In the rapidly developing digital age, data has become one of the most important production factors to promote industrial development, and has truly become a digital energy that creates economic wealth. Protecting the security of data assets has become an unavoidable and important proposition for high-quality development of enterprises.
On June 13, Tencent Security and IDC released the "Digital Security Immunity" model framework, which pointed out that enterprises need to protect the two core assets of enterprise data and digital business as the goal of enterprise security construction, and in the data security governance link, build enterprise Data ecology, accelerate the release of compliant data value, and build a "fortress" of digital security immunity.
In the technology sharing session, Dong Zhiqiang, an outstanding scientist of Tencent and head of Tencent Security Cloud Ding Lab, delivered a speech titled "Data Security Becomes the Security DNA of Enterprise Digital Transformation". He pointed out that as the security DNA of enterprise digital transformation, data security governance needs From the four key steps of data default security endogenous business, data visibility, manageability and controllability, and intelligent operation to promote closed-loop.
 (Dong Zhiqiang, Distinguished Scientist of Tencent, Director of Tencent Security Cloud Ding Lab)
(Dong Zhiqiang, Distinguished Scientist of Tencent, Director of Tencent Security Cloud Ding Lab)
Data security lag restricts enterprise digital security construction
Data security is a hot topic in the current era, and it is also a key factor that all enterprise security participants pay attention to. However, the current data security system construction capabilities of most enterprises are insufficient, and the perception of data leakage lags behind. According to the "2023 Enterprise Security Construction Level Sampling Survey Report" formed by Tencent Security and Anzai's joint survey of 1,500 CSOs, the current security construction of enterprises mainly revolves around network security, focusing on emergency response to security incidents, and the proportion of data governance is only 8.4% %.
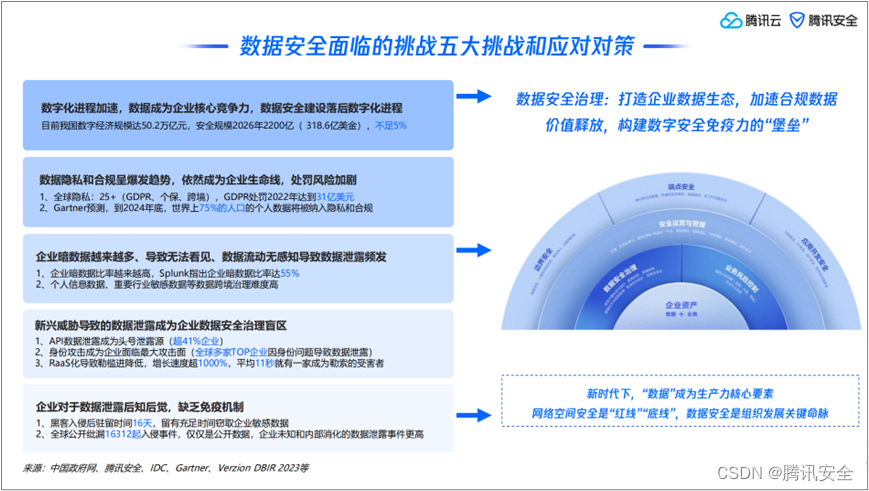
Dong Zhiqiang said that data security is the key lifeblood of organizational development. In the new era, data security faces five major challenges: first , data security construction lags behind the digitalization process, and digital security investment accounts for less than 5% of the overall investment in enterprise digitalization; Privacy and compliance are exploding, data has become the lifeline of enterprises, and the risk of punishment has intensified; third, data is invisible and data flow is unaware, resulting in frequent data leakage; fourth, data leakage caused by emerging threats has become a blind spot for enterprise data security governance , API data leaks and identity attacks have impacted corporate data security defenses, and RaaS has led to a further reduction in the threshold for extortion. On average, every 11 seconds, an enterprise becomes a victim of extortion virus; fifth, enterprises lack immunity to data leakage mechanism.
In the practice of building a data security system, enterprises still have difficulties in realizing simultaneous planning, construction, and use of data and security. When they realize the importance of data security construction and perform secure access, security risks are often seen everywhere. In this regard, Dong Zhiqiang said that data security governance needs to build an enterprise data ecosystem, accelerate the release of compliant data value, and build a "fortress" of digital security immunity.
Data security immunity builds a barrier to the protection of enterprise core assets
Dong Zhiqiang pointed out that the construction of data security governance needs to focus on four major steps:
First, the data is safe by default and integrated into the business. To deeply integrate data security into business, it is necessary to build a data default security system and integrate it into the enterprise security system design, including data transmission encryption, storage encryption, etc. Embedding data security into the business system can enable organizations to have innate data security immunity to a certain extent.
Second, the data can be seen, and the data security link flow can be perceived. Build visible capabilities for enterprise data, personal data, and highly sensitive industry regulatory data, and track the flow of data inside and outside the enterprise. Data is in different business scenarios, and the corresponding security requirements will also change, which requires classified and hierarchical management of decentralized and unstructured data.
Third, improve data protection and defense capabilities and build an immune system. Data security can be controlled, and risks can be quickly dealt with. At the level of technical capabilities, platforms and tools are provided for data security.
Fourth, intelligent operation of data security and closed-loop risk. Through the intelligent operation of DataSecOps, the closed loop of data risks is promoted and continuous iterative improvements are made. The core goal of digital data security is to "zero" the bottom line of enterprise-level protection against data leakage.

Through the accumulation of its own data security practice experience and capability standardization, Tencent Security has built several key capabilities including data security center DSGC, data security gateway CASB, key management system KMS, confidential computing and federated learning CCP, and collaborated with Tencent Cloud's various Security capabilities form a closed data security protection network to help enterprises maximize security benefits.
In addition, Dong Zhiqiang said that enterprises need to focus on their own business needs to evaluate and analyze their own data risk tolerance, and formulate targeted solutions based on their own risk tolerance and business needs. Effective implementation of data security work.
At present, Tencent Security has provided stable and reliable data security products and services for corporate customers in financial industries including digital government affairs, retail, and automobiles. Digital security is integrated into the security DNA of enterprise digital transformation to promote the sustainability of ecological data security governance.