Generally speaking, after the version function test is completed, the corresponding use cases are also automated, and the performance, compatibility, and stability tests are also completed, we need to consider the security of the system, especially when it comes to transactions, payments, and user account information. modules, security vulnerabilities will bring extremely high risks.
one. Security testing principles and common security threats:
1. Security requirements:
※Authentication: Requests for authenticated users are returned
※Access control: authority control and data protection for unauthenticated users
※Integrity: The user must receive the information sent by the server accurately
※Confidentiality: information must be accurately delivered to the intended user
※ Reliability: How often does it fail? How long does it take for the network to recover from a failure? What steps are taken to deal with catastrophic failure? (Personally understand that this place should be more in the category of fault tolerance and disaster recovery testing)
※Non-repudiation: users should be able to prove that the received data comes from a specific server
2. Common security test content
access control
SQL injection
URL security test
XSS (Cross Site Scripting)
CSRF (Cross Site Request Forgery)
URL redirection vulnerability
Other Security Considerations
Next, we take a common MVC architecture website implemented by C# as an example to analyze specific security testing angles.
2. Authority control
Permission control is relatively simple, and I have been exposed to a lot during the functional testing process, mainly considering the following aspects:
1. User permissions: We assume that there are two users A and B; where A has a high permission level and B has a low permission level:
Only A can perform the operation, but B can not perform the operation;
Only A can see the page, B can not see it;
2. Page authority:
You must log in to see the page, can you directly access it without logging in?
A page that must be ABC, can it be directly AC?
Generally speaking, the simple authority control page test is not complicated, but because the authority control is closely integrated with subsequent URL jumps, sessions, etc., it is proposed separately.
3. URL redirection vulnerability
1. Implementation principle:
The server does not check and control the incoming redirection URL variable, which may lead to the malicious construction of any malicious URL and induce users to redirect to malicious websites.
Generally speaking, the test method for URL redirection is to modify the legal URL in the parameter to an illegal URL, and then check whether it can be redirected normally or whether the response packet contains any constructed URL.
2. Test method:
Modify the legal URL in the parameter to an illegal URL, and then check whether it can jump normally or whether the response packet contains any constructed URL
4. Considerations from other security perspectives
1. Installation package test: For programs on the C/S side, the installation package mainly considers decompilation, signature, integrity, permissions, etc.
2. Database: Sensitive fields in the database, such as user names and passwords, should be encrypted before storage; sensitive information such as cookies should also consider setting an expiration time, etc.;
3. Try not to include sensitive information in logs and configuration files
4. Account security: Encrypted storage of passwords in the database, encryption of transmitted passwords, locking of passwords after multiple input errors, processing of multi-device login, identity verification after logout, etc.
5. Considering the needs of the actual version: For example, an e-commerce APP, when submitting an order interface, the order information and the total amount of the order are passed in, and the payment interface pays according to the total amount passed in by the order submission interface; the problem is that the payment interface completely trusts If the order amount has not been verified, you can directly call the order interface to forge the amount to shop at a cheap price.
Network security learning resource sharing:
Zero-based entry
For students who have never been exposed to network security, we have prepared a detailed learning and growth roadmap for you. It can be said that it is the most scientific and systematic learning route, and it is no problem for everyone to follow this general direction.
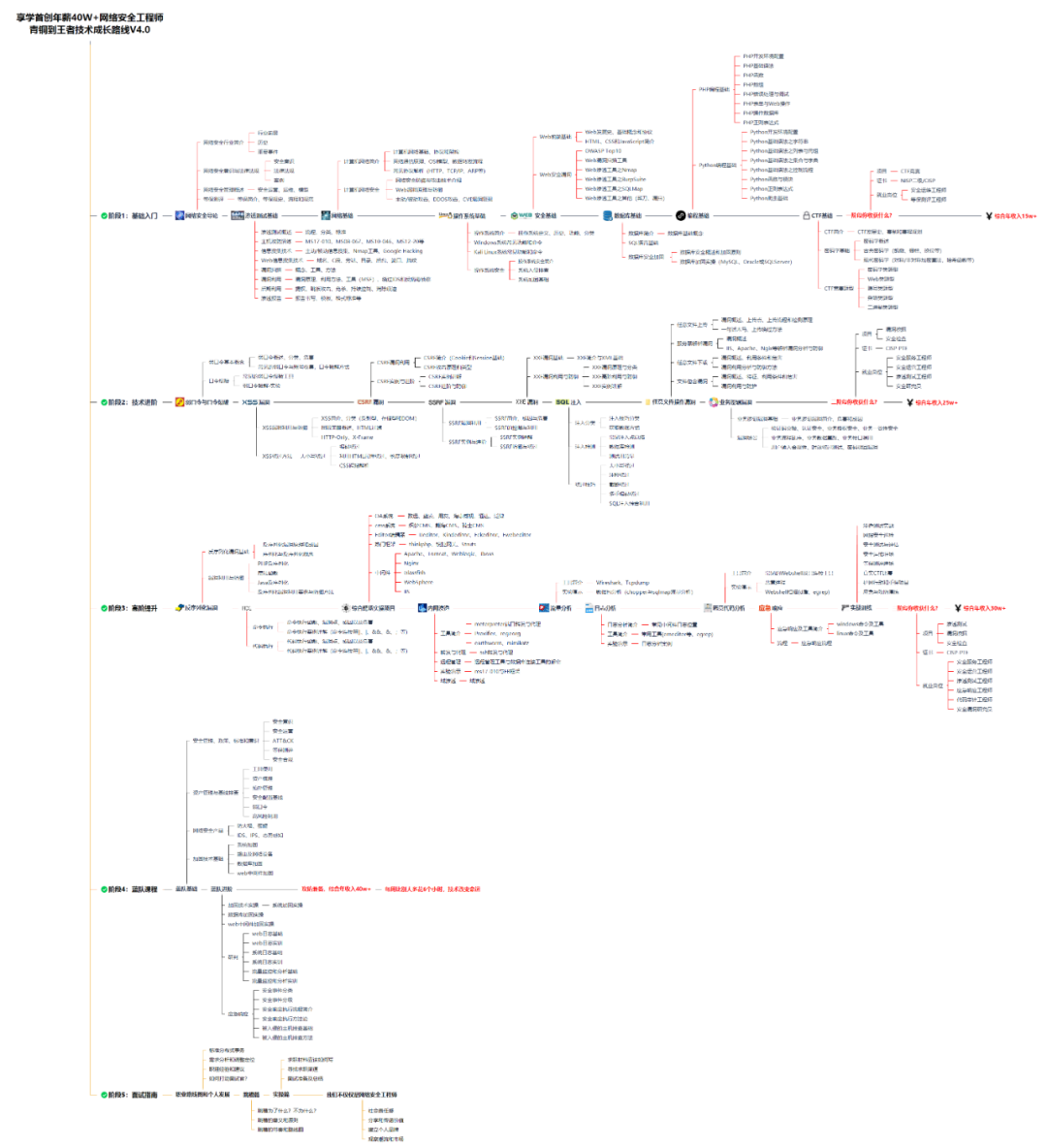
At the same time, there are supporting videos for each section corresponding to the growth route:
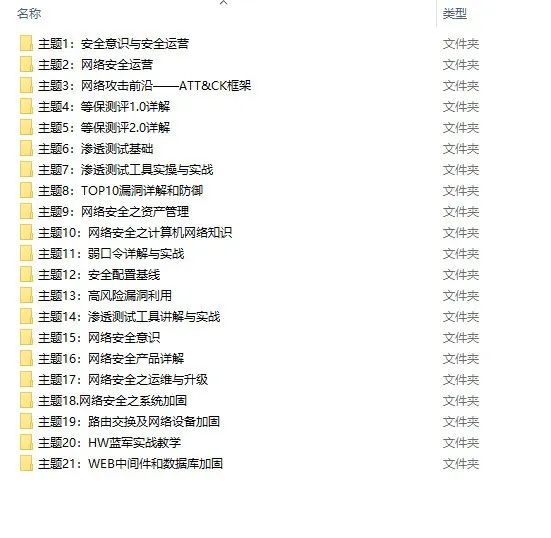
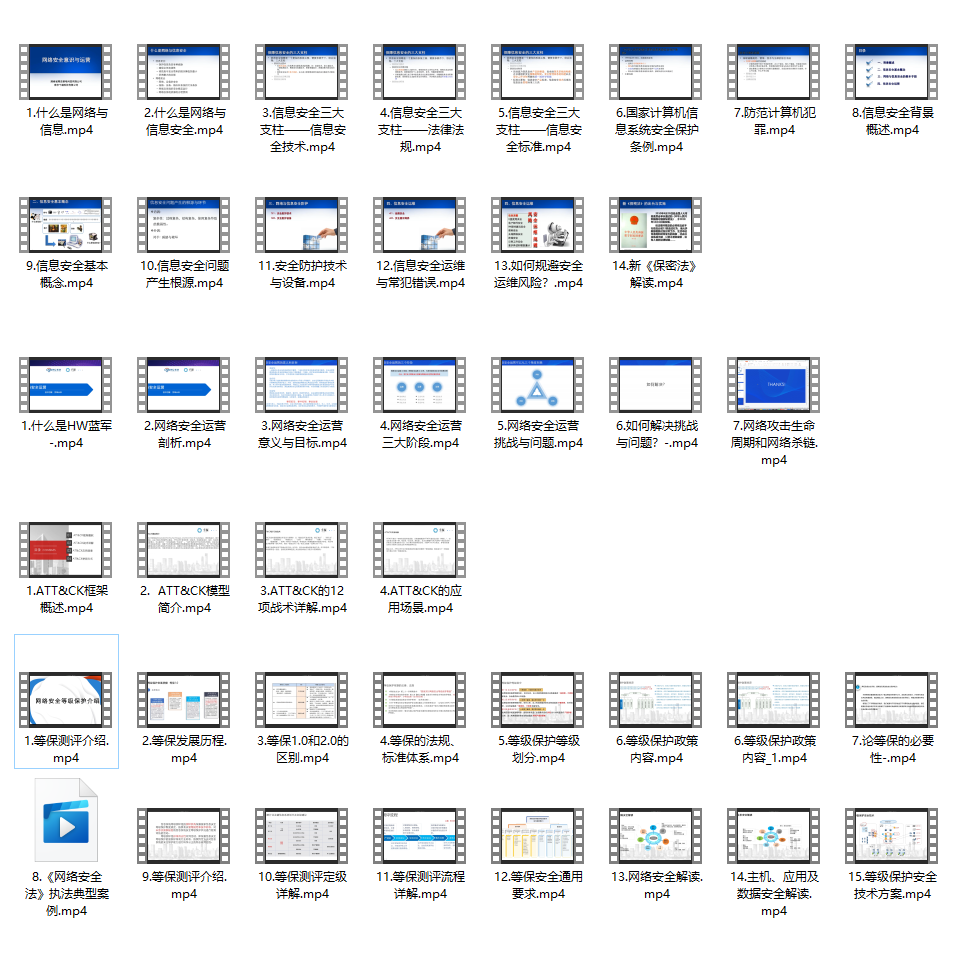
Due to the limited space, only part of the information is shown, you need to click the link above to get it