HTTP stateless protocol
HTTP is a stateless protocol. Each request of the browser is processed independently by the server and is not associated with previous or subsequent requests. Therefore, any user can access server resources through the browser.
session and cookie mechanism
Sessions are server-level, cookies are browser-level.
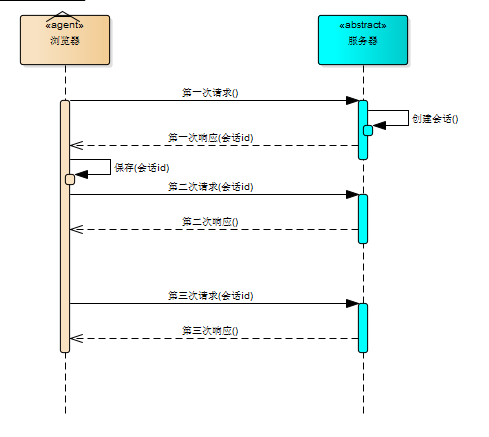
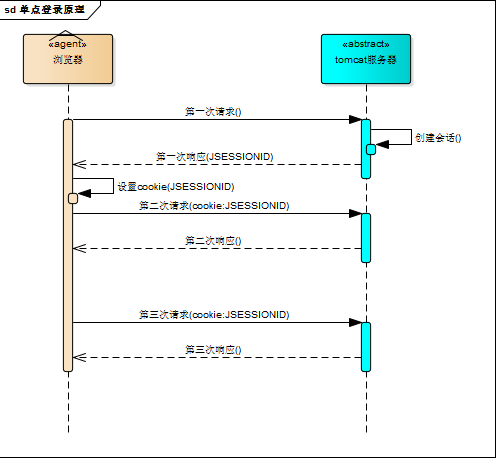
session: The first time the browser requests the server, the server creates a session and sends the session id to the browser as part of the response. The browser stores the session id, and every time the browser accesses the server, the session id will be attached to the server. According to the session id, it is known whether it is the same user.
cookie: session mechanism Every time the browser accesses the server, the server must judge the session id once, which is obviously not suitable. So the browser to maintain the session id is the cookie mechanism. The browser automatically attaches cookie information every time it visits the server.
The cookie and session mechanism can ensure that after a user logs in to a system, subsequent operations do not need to log in to the system again within a certain period of time.
Multi-system solution 1--Top level domain name
The above sessions and cookies are only applicable to a single system, but when the number of systems becomes multi-system, we can’t access a branch system and log in once, so the domain names of these subsystems are unified into a top-level domain name, and then the The cookie domain is set to the top-level domain name, so that cookies can be shared between subsystems.
sign in
from where
There are many limitations due to shared cookies. For example, it is difficult to unify domain names, and it is difficult to unify subsystem technologies. Therefore, a brand-new login method is needed to realize the login of multi-system application groups -- single sign-on.
what is
The full name of single sign-on is single sign on, or SSO for short. It means that when you log in to one system in a multi-system application group, you can be authorized in all other systems without logging in again, including single sign-on and single logout.
How to achieve
Log in
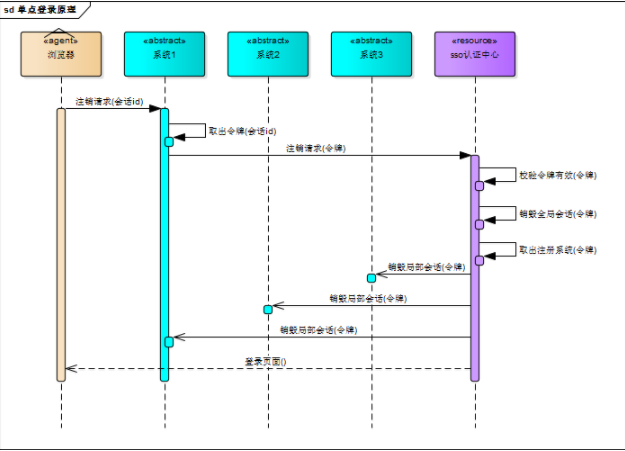
sso需要一个独立的认证中心,只有认证中心能接受用户的用户名密码等安全信息,其他系统不提供登录入口,只接受认证中心的间接授权。间接授权通过令牌实现,sso认证中心验证用户的用户名密码没问题,创建授权令牌,在接下来的跳转过程中,授权令牌作为参数发送给各个子系统,子系统拿到令牌,即得到了授权,可以借此创建局部会话,局部会话登录方式与单系统的登录方式相同。具体过程如图所示:
操作步骤如下:
1.用户访问系统1的受保护资源,系统1发现用户未登录,跳转至sso认证中心,并将自己的地址作为参数
2.sso认证中心发现用户未登录,将用户引导至登录页面
3.用户输入用户名密码提交登录申请
4.sso认证中心校验用户信息,创建用户与sso认证中心之间的会话,称为全局会话,同时创建授权令牌
5.sso认证中心带着令牌跳转会最初的请求地址(系统1)
6.系统1拿到令牌,去sso认证中心校验令牌是否有效
7.sso认证中心校验令牌,返回有效,注册系统1
8.系统1使用该令牌创建与用户的会话,称为局部会话,返回受保护资源
9.用户访问系统2的受保护资源
10.系统2发现用户未登录,跳转至sso认证中心,并将自己的地址作为参数
11.sso认证中心发现用户已登录,跳转回系统2的地址,并附上令牌
12.系统2拿到令牌,去sso认证中心校验令牌是否有效
13.sso认证中心校验令牌,返回有效,注册系统2
14.系统2使用该令牌创建与用户的局部会话,返回受保护资源骤
注销
在一个子系统中注销,所有的子系统都会注销。如下图所示:
具体操作步骤
1.用户向系统1发起注销请求
2.系统1根据用户与系统1建立的会话id拿到令牌,向sso认证中心发起注销请求
3.sso认证中心校验令牌有效,销毁全局会话,同时取出所有用此令牌注册的系统地址
4.sso认证中心向所有注册系统发起注销请求
5.各注册系统接收sso认证中心的注销请求,销毁局部会话
6.sso认证中心引导用户至登录页面