can make many vulnerabilities unusable without encoding or other special bypasses, and it also allows penetration testers A very headache. When this option is set to on, backslashes will be automatically added in front of single quotes, double quotes, backslashes and empty characters in GET, POST, and COOKIE variables, but $_SERVER variables will not be filtered in PHP5 , leading to the exploitation of many vulnerabilities like client-ip and referer. Magic_quotes_gpc is deprecated after PHP5.3, and magic_quotes_gpc is canceled after PHP5.4. When the PHP version is less than 4.2.3, the configuration range is PHP_INI_ALL; when the PHP version is greater than 4.2.3, it is PHP_INI_PERDIR - magic_quotes_runtime (automatic filtering of magic quotes)
magic_quotes_runtime also automatically adds backslashes in front of single quotes, double quotes, backslashes and empty characters. The difference from magic_quotes_gpc is that the processing objects are different. magic_quotes_runtime only filters the data obtained from the database or files, and its role is also very important, because many programmers only filter the data input from the outside, but never think about it from The data acquired by the database will also have special characters, so the attacker’s method is to write the attack code into the database first, and then trigger the estimation after the program reads and uses the contaminated data. Similarly, magic_quotes_runtime is also canceled after PHP5.4, and the configuration range is PHP_INI_ALL - magic_quotes_sybase (automatic filtering of magic quotes)
The magic_quotes_sybase command is used to automatically filter special characters. When set to on, it will override the configuration of magic_quotes_gpc=on, even if gpc=on is configured, it has no effect. What this instruction has in common with gpc is that the objects to be processed are consistent, that is, GET, POST, and Cookie are all processed. The difference between them is that they are processed in different ways. magic_quotes_sybase only escapes the empty characters and programs double quotes for single quotes. Compared with gpc, its configuration range is PHP_INI_ALL, which was removed in PHP5.4.0 - safe_mode (safe mode)
safe mode is a security mechanism embedded in PHP. When safe_mode=on, the commands that can be configured in the linkage include safe_mode_includea_dir, safe_mode_exec_dir, safe_mode_allowed_env_vars, and safe_mode_protected_env_vars. The configuration range of the safe_mode directive is PHP_INI_SYSTEM, which is canceled after PHP5.4 - open_basedir PHP accessible directory
The open_basedir command is used for which directories PHP can only access now. Usually we only need to set the web file directory. If you need to load an external script, you also need to add the directory path where the script is located to the open_basedir command. Multiple directories Separate by semicolon. One thing to note with open_basedir is that what is specified is now actually a prefix, not a directory name. If you want to restrict access only to the specified directory, end the pathname with a slash - disable_functions (disable function)
When you need to use instructions to disable dangerous functions, remember to add the dl() function to the forbidden list, because attackers can use the dl() function to load custom PHP extensions to break through the restrictions of the disable_functions instruction . The directive for disable_functions is restricted to php_ini_only - display_errors and error_reporting error display
display_errors indicates whether to display internal errors in PHP scripts. When debugging PHP, PHP error display is usually turned on, but in a production environment, it is recommended to turn off PHP error echo, that is, set display_errors=off to avoid Some safety hazards. When setting display_errors=on, you can also configure a command error_reporting, which is used to configure the level of error display, which can be configured using numbers or built-in constants. The configuration scope of these two directives is PHP_INI_ALL
PHP Dangerous Function Induction
In PHP, the following functions are dangerous functions that are often used in PHP:
- include/require/include_once/require_once
- eval/assert/preg_replace/create_function
- system/passthru/exec/shell_exec
- file_get_contents/fread/readfile/file/show_source
- file_put_contents/fwrite/mkdir
- unlink/rmdir
- move_uploaded_file/copy/rename
- extract/parse_str
- simplexml_load_files/simplexal_load_string
- deinialize
- urldecode/base64_decode
code execution function
eval executes strings as PHP codes. Many common webshells use eval to execute specific operations.
assert also executes strings as PHP codes.
preg_replace is a regular expression function
create_function creates anonymous functions and executes incoming commands
contains functions
The main function of the file inclusion function is to include and run the specified file, include/require/include_once/require_once $file, if $file is controllable, we can include any file, so as to achieve the purpose of getshell, and the inclusion function can also read Take arbitrary file content, which requires the use of supported protocols and encapsulation protocols and filters
command execution function
exec() Execute an external program
system() Execute an external program and display the output
The parameters that can be executed as long as the command can control the system command
file manipulation function
copy: copy the file
file_get_contents: read the entire file into a string
file_put_contents: write a string to the file
unlink: delete the file
rmdir: delete the directory
deserialization function
unserialize deserializes a serialized object