
Detailed explanation of components
Detailed explanation of istio components
There are many Istio service components. From the above process, you can basically see how each component cooperates. The specific purpose and function of each component are explained below.
[root@k8smaster ~]# kubectl get svc -n istio-system | awk '{print $1}'
istio-egressgateway
istio-ingressgateway
istiod
Pilot
Pilot is the main control component of Istio, which issues commands to control the client. Throughout the system, Pilot accomplishes the following tasks:
1. Obtain service information from the registry of Kubernetes or other platforms to complete the service discovery process.
2. Read Istio's various control configurations, and after conversion, send them to the data plane for implementation.
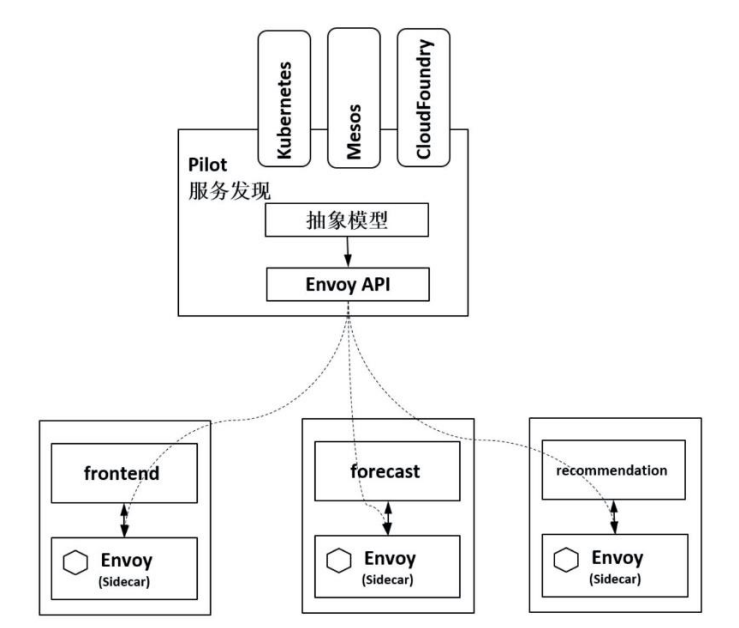
Pilot sends the configuration content to Envoy on the data plane, and Envoy converts the definition information such as routing, service, monitoring, and clustering into local configuration according to Pilot instructions, and completes the implementation of control behavior.
1) Pilot provides service discovery for Envoy
2) Provide traffic management functions (eg, A/B testing, canary releases, etc.) and resilience functions (timeouts, retries, circuit breakers, etc.);
3) Generate envoy configuration
4) Start envoy
5) Monitor and manage the running status of envoy, such as pilot-agent is responsible for restarting envoy when envoy fails, or reload envoy after envoy configuration changes
Envoy
What is Envoy?
Envoy is a high-performance proxy developed in C++ that coordinates inbound and outbound traffic for all services in a service mesh.
Envoy has many powerful features such as:
Dynamic Service Discovery
load balancing
TLS termination
HTTP/2 and gRPC proxy
breaker
health examination
traffic split
grayscale release
fault injection
What is the relationship between Envoy and services in Istio?
Envoy and Service A belong to the same Pod and share the network and namespace. Envoy proxies the traffic in and out of Pod A, and acts on Service A according to the rules of external requests.
What is Pilot-agent?
Envoy does not directly interact with k8s. The Pilot-agent process managed by pilot-agent generates the Envoy configuration file according to the configuration information in the K8S APIserver, and is responsible for starting the Envoy process.
Envoy is started by the Pilot-agent process. After startup, Envoy reads the configuration file generated by the Pilot-agent for it, and then obtains the address of the Pilot according to the configuration of the file, and pulls the dynamic configuration information from the pilot through the data plane, including routing ( route), listener (listener), service cluster (cluster) and service endpoint (endpoint).
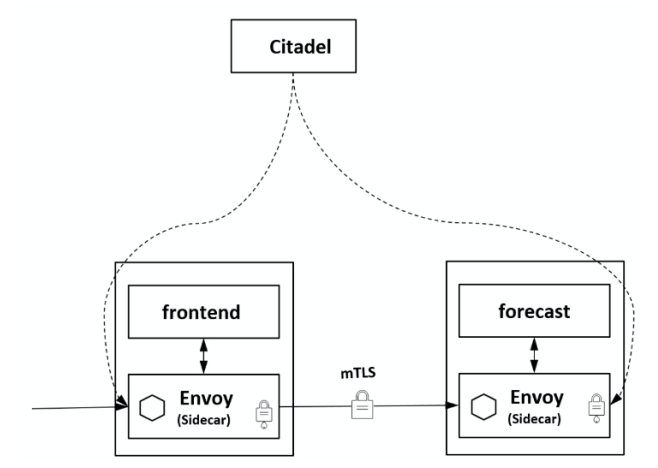
Citadel
Responsible for handling TLS communication between different services on the system. Citadel acts as a Certificate Authority (CA) and generates certificates to allow secure mTLS communication in the data plane.
Citadel is the core security component of Istio, providing automatic generation, distribution, rotation and revocation of keys and certificates. Citadel has been monitoring Kube-apiserver, generating certificate keys for each service in the form of Secret, and mounting a volume to the Pod when the Pod is created. The proxy container uses these files for service identity authentication, and then proxies both ends. The service implements security functions such as mutual TLS authentication, channel encryption, and access authorization. As shown in the figure, the frontend service uses HTTP to access the forecast service, and the authentication function can be added to the service through configuration. The Envoys on both sides will establish a TLS channel for mutual authentication, thereby enabling HTTPS for mutual authentication between services.
Galley
Galley is istio's configuration validation, extraction, processing and distribution component. Galley is a service that provides configuration management. The implementation principle is to verify the configuration through the ValidatingWebhook provided by k8s.
Galley enables Istio to work with other environments than Kubernetes because it can convert disparate configuration data into a common format that Istio understands.
Ingressgateway
Ingressgateway is the gateway at the entrance, and access to services in the grid from outside the grid is done through this gateway. istio-ingressgateway is a Loadbalancer-type Service. Unlike other service components, which only have one or two ports, istio-ingressgateway opens a set of ports, which are the external access ports for services in the grid. As shown in the figure below, the load of the grid ingress gateway istio-ingressgateway is the same execution process as that of the sidecars in the grid. It also receives traffic rules from the Pilot and executes them like other sidecars in the grid.
Sidecar-injector
Sidecar-injector is the component responsible for automatic injection. As long as automatic injection is enabled, istio-sidecar-injector will be automatically called to inject the Sidecar container into the Pod when the Pod is created.
In the Kubernetes environment, according to the automatic injection configuration, when Kube-apiserver intercepts the request created by the Pod, it will call the automatic injection service istio-sidecar-injector to generate the description of the sidecar container and insert it into the definition of the original Pod. The created Pod includes not only the business container but also the Sidecar container. This injection process is transparent to the user.
other components
In addition to Istio's own components prefixed with "istio", Jaeger-agent, Jaeger-collector, Jaeger-query, Kiali, Prometheus, Grafana, Tracing, Zipkin and other components are generally installed in the cluster. These components provide Istio calls Chain, monitoring and other functions, you can choose to install to complete the complete service monitoring and management functions.
write at the end
It is not easy to create, if you think the content is helpful to you, please give me a three-link follow to support me! If there are any mistakes, please point them out in the comments and I will change them in time!
Series currently being updated: Learning istio from scratch
Thank you for watching, the article is mixed with personal understanding, if there is any error, please contact me to point out~