Business Security for Web Attack and Defense: Callback Custom Test

Business security refers to measures or means to protect business systems from security threats. Business security in a broad sense should include the software and hardware platforms (operating systems, databases, middleware, etc.) that run the business, the business system itself (software or equipment), and the security of services provided by the business ; business security in the narrow sense refers to the business system’s own software. and service security .
Table of contents:
Step 2: Find the link with the callback parameter in the URL.
Disclaimer:
It is strictly forbidden to use the technology mentioned in this article to carry out illegal attacks, otherwise the consequences will be at your own risk, and the uploader will not bear any responsibility.
Callback custom test:
Test principle and method:
There is a same-origin policy in the browser. The so-called same-origin refers to the same domain name, protocol, and port. When using Ajax to transmit data asynchronously, there are restrictions between non-same-origin domain names. One of the solutions is JSONP (JSON with Padding). The basic principle uses the <script> </script> element tag in HTML to remotely call the JSONP file To achieve data transfer, the Callback (callback function) parameter is generally used in JSONP technology to declare the function name used when calling back. There are often security issues here. Because there is no whitelist method to limit the Callback function name, the attacker can automatically Define the content of Callback to trigger vulnerabilities such as XSS.
Testing process:
Before the test, the attacker uses the crawler function of Burp Suite to crawl the website and screens out requests with Callback or JSONP parameters. Please judge the Content-Type of the request response . If the Content-Type is text/html , then Go to the next step, and then the attacker analyzes the Content-Type parameter. If the Callback parameter allows the attacker to insert HTML tags, there is a vulnerability.
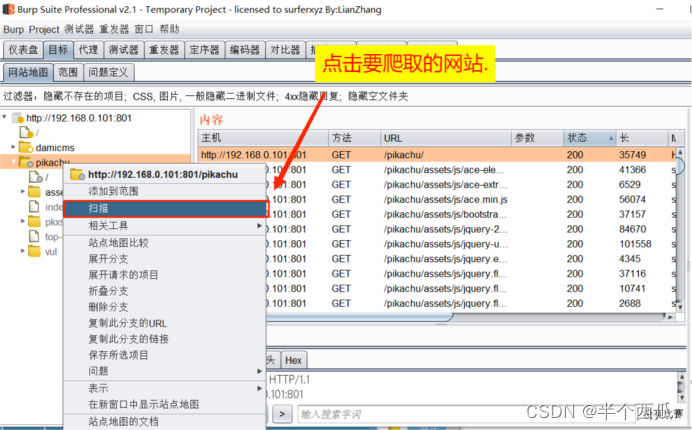
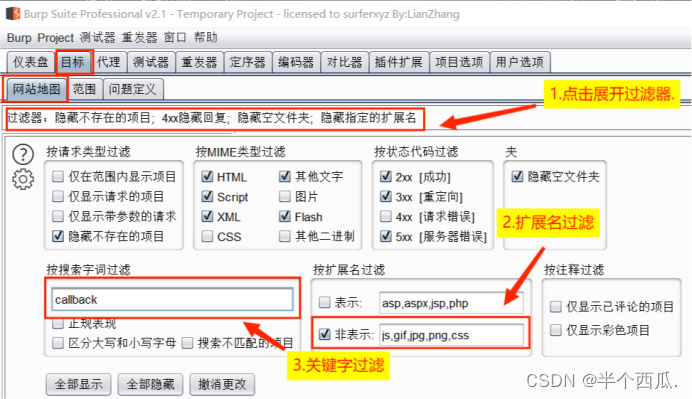
Step 1: Use the crawler function of Burp Suite to start crawling from the focused directory (usually the root directory of the website), select the item to start crawling in the HTTP history tab, right-click and select " Spider from here ". The crawled results will be displayed in Target --> Site map . After crawling, use the Burp Suite filtering function to find the link with the Callback parameter. (After entering the keyword, click the " 1 " position to make the filtering function take effect)
Step 2: Find the link whose URL has the callback parameter.
Step 3: Check whether the Content-Type of the HTTP Response (check the response packet) corresponding to the URL is text/html . If the Content-Type is text/html , the tag we input will be recognized by the browser. Then send the corresponding request to the Repeater (retransmitter)
Step 4: Check whether the Callback parameter is filtered and controllable. At this time, we need to add some text HTML tags before the Callback parameter value, and do not use script and other tags directly to avoid detection by protection devices such as waf . Here we use the first-level tag <h1> . For example: callback= <h1>Test</h1> jsonp1 , then send it to see if there is <h1>Test</h1> content in the response , if there is a loophole, then delete the parameter of info (in the URL) to get Shorten the URL .
Step 5: In the simplified URL, replace the callback parameter with a malicious HTML tag, and use it in a new browser.
Repair suggestion:
(1) Strictly define the Content-Type in the HTTP response as json data format: Content-Type: application/json
(2) Create a whitelist of the Callback function. If the incoming Callback parameter value is not in the whitelist, jump to the unified exception page to prevent it from continuing to output.
(3) HTML entity encoding is performed on the Callback parameter to filter out " < ", " > " and other characters.
Books to learn: A Practical Guide to Web Attack and Defense Business Security.