In most cases, the distribution of local variables in the stack is adjacent, but there may be exceptions due to compilation optimization and other needs. We need to deal with the specific situation in dynamic debugging. For the purpose of explaining the basic principles here, we can temporarily think that local variables are close together in the stack.
Provide theoretical basis Next use: Illegal super long password to modify the adjacency variable authenticated of bufer to bypass the password verification procedure
Rationale for Modifying Adjacency Variables
Through the previous article: Function calling convention and related instructions - 0day exploit principle (5)_luozhonghua2000's blog - CSDN blog , we already know the details of function calls and the distribution of data in the stack. As shown in Figure 5, the local variables of the function are arranged next to each other in the stack. If there are buffers such as arrays in these local variables, and there is an array out-of-bounds defect in the program, then the out-of-bounds array elements may destroy the values of adjacent variables in the stack, or even destroy the EBP value saved in the stack frame, Important data such as return address.
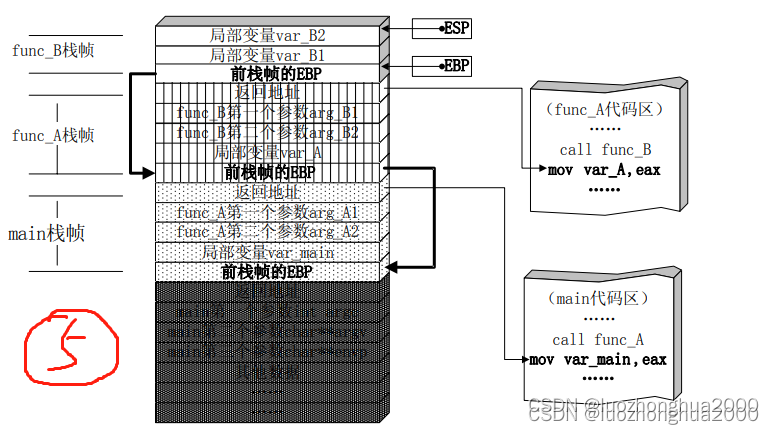
We will use a very simple example to illustrate how destroying local variables on the stack affects the security of the program.
#include <stdio.h>
#define PASSWORD "1234567"
int verify_password (c