[Learning Difficulty: ★★★☆☆, Frequency of Use: ★★★★☆】
6.1. Pattern Motivation
In some cases, a client does not want or cannot directly refer to an object, at this time, a third party called a "proxy" can be used to achieve indirect reference. The proxy object can act as an intermediary between the client and the target object, and can remove content and services that the client cannot see or add additional services that the client needs through the proxy object.
By introducing a new object (such as a small picture and a remote proxy object) to realize the operation of the real object or use the new object as a substitute for the real object, this implementation mechanism is the proxy mode, which is indirectly accessed by introducing a proxy object An object, this is the pattern motivation of the proxy pattern.
In recent years, Daigou has gradually become an important branch of e-commerce. What is purchasing on behalf of you, in simple terms, is to find someone to help you buy the goods you need. Of course, you may need to pay a certain fee to the person who implements purchasing on behalf of you. Purchasing agents are usually divided into two types: one is because a certain product cannot be bought locally, or because the price of the local product is more expensive than that in other regions, so the entrusted person buys the product in other regions or even abroad, and then Deliver goods by express delivery or bring them back directly; there is also a kind of proxy purchasing. Due to the lack of information about the goods that consumers want to buy, they cannot determine their actual value and do not want to be ripped off by merchants, so they have to entrust intermediaries to help them bargain or buy goods for them. It buys it on behalf of others. Purchasing agent website came into being for this purpose, it provides consumers with online purchasing agent service, if you like the goods on a foreign shopping website, you can log on to the purchasing agent website to fill out the purchasing agent form and pay, the purchasing agent website will help to make the purchase and then send it to you through the courier company Goods are shipped to consumers. The commodity purchasing process is shown in Figure 15-1:
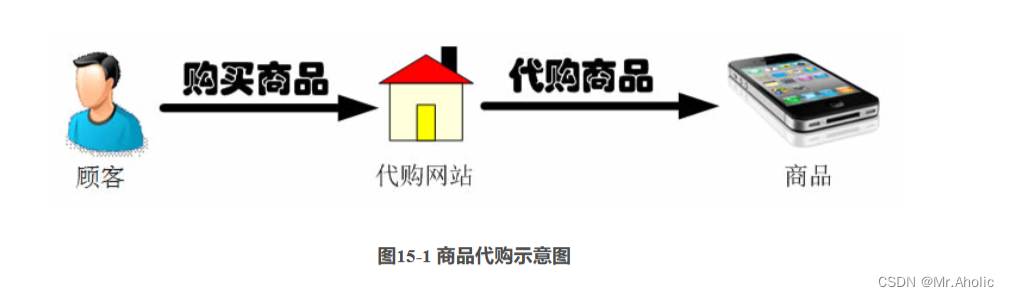
In software development, there is also a design pattern that can provide similar functionality to purchasing websites. For some reason, the client does not want or cannot directly access an object. At this time, a third party called a "proxy" can be used to achieve indirect access. The design pattern corresponding to this solution is called the proxy pattern.
Proxy mode is a widely used structural design mode with many variations. Common proxy forms include remote proxy, protection proxy, virtual proxy, buffer proxy, smart reference proxy, etc. These different proxy forms will be learned later .
6.2. Schema Definition
Proxy Pattern: Provide a proxy to an object, and the proxy object controls the reference to the original object. The English of the proxy mode is called Proxy or Surrogate, which is an object structure mode.
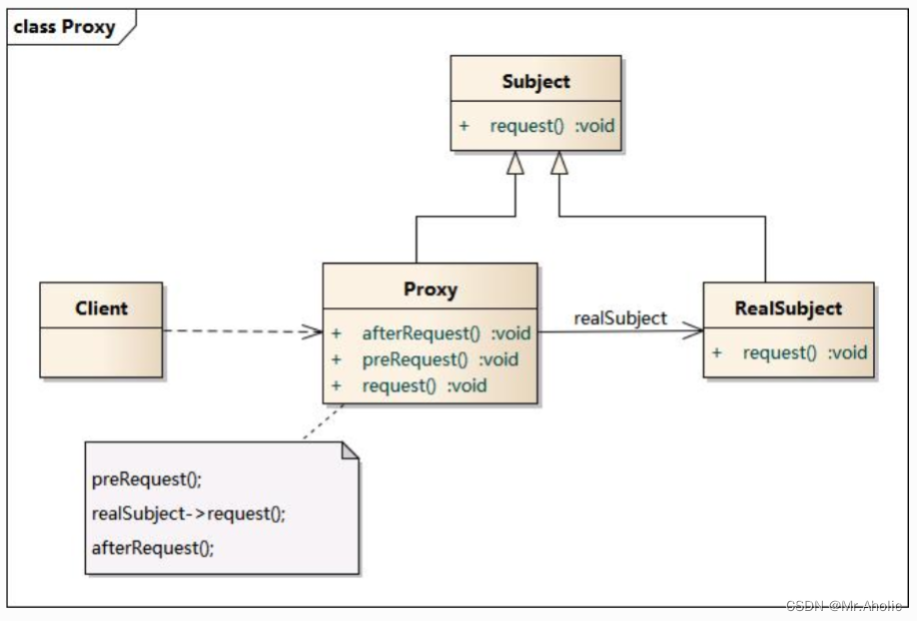
6.3. Schema structure
The proxy mode includes the following roles:
- Subject: The abstract subject role , which declares the common interface of the real subject and the proxy subject, so that the proxy subject can be used anywhere the real subject is used, and the client usually needs to program against the abstract subject role.
- Proxy: proxy theme role , which contains a reference to the real theme, so that the real theme object can be manipulated at any time; an interface identical to the real theme role is provided in the proxy theme role, so that the real theme can be replaced at any time; The proxy theme role can also control the use of the real theme, is responsible for creating and deleting the real theme object when needed, and imposes constraints on the use of the real theme object. Typically, in the role of a proxy topic, the client needs to perform other operations before or after invoking the referenced real topic operation, rather than simply calling operations on the real topic object.
- RealSubject: The real subject role , which defines the real object represented by the proxy role, realizes real business operations in the real subject role, and the client can indirectly invoke the operations defined in the real subject role through the proxy subject role.
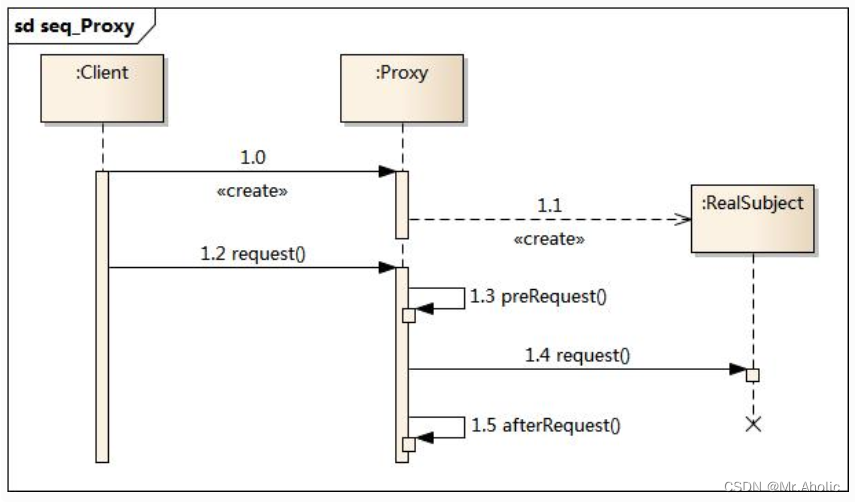
6.4. Timing Diagram
6.5. Code Analysis
The structure diagram of the proxy mode is relatively simple, but it is much more complicated in the actual use and implementation process, especially the design and implementation of the proxy class.
The abstract theme class declares the public methods of the real theme class and the proxy class. It can be an interface, an abstract class, or a concrete class. The client programs for the abstract theme class and treats the real theme and the proxy theme consistently. Typical abstract theme class code as follows:
abstract class Subject
{
public abstract void Request();
}
The real theme class inherits the abstract theme class and provides the concrete implementation of business methods. Its typical code is as follows:
class RealSubject : Subject
{
public override void Request()
{
//业务方法具体实现代码
}
}
The proxy class is also a subclass of the abstract theme class. It maintains a reference to the real theme object, calls the business method implemented in the real theme, and can add some new methods to the function on the basis of the original business method when calling. To expand or restrict, the simplest proxy class implementation code is as follows:
class Proxy : Subject
{
private RealSubject realSubject = new RealSubject(); //维持一个对真实主题对象的引用
public void PreRequest()
{
…...
}
public override void Request()
{
PreRequest();
realSubject.Request(); //调用真实主题对象的方法
PostRequest();
}
public void PostRequest()
{
……
}
}
In the actual development process, the implementation of the proxy class is much more complicated than the above code. The proxy mode can be divided into many types according to its purpose and implementation method. Several commonly used proxy modes are briefly described as follows:
- (1) Remote Proxy: Provide a local proxy object for an object located in a different address space. This different address space can be in the same host or in another host. Agents are also known as ambassadors (Ambassador).
- (2), Virtual Proxy (Virtual Proxy): If you need to create an object that consumes a lot of resources, first create a relatively small object to represent it, and the real object will only be created when needed.
- (3) Protect Proxy: It controls the access to an object and can provide different users with different levels of usage rights.
- (4) Cache Proxy: Provide temporary storage space for the results of a certain target operation, so that multiple clients can share these results.
- (5) Smart Reference Proxy: When an object is referenced, it provides some additional operations, such as recording the number of times the object is called.
Among these commonly used proxy patterns, some proxy classes are very complex in design, such as the remote proxy class, which encapsulates the underlying network communication and calls to remote objects, and its implementation is relatively complicated.
6.6. Schema analysis
6.7. Examples
1. An example shows that
a software company undertook the development task of a fee-based business information query system of an information consulting company. The basic requirements of the system are as follows:
- (1) Users need to pass identity verification before conducting business information inquiries, and only legitimate users can use the inquiry system;
- (2) When querying business information, the system needs to record the query log so that the query fee can be charged according to the number of queries.
The developers of this software company have completed the development task of the business information query module, and now hope to add authentication and logging functions to the original system in a loosely coupled manner, so that the client code can treat the original business information query without distinction module and the business information query module after adding new functions, and may add some new functions in the information query module in the future.
Try to design and realize the charging business information query system by using the agent mode.
2. Example analysis and class diagram
Through analysis, an indirect access method can be used to realize the design of the business information query system, and a proxy object is added between the client object and the information query object, so that the proxy object can realize identity verification and logging functions without directly modifying the original business information query object, as shown in Figure 15-3:
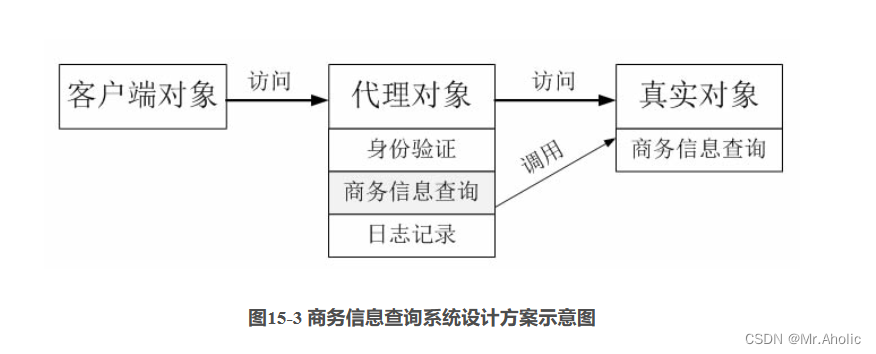
In Figure 15-3, the client object indirectly accesses the real object with the business information query function through the proxy object. In addition to invoking the business information query function of the real object, the proxy object also adds functions such as identity verification and logging. The business information query system is designed using the agent mode, and the structure diagram is shown in Figure 15-4.
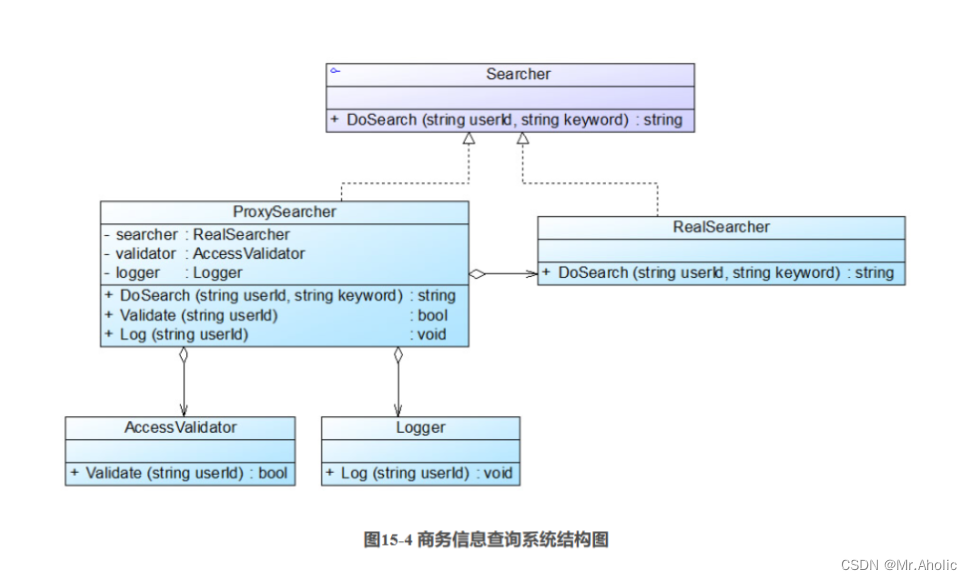
In Figure 15-4, the business class AccessValidator is used to verify user identity, the business class Logger is used to record user query logs, Searcher acts as an abstract theme role, RealSearcher acts as a real theme role, and ProxySearcher acts as a proxy theme role.
6.7.1 Production
package com.zyz.demo;
/**
* @author zyz
* @version 1.0
* @data 2023/5/22 18:55
* @Description:
*/
//身份验证类,业务类,它提供方法Validate()来实现身份验证。
class AccessValidator {
public Boolean Validate(String userId){
if(userId.equals("张三")){
System.out.println(userId+",通过校验,登录成功");
return true;
}else{
System.out.println(userId+",未通过校验,登录失败!!!");
return false;
}
}
}
//日志记录类,业务类,它提供方法Log()来保存日志。
class Logger{
public void Log(String userId){
System.out.println("更新数据库,用户" + userId + "查询次数加1");
}
}
//抽象查询类,充当抽象主题角色,它声明了DoSearch()方法
interface Searcher{
public String DoSearch(String userId, String keyword);
}
//具体查询类,充当真实主题角色,它实现查询功能,提供方法DoSearch()来查询信息。
class RealSearcher implements Searcher{
/**
* 模拟查询商务信息
* @param userId
* @param keyword
* @return
*/
@Override
public String DoSearch(String userId, String keyword) {
System.out.println("用户:"+ userId+",使用关键词:" + keyword + "查询商务信息!");
return "我查询了数据";
}
}
//代理查询类,充当代理主题角色,它是查询代理,维持了对RealSearcher对象、AccessValidator对象和Logger对象的引用。
class ProxySearcher implements Searcher{
private RealSearcher searcher = new RealSearcher(); //维持一个对真实主题的引用
private AccessValidator validator;
private Logger logger;
@Override
public String DoSearch(String userId, String keyword) {
if(this.Validate(userId)){
String result = searcher.DoSearch(userId,keyword);//调用真实主题对象的查询方法
this.Log(userId);//记录日志
return result; //返回查询结果
}
return null;
}
/**
* 创建访问验证对象并调用其Validate()方法实现身份验证
* @param userId
* @return
*/
public Boolean Validate(String userId)
{
validator = new AccessValidator();
return validator.Validate(userId);
}
/**
* 创建日志记录对象并调用其Log()方法实现日志记录
* @param userId
*/
public void Log(String userId)
{
logger = new Logger();
logger.Log(userId);
}
}
6.7.2 Client
package com.zyz.demo;
/**
* @author zyz
* @version 1.0
* @data 2023/5/22 19:12
* @Description: 客户端
*/
public class Client {
public static void main(String[] args) {
Searcher searcher;
searcher = new ProxySearcher();
String result = searcher.DoSearch("张三","天龙八部");
System.out.println(result);
}
}
6.7.3 Test results
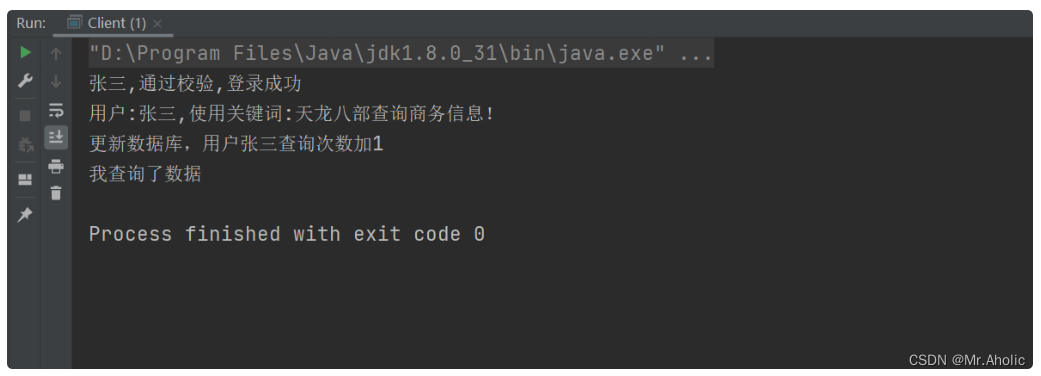
This example is an application example of a protection proxy and a smart reference proxy. In the proxy class ProxySearcher, the authority control and reference counting of the real theme class are implemented. If you need to add a new access control mechanism and new functions when accessing the real theme, you only need to add A new proxy class, modify the configuration file, and use the new proxy class in the client code. The source code does not need to be modified, which conforms to the principle of opening and closing.
6.8. Advantages
Advantages of the proxy model
- The proxy mode can coordinate the caller and the callee, which reduces the coupling of the system to a certain extent.
- The remote proxy enables the client to access the objects on the remote machine. The remote machine may have better computing performance and processing speed, and can quickly respond and process client requests.
- By using a small object to represent a large object, the virtual agent can reduce the consumption of system resources, optimize the system and improve the running speed.
- Protection proxies control access to real objects.
6.9. Disadvantages
Disadvantages of proxy mode
- Some types of proxy patterns may slow down request processing due to the addition of proxy objects between the client and the real subject.
- Implementing proxy patterns requires extra work, and some proxy patterns are very complex to implement.
6.10. Applicable environment
According to the purpose of using the proxy mode, the common proxy modes are as follows:
- Remote (Remote) proxy: Provide a local proxy object for an object located in a different address space. This different address space can be in the same host or in another host. The remote proxy is also called ambassador ( Ambassador).
- Virtual (Virtual) proxy: If you need to create an object that consumes a lot of resources, first create a relatively small object to represent it, and the real object will only be created when needed.
- Copy-on-Write agent: It is a kind of virtual agent that delays the copy (cloning) operation until it is only executed when the client really needs it. Generally speaking, deep cloning of an object is an expensive operation. The Copy-on-Write agent can delay this operation, and the object is only cloned when it is used.
- Protection (Protect or Access) agent: Controls access to an object, and can provide different users with different levels of usage permissions.
- Cache proxy: Provide temporary storage space for the results of a certain target operation, so that multiple clients can share these results.
- Firewall agent: protect the target from malicious users.
- Synchronization (Synchronization) agent: enables several users to use an object at the same time without conflict.
- Smart Reference (Smart Reference) agent: When an object is referenced, it provides some additional operations, such as recording the number of times this object is called, etc.
6.11. Schema Application
Distributed technologies such as EJB and Web Service are all applications of the proxy mode. The RMI mechanism is used in EJB. The enterprise-level bean in the remote server has a stub proxy locally. The client uses the stub to call the method defined in the remote object without directly interacting with the remote object. In the use of EJB, a public interface needs to be provided, and the client program does not need to know the implementation details of stubs and remote EJB for this interface.
6.12. Schema Extensions
Several commonly used proxy modes
- Image proxy: A very common application example of the proxy mode is the control of large image browsing.
- When the user visits the web page through the browser, the real large image is not loaded first, but is processed through the method of the proxy object. In the method of the proxy object, a thread is first used to load a small image to the client browser, and then the image is loaded in the background Use another thread to call the loading method of the large image to load the large image to the client. When a large picture needs to be browsed, the large picture is displayed in a new web page. If the loading work has not been completed when the user browses the large image, another thread can be started to display the corresponding prompt information. Through proxy technology combined with multi-threaded programming, the loading of real pictures can be operated in the background without affecting the browsing of pictures in the foreground.
- Remote agent: The remote agent can hide the details of the network, so that the client does not have to consider the existence of the network. Customers can completely think that the remote business object being proxied is local rather than remote, and the remote proxy object undertakes most of the network communication work.
- Virtual agent: When the loading of an object is very resource-intensive, the advantages of virtual agent are very obvious. The Virtual Proxy pattern is a memory-saving technique, where objects that take up a lot of memory or deal with complex objects will be deferred until they are used.
- When the application starts, the proxy object can be used instead of the real object to initialize, which saves memory usage and greatly speeds up the system startup time.
dynamic proxy - Dynamic proxy is a more advanced proxy mode, and its typical application is Spring AOP.
- In the traditional proxy mode, the client calls the request() method of the RealSubject class through the Proxy, and at the same time encapsulates other methods (such as preRequest() and postRequest()) in the proxy class to handle some other problems.
- If the proxy mode is used in this way, the real subject role must already exist in advance and be used as an internal member attribute of the proxy object. If a real theme role must correspond to a proxy theme role, this will lead to a sharp increase in the number of classes in the system, so it is necessary to find a way to reduce the number of classes in the system. In addition, how to use it without knowing the real theme role in advance Proxy subject role, this is a problem that dynamic proxy needs to solve.
6.13. Summary
In the proxy mode, it is required to provide a proxy to an object, and the proxy object controls the reference to the original object. The English of the proxy mode is called Proxy or Surrogate, which is an object structure mode. - The proxy mode contains three roles: the abstract theme role declares the common interface between the real theme and the proxy theme; the proxy theme role contains a reference to the real theme inside, so that the real theme object can be manipulated at any time; the real theme role defines the proxy role The real object represented implements real business operations in the real subject role, and the client can indirectly call the methods defined in the real subject role through the proxy subject role. - The advantage of the proxy mode is that it can coordinate the caller and the callee, which reduces the coupling of the system to a certain extent; its disadvantage is that due to the addition of proxy objects between the client and the real subject, some types of proxy modes may It will slow down the processing speed of the request, and additional work is required to implement the proxy mode, and the implementation of some proxy modes is very complicated. The remote proxy provides a local representative object for an object located in a different address space, which enables the client to access the object on the remote machine. The remote machine may have better computing performance and processing speed, and can quickly respond and process customers. end request. - If you need to create an object that consumes a lot of resources, first create a relatively small object to represent it. The real object will only be created when needed. This small object is called a virtual proxy. By using a small object to represent a large object, the virtual agent can reduce the consumption of system resources, optimize the system and improve the running speed. - The protection agent can control the access to an object, and can provide different users with different levels of usage rights.
6.13.4 Extension
1 Remote Proxy
Remote proxy (Remote Proxy) is a commonly used proxy mode, which enables client programs to access objects on remote hosts. Remote hosts may have better computing performance and processing speed, and can quickly respond and process customers. end request. The remote proxy can hide the details of the network, so that the client does not have to consider the existence of the network. The client can completely think that the proxied remote business object is local rather than remote, and the remote proxy object undertakes most of the network communication work and is responsible for invoking remote business methods.
The schematic diagram of the remote agent is shown in Figure 15-5. The client object cannot directly access the business object in the remote host, but can only use indirect access. The remote business object has a proxy object in the local host, which is responsible for the access and network communication of the remote business object, which is transparent to the client object. The client does not need to care about who implements the specific business, it only needs to directly interact with the proxy object in the local host according to the method defined by the service interface.
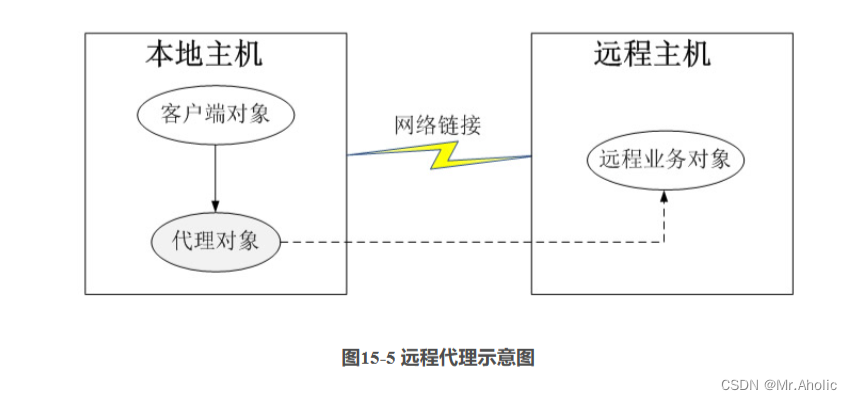
In distributed technology based on .NET platform, such as DCOM (Distribute Component Object Model, Distributed Component Object Model) and Web Service, the remote proxy mode is applied, and you can refer to relevant materials for extended learning.
2 Virtual proxy
Virtual proxy (Virtual Proxy) is also a commonly used proxy mode. For some objects that occupy more system resources or take a long time to load, a virtual proxy can be provided for these objects. Before the real object is successfully created, the virtual proxy acts as a substitute for the real object, and after the real object is created, the virtual proxy forwards the user's request to the real object.
In general, virtual proxies can be considered in the following two situations:
-
(1) Due to the complexity of the object itself or the network, an object requires a long loading time. At this time, a proxy object with a relatively short loading time can be used to represent the real object. Usually, multi-threading technology can be combined during implementation, one thread is used to display proxy objects, and other threads are used to load real objects. This virtual proxy mode can be applied when the program starts. Since the time and processing complexity of creating a proxy object is less than that of creating a real object, when the program starts, the proxy object can be used instead of the real object initialization, which greatly speeds up the process. The boot time of the system. When the real object needs to be used, it is referenced through the proxy object. At this time, the real object may have been successfully loaded, which can shorten the user's waiting time.
-
(2) When loading an object consumes system resources, it is also very suitable to use virtual proxy. Virtual proxies can defer the creation of objects that take up a lot of memory or are very complex to use until they are used. Before that, a proxy object that takes up relatively few resources is used to represent the real object, and then the proxy object is used to represent the real object. Reference to the real object. In order to save memory, the object is created when the real object is referenced for the first time, and the object can be reused multiple times. It is necessary to check whether the required object has been created each time it is accessed, so it needs to be present when accessing the object. Sex detection, which consumes a certain amount of system time, but can save memory space, which is a practice of exchanging time for space.
-
Regardless of the above situations, the virtual proxy uses a "false" proxy object to represent the real object, and indirectly references the real object through the proxy object, which can improve the performance of the system to a certain extent.
3 Cache proxy
Cache proxy (Cache Proxy) is also a more commonly used proxy mode, which provides temporary cache storage space for the results of a certain operation, so that these results can be shared in subsequent use, thus avoiding duplication of certain methods Execute to optimize system performance.
Classes such as Product, Category, and Item are defined in the Business Logic Layer (BLL) of the Microsoft sample project PetShop 4.0, which encapsulate related business methods and are used to call Data Access Layer (Data Access Layer, DAL) objects Access the database to obtain relevant data. In order to improve the system performance, PetShop 4.0 adds a cache mechanism for these implementation methods, and introduces a new object to control the original BLL business logic object. These new objects correspond to the proxy objects in the proxy mode. After the introduction of the proxy mode, the encapsulation of business objects at the cache level is realized, and the control of business objects is enhanced. If the data to be accessed already exists in the cache, there is no need to repeatedly execute the method of obtaining data, and directly return to the storage The data in the cache will do. Since the exposed methods of the original business object (real object) and the new proxy object are consistent, there is no substantial difference between calling the proxy object and the real object for the caller, that is, the client.
These newly introduced proxy classes include ProductDataProxy, CategoryDataProxy and ItemDataProxy, etc. Let’s take the PetShop.BLL.Product business object as an example. PetShop 4.0 creates a proxy object ProductDataProxy for it, and calls the GetProductsByCategory() method of the Product class in the business logic layer in the GetProductsByCategory() method of ProductDataProxy, and adds a cache mechanism. As shown in Figure 15-6:
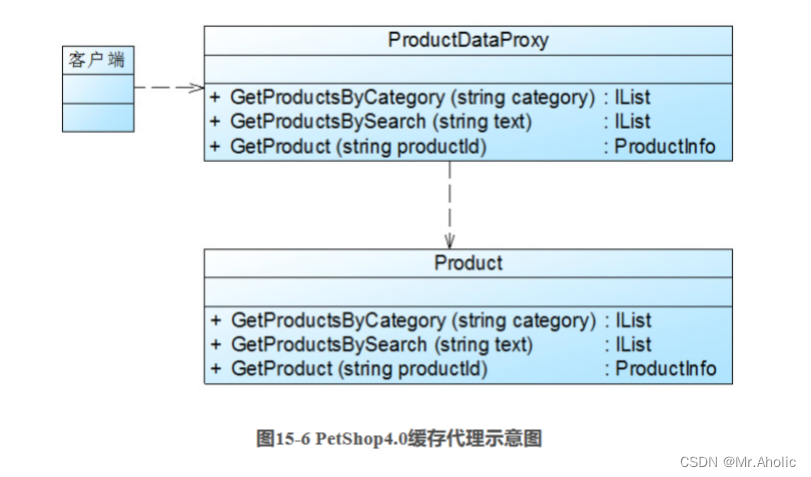
The following code snippets exist in the ProductDataProxy class:
public static class ProductDataProxy
{
private static readonly int productTimeout = int.Parse(ConfigurationManager.AppSettings ["ProductCacheDuration"]);
private static readonly bool enableCaching = bool.Parse(ConfigurationManager. AppSettings["EnableCaching"]);
public static IList GetProductsByCategory(string category)
{
Product product = new Product();
//如果缓存被禁用,则直接通过product对象来获取数据
if (!enableCaching)
{
return product.GetProductsByCategory(category);
}
string key = "product_by_category_" + category;
//从缓存中获取数据
IList data = (IList )HttpRuntime.Cache[key];
//如果缓存中没有数据则执行如下代码
if (data == null)
{
data = product.GetProductsByCategory(category);
//通过工厂创建AggregateCacheDependency对象
AggregateCacheDependency cd = DependencyFacade.GetProductDependency ();
//将数据存储在缓存中,并添加必要的AggregateCacheDependency对象
HttpRuntime.Cache.Add(key, data, cd, DateTime.Now.AddHours(product Timeout), Cache.NoSlidingExpiration, CacheItemPriority.High, null);
}
return data;
}
……
}
In the above code, AggregateCacheDependency is a new class from .NET Framework 2.0, which is responsible for monitoring the collection of dependency objects. When any dependency object in this collection changes, the cache object corresponding to the dependency object will be automatically removed. AggregateCacheDependency will not be described in detail here, and you can refer to relevant materials for extended learning.
Compared with the GetProductsByCategory() method of the Product object in the business logic layer, the above code adds a cache mechanism. When there is no relevant data item in the cache, directly call the GetProductsByCategory() method of the business logic layer Product to obtain the data, and store it in the cache together with the corresponding AggregateCacheDependency object. In each business method of the ProductDataProxy class, the Product class is instantiated, and then the corresponding method of the Product class is called, so the relationship between ProductDataProxy and Product is a dependency. This is a variant of the standard proxy mode, which can be used according to the standard proxy mode. It is improved, including the introduction of high-level abstract interfaces.