 Hacker, for many people, is a synonym for mystery. Coupled with the exaggerated artistic expression of film and television works, hackers, a group that originally only focused on technology, exude a mysterious color that is both righteous and evil.
Hacker, for many people, is a synonym for mystery. Coupled with the exaggerated artistic expression of film and television works, hackers, a group that originally only focused on technology, exude a mysterious color that is both righteous and evil.
Hacker comes from the word hacker in English. It used to refer to highly skilled computer experts who are enthusiastic about computer technology, especially programmers. They are gradually divided into white hats, gray hats, and black hats.
Among them, white hat hackers are called ethical hackers. They will not illegally invade the user network, but check the efficiency of the company's security system through a series of tests; black hat hackers are just the opposite of white hat hackers, they often destroy user network data for personal gain, so as to further commit cyber crimes; and Gray-hat hackers, who have both the attributes of white-hat and black-hat hackers, seek adequate compensation around benefits.
If you want to use the technology you have learned to make illegal profits, I advise you to give up as soon as possible. A gentleman loves money and obtains it in a proper way. If you want to become a qualified white hat hacker, you must abide by the "rules of the rivers and lakes".
Let's take a look at how to become a (white hat) hacker from scratch.

The early Internet was very monotonous, with only static pages. Now, with the development of technology, most sites on the web are actually web applications, which perform two-way information transmission between the server and the browser. They support logins, financial transactions, search, and user-generated content. Users only need to have a browser to realize various functions.
Web refers to the front-end page to back-end services of a website, such as our common Javascript, PHP, Python, Mysql, jQuery, Docker, etc., including development, operation and maintenance of these services.
So web security is a way of exploring the web from a security perspective.
In order to understand some common loopholes more easily, let's take a look at this test paper first:
Examination Paper
Candidate Name: Candidate Student Number:
1. Complementary poetry
The bright moonlight in front of the bed, . Chunmian does not feel dawn, .
2. Mathematical operations (fill in the numbers in brackets)
3500 + 400 * 3 / 2 + 1 =( )
4 ( 1 + 2) / 3 * 400 +500 = ( )
Candidate Name: __________
Candidate ID: __________
First of all, let's look at this, fill in the name and student number, is there a "loophole" here?
The answer is: yes.
The student's name and student number are written here, without any protection measures, so you only need to peek at this part of someone's test paper, and then write the name and student student number on your test paper as the same as his The same can be disguised as his identity.
The vulnerability attack was successful. Let's see the next one:
1. Complementary poetry
The bright moonlight in front of the bed, . Chunmian does not feel dawn, .
Is there a loophole in this question?
The answer is: yes.
The answers to this question should have been "Suspected to be frost on the ground" and "Smell birds singing everywhere"
However, there is no stipulation in the question that punctuation cannot be added to the answer. Therefore, I can completely put "Suspect is frost on the ground, raise your head to look at the bright moon, lower your head to think of your hometown" and "I hear birds singing everywhere, the sound of wind and rain at night, how much do you know about flowers falling?" "Write it in as an answer.
The vulnerability was successfully attacked again. Next:
2. Mathematical operations (fill in the numbers in brackets)
3500 +400 * 3 / 2 + 1 = ( )
4 ( 1 + 2) / 3 * 400 +500 = ( )
Is there a loophole in this question?
The answer is: yes.
The author of the question stipulated that only numbers can be filled in, but he didn’t say what the number is, nor how many digits, so my answer can be the Chinese number "one hundred one ten yuan", the Roman numeral "MCI" or the binary "0000000000001101 ".
The third attack of the loophole was successful.

This test paper simply simulates the idea of attacking web vulnerabilities. In practice, when we open a web page, submit login or search, we will go through a series of processing done by the server and then return to the browser. During this process, the data we submit will be into a series of filling-in-the-blank questions, some of which we can guess, some of which are unexpected, some of which will be filled in through SQL queries, and some will be brought into the command line for execution, and finally the The result is returned to the browser to fill in the blanks, which is the last result we see.
In data transmission, we can simply divide the web into several levels:
-
Browser: The browser is the client, providing data information interaction between the client and the server.
-
http: There is a web request when the client interacts with the web server. This request is based on a unified application layer protocol - the HTTP protocol to exchange data. HTTP is a lightweight protocol that requires no connection and provides fault tolerance for communication errors.
-
Middleware: Middleware are common services that sit between platforms (hardware and operating systems) and applications.
-
Server container: The Server container is responsible for parsing user requests and scripting languages, such as Tomcat, JBoss, etc. We visit the webpage and see the content processed by the web container.
-
Database: Dynamic pages can provide interactive information query services, mainly relying on the implementation of web databases, providing external web pages containing forms as access interfaces, and query results are also returned to users in the form of web pages containing data lists.
Of course, in addition to these data may also flow to some invisible third-party service providers.
The following figure shows the data transmission process, as well as the vulnerabilities that often occur at different stages and their causes:
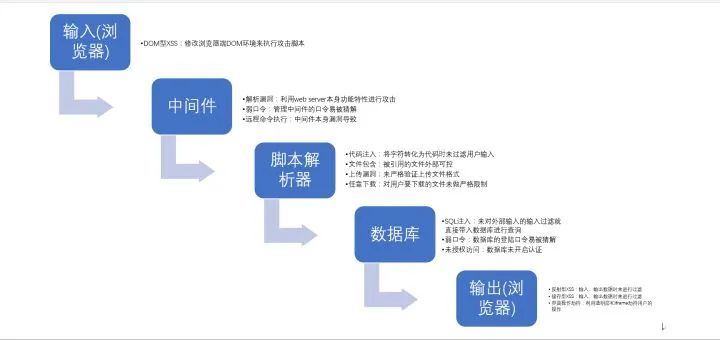
Our common types of web vulnerabilities mainly include SQL injection, XSS, remote command execution, and unauthorized access. Below we use examples to introduce these types of vulnerabilities for you.
(SQL injection)
The so-called SQL injection is to insert SQL commands into Web forms to submit or input query strings for domain names or page requests, and finally trick the server into executing malicious SQL commands.
- select * from username = ____ and password=_____
- select * from username “test” or “”=“” and password=“123456”
(XSS)
XSS is when an attacker inserts malicious script code into a web page. When the user browses the page, the script code embedded in the web will be executed, thereby achieving the purpose of maliciously attacking the user.
-
Hello, dear ______
-
hello, dear xxx
(remote command execution)
The remote command execution is that the user submits the execution command through the browser, because the server does not filter the execution function, resulting in the execution of the command.
- ping _______
- ping www.baidu.com & wget xxxxxxxxxxx
(overreach)
Unauthorized vulnerability is a relatively common type of vulnerability. It can be understood that a normal user A can only add, delete, modify and check some of his own information, but due to the momentary negligence of the programmer, there is no A judgment is made to determine whether the information to be operated belongs to the corresponding user, which may cause user A to operate other people's information.
- Cookie: uid=11426;
- Cookie: uid=1;
Regarding ultra vires, it is just like the name part in the body of the test paper.
Then show a flow chart of data transmission, so as to intuitively and clearly see how data works in each layer and possible loopholes:
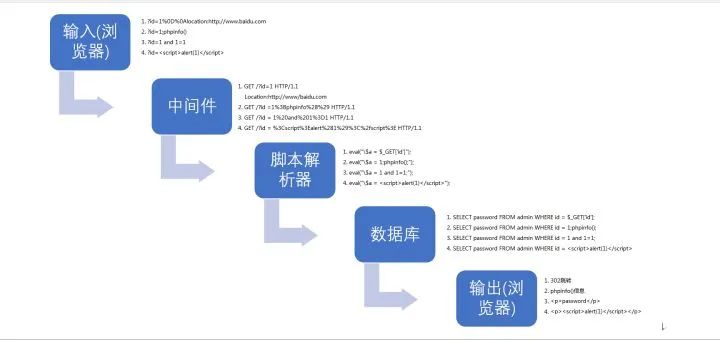
After understanding these vulnerabilities, we can see that the principles are somewhat similar and very simple. Of course, as long as we no longer limit ourselves to conceptual nouns, we will find that most of the vulnerabilities in web security are very simple. More often than not, finding a complex vulnerability requires nothing more than patience. Concept is not a sacred thing, and concept is often just bullshit. Many concepts arise because of the need to recognize and generalize some existing phenomenon. Concepts may be necessary but not necessarily so.
In other words, concepts can only be seen as one of the results of an effort to describe. Or it can also be said that the concept is the product of the self-promotion of the person who proposed the concept, and has little to do with other people. Even, some concepts are invented with 'ulterior motives' to rationalize certain phenomena that do not need to be rationalized but exist.
So don't stick yourself to such a concept to think about the essence of the problems you are facing. Only by forgetting the concept can you see clearly the relationship between you and the thing itself.
Where to start with no foundation at all? It is difficult to learn web security without a foundation at all, so the suggestions are as follows:
1. Tools
2. Use AWVS to scan several test websites to get a general understanding
http://testphp.vulnweb.com/http://testhtml5.vulnweb.com http://testasp.vulnweb.comhttp://testaspnet.vulnweb.com
3. Reproduce the scanned vulnerabilities and learn how to use them. Mainly understand: XSS, SQL injection, remote code execution
4. The book "Detailed PHP"
5. Use PHP to write a script that lists directories, and you can list any directory through parameters
6. Use PHP to grab the content of a web page and output it
7. Use PHP to grab the content of a web page and write it to the Mysql database and then output
8. Manually find the loopholes in http://testphp.vulnweb.com/, and compare the results of AWVS
9. Books "Hacker Attack and Defense—Detailed Explanation of Web Security Practical Combat" and "The Road to Security: Analysis of Web Penetration Technology and Practical Cases (2nd Edition)"
10. If you still can't read it, find a book on Web security that you can read.

In addition, this is a path of persistence, and the three-minute enthusiasm advises you to give up as soon as possible; practice more and think more, don't leave the tutorial and don't know anything. It is best to complete the technical development independently after reading the tutorial.
Internet Security & Hacking Learning Resource Sharing:
Share with you a complete set of network security learning materials, and give some help to those who want to learn network security!
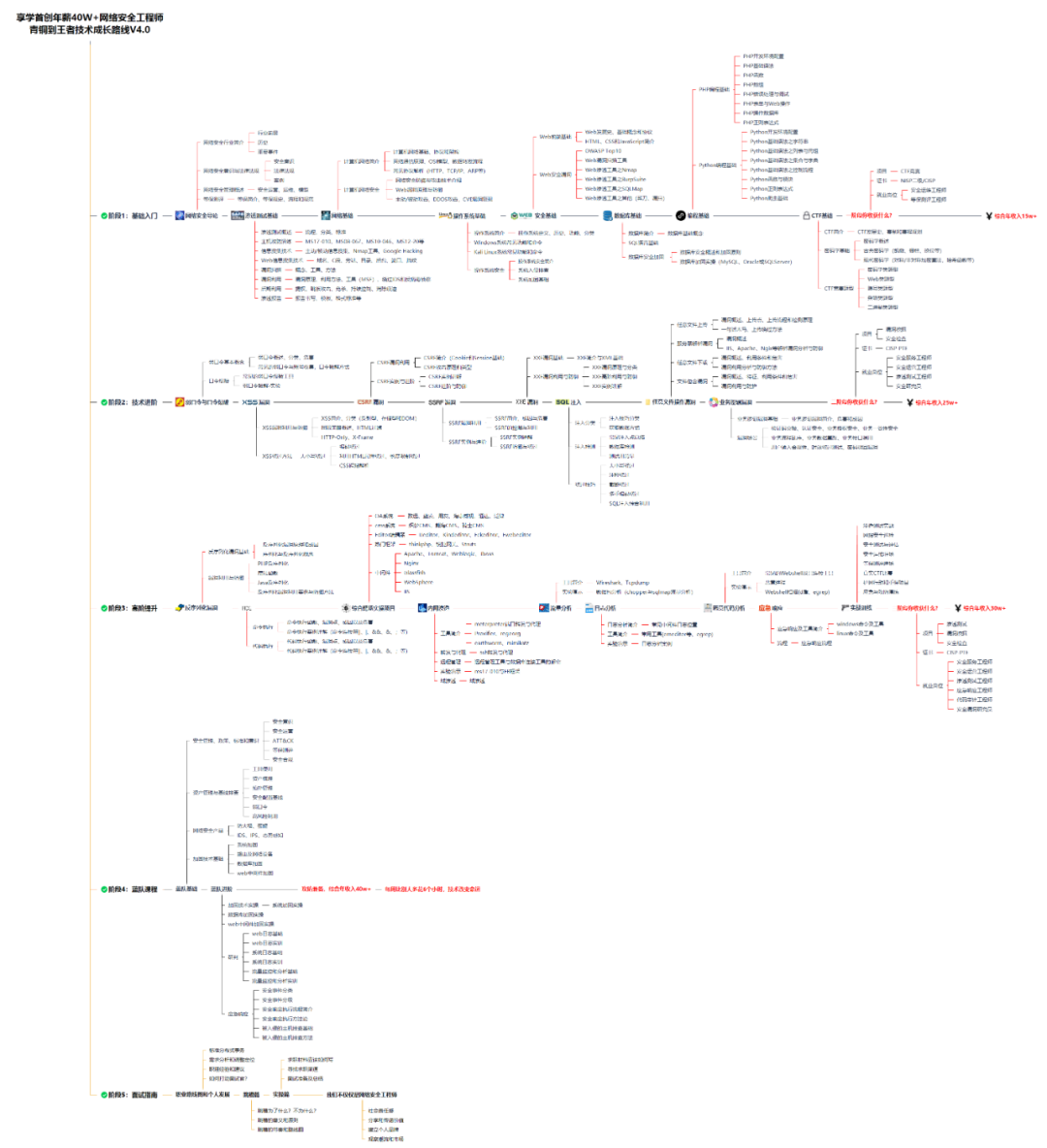
For students who have never been exposed to network security, we have prepared a detailed learning and growth roadmap for you. It can be said that it is the most scientific and systematic learning route, and it is no problem for everyone to follow this general direction.
Due to the limited space, only part of the information is displayed, friends, if necessaryA full set of " Introduction to Network Security + Advanced Learning Resource Pack ",needClick on the link belowYou can go to get
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing
At the same time, there are supporting videos for each section corresponding to the growth route:
Due to the limited space, only part of the information is displayed, friends, if necessaryA full set of " Introduction to Network Security + Advanced Learning Resource Pack ",needClick on the link belowYou can go to get
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing
Video supporting materials & domestic and foreign network security books and documents
Of course, in addition to supporting videos, we also organize various documents and books for you.
All the data is 282G in total , if you need it, friendsA full set of " Introduction to Network Security + Advanced Learning Resource Pack ",needClick on the link belowYou can go to get
CSDN spree: "Hacker & Network Security Introduction & Advanced Learning Resource Pack" free sharing