
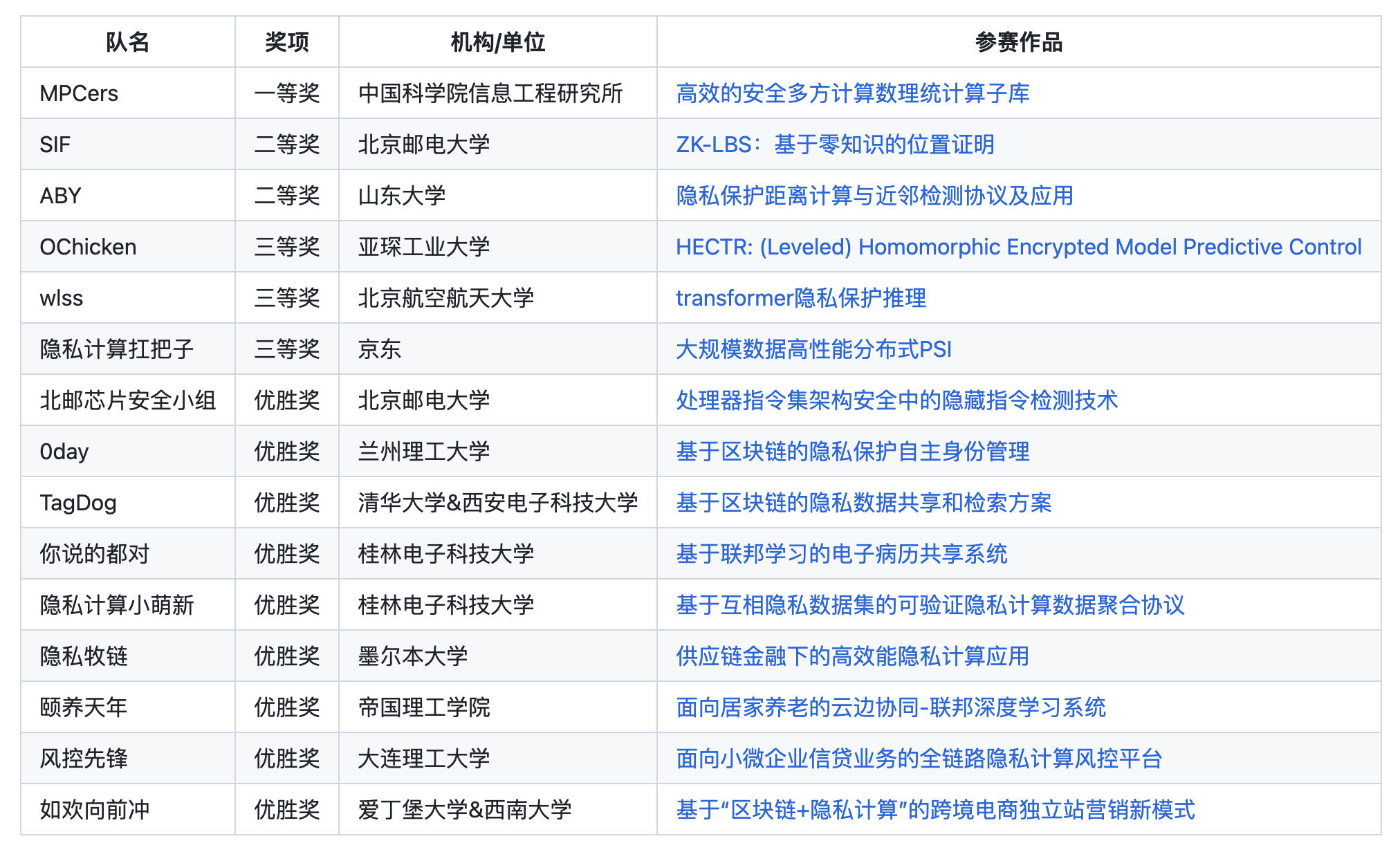
"2022 Privacy Computing HACKATHON Competition" is a creative competition around privacy computing technology jointly sponsored by OpenMPC and CSDN! This competition has attracted many participating teams from well-known universities, enterprises and institutions at home and abroad to sign up for the competition. The competition lasted for several months. After rigorous evaluation by the judging group, 15 participating teams stood out and won the honor. Since the winning teams have been announced before, I won't repeat them here! Today I only talk about projects and source code.
In line with the principle of open source co-construction, fairness and transparency, after friendly communication and negotiation with the winners, we unanimously decided to contribute the source code/PPT/scheme of the competition to the PrimiHub open source community through Pull request (PR).
We hope that through open source, we sincerely invite privacy computing enthusiasts, practitioners, and geeks to join us to optimize the participating code, improve the program, and give feedback. The PrimiHub open source community is willing to work with the award-winning team to use the power of open source to promote the research and innovation of privacy computing technology, and accelerate the deep integration of privacy computing technology and industry application scenarios.
After seeing so many excellent projects, the editor really couldn't resist sharing the results of the contest with you, so I sorted out this article while I was busy contacting various parties to promote the prize distribution. Now, let us walk into these entries together!
MeteorLib
- Work: Efficient Secure Multi-Party Computing Mathematical Statistics Computing Sublibrary
- Team: MPCers
- Awards: First Prize
As we all know, secure multi-party computing can effectively ensure that multi-party data is available and invisible, thereby effectively protecting private data. However, existing secure computing solutions are expensive and difficult to apply at large data scales.
MeteorLib is an efficient and secure multi-party computing mathematical statistics sub-library based on Meteor. It can effectively reduce the online overhead of participants. The design comes from the paper eprint/2023/100 ( https://eprint.iacr.org/2023 /100).
Source code: https://github.com/primihub/hackathon/blob/master/winning-project/MeteorLib/README.md
ZKLBS
- Work: Zero-knowledge-based proof of location
- Team: SIF
- Awards: Second Prize
With the development of precise positioning technology, more and more location-based services (LBS) have improved people's lives. But most LBSs require Proof of Location (PoL) to prove that users meet service requirements, thus exposing users' privacy.
In order to solve the possible problems caused by the leakage of personal location information, the ZKLBS zero-knowledge proof project was born according to the zero-knowledge position proof (zk-PoL) protocol. It can ensure that users participating in the evaluation have indeed arrived at the scenic spot or business when only providing longitude and latitude coordinates as public parameters. It is suitable for scenarios such as scenic spots, business evaluations, and consumption coupons in specific areas.
Source code: https://github.com/primihub/hackathon/blob/master/winning-project/ZKLBS/README.md
ABY-PPLP
- Work: Privacy-preserving distance calculation and neighbor detection protocol and application
- Team: ABY
- Awards: Second Prize
Location-based service application providers require users to submit accurate location information to obtain a better user experience. However, while users obtain great convenience, they also completely detach location information, which is easy to be tracked by malicious application service providers.
Driven by the dual requirements of location protection and location services, ABY-PPLP integrates location privacy, interaction rounds, communication overhead, post-quantum security and other influencing factors, and uses (full) homomorphic encryption, Bloom filter and other privacy enhancements, etc. technology, achieving the goals of low interaction, low latency, and post-quantum security. This technology can solve the problem of close contact tracking while paying attention to the pain points of user privacy data leakage. It has a better privacy distance calculation function for location protection and has a broad market at home and abroad.
Source code: https://github.com/primihub/hackathon/blob/master/winning-project/ABY/README.md
HECTR
- 作品:(Leveled) Homomorphic Encrypted Model Predictive Control
- Team: OChicken
- Awards: Third Prize
This project implements an encrypted model predictive control. The author refines and simplifies the core of the problem into dense-state matrix-vector multiplication, where the matrix is related to the model parameters, the vector is the current state and control, and the multiplication result is the optimal control at the next moment. The author uses the self-developed homomorphic encryption library GPQHE and the encryption control library HECTR to verify the consistency of the results of non-encryption control and encryption control.
Source code: https://github.com/OChicken/HECTR
Ray-PSI (code optimization, not yet open source)
- Work: Large-Scale Data High-Performance Distributed PSI
- Team: Take the lead in privacy computing
- Awards: Third Prize
Privacy Set Intersection (PSI) is the premise of federated modeling. In large-scale data scenarios (such as e-commerce daily intersecting and training tens of billions of data), there are high requirements for the performance of PSI. PSI performs horizontal distributed expansion to solve the performance bottleneck of a single machine. This product combines Ray and PSI to effectively solve the problems of unnecessary data storage in distributed data processing and ensure the consistency of data splitting on both sides. It greatly improves the efficiency of PSI's distributed transformation and development, and greatly reduces PSI is time consuming.
Source code: https://github.com/primihub/hackathon/blob/master/winning-project/ray_psi/README.md
PPT
- Work: transformer privacy protection reasoning
- Team: wlss
- Awards: Third Prize
In recent years, the transformer neural network has stood out with its excellent design and has been combined and applied to its own models by various platforms, such as BERT, ViT and GPT. In order to obtain the corresponding services, the interaction between the user and the platform will lead to the disclosure of the privacy of both parties.
According to different security requirements, the project designed and implemented two transformer secure two-party reasoning schemes based on homomorphic encryption and secure multi-party computing.
-
Two-party inference of transformer security based on homomorphic encryption: Provide equivalent services to clients on the premise that the server does not obtain any client privacy;
-
Transformer secure two-party reasoning based on secure multi-party computation: Provide efficient online services for clients while meeting server-side model parameters and client-side private data security requirements;
Source code: https://github.com/primihub/hackathon/blob/master/winning-project/PPT/README.md
at last
Due to the limited space, I will not introduce them one by one here. The following is the summary address of all award-winning projects. Interested friends can check them out by themselves.
It's been a long time since I came out, I'm going to flash back to move bricks. Finally, if you think these projects are not bad, please click Star to support them. Your encouragement is very important to us! ❤️
Graduates of the National People’s University stole the information of all students in the school to build a beauty scoring website, and have been criminally detained. The new Windows version of QQ based on the NT architecture is officially released. The United States will restrict China’s use of Amazon, Microsoft and other cloud services that provide training AI models . Open source projects announced to stop function development LeaferJS , the highest-paid technical position in 2023, released: Visual Studio Code 1.80, an open source and powerful 2D graphics library , supports terminal image functions . The number of Threads registrations has exceeded 30 million. "Change" deepin adopts Asahi Linux to adapt to Apple M1 database ranking in July: Oracle surges, opening up the score again