wrong information:
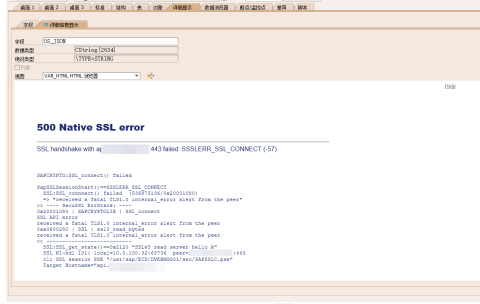
500 Native SSL error :
SSL handshake with api.uat 443 failed: SSSLERR_SSL_CONNECT -57
SAPCRYPTO:SSL_connect failed
received a fatal TLS1.0 internal_error alert from the peer
This error is about ABAP as a client, unable to establish a secure link via https to an external server providing the API.
The certificate has been strustimported ssl.
Someone in the SAP community had a similar question and it was not answered.
There is an answer in this github issue .
Some netizens have 7.5 SP02successfully 7.4 SP05solved this error on two different versions of and .
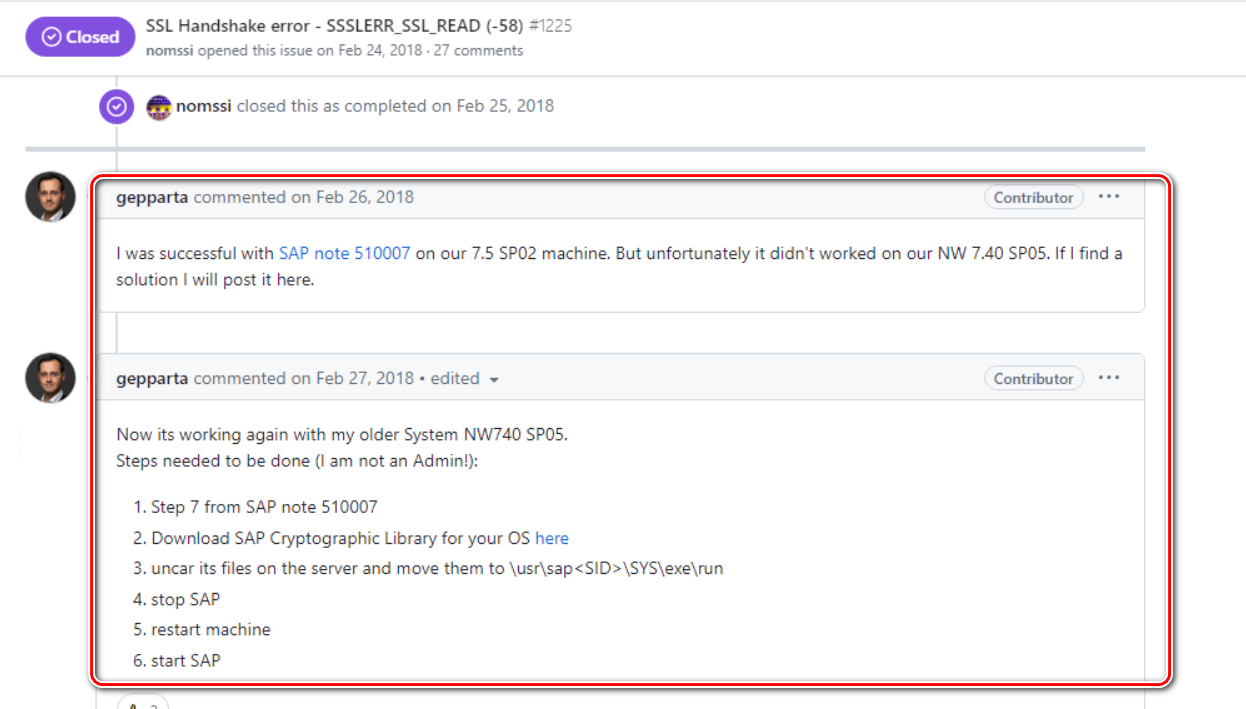
This is the technical domain of pure SAP basis.
7.5 SP02
Follow the configuration introduced in SAP note 510007 to configure the SAP ABAP SSL server side.
7.4 SP05
-
Execute Step 7 of SAP note 510007.
-
Download SAP Cryptographic Library, link here .
-
After decompression, copy the file to this path:
\usr\sap<SID>\SYS\exe\run -
restart server
Note: There is a dedicated team within SAP for such server configuration issues. I don't know much about configuration issues like this, the above is from a Google search, I haven't really tried it myself (on the SAP system we work on, I don't have enough permissions).
Supplement - What is an SSL handshake?
SSL handshake is a handshake protocol in the SSL/TLS protocol, which is used to establish a secure communication connection between the client and the server. It is completed at the beginning of the SSL/TLS handshake protocol, through several steps to negotiate keys, verify the identity of the other party, establish a secure channel, etc.
The process of SSL handshake is roughly as follows:
- The client initiates an SSL connection request to the server.
- The server responds to the client by sending its digital certificate, which contains the server's public key and server information.
- The client verifies whether the digital certificate of the server is valid and legal, and if it is legal, generates a random number as an encryption key.
- The client uses the server's public key to encrypt the generated random number and sends it to the server.
- The server uses its own private key to decrypt the random number sent by the client, and then uses the random number to generate an encryption key.
- The server will use this encryption key to encrypt the data and send it to the client.
- The client also uses this encryption key to encrypt data and send it to the server.
- The SSL handshake ends and a secure communication connection is established between the client and server.
The purpose of SSL handshake is to establish a secure communication connection between the client and the server to ensure the confidentiality, integrity and credibility of the communication. It is a very important link in the SSL/TLS protocol, and it is also the key to ensuring communication security.