Contents
1. Introduction 2.
Overview of related technologies
(1) J2EE technology based on MVC design pattern
(2) MySql database management system
(3) System security based on B/S structure
3. Overall design of enterprise personnel management system
(1) System requirements Analysis
1. Functional structure decomposition
2. Employee file management module
3. Employee salary management module
(2) Overall system structure design
4. Detailed design of enterprise personnel management system
(1) User login design
(2) Employee file management module design
(3) Employee attendance management module design
(4) Database design
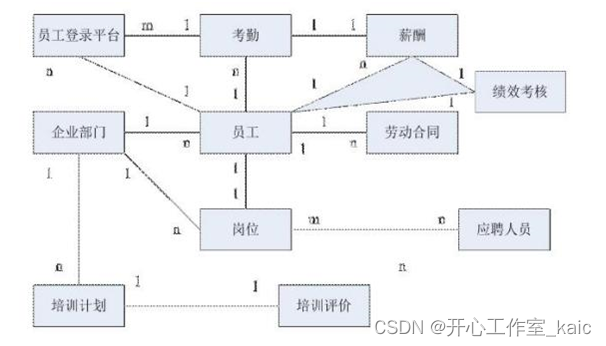
1. Database conceptual structure design
2. Database table structure design
5. Implementation of enterprise personnel management system
(1) User login implementation
(2) Employee file management module implementation
(3) Employee attendance management Module realization
6. System test
(1) Test environment
(2) Test case
1. Login function test case
2. Employee file module test case
3. Employee attendance module test case
Conclusion
References
Acknowledgments
Design and Implementation of Enterprise Personnel Management System Based on J2EE Technology
Abstract
With the continuous development of information technology, the environment of computer support hardware has been continuously improved, and various information systems have emerged like bamboo shoots after the rain, which is extremely convenient for the increasingly intense enterprise management work. Today's society has entered the information age of the 21st century, and enterprises have an urgent need for management information systems. Especially with the development of the enterprise, the human resource team is constantly growing, which puts forward new requirements for its management. Based on the analysis of the problems in the personnel management system based on the C/S framework, J2EE and b/S framework are used for model design, system analysis and system development. The layer model, display layer and layer controller meet the requirements of the Federal Strategic Plan J2EE server. In addition, the technology should be based on physical layer design and database application based on J2EE logic, as well as the selection of Arwin cellular database and information management system. Based on requirement analysis J2EE standardized modeling technology, database technology, personnel management project application and realization of personnel management system.
Key words: personnel management system; J2EE; MySql
Design and Implementation of Enterprise Personnel
Management System Based on J2EE Technology
Abstract
With the continuous development of information technology, the environment for computer supported hardware is constantly improving, and various information systems are emerging like bamboo shoots after a rain, which is extremely convenient for the increasingly fierce enterprise management work. Today's society has entered the information age of the 21st century, and enterprises have an urgent need for management information systems. Especially with the development of enterprises, the human resources team continues to grow, posing new requirements for its management. Based on the analysis of the problems in the personnel management system based on the C/S framework, J2EE and B/S frameworks are used for model design, system analysis, and system development. The layer model, display layer, and layer controller meet the requirements of the federated strategic plan J2EE server. In addition, this technology should also be based on physical layer design and database applications based on J2EE logic, as well as the selection of Arwin cellular databases and information management systems. Standardized modeling technology based on requirement analysis J2EE, database technology, personnel management project application, and implementation of personnel management system.
Keywords: personnel management system; J2EE; MySql
1. Introduction
In the stage of enterprise-level data processing, the most commonly used method is data warehouse. The company collects raw cloud data and all external data through a data warehouse for leadership to make decisions. Provide efficient and comprehensive decision-making for services. A data warehouse is a part of a decision support system and environment that includes large volumes of related data and information from different sources. The database collects all pre-set user information and provides program system developers with information about all employees in the organization's human resources. The list expands the data storage and management system. It extends data repositories from on-premises solutions to external solutions to all users in the organization. Data storage technology and e-commerce. In this way, the information resources in the data warehouse can be fully utilized and decisions can be made during the development phase. Therefore, enterprise projects can be applied. The user data repository goes deeper. Software tools or data collection tools developed by manufacturers can be used to achieve these goals. Software development companies develop software that can effectively integrate business intelligence data warehouses.
2. Overview of related technologies
(1) J2EE technology based on MVC design pattern
The controller view of the joint audit task model is the first construct that distinguishes between business logic and logical presentation. It goes into the data layer, display layer, and layer controllers. The control layer is mainly used to coordinate the data of the display layer. Users need to integrate the two parts of the display layer into the data layer, and then design a three-tier architecture. The main difference is that the federated validation task model separates the business logic. The software system based on the Java J2EE development architecture provides developers with reusable interfaces, multi-level software system models, transaction control models, and standardized software security models. This approach avoids just-in-time delivery, multi-tier distributed software system model applications, transactional control methods, and a unified program security model. Elements of a J2EE solution are not bound by products or APIs produced by the manufacturer:
development based on the Java J2EE architecture belongs to the domain of project computing. For example, business units, database connections, network technologies, relay messages, interconnections, etc. Based on this structure, more and more people develop open standard products through system architecture software. Security and stability. Java based on the J2EE framework is a unified software development platform, which can be used by different suppliers to interact and reduce the risk of monopoly. J2EE-based software applications are rapidly evolving, and products are ready-to-use, developed and ready to run. The advantage of this project is that the development will be completed in a short period of time, and all projects have been completed in a short period of time and can be put into use quickly.
(2) MySql database management system
SQL was the first small relational database management system developed by SQL AB in Sweden. Buy from Microsoft SQL Database, which currently supports many existing operating systems. The current home page (including DB2 and Oracle) "is the service offering
large database of vendors. Many databases are stored in one repository. Module providers who use database access language now usually use "integrated language". It has the advantages of low cost and multiple open source codes. It is the best database system developed on the Internet for small and medium-sized enterprises. Data providers usually use various Standards to support simple installation and high availability. Effective, network support for multiple information types;
(3) System security based on B/S structure
Security requirements in system development include local network security, high security of data transmission, control and authentication requirements, and data availability, processing and transmission. A common encryption method for storing data is technical database file encryption.