overview
The BGW protocol can be used to evaluate arithmetic circuits including addition, multiplication, and constant multiplication gates on the domain. This protocol can rely on the Shamir secret sharing scheme and use its homomorphic characteristics to properly process each secret share. perform secure calculations.
Addition gate
Arithmetic addition sharing (two parties)
One party holds the ciphertext and the other holds the key.
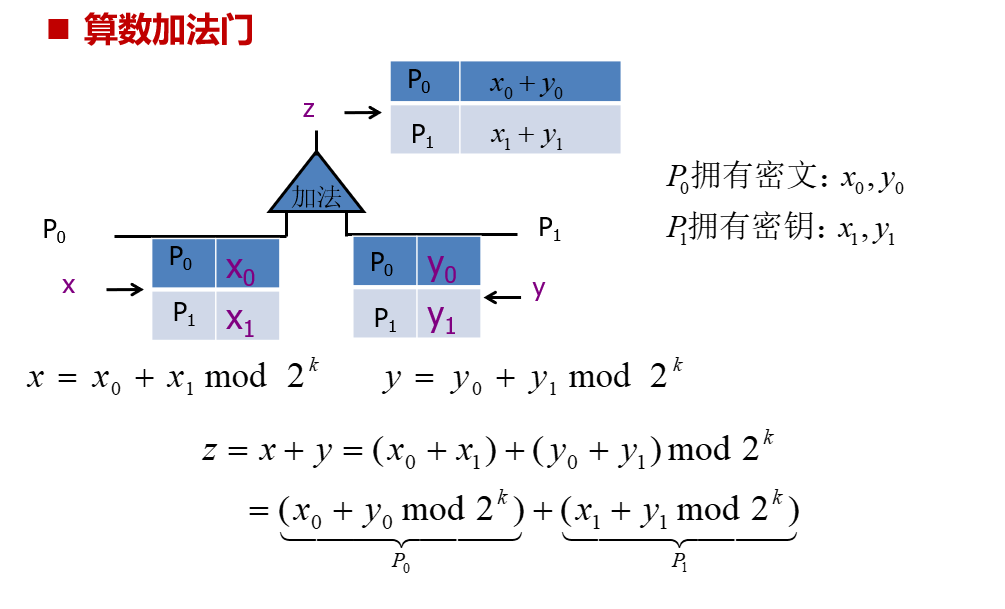
Obviously, the arithmetic addition gate completes the calculation result without interaction, and the calculation can be completed locally. (The GMW protocol is equivalent to mod 2 computing.)
Additive sharing based on Shamir scheme (multi-party)
Consider two input gates x , yx,yx,y , an output gatezzThe addition gate of z , calculatez = y + xz=y+xz=y+x . Also, to achieve sharing, the input wire values of the two input gates need to be secretly split among multiple parties. First for each input wire for the value to be enteredxoryx \quad or \quad yxory , select attA polynomial of order t , then Shamir's( t , n ) (t,n)(t,n ) share, distribute the secret share to other participants, so assuming that there arennn participants, then you will getnn secret shares from different input wires. Local summation and accumulation, the output gatezzOne of the z- values ( t , n ) (t,n)(t,n ) share. Justt+1 t+1t+One or more joint reconstruction secrets can restore the final addition result.
multiplication gate
Arithmetic multiplication shared (two parties)
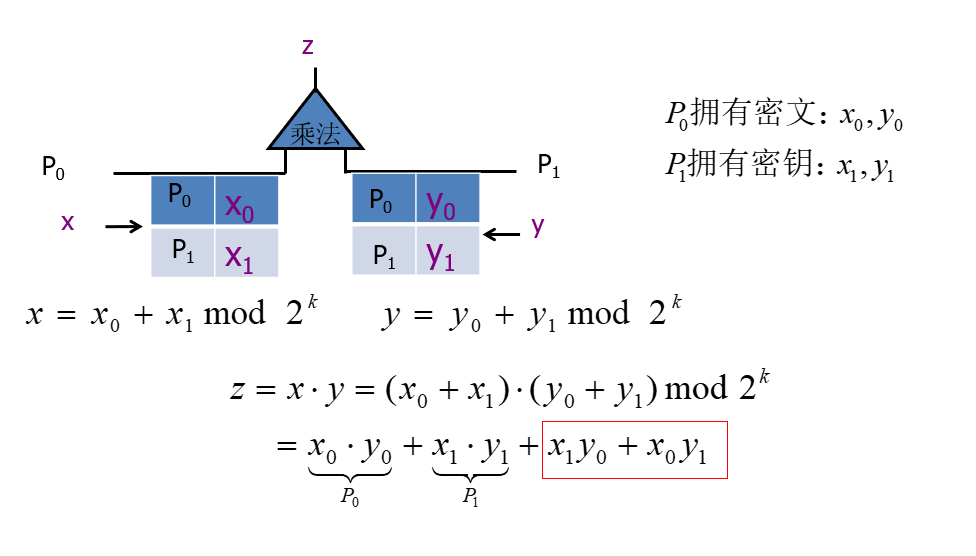
Obviously, like the GMW protocol, in addition to the part that can be calculated by itself, there will be more results that must be calculated through interaction. If the same OT protocol as Boolean sharing is used, there are many possible situations for each unknown data, and there are even more combinations of multiples. In order to protect privacy and cover the output of the sub-circuit, it is necessary to add a mask. Here, a multiplication triplet is used.
Beaver triples (multiplicative triples)
A construction paradigm of the MPC protocol : it is divided into a preprocessing stage when the input of the participant is unknown and an online stage when the input is selected by the participant . The preprocessing stage will generate some random quantities that have a certain correlation with each other for the participants. Participants can consume these random amounts during the online phase.
In the previous approach, we can see that the only real overhead in the protocol is the communication overhead in evaluating each multiplication gate, hence the adoption of triplets here shifts most of the communication to the preprocessing stage.
The so-called multiplication triplet, namely ab = c ab=cab=c, a a a andbbb is a random number randomly selected from the field, and each multiplication gate evaluation needs to consume a triplet
Step
Still consider two input gates x , yx,yx,y , an output gatezzThe multiplication gate of z , computingx ∗ y = zx * y = zx∗y=z , first add a mask to the two input values, that is, split the elements of the triplet in two ways. That isa = a 0 + a 1 , b = b 0 + b 1 a = a_0 + a_1,b=b_0+b_1a=a0+a1,b=b0+b1, Let the two parties hold a part respectively, notice that ab = ( a 0 + a 1 ) ( b 0 + b 1 ) = a 0 b 0 + a 0 b 1 + a 1 b 0 + a 1 b 1 ab=( a_0+a_1)(b_0+b_1)=a_0b_0+a_0b_1+a_1b_0+a_1b_1ab=(a0+a1)(b0+b1)=a0b0+a0b1+a1b0+a1b1, split it into two parts ( ab ) 0 (ab)_0(ab)0sum ( ab ) 1 (ab)_1(ab)1
The specific operation can call the method of homomorphic encryption, assuming that a homomorphic encryption algorithm (such as Paillier) is selected
- P 1 P_1 P1CalculateE ( a 1 ) , E ( b 1 ) E(a_1),E(b_1)And ( a1),E(b1) and send toP 0 P_0P0
- P 0 P_0 P0计算 E ( b 1 ) a 0 E ( a 1 ) b 0 E ( a 0 b 0 − a 1 b 1 ) = E ( a 0 b 0 + a 0 b 1 + a 1 b 0 − a 1 b 1 ) E(b_1)^{a_0}E(a_1)^{b_0}E(a_0b_0-a_1b_1)=E(a_0b_0+a_0b_1+a_1b_0-a_1b_1) E(b1)a0And ( a1)b0And ( a0b0−a1b1)=And ( a0b0+a0b1+a1b0−a1b1) toP 1 P_1P1
- P 1 P_1 P1just decrypt
- At this time (ab) 0 = a 1 b 1 (ab)_0=a_1b_1(ab)0=a1b1,而 ( a b ) 1 = a 0 b 0 + a 0 b 1 + a 1 b 0 (ab)_1=a_0b_0+a_0b_1+a_1b_0 (ab)1=a0b0+a0b1+a1b0
Currently two parts have xi , yi , ai , bi x_i,y_i,a_i,b_ixi,yi,ai,bi。
- 让x,yx,yx , y in a masked mannere = x + ae=x+ae=x+a和 f = y + b f= y+b f=y+b export, immediate releasexi + ai , yi + bi x_i+a_i,y_i+b_ixi+ai,yi+bi, so that both parties can locally calculate e , fe,fe,f
- Calculate xy = ( e − a ) ( f − b ) = ef − fa − eb + ab \begin{aligned} xy&=(ea)(fb)\\ &= ef-fa-eb+ab \end{aligned }xy=(e−a)(f−b)=ef−fa−eb+ab, then split it up and get ( xy ) 0 = − fa 0 − eb 0 + ( ab ) 0 ( xy ) 1 = ef − fa 1 − eb 1 + ( ab ) 1 \begin{array}{lcl} (xy)_0=-fa_0-eb_0+(ab)_0 \\ (xy)_1=ef-fa_1-eb_1+(ab)_1 \end{array}(xy)0=−fa0−eb0+(ab)0(xy)1=ef−fa1−eb1+(ab)1
- Cooperate with the previously calculated ( ab ) 0 (ab)_0(ab)0sum ( ab ) 1 (ab)_1(ab)1The result can be obtained locally.
multiplicative sharing
Shamir-based secret distribution scheme
= Still consider two input gates x , yx,yx,y , an output gatezzThe multiplication gate of z , computingx ∗ y = zx * y = zx∗y=z , intuitively, is essentiallythe ttMultiply polynomials of degree t , this will give a degree2 t 2t2 polynomial in t , assumed to be q ( x ) q(x)q ( x ) , the secret share of each participant is a point on this polynomialq ( i ) = [ vx ] [ vy ] q(i)=[v_x][v_y]q(i)=[vx][vy] (Note:[ ] [][ ] stands for( t , n ) (t,n)(t,n ) Shamir’s secret share), obviously recovering the correct result requires at least2 t + 1 2t+12t _+1 secret share, which already exceeds the threshold tt of the Shamir secret sharingschemet , so how to solve the threshold overflow problem? There is no doubt that the product polynomials need to be reduced in order. Note: The requirement 2 t + 1 < n 2t+1<n
needs to be met here2t _+1<n , that is, the security is based on the majority-honest assumption.
Goal: getq( 0 ) q(0)effective secret shares for q ( 0 ) with polynomial order not exceeding thresholdttt , so thatt + 1 t+1t+1 person can recover the secretq ( 0 ) q(0)q ( 0 ) .
The core idea: use the linear function of the secret share of the participants to expressq ( 0 ) = ∑ i = 1 2 t + 1 λ iq ( i ) q(0)=\sum^{2t+1}_{i=1} \lambda_i q(i)q(0)=∑i=12 t + 1liq ( i ) , which is a( t , n ) (t,n)(t,n ) share-to-additionttA form of t , that is,q ( 0 ) q(0)q ( 0 ) is converted to2 t + 1 2t+12t _+Sum of 1 secret share. Then the number of the participant is[ 1 , 2..2 t ] [1,2..2t][1,2..2 t ] such a growth method, addλ i \lambda_iliIs a value that can be calculated by knowing the number, then you can simulate 2 t + 1 2t+1 locally2t _+1 secret share for summing.
The specific step-down steps are as follows:
- First, each participant based on its own q ( i ) q(i)q ( i ) performs a Shamir's( t , n ) (t,n)(t,n ) secret share, and the corresponding secret share[q (i)] [q(i)][ q ( i )] is sent to other participants, that is, each participant sendsq ( i ) q(i)q ( i ) as secret and constant term, choose attThe t -order polynomial distributes the corresponding sub-secret shares to other participants.
- Each participant calculates locally [ q ( 0 ) ] = ∑ i = 1 2 t + 1 λ i [ q ( i ) ] [q(0)]=\sum^{2t+1}_{i=1} \lambda_i [q(i)][q(0)]=∑i=12 t + 1li[q(i)], [ q ( 0 ) ] [q(0)] [ q ( 0 )] represents the product secret valueq ( 0 ) q(0)The effective share of q ( 0 ) ,λ i \lambda_iliis the corresponding Lagrange coefficient.
At this time because [ q ( i ) ] [q(i)][ q ( i )] is a( t , n ) (t,n)(t,n ) sharing, then everyone calculates[ q ( 0 ) ] [q(0)][ q ( 0 )] is a( t , n ) (t,n)(t,n ) sharing. This completes the step-down operation.
Based on random input and triplet scheme (additive secret sharing)
Each party constructs triplets [ a ] [ b ] = [ c ] [a][b]=[c] for each multiplication gate[a][b]=[ c ] (Hold by oneself, other participants do not know, knowing ab, c is determined), each participant holds a secret share[ vx ], [ vy ] [v_x],[v_y][vx],[vy] (For each participant's input wire, a secret share will be randomly assigned, only the corresponding participant knows its value, andv = ∑ i = 1 n [ v ] v=\sum^n_{i=1}[v ]v=∑i=1n[ v ] ) want to calculate[vxvy][v_x v_y][vxvy]
(Note:[ ] [][ ] is the sub-secret share shared by addition, namelya = ∑ i = 1 n [ a ] , b = ∑ i = 1 n [ b ] a=\sum^n_{i=1}[a],b=\ sum^n_{i=1}[b]a=∑i=1n[a],b=∑i=1n[ b ] ), the calculation steps are as follows
- Each participant calculates locally [ d ] = [ vx − a ] [d] = [v_x - a][d]=[vx−a ] and publicly
- Each party computes locally [ e ] = [ vy − b ] [e] = [v_y - b][e]=[vy−b ] and publicly
- Then there is the following equation
v x v y = ( v x − a + a ) ( v y − b + b ) = ( d + a ) ( e + b ) = d e + d b + a e + a b = d e + d b + a e + c \begin{aligned} v_x v_y &=(v_x -a +a)(v_y-b+b) \\ &= (d+a)(e+b) \\ &= de+db+ae+ab \\ &= de+db+ae+c \end{aligned} vxvy=(vx−a+a)(vy−b+b)=(d+a ) ( e+b)=d e+db+ae+ab=d e+db+ae+c
d , e d,e d,e is disclosed, and[ a ] , [ b ] , [ c ] [a],[b],[c][a],[b],[ c ] Each participant holds, so each participant can calculate the secret share
[ vxvy ] = de + d [ b ] + e [ a ] + [ c ] [v_x v_y]=de+d[b]+ e[a]+[c][vxvy]=d e+d[b]+and [ to ]+[c]
reference
Introduction to Practical Secure Multi-Party Computation
Arithmetic Sharing