1. Unified authentication idea under the microservice architecture
Session-based authentication method:
In a distributed environment, there is a problem with session-based authentication. Each application service needs to store user identity information in the session. To distribute local requests to another application service through load balancing, session information needs to be brought over. , otherwise it will re-authenticate. We can use programs such as Session sharing and Session pasting.
The Session solution also has disadvantages, such as being based on cookies, the mobile terminal cannot be used effectively, etc.
Token-based authentication method
Based on the token authentication method, the server does not need to store authentication data, which is easy to maintain and has strong scalability. The client can store the token anywhere, and can realize the unified authentication mechanism of web and app. Its disadvantages are also obvious. Due to its self-contained information, the token generally has a large amount of data, and it needs to be transmitted every time it is requested, so it occupies a lot of bandwidth. In addition, the token signature verification operation will also bring additional processing load to the CPU.
2. OAuth2 open authorization protocol/standard
2.1 Introduction to OAuth2
OAuth (Open Authorization) is an open protocol/standard that allows users to authorize third-party applications to access their information stored on another service provider without providing usernames and passwords to third-party applications or sharing their data with all content.
Allows users to authorize third-party applications to access their information stored on another service provider without providing usernames and passwords to third-party applications or sharing all content of their data.
Combining the scene of "using QQ to log in to pull the hook" to split and understand the above sentence:
- User: ourselves
- Third-party application: Lagou.com
- Another service provider: QQ
- OAuth2 is a continuation of the OAuth protocol, but it is not backward compatible with OAuth1, that is, OAuth1 is completely abolished.
2.2, OAuth2 protocol role and process
If Lagou.com wants to develop and use the function of QQ login, then Lagou.com needs to register on the QQ platform in advance (otherwise, why should QQ accompany Lagou.com to play authorized logins).
- Lagou.com——Registration——>QQ Platform
- The QQ platform will issue some parameters to Lagou.com, and you need to carry these parameters when you go online for authorized login (just opened the authorization page?):
- client_id: client id (QQ is ultimately equivalent to an authentication and authorization server, and Lagou.com is equivalent to a client, so it will give a client id), which is equivalent to an account
- secret: equivalent to password
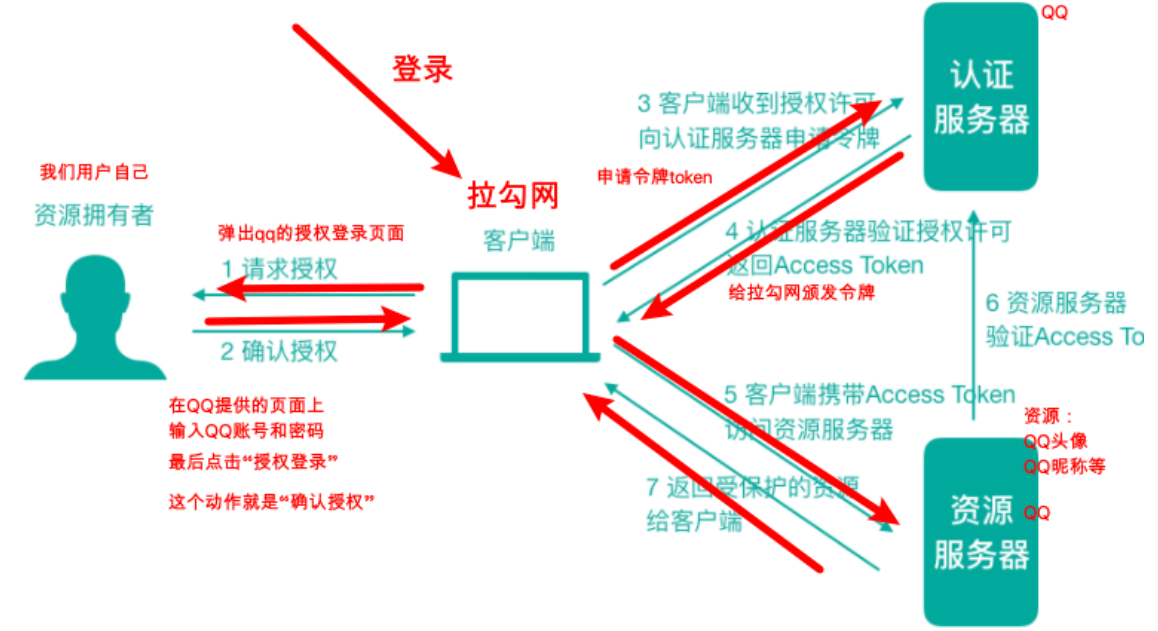
- Resource Owner: can be understood as the user himself
- Client (Client): the website or application we want to log in, such as Lagou.com
- Authentication Server (Authorization Server): can be understood as WeChat or QQ
- Resource Server (Resource Server): can be understood as WeChat or QQ
2.3. Under what circumstances should OAuth2 be used?
Scenarios for third-party authorized login : For example, when we often log in to some websites or applications, we can choose to use third-party authorized login methods, such as: WeChat authorized login, QQ authorized login, Weibo authorized login, etc. This is a typical OAuth2 scenes to be used.
Single sign-on scenario : If there are many microservices in the project or many services in the company, you can set up an authentication center (acting as the authentication platform role), and all services must go to this authentication center for authentication, only one login, You can freely serialize services within multiple authorized scopes.
2.4. Token authorization method of OAuth2
- Authorization code (authorization-code)
- Password (password) provide? Account name + password in exchange for token token
- hidden (implicit)
- client credentials
The callback address is used in the authorization code mode, which is the most complicated authorization method. Third-party logins such as Weibo, WeChat, and QQ are this mode. We focus on the password mode commonly used in interface docking (provide user name + password in exchange for token).