Network troubleshooting commands
window
Ping is a special term for submariners, which means echoing sonar pings. Ping is a very useful TCP/IP tool in the network. Its main function is to detect network connectivity and analyze network speed.
Parameter explanation:
We enter "ping/?" and press Enter to display some parameters of ping. Let me explain the meaning and use of each parameter:
ping [-t] [-a] [-n count][-l length] [-f] [-i ttl] [-v tos] [-r count] [-s count] [-j computer-list] |[-k computer-list] [-w timeout] destination-list
-t Ping the specified computer until interrupted.
-a Resolve addresses to computer names.
-n count Send the number of ECHO packets specified by count. The default value is 4.
-l length Send an ECHO packet containing the amount of data specified by length. The default is 32 bytes; the maximum value is 65,527.
-f Send a "don't fragment" flag in the packet. The packet will not be fragmented by the gateway on the route.
-i ttl Set the "time to live" field to the value specified by ttl.
-v tos Set the "Type of Service" field to the value specified by tos.
-r count Record the route of outgoing and return packets in the "record route" field. count can specify a minimum of 1 and a maximum of 9 computers.
-s count Specifies the timestamp for the number of hops specified by count.
-j computer-list Route packets using the list of computers specified by computer-list. Consecutive computers can be separated by intermediate gateways (routing sparse source) The maximum number of IPs allowed is 9.
-k computer-list Route packets using the list of computers specified by computer-list. Consecutive computers cannot be separated by intermediate gateways (routing strict source) The maximum number of IPs allowed is 9.
-w timeout Specifies the timeout interval in milliseconds.
destination-list Specifies the remote computers to ping.
Use ping IP address
tracert can list the routing nodes that the packet passes through, and the delay of each hop in the IP network. (The delay here refers to: the time required for the packet to be sent from the information source to the destination, and the delay is also divided into many types - propagation delay, transmission delay, processing delay, queuing delay, etc., which is one of the bottlenecks of most website performance one)
parameter
The format of the tracert command is: tracert [-d] [-h maximum_hops] [-j host-list] [-w timeout] [-R] [-S srcaddr] [-4] [-6] target_name.
①, -d means not to resolve the address into a host name.
②, -h maximum_hops indicates the maximum number of hops to search for the target.
③, -j host-list indicates loose source routing together with the host list (only applicable to IPv4).
④, -w timeout indicates the timeout (in milliseconds) for waiting for each reply.
⑤, -R means to track the round-trip path (only applicable to IPv6).
⑥, -S srcaddr indicates the source address to be used (only applicable to IPv6).
⑦, -4, and -6 indicate mandatory use of IPv4 or IPv6.
⑧, target_name indicates the name or IP address of the target host.
Curl is mainly used to interact data with web servers; common functions include uploading and downloading files, accessing server pages
Function
The curl command is a powerful network tool. It can download files through http, ftp, etc., and can also upload files. It also supports many protocols such as HTTPS, and also supports POST, cookies, authentication, and downloading partial files from specified offsets. , user agent string, speed limit, file size, progress bar and other features. In fact, curl is far more than the functions mentioned above. You can read the man page through man curl to get more information. A similar tool is wget. The curl command is implemented using the libcurl library. The libcurl library is often used in C programs to process HTTP requests. curlpp is a C++ package of libcurl. These things can be used in the development of web crawling, network monitoring, etc., and curl Commands can help to troubleshoot problems encountered during development.
-a/–append When uploading files, append to the target file
-A/–user-agent Set the user agent to send to the server
- anyauth can use "any" authentication method
-b/--cookie <name=string/file> cookie string or file read location - basic Use HTTP basic authentication
-B/–use-ascii Use ASCII/text transmission
-c/–cookie-jar Write the cookie to this file after the operation is over
-C/–continue-at breakpoint continuation
-d/– data HTTP POST to transmit data
–data-ascii post data in ascii mode
–data-binary post data in binary mode
–negotiate use HTTP authentication
–digest use digital authentication
–disable-eprt prohibit the use of EPRT or LPRT
–disable- epsv prohibits the use of EPSV
-D/–dump-header write header information to the file
–egd-file set EGD socket path for random data (SSL)
–tcp-nodelay use TCP_NODELAY option
-e/–referer source URL
-E /–cert <cert[:passwd]> client certificate file and password (SSL)
–cert-type certificate file type (DER/PEM/ENG) (SSL)
–key private key file name (SSL)
–key-type private Key file type (DER/PEM/ENG) (SSL)
–pass private key password (SSL)
–engine encryption engine to use (SSL). “–engine list” for list
–cacert CA certificate (SSL)
–capath CA directory (made using c_rehash) to verify peer against (SSL)
–ciphers SSL password
–compressed requires the return to be compressed (using deflate or gzip)
–connect-timeout set the maximum request time
– create-dirs Create a directory hierarchy of the local directory
–crlf upload is to convert LF to CRLF
-f/–fail do not display http errors when the connection fails
–ftp-create-dirs Create a remote directory if it does not exist
–ftp-method [multicwd/nocwd/singlecwd] Control the use of CWD
–ftp-pasv use PASV/EPSV instead of port
–ftp-skip-pasv-ip When using PASV, ignore the IP address
–ftp-ssl try to use SSL/TLS for ftp Data transmission
–ftp-ssl-reqd requires SSL/TLS for ftp data transmission
-F/–form <name=content> simulates http form submission data
-form-string <name=string> simulates http form submission data
-g/ --globoff disable URL sequences and ranges use {} and []
-G/--get send data as get
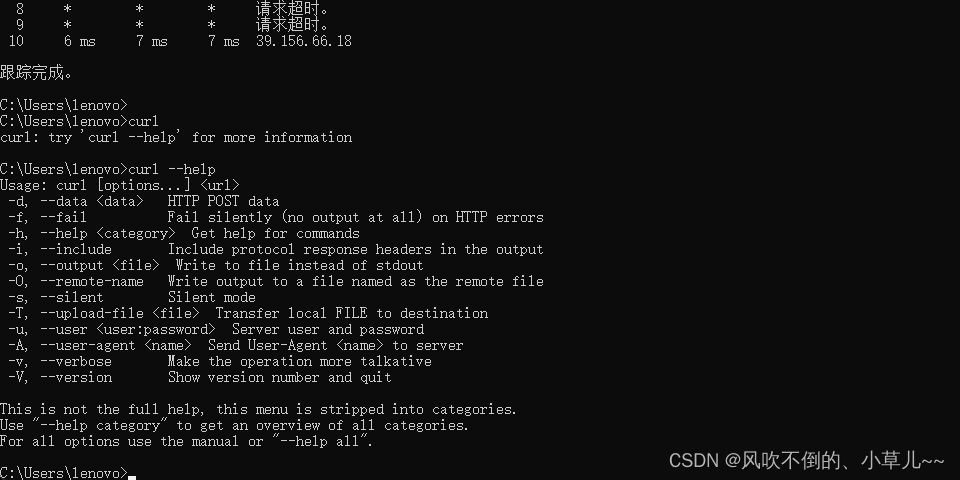
-h/--help help
-H/–headerPass custom header information to the server
--ignore-content-length length of ignored HTTP header information
-i/--include include protocol header information in output
-I/--head only display document information read
from file -j/--junk -session-cookies ignore session cookies - interface specifies the network interface/address to use
- krb4 <level> Enable with specified security level krb4
-j/–junk-session-cookies read file into ignore session cookie
–interface use specified network interface/address
–krb4 use specified security level krb4
-k/–insecure allow not Use the certificate to the SSL site
-K/–config specify the configuration file read
-l/–list-only list the file names in the ftp directory
–limit-rate set the transmission speed
–local-port force the use of the local port number
-m/ –max-time set the maximum transfer time
–max-redirs set the maximum number of read directories
–max-filesize set the maximum total number of downloaded files
-M/–manual display all manual
-n/–netrc read users from the netrc file name and password
--netrc-optional use .netrc or URL to override -n
--ntlm use HTTP NTLM authentication
-N/--no-buffer disable buffered output
-o/--output write output to this file
-O/--remote- name write output to this file, keeping the filename of the remote file
-p/ --proxytunnel use HTTP proxy
--proxy-anyauth choose any proxy authentication method
--proxy-basic use basic authentication on proxy
--proxy-digest use digital authentication on proxy
--proxy-ntlm use ntlm authentication on proxy
-P/ --ftp-portUse port address instead of PASV
-Q/–quote Before file transfer, send command to server
-r/–range Retrieve
random file from HTTP/1.1 or FTP server byte range –range-file Read (SSL)
– R/–remote-time When generating files locally, keep the remote file time
–retry When there is a problem with the transmission, the number of retries
–retry-delay When there is a problem with the transmission, set the retry interval
–retry-max-time There is a problem with the transmission When, set the maximum retry time
-s/--silent silent mode. print nothing
-S/ --show-error show errors
--socks4 <host[:port]> proxy given host and port with socks4
--socks5 <host[:port]> proxy given host and port with socks5
--stderr
- t/–telnet-option <OPT=val> Telnet option setting
–trace debug the specified file
–trace-ascii Like –trace but no hex output
–trace-time add timestamp when tracing/detailed output
-T/– upload-file Upload file
–url Spet URL to work with
-u/–user <user[:password]> Set server user and password
-U/–proxy-user <user[:password]> set proxy username and password
-v/–verbose
-V/–version display version information
-w/–write-out [format] what to output after completion
-x/– proxy <host[:port]> Use HTTP proxy on given port
-X/--request specify what command
-y/--speed-time Time to drop speed limit. Default is 30
-Y/--speed-limit stop transmission speed limit, speed time 'seconds'
-z/--time-cond transmission time setting
-0/--http1.0 use HTTP 1.0
-1/--tlsv1 use TLSv1 (SSL)
-2/–sslv2 use SSLv2 (SSL)
-3/–sslv3 use SSLv3 (SSL)
–3p-quote like -Q for the source URL for 3rd party transfer
–3p-url use url for third party transfer
–3p -user use username and password for third-party transfer
-4/–ipv4 use IP4
-6/–ipv6 use IP6
-#/–progress-bar use progress bar to display current transfer status
use
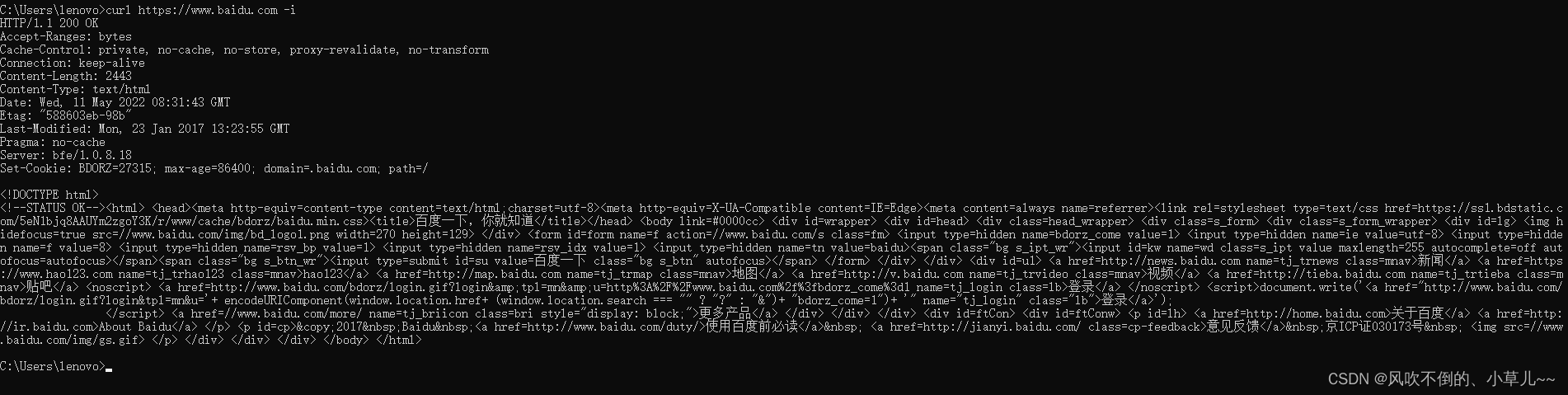
curl https://www.baidu.com -i
-i to view header information
Telnet is used to remotely log in to a computer on the network to check whether a certain port is available
Common commands for Telnet client commands:
open: Use openhostname to establish a Telnet connection to the host.
close : Use the command close to close the existing Telnet connection.
display : Use the display command to view the current settings of the Telnet client.
send : Use the send command to send commands to the Telnet server. The following commands are supported:
ao : Abort the output command.
ayt : "Are you there" command.
esc : Send the current escape character.
ip : Interrupt process command.
synch : Perform a Telnet synchronization operation.
brk : Send a signal.
quit : Use the quit command to exit the Telnet client.
All commands other than those listed in the above table will be sent to the Telnet server as strings. For example, send abcd will send the string abcd to the Telnet server so that it will appear in the Telnet session window.
Telnet is used to remotely log in to computers on the network, and remotely manage computers through the command line. It should be noted that the remote machine must start the telnet server, otherwise the telnet command cannot be opened.
For example: Enter "telnet 114.80.67.193" in the command prompt and press the Enter key, but for safety reasons, you need to enter "n" and press the Enter key, and a login prompt will appear. After entering the login name, press the Enter key to log in to the remote machine.
Use the open subcommand of telnet to remotely log in to the remote machine. Command format: open hostname[port], hostname is ip address, port is 23 by default. Enter "open 114.80.67.193" at the telnet prompt and press Enter. Enter "n" again, and enter the user name and password according to the prompt to log on to the remote machine.
Use the unset subcommand of telnet to disable the local echo function. Operation process: first enter "telnet" in the command prompt and press the Enter key; then enter "setlocalecho" and press the Enter key to enable the local echo function; if you want to disable the echo function, just enter the telnet command prompt Enter "unsetlocalecho" after the symbol, and press Enter.
use
telnet ip port: Check whether a certain port on a certain machine can be accessed, such as: telnet 114.80.67.193 8080
Exit command: exit—exit the dos window,
q!,wq—exit vi editor
ctrl+] under Linux, and then press q—quit from the telnet interface
quit—quit...
telnet is mainly used for remote login, I only use it simply, please find the information yourself for details
The netstat command checks whether a certain port number is occupied and which process is occupied
use
netstat -ano
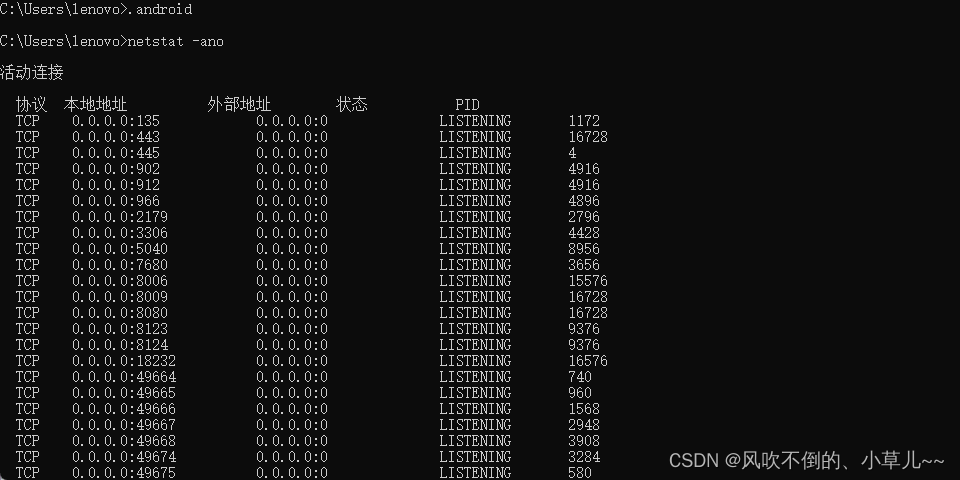
can filter and find netstat -ano|findstr 8080

parameter
Displays protocol statistics and current TCP/IP network connections.
NETSTAT [-a] [-b] [-e] [-n] [-o] [-p proto] [-r] [-s] [-t] [-v] [interval]
-a Displays all connections and listening ports. -b Displays the executables
included in creating each connection or listening port .
In some cases the executable is known
to have multiple independent components, and in these cases
the sequence of components involved in creating a connection or listening to a port
is displayed. In this case, the executable component name
is in [] at the bottom, the component it calls at the top,
and so on, up to the TCP/IP section. Note that this option may take a long time and may fail
if you do not have sufficient permissions . -e Display Ethernet statistics. This option can be used in combination with the -s option. -n Displays addresses and port numbers numerically. -o Displays the owning process ID associated with each connection. -p proto Display connections for the protocol specified by proto; proto can be one of the following protocols: TCP, UDP, TCPv6, or UDPv6. If used with the -s option to display statistics by protocol, proto can be one of the following protocols: IP, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, or UDPv6. -r Displays the routing table. -s Display statistics by protocol. By default, statistics for IP, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, and UDPv6 are displayed; the -p option is used to specify a subset of the default. -t Display current connection offload status. -v when used with the -b option will display the
Component that creates connection or listening ports for all executable components
.
interval Redisplays the selected statistics,
pausing the interval in seconds between each display. Press CTRL+C to stop redisplaying
statistics. If omitted, netstat displays current
configuration information (only once)
tasklist command displays a list of currently running processes on a computer
The tasklist command displays a list of currently running processes on the local computer or on a remote computer. Commands are used in conjunction with filters to filter according to our needs and find the process information we need to know. tasklist replaces the tlist.exe tool.
Usage: tasklist [/s [/u [] [/p ]]] [{/m | /svc | /v}] [/fo {table | list | csv}] [/nh] [/fi [/fi [ … ]]]
Parameter list:
/S system Specifies the remote system to connect to.
/U [domain]user Specifies which user to use to execute this command.
/P [password] Specifies a password for the specified user.
/M [module] Lists all processes calling the specified DLL module.
If no module name is specified, display all modules loaded by each process.
/SVC Displays services in each process.
/V Specifies that verbose information be displayed.
/FI filter Displays a list of processes matching the filter specified.
 .Use the filter to find the specified process
.Use the filter to find the specified process
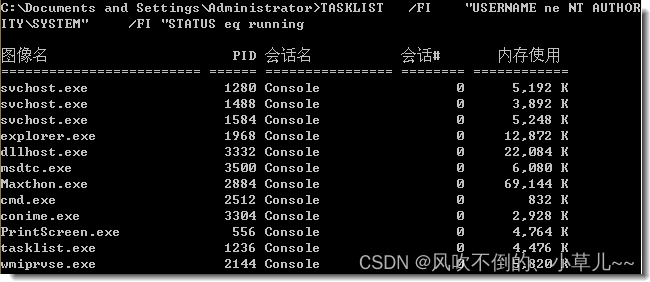
Enter at the command prompt: TASKLIST /FI "USERNAME ne NT AUTHORITY\SYSTEM" /FI "STATUS eq running"
This will list all processes running in the system that are not "SYSTEM" .
taskkill Use this tool to kill tasks by process ID (PID) or image name.
TASKKILL [/S system [/U username [/P [password]]]]
{ [/FI filter] [/PID processid | /IM imagename] } [/T] [/F]
parameter
/S system Specifies the remote system to connect to.
/U [domain]user Specifies the user context under which this command should be executed.
/P [password] Specifies a password for the provided user context. If omitted, prompts for input.
/FI filter Applies a filter to select a set of tasks. " " is allowed . For example, image_name eq acme
/PID processid specifies the PID of the process to be terminated. Use TaskList to get PID.
/IM imagename Specifies the image name of the process to be terminated. The wildcard '*' can be used to specify all task or image names.
/T Terminates the specified process and child processes enabled by it.
/F Specifies to forcefully terminate the process.
/? Displays a help message.
filter
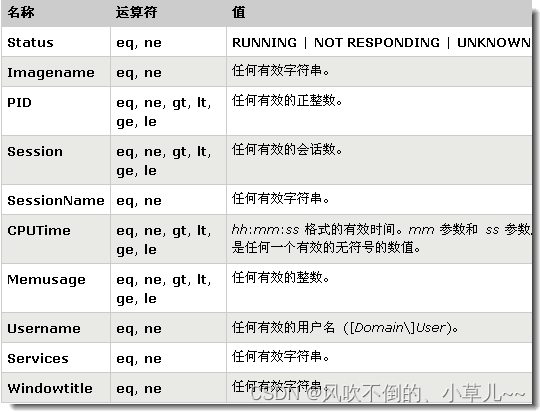
Filter Name Valid Operators Valid Values
STATUS eq, ne RUNNING
NOT RESPONDING
IMAGENAME eq, ne Image Name
PID eq, ne, gt, lt, ge, le Value
SESSION eq, ne, gt, lt, ge, le Session Number
CPUTIME eq , ne, gt, lt, ge, le CPU time
MEMUSAGE eq, ne, gt, lt, ge, le Memory usage in KB
USERNAME eq, ne User name in format [domain]user
MODULES eq, ne DLL name
SERVICES eq, ne service name
WINDOWTITLE eq, ne window title
说明
1) 只有在应用筛选器的情况下,/IM 切换才能使用通配符 '*'。
2) 远程进程总是要强行 (/F) 终止。
3) 当指定远程机器时,不支持 "WINDOWTITLE" 和 "STATUS" 筛选器。
TASKKILL /IM notepad.exe
TASKKILL /PID 1230 /PID 1241 /PID 1253 /T
TASKKILL /F /IM cmd.exe /T
TASKKILL /F /FI "PID ge 1000" /FI "WINDOWTITLE ne untitle*"
TASKKILL /F /FI "USERNAME eq NT AUTHORITY\SYSTEM" /IM notepad.exe
TASKKILL /S system /U 域\用户名 /FI "用户名 ne NT*" /IM *
TASKKILL /S system /U username /P password /FI "IMAGENAME eq note*"
ipconfig to view network information
ipconfig view network information
ipconfig/all view all network information
lion
traceroute is a tool used to detect the number of gateways passed between the sending host and the target host.
Use
traceroute www.baidu.com
to introduce
the principle of traceroute is to try to send a probe packet with the smallest TTL (time to live) to track the gateway through which the data packet reaches the target host, and then listen for an ICMP response from the gateway. The send packet size defaults to 38 bytes.
Principle: The program realizes its function by increasing the time to live (TTL). Whenever a data packet (3 data packets including the source address, destination address and time stamp when the packet is sent) passes through a router, its lifetime will be decremented by 1. When its survival time is 0, the host cancels the data packet and sends an ICMP (Internet Control Message Protocol. It is a sub-protocol of the TCP/IP protocol family, used to transmit control messages between IP hosts and routers. The control message refers to the message of the network itself, whether the network is unreachable, whether the host is reachable, whether the route is available, etc. Although these control messages do not transmit user data, they play an important role in the transmission of user data.) TTL data packets to the original sender of the packet.
The complete process of the traceroute program: first, it sends an IP packet with a TTL field of 1 to the destination host, and the first router that processes the packet reduces the TTL value by 1, then discards the datagram, and sends an ICMP packet to the source host. message ("timeout" information, this message contains the IP address of the router, so that the address of the first router is obtained), and then traceroute sends a datagram with a TTL of 2 to obtain the IP address of the second router, This process continues until the datagram reaches the destination host.
1. Command format:
traceroute [parameters] [host]
2. Command function:
The traceroute command allows you to trace the routing path of network data packets. The default data packet size is 40Bytes, and the user can set it separately.
Specific parameter format: traceroute [-dFlnrvx][-f<survival value>][-g<gateway>…][-i<network interface>][-m<survival value>][-p<communication port>][ -s<source address>][-t<service type>][-w<timeout seconds>][host name or IP address][packet size]
3. Command parameters:
-d Use the debugging function at the Socket level.
-f Set the size of the survival value TTL of the first detection packet.
-F Sets the do-not-break bit.
-g Set the source routing gateway, up to 8 can be set.
-i Send packets using the specified network interface.
-I Use ICMP responses instead of UDP data messages.
-m Set the size of the maximum survival value TTL of the detection packet.
-n Use the IP address directly instead of the hostname.
-p Set the communication port of the UDP transport protocol.
-r Ignore the ordinary Routing Table, and send the data packet directly to the remote host.
-s Set the IP address of the local host to send out packets.
-t Set the TOS value of the detection packet.
-v Displays the execution of the command in detail.
-w Set the time to wait for the report from the remote host.
-x Turns on or off the correctness check of the data packet.
ip addr View network configuration information
nslookup is used to query DNS records, check whether the domain name resolution is normal, and is used to diagnose network problems when the network fails
nslookup domain [dns-server]
//如果没有指定dns服务器,就采用系统默认的dns服务器。
nslookup -qt = type domain [dns-server]
type:
A -->地址记录
AAAA -->地址记录
AFSDB Andrew -->文件系统数据库服务器记录
ATMA -->ATM地址记录
CNAME -->别名记录
HINHO -->硬件配置记录,包括CPU、操作系统信息
ISDN -->域名对应的ISDN号码
MB -->存放指定邮箱的服务器
MG -->邮件组记录
MINFO -->邮件组和邮箱的信息记录
MR -->改名的邮箱记录
MX -->邮件服务器记录
NS --> 名字服务器记录
PTR ->反向记录
RP -->负责人记录
RT -->路由穿透记录
SRV -->TCP服务器信息记录
TXT -->域名对应的文本信息
X25 -->域名对应的X.25地址记录
More detailed information query
nslookup -d [其他参数] domain [dns-server]
//只要在查询的时候,加上-d参数,即可查询域名的缓存