Message digest algorithm, commonly used in password processing of some medium and large websites
Typical characteristics of a message digest algorithm:
- same message, same digest
- Digest length is fixed regardless of message length (same algorithm)
- different messages, the digest will hardly be the same
Common message digest algorithms are:
- MD series: MD2 (128bit), MD4 (128bit), MD5 (128bit)
- SHA family: SHA-1 (160bit), SHA-256 (256bit), SHA-384 (384bit), SHA-512 (512bit)
Taking MD5 as an example, the operation result is composed of 128 binary numbers. Usually, it will be converted into a hexadecimal number to represent, which is a 32-bit hexadecimal number.
Therefore, the types of operation results of the MD5 algorithm are 2 to the 128th power, namely: 340282366920938463463374607431768211456
Since the message algorithm will lose part of the data during the operation, the message algorithm is irreversible!
When using the message digest algorithm to process password encryption, any "cracking" will not be "obtaining the original text calculated from the ciphertext"!
On the Internet, there are some platforms that record simple plaintext and ciphertext correspondence databases to achieve the effect of "querying the original text based on the ciphertext". However, as long as the original text is complex enough (more than 8 bits long), in order to ensure The complexity should use "salt", which will be one of the components of the data being operated, for example: it is impossible for these platforms to include their correspondence!
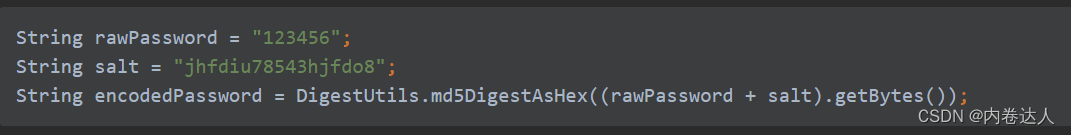
Even though the original password is very simple, for the calculation process, the real original data has already been changed 123456jhfdiu78543hjfdo8. It is impossible for such a corresponding relationship between the original text and the cipher text to be included by various platforms!
Therefore, in order to ensure the security of user passwords, the feasible methods are:
-
Require users to use stronger original passwords
- require a longer password
- Require more variety in the types of characters contained in passwords
-
With salt
- In theory, the more complicated the salt value, the better, but there is no need to overcomplicate it
- The specific use of the salt value is not stipulated. In principle, as long as it can make the calculated data complicated
-
Cyclic encryption
- Use the ciphertext obtained by the first operation as the original text, and perform the second operation, and so on for many times
-
Use a message digest algorithm with a longer bit length
-
Combining the above methods