1. What are the layers of the TCP/IP network model?
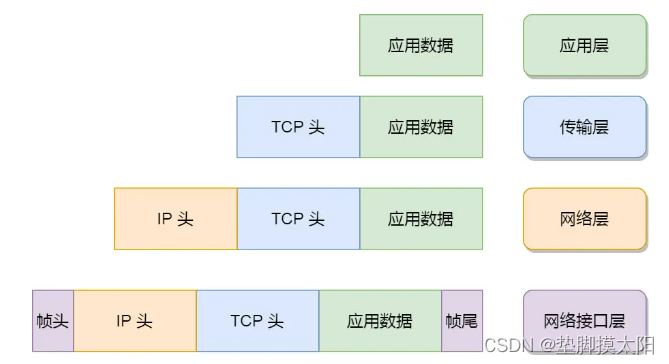
A TCP/IP network is usually divided into 4 layers from top to bottom, namely application layer, transport layer, network layer and network interface layer .
The encapsulation format of each layer:
The transmission unit of the network interface layer is frame (frame), the transmission unit of IP layer is packet (packet), the transmission unit of TCP layer is segment (segment), and the transmission unit of HTTP is message or message (message). However, there is no essential distinction between these nouns, and they can be collectively referred to as data packets.
2. What is HTTP?
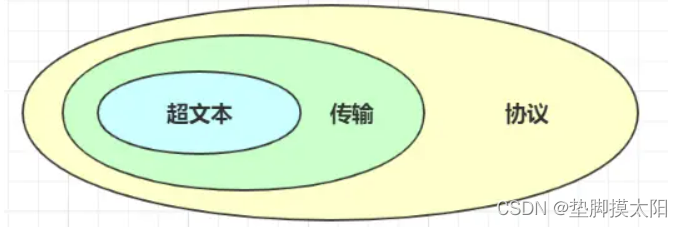
HTTP is Hypertext Transfer Protocol, that is HyperText Transfer Protocol .
3. What are the common status codes of HTTP?
4. What is the difference between GET and POST?
The semantics of GET is to request to get the specified resource. The GET method is safe, idempotent, and cacheable.
The semantics of POST is to process the specified resource according to the request load (message body), and the specific processing method varies depending on the resource type. POST is not safe, not idempotent, and (most implementations) not cacheable.
5. What are the implementation methods of HTTP caching?
There are two implementations of HTTP caching, namely mandatory caching and negotiation caching .
Mandatory caching : Strong caching means that as long as the browser judges that the cache has not expired, it will directly use the browser's local cache. The initiative to decide whether to use the cache lies with the browser.
Negotiation cache: Negotiation cache is to determine whether to use local cache according to the negotiation result after negotiating with the server.
6. What is the difference between HTTP and HTTPS?
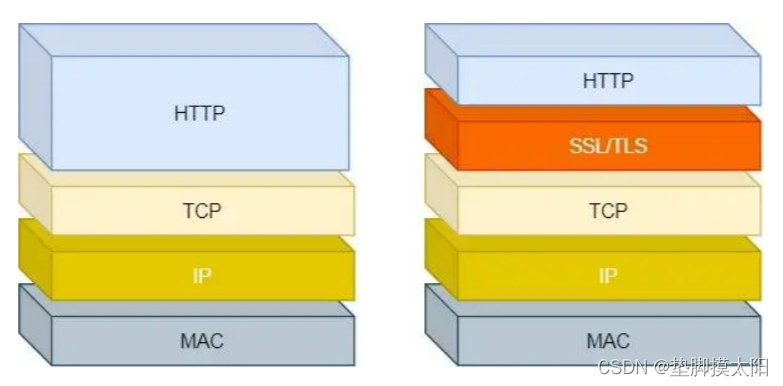
HTTP is a hypertext transfer protocol, and information is transmitted in clear text, which poses security risks. HTTPS solves the insecure defect of HTTP, adding SSL/TLS security protocol between TCP and HTTP network layers, so that messages can be encrypted for transmission.
HTTP connection establishment is relatively simple, and HTTP message transmission can be carried out after TCP three-way handshake. However, after the TCP three-way handshake, HTTPS needs to carry out the SSL/TLS handshake process before entering encrypted message transmission.
The default ports of the two are different, the default port number of HTTP is 80, and the default port number of HTTPS is 443.
The HTTPS protocol needs to apply for a digital certificate from a CA (Certificate Authority) to ensure that the identity of the server is trusted.
7. Which problems of HTTP does HTTPS solve?
Since HTTP is transmitted in clear text, there are three risks in terms of security:
- The risk of eavesdropping , for example, the communication content can be obtained on the communication link, and the user number is easily lost.
- Risks of tampering , such as mandatory placement of spam ads, visual pollution, and blindness of users.
- The risk of impersonation , such as pretending to be Taobao website, the user's money is easy to lose.
HTTP S adds
SSL/TLSa protocol between the HTTP and TCP layers, which can well solve the above risks:
- Information encryption : Interaction information cannot be stolen, but your account will be lost because of "forgotten" account.
- Verification mechanism : The content of the communication cannot be tampered with. If it is tampered with, it will not be displayed normally, but Baidu’s “PPC” can still search for spam ads.
- Identity certificate : Prove that Taobao is the real Taobao, but your money will still be lost because of "chopping hands".
- It can be seen that as long as it does not do "evil", the SSL/TLS protocol can ensure that communication is safe.
8. How does HTTPS solve the three risks of HTTP in (7)?
- The hybrid encryption method realizes the confidentiality of information and solves the risk of eavesdropping.
- The abstract algorithm is used to achieve integrity , which can generate a unique "fingerprint" for the data, and the fingerprint is used to verify the integrity of the data, which solves the risk of tampering.
- Putting the server public key into the digital certificate solves the risk of impersonation.
9. Is HTTPS necessarily safe and reliable?
The HTTPS protocol itself has no loopholes so far. Even if you successfully conduct a man-in-the-middle attack, it essentially takes advantage of the client's loopholes (the user clicks to continue to visit or is maliciously imported forged root certificates), and it is not that HTTPS is not secure enough .
10. What is TCP?
TCP is a connection-oriented, reliable, byte stream-based transport layer communication protocol.
Connection-oriented : it must be "one-to-one" to connect, unlike the UDP protocol, one host can send messages to multiple hosts at the same time, that is, one-to-many cannot be done;
Reliable : No matter what link changes occur in the network link, TCP can guarantee that a message will reach the receiving end;
Byte stream : When a user message is transmitted through the TCP protocol, the message may be "grouped" into multiple TCP messages by the operating system. If the receiver's program does not know the "message boundary", it cannot read a valid message. user messages. Moreover, TCP packets are "ordered". When the "previous" TCP packet is not received, even if it receives the following TCP packet first, it cannot be thrown to the application layer for processing. ” TCP packets will be discarded automatically.
The article is simplified from Brother Xiaolin's website, Brother Xiaolin yyds!
Mainly for self-study records!
Website Diagram Network Introduction | Xiaolin coding (xiaolincoding.com)