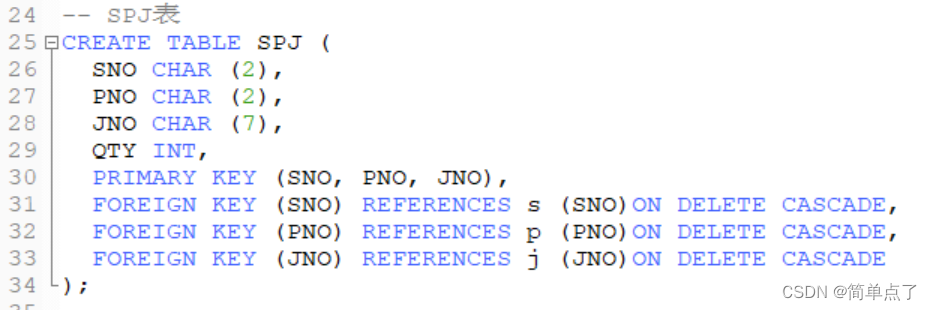
Experiment 4 Database Security and Integrity
one. Purpose of the experiment
1. To deepen the understanding of database security and integrity;
2. To learn authorization and recovery;
4. To understand and experience the role of database entity integrity, referential integrity, and user-defined integrity constraints.
2. Experimental content
Authorize and reclaim permissions for each table and user that has been built. After the operation, check whether the authorized user really has the right to operate the data granted, and whether the user after the power revocation operation really loses the revocation The right to manipulate data.
Define various integrity constraints, and then enter various data to verify the effect of the constraints
- Set the query permission for user a on the SPJ table. Log in as a to verify the permissions of a .
experiment procedure:
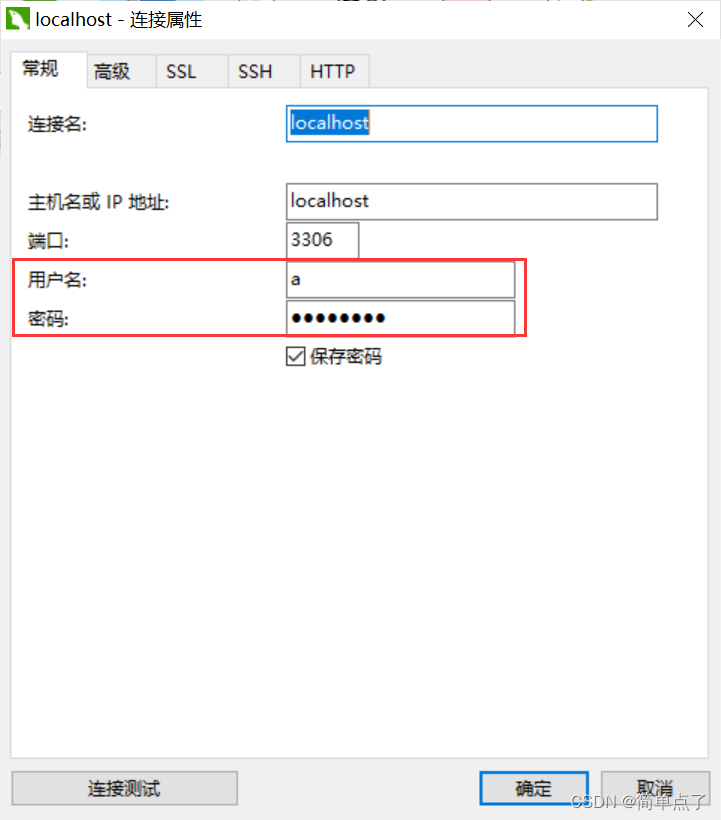
(1) Create a user first, and the password is "password":
CREATE USER 'a' IDENTIFIED WITH mysql_native_password BY'password';
(2) Verify the permission of a before authorization:
Log in:
Run the query statement:
SELECT sno
from spj
It was found that there is no access to the database:
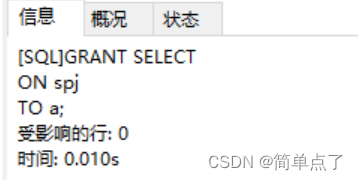
(3) Authorize again:
GRANT SELECT
ON spj
TO a;
(4) Login to verify the authority of a:
SELECT sno
from spj
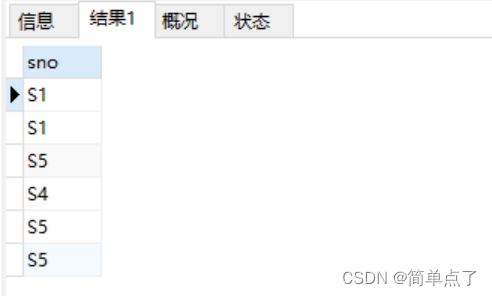
Experimental results:
create:

Authorization:
Result analysis:
When creating a user, create 'a'@%, do not create a@host, otherwise it cannot be authorized.
- Set user b to have modification permission on S list and P list, and require b to be able to grant this permission to other user c . Log in with b and c respectively , and verify the permissions of b and c .
experiment procedure:
(1) Create user b with password "bpassword":
CREATE USER 'b' IDENTIFIED WITH mysql_native_password BY'bpassword';
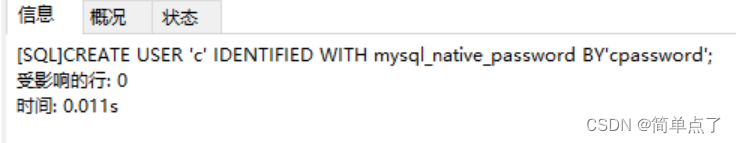
(2) Create c user with password "cpassword":
CREATE USER 'c' IDENTIFIED WITH mysql_native_password BY'cpassword';
(3) Authorize (grant query and modification permissions, only modification permissions are not allowed):
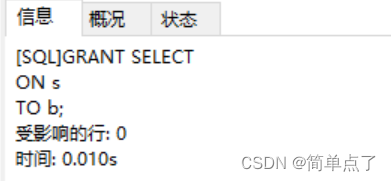
GRANT SELECT
ON s
TO b;
GRANT UPDATE
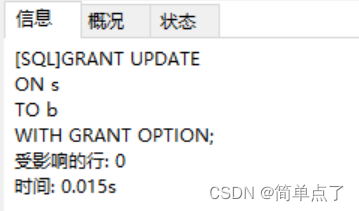
ON s
TO b
WITH GRANT OPTION;
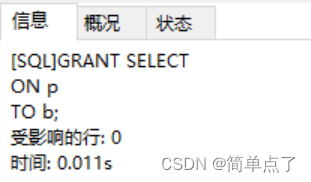
GRANT SELECT
ON p
TO b;
GRANT UPDATE
ON p
TO b
WITH GRANT OPTION;

(4) Log in to user b and verify permissions:
(5) Log in b and change the SNAME in table s5 of s to "for the people" and the city to "Beijing"
UPDATE s
SET SNAME='for the people',CITY='Beijing'
WHERE sno='S1';

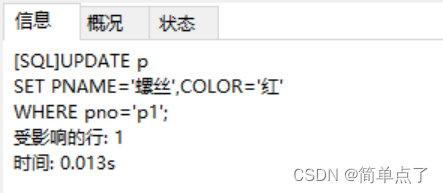
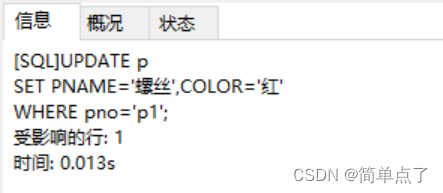
(6) Change p1 in the p table to screw, and change the color to red
UPDATE p
SET PNAME='screw',COLOR='red'
WHERE pno='p1';
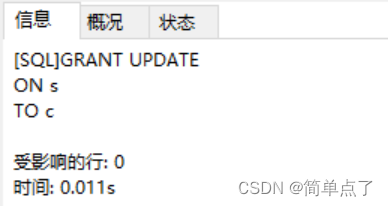
(7) Log in to b, execute the authorization authority, and grant c the query and modification authority to the s and p tables
GRANT SELECT
ON s
TO c;

GRANT UPDATE
ON s
TO c
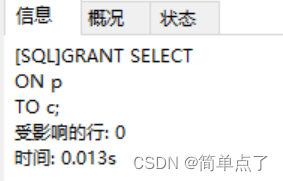
GRANT SELECT
ON p
TO c;
GRANT UPDATE
ON p
TO c
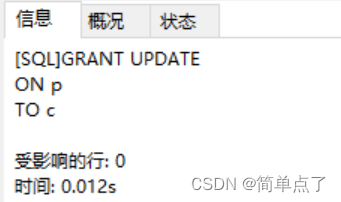
(8) Log in to c, change the SNAME in table s5 of s to "Weimin" and the city to "Shanghai"
UPDATE s
SET SNAME='for the people', CITY='Shanghai'
WHERE sno='S1';

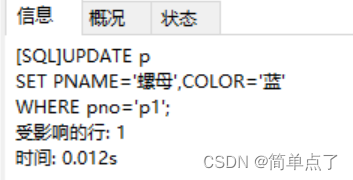
(9) Change p1 in the p table to a nut, and change the color to blue
UPDATE p
SET PNAME='Nut',COLOR='Blue'
WHERE pno='p1';
Experimental results:
(1) Create user b with password "bpassword":

(2) Create c user with password "cpassword":
(3) Authorize (grant query and modification permissions, only modification permissions are not allowed):

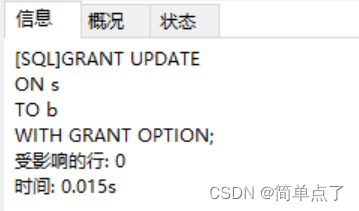
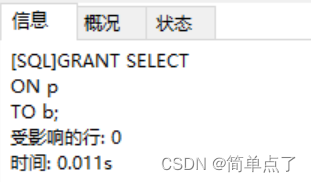
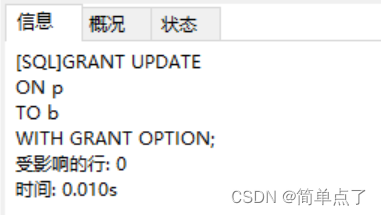
(4) Log in to user b and verify permissions:
(5) Log in b and change the SNAME in table s5 of s to "for the people" and the city to "Beijing"
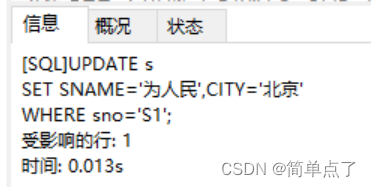
(6) Change p1 in the p table to screw, and change the color to red
(7) Log in to b, execute the authorization authority, and grant c the query and modification authority to the s and p tables
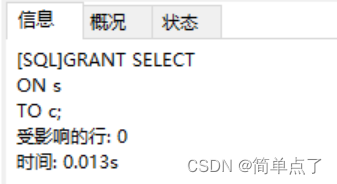
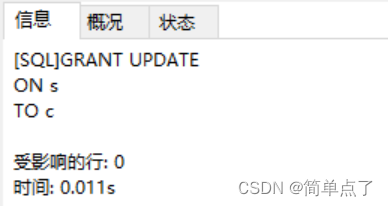
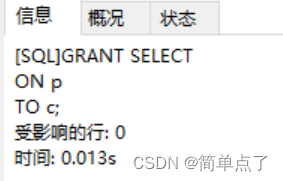

(8) Log in to c, change the SNAME in table s5 of s to "Weimin" and the city to "Shanghai"
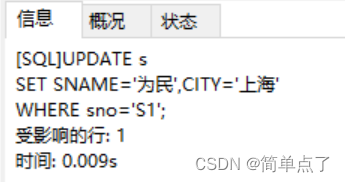
(9) Change p1 in the p table to a nut, and change the color to blue
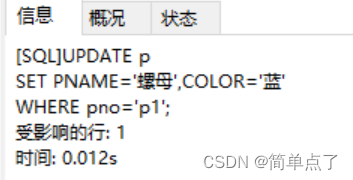
Result analysis:
When granting modification permission to a user, remember to grant query permission at the same time, and update cannot be done without select
- Take back the permissions of users a and b , and verify the status of the permissions of user c .
experiment procedure:
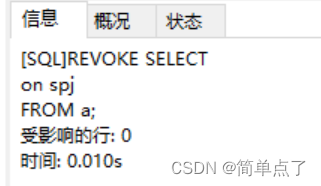
(1) Take back the query permission of a on the spj table:
REVOKE SELECT
on spj
FROM a;
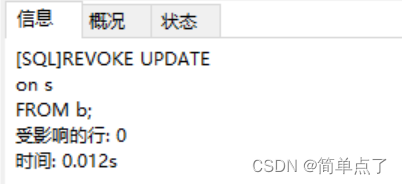
(2) Take back b's permission to modify tables s and p:
REVOKE UPDATE
on s
FROM b;
REVOKE UPDATE
on p
FROM b;
(3) Verify whether user c still has permission to change tables s and p:
login c:
Change the SNAME in s table s5 to "Weiguo" and the city to "Guangzhou"
UPDATE s
SET SNAME='for the country',CITY='Guangzhou'
WHERE sno='S1';
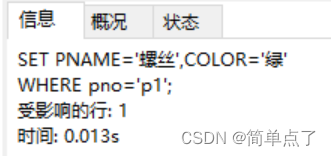
Change p1 in the p table to screw, and change the color to green
UPDATE p
SET PNAME='screw',COLOR='green'
WHERE pno='p1';
Experimental results:
(1) Take back the query permission of a on the spj table:
(2) Take back b's permission to modify tables s and p:

(3) Verify whether user c still has permission to change tables s and p:

Result analysis:
Only the authority of b is withdrawn, but the authority granted to c by b is not withdrawn, indicating that mysql has not performed cascading recovery.
4. For the table created in Experiment 1 , use the graphical user interface to establish a foreign key relationship and verify the role of the foreign key.
experiment procedure:
- Right-click--Design Table--Foreign Key--Create Foreign Key
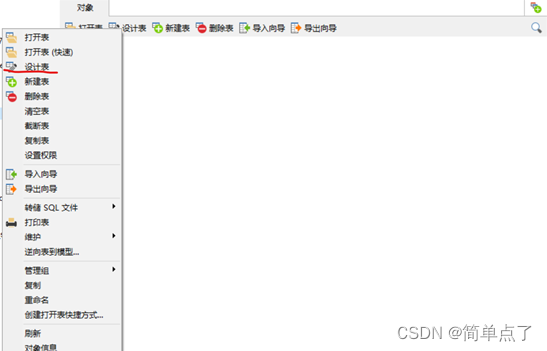

(2) Verify the role of the foreign key: (insert a piece of data that violates the foreign key constraint in the spj table)
insert ('S8', 'P1', 'J9', 200) into the spj table:
INSERT INTO spj VALUES('S8' ,'P1','J9',300);
Experimental results: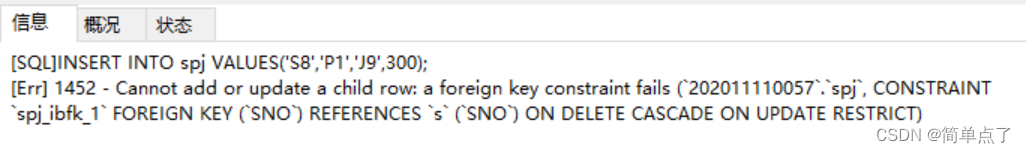
Result analysis:
The S table is up to S6, the p table is up to P6, and the j table is up to J7. The inserted data violates the foreign key constraint, so an error will be reported.
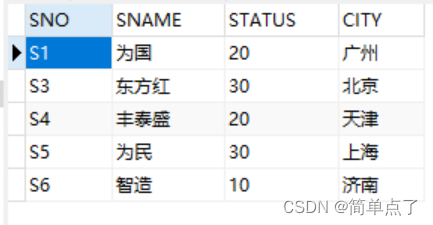
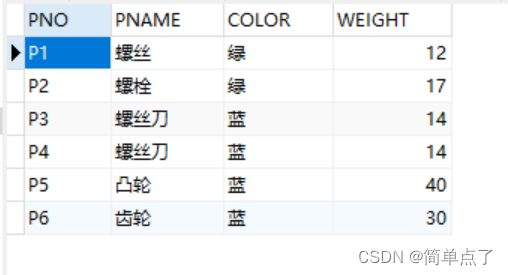
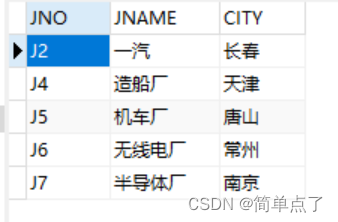
5. For the table created in Experiment 1, set the color of the parts must be within the seven color ranges of red, orange, yellow, green, blue, blue, and purple, and the weight of the parts cannot exceed 50 constraints, and give these two constraints Conditional naming, the name is the full spelling of your own name.
experiment procedure:
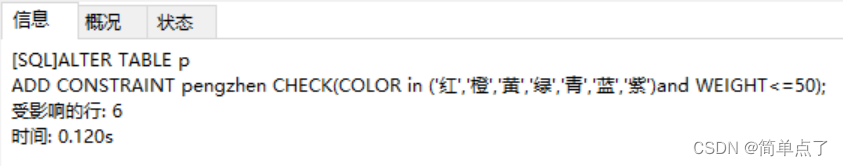
(1) Add constraints:
ALTER TABLE p
ADD CONSTRAINT pengzhen CHECK(COLOR in ('red','orange','yellow','green','green','blue','purple')and WEIGHT<=50);
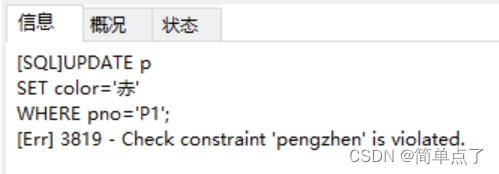
(2) To verify whether the constraint is useful, change the "green" of P1 in the p table to "red"
UPDATE p
SET color='red'
WHERE pno='P1';
Experimental results:
(1) Add constraints:
(2) To verify whether the constraint is useful, change the "green" of P1 in the p table to "red"
Result analysis:
To verify whether the constraints are useful, change the "green" of P1 in the p table to "red", and an error will be reported when running, and the pengzhen constraint already exists. The data cannot be changed.
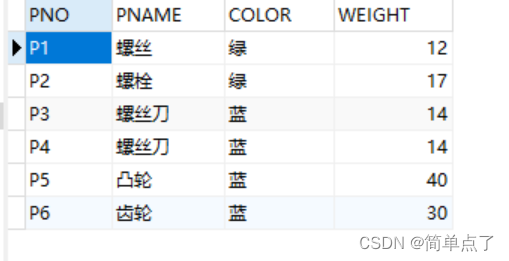
6. Set the number of supplied parts in the SPJ table to no more than 1000
experiment procedure:
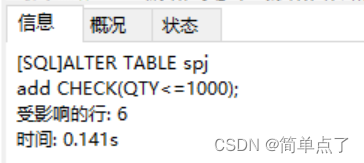
(1) Add constraints:
ALTER TABLE spj
add CHECK(QTY<=1000);
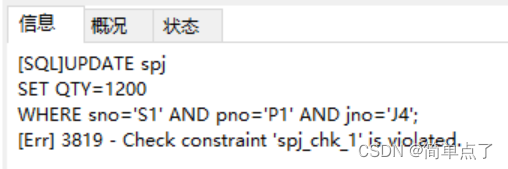
- Change the QTY of the first piece of data to 1200 in the spj table
UPDATE spj
SET QTY=1200
WHERE sno='S1' AND pno='P1' AND jno='J4';
Experimental results:
- Add constraints:
(2) Change the QTY of the first piece of data to 1200 in the spj table
Result analysis:
Due to the existence of constraints, the data cannot be modified to a number greater than 1000.
7. Set the supplier number in the S table to start with the letter 'S'
Experimental process:
ALTER TABLE s
add CHECK(sno like 's%');
Experimental results:
Result analysis:
create constraints, CHECK(sno like 's%')
8. Verify the entity integrity of each table.
Experimental process:
-- Verify the entity integrity of table s
-- (1) Insert a piece of normal data into table s
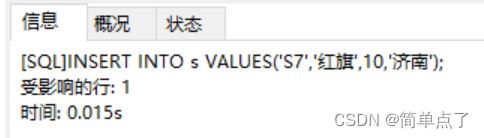
INSERT INTO s VALUES('S7','Red Flag',10,'Jinan');
-- (2) Insert a piece of duplicate data into table s
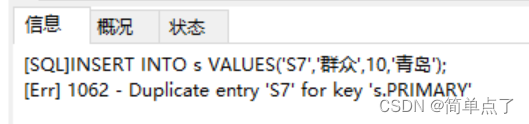
INSERT INTO s VALUES('S7','People',10,'Qingdao'); -- (
3) Insert an empty piece of data into table s
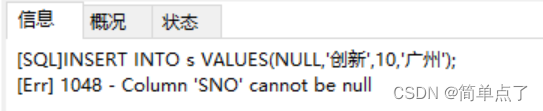
INSERT INTO s VALUES('',' Innovation',10,'Guangzhou');
-- Verify the entity integrity of the p table
-- (1) Insert a normal data into the p table
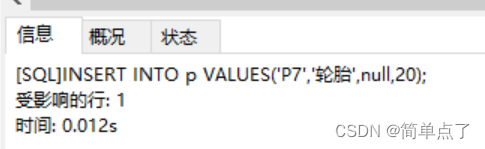
INSERT INTO p VALUES('P7','tire',null,20);
-- (2) Insert a piece into the p table Repeated data
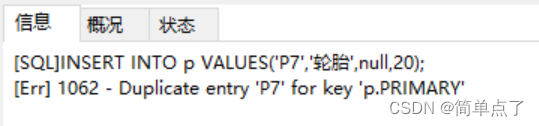
INSERT INTO p VALUES('P7','tire',null,20);
-- (3) Insert an empty data into the p table
INSERT INTO p VALUES(NULL,'nail',null,5);
-- Verify the entity integrity of table j
-- (1) Insert a piece of normal data into table j
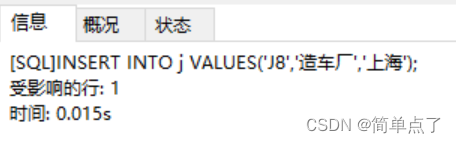
INSERT INTO j VALUES('J8','Car Factory','Shanghai');
-- (2) Insert into table j A piece of repeated data
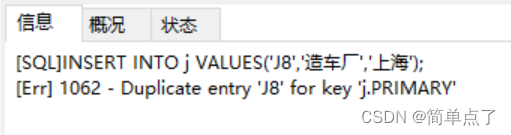
INSERT INTO j VALUES('J8','Car Factory','Shanghai');
-- (3) Insert an empty piece of data into table j
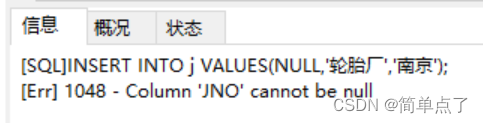
INSERT INTO j VALUES(NULL,'Tire Factory','Nanjing ');
-- Verify the entity integrity of the spj table
-- (1) Insert a piece of normal data into the spj table
INSERT INTO spj VALUES('S7','P6','J7',300);
-- (2) Insert into the spj table Insert a duplicate data
INSERT INTO spj VALUES('S7','P6','J7',300);
-- (3) Insert an empty data into the spj table
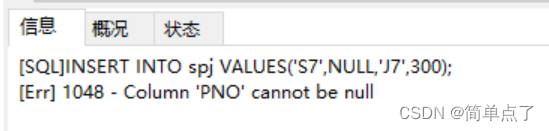
INSERT INTO spj VALUES('S7',NULL,' J7',300);
Experimental results:
-- Verify the entity integrity of table s
-- (1) Insert a piece of normal data into table s ('S7','Red Flag',10,'Jinan')
-- (2) Insert a piece of duplicate data into the s table ('S7','People',10,'Qingdao')
-- (3) Insert an empty piece of data into table s ('','Innovation',10,'Guangzhou')
--Verify entity integrity of p table
-- (1) Insert a piece of normal data into the p table ('P7','tire',null,20)
-- (2) Insert a piece of repeated data into the p table ('P7','tire',null,20)
-- (3) Insert an empty piece of data into the p table (NULL,'nail',null,5)

-- Verify entity integrity of table j
-- (1) Insert a piece of normal data into the j table ('J8', 'car factory', 'Shanghai')
-- (2) Insert a piece of duplicate data into table j ('J8', 'car factory', 'Shanghai')
-- (3) Insert an empty data into the j table (NULL,'tire factory','Nanjing')
--Verify entity integrity of spj table
-- (1) Insert a piece of normal data into the spj table ('S7','P6','J7',300)

-- (2) Insert a piece of duplicate data into the spj table ('S7','P6','J7',300)

-- (3) Insert an empty data into the spj table ('S7', NULL, 'J7', 300)
Result analysis:
Due to the integrity constraints defined when the s, p, and j tables are created, duplicate data cannot be inserted, and data whose primary code is null cannot be inserted. The above statement verifies the integrity constraints.