Article Directory
foreword
With the development of information technology, especially network and digital imaging technology, digital image has become the main source of people's acquisition and exchange of information and one of the important carriers of information dissemination. The emergence of image digital storage and various image processing software makes editing and modification of digital images easier. Digital image processing technology improves the display quality of images. If tampering and forging digital images are used in news media, court evidence, scientific discovery and other fields, it may have a serious negative impact on the integrity of the society, the credibility of the government and the authenticity of science. Therefore, how to detect and identify the authenticity and integrity of digital images has become a frontier research topic at home and abroad in recent years. It not only has important academic value, but also has important social significance and broad application prospects. This paper introduces the fragile watermark based on Hamming code proposed in the document **[1]**.
[1] F. Rasouli and M. Taheri, “A New Fragile Watermarking based on Distributed Hamming Code,” 2021 26th International Computer Conference, Computer Society of Iran (CSICC), 2021, pp. 1-5, doi: 10.1109/CSICC52343 .2021.9420541
1. What is a fragile watermark?
Fragile watermarking is a kind of digital watermarking to ensure the integrity of digital images by judging whether the digital images have been tampered with. The watermark information can detect and locate the tampered area along with the destruction of the embedded watermarked image. In recent years, researchers have proposed many image-based self-restoring fragile watermarking schemes. There are mainly two embedding methods, one is the fragile watermark based on the transform domain, and the other is the fragile watermark based on the spatial domain. The fragile watermark based on the transform domain is to convert the original image from the spatial domain image to the transform domain image through DCT transform, DWT transform, DFT transform, etc., and embed the watermark in the corresponding frequency band according to certain embedding rules. Substituting and exchanging coefficients for frequency bands, etc. Most researchers have chosen the self-embedding method in the spatial domain. The self-embedding method is to calculate the relevant features of the image as a watermark and embed it into the image itself.
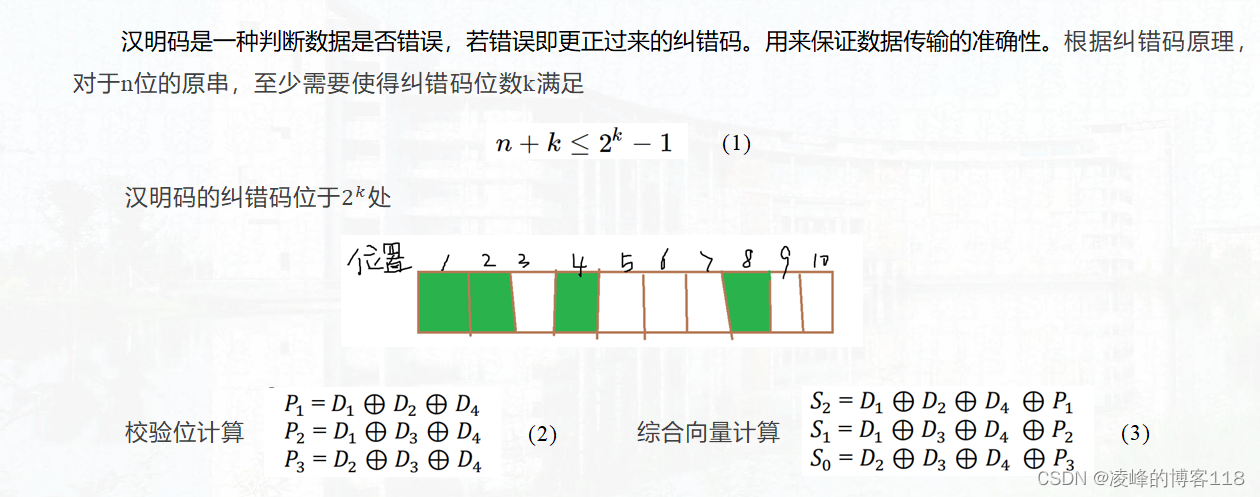
2. Hamming code
3. Algorithm introduction
Algorithm framework
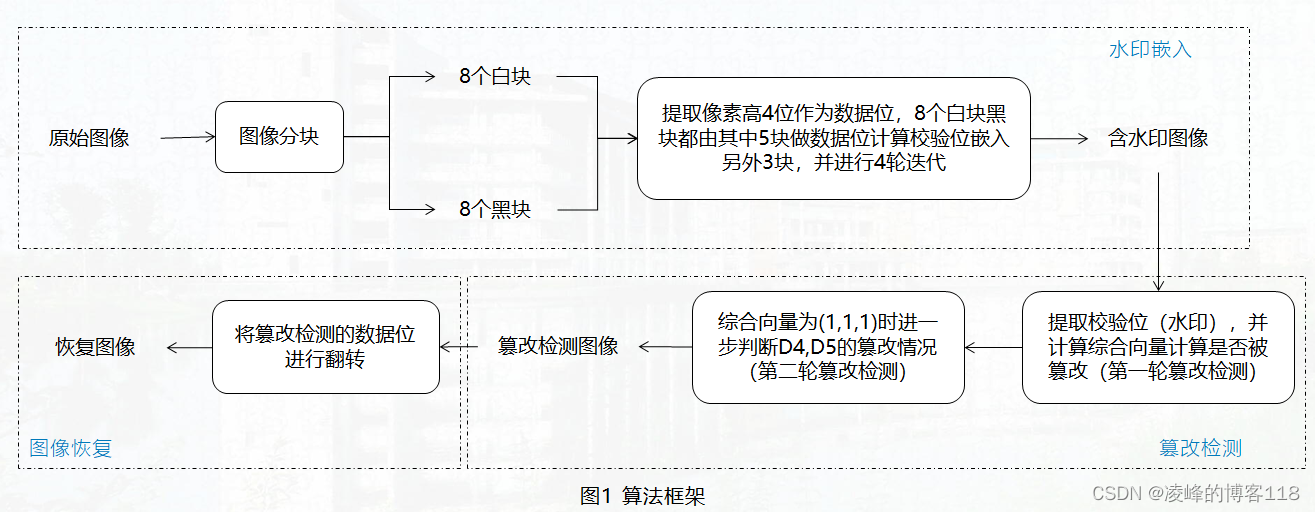
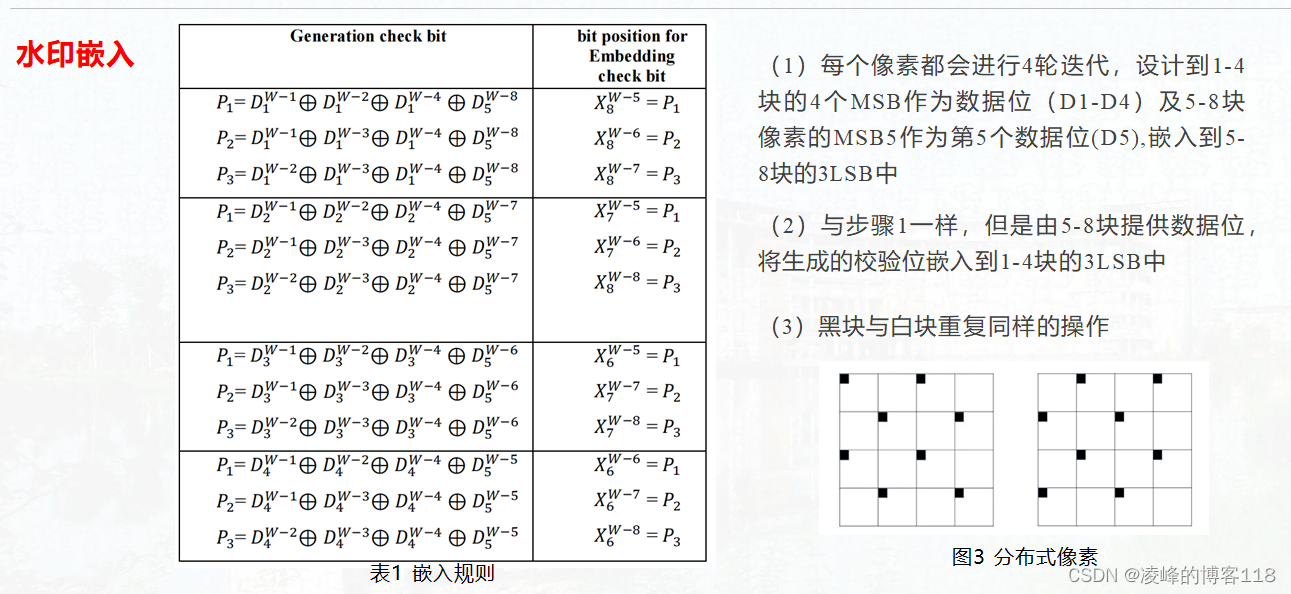
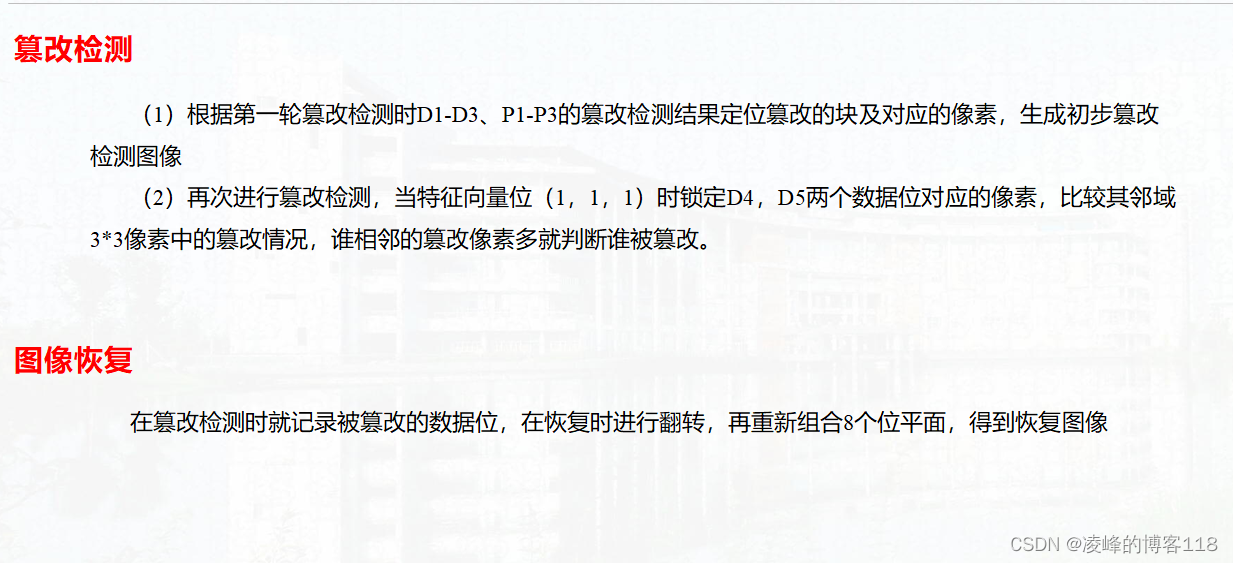
Algorithm principle


4. Experiment and simulation
1. Zone tampering:

2. Add random noise
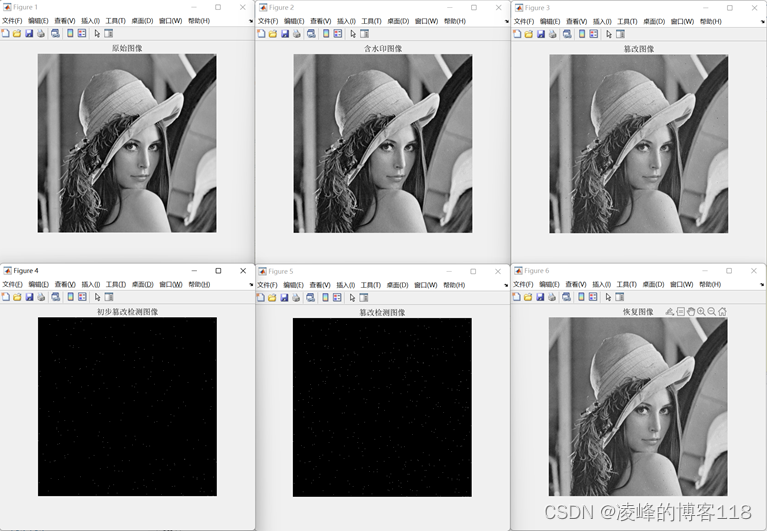
3. Collage attack

4. Experimental data
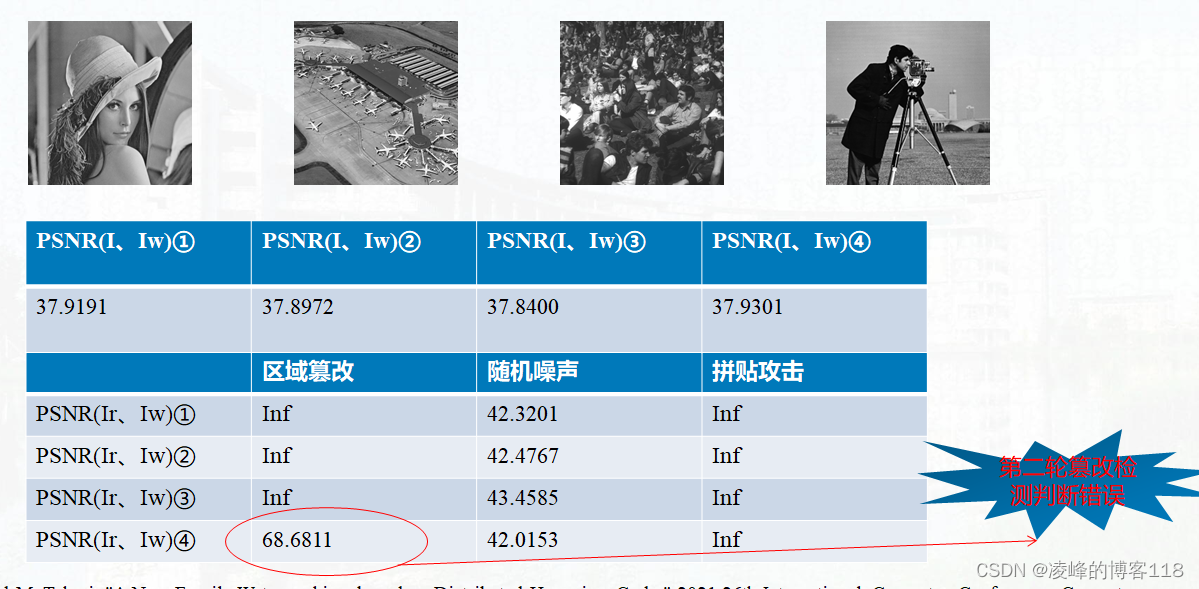
5. Data Analysis
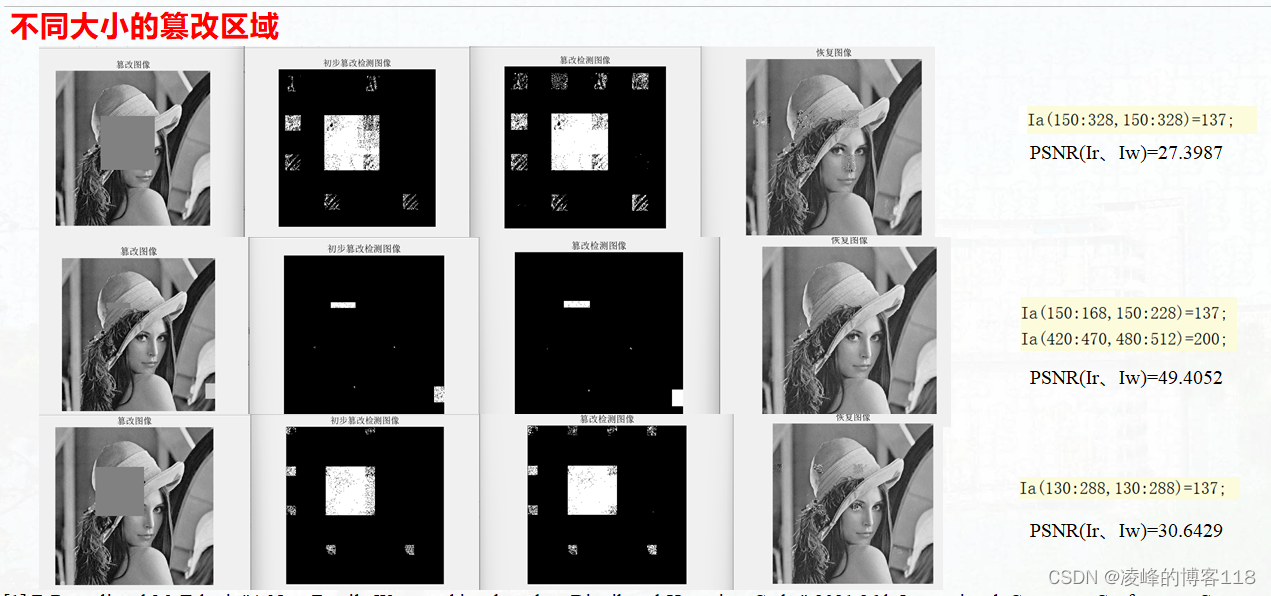
V. Conclusion
