https://blog.csdn.net/heyangyi_19940703/article/details/51208678

1. What is Single Sign-On (Single Sign-On)
SSO is a unified authentication and authorization mechanism, which means that the same user who accesses protected resources in different applications on the same server only needs to log in once, that is, after passing the security verification in one application, when accessing protected resources in other applications , you no longer need to re-login for verification.
2. What problem does single sign-on solve?
It solves the problem that users only need to log in once to access all mutually trusted application systems without having to log in repeatedly.
For example, forum applications, blog applications, and download application modules in CSDN. As long as we visit any sub-application in CSDN, we do not need to log in when we visit other application sites.
3. In the company, SSO has also been developed through .NET. I have seen a lot of SSO implementation methods on the Internet. Summarize some development experience in actual project development. Take a look at the flow chart below:
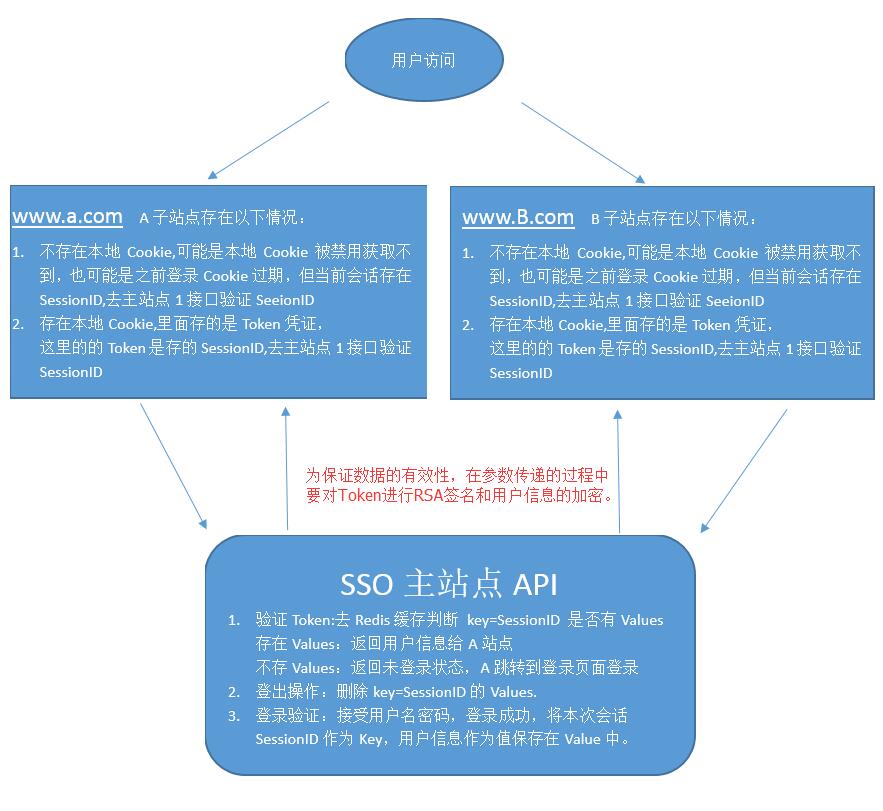
1. The user visits the site for the first time.
1. The user visits > www.a.com for the first time. At this time, the site does not record the previously logged-in cookie.
2. If no user is logged in, then jump to the Login page.
3. The user now enters the user name and password to log in, requests SSO to log in to the API, the login is successful, and a record such as Key=SessioID, Values=UserInfo is cached in Redis, and the cache time can be configured. Response returns the login authentication status, and user information.
4. 用户登录成功,记录下凭证,即此刻的SessionID写入Cookie.然后跳转到www.a.com
5. 这个时候有了Cookie,将记录的Cookie,也就是SessioID请求SSO验证Token接口,因为登录成功记录了Key=SessionID,所有可以获取到Values=即用户信息,Response 返回用户信息。
6. 用户现在去访问www.B.com站点,B站点无Cookie,这里SessionID还是当前会话的SessionID,所有区请求SSO主站点验证Token接口,发现存在Key=SessionID,返回登录状态成功,用户信息。在B站点下记录Cookie 即token 配置。
这样用户第一次访问A站点,从第一次登录,到访问其他站点的流程就走完了。
二.用户中途关闭浏览器,然后打开浏览器,访问B站点:
1. 发现存在Cookie, 即Token凭证,去SSO主站的,验证发现存在Key=SessioID,获取Values将UserIno返回给用户,返回用户任在登录状态。这样访问应用之前访问过的站点依旧在登录状态。
2. 如果用户在执行访问第二个应用,这时候Redis缓存的登录状态过期,则返回验证凭证失败。这时候第二个应用跳转到登录状态,走用户登录的流程以及后续验证流程。
注意记录Cookie的过期时间应该保证与Redis的过期时间一致性,不能在Redis缓存的过期时间之后过期,这样在用户此时访问第一个应用站点的时候,发现Cookie不存在,就会通过SessionID去验证凭证,发现这时候是过期后重新登陆,会将此时的登陆状态写入Cookie.
三.登出
只需要清除本地Cookie,调用SSO站点接口清除登陆缓存的状态即可实现登出。
四.注意:
In actual project development, various situations will be encountered, such as interface call parameter constraints, signature, encryption, etc. between the sub-site and the main SSO site. And the implementation of SSO login interface of pure html site, or the jump interface of pure .NET application website, these must be distinguished. Only after a detailed understanding of the principle of SSO to achieve single sign-on can the development be done with half the effort.
If a worker wants to do a good job, he must first sharpen his tools.