The software tool provided by Hongke – FLEX Dispatch, integrates powerful tools such as OPC UA data aggregation, simulation, and firewall traversal, which can greatly reduce your equipment and data management and operation and maintenance costs!
Practical meaning
The general OPC UA connection will occupy one port for communication. If you want to use the firewall at the same time, you can only set a whitelist in the firewall to allow the communication port.
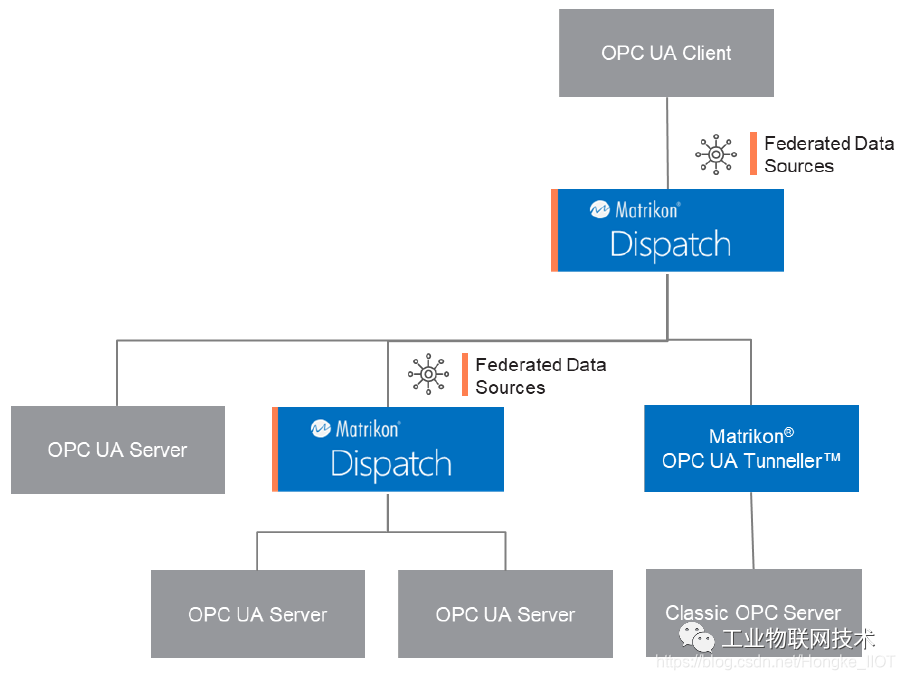
The FLEX firewall traversal function (FireBridge) allows users to set up a specified OPC UA client for the OPC UA server to make a reverse connection. The connection can ignore the firewall's inbound blocking rule-even if the inbound rule is disabled. The port can still communicate with the specified client. In addition, the inbound traffic of other clients or other software through the port will be blocked by the firewall. In other words, FLEX Dispatch allows users to make OPC UA connections in a more secure environment using firewalls.
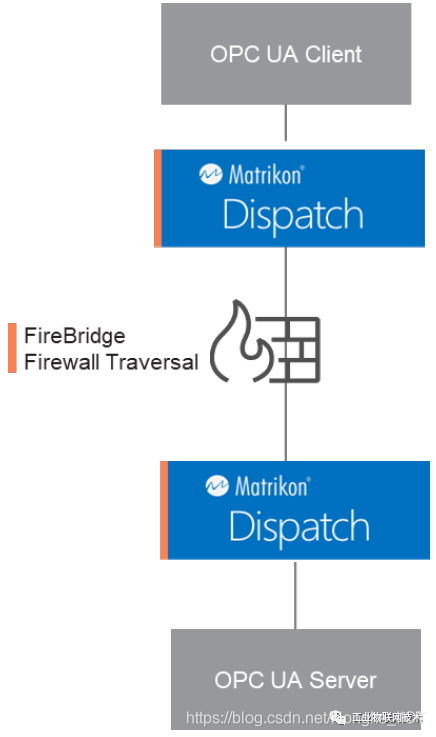
for example
The above explanation may be difficult to understand to some friends, so let's take a life example to explain to you:
In a closed management community, the owner can only enter and exit from the front entrance of the community with the owner's card (the server host has a firewall on). At this time, the property is going to deploy a courier cabinet (OPC UA server program). The general approach is to change a recess in the community wall and put the courier cabinet in this recess (open the port for the OPC UA program). Allow the courier (OPC UA client) to perform operations such as pick-up and drop-out from the express cabinet from the outside.
But at this time there is a risk: other people passing by can also damage the express cabinet (initiate an attack) or enter the pickup code to try to pick it up (exhaustive attack attempts to obtain operating permissions).

And there is a better method (FLEX Dispatch's solution to the firewall): install the express cabinet inside the community, and then the community property (administrator user) actively contact the courier in charge of the express cabinet to obtain his ID number ( Client Endpoint Url) and let the security at the gate of the community register, allowing the courier to enter the community with his ID card to operate the express cabinet. In this way, other people still cannot enter the community, and naturally cannot perform malicious operations on the express cabinet.
How to do it
Practical preparation
Hardware :
an x86 host (win10 is taken as an example in this article, it is recommended to choose win10 64-bit professional or enterprise version, the software supports Linux, and a virtual machine can be used to replace the physical host)
Software :
✔ Hongke Matrikon OPC UA Explorer
✔ Hongke Matrikon FLEX Dispatch for Windows
(all software can be contacted by Guangzhou Hongke for a one-month trial)
Note :
a) When you download and install the Matrikon software for the first time, choose to install all components by default, which will include the environment required for OPC UA communication to avoid unexpected errors.
b) In the Windows system, you need to open the group policy to set a user who can log in as a service.
c) Please remember the instance name and port number set during FLEX Dispatch installation (the default port number is 55000).
Practical steps
a) Firewall part:
To simulate the situation where the firewall is turned off, we can first go to the Windows control panel of the server host, disable the release rules that are automatically set when FLEX Dispatch is installed in the advanced settings of the firewall, and then add a new rule that prohibits inbound.
In the demonstration example of this article, the port of the server FLEX Dispatch is 55000, and the FireBridge communication port will be set to 55003. The firewall prohibits the inbound port range from 55000-55005, and includes the FLEX Dispatch server and FireBridge communication ports.
b) Server part:
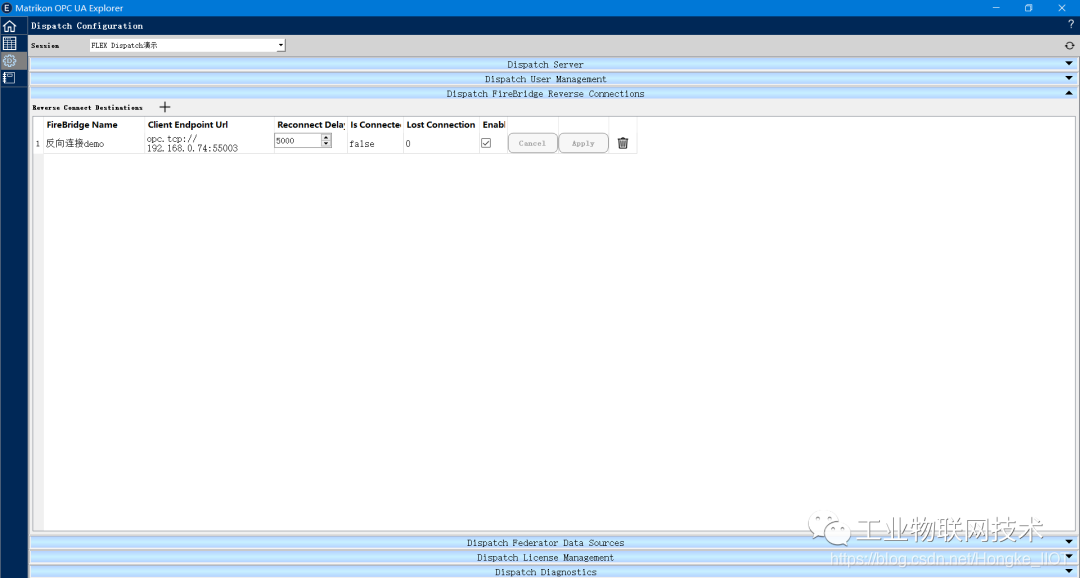
First connect to the FLEX Dispatch server located on this machine, and configure the data source content.
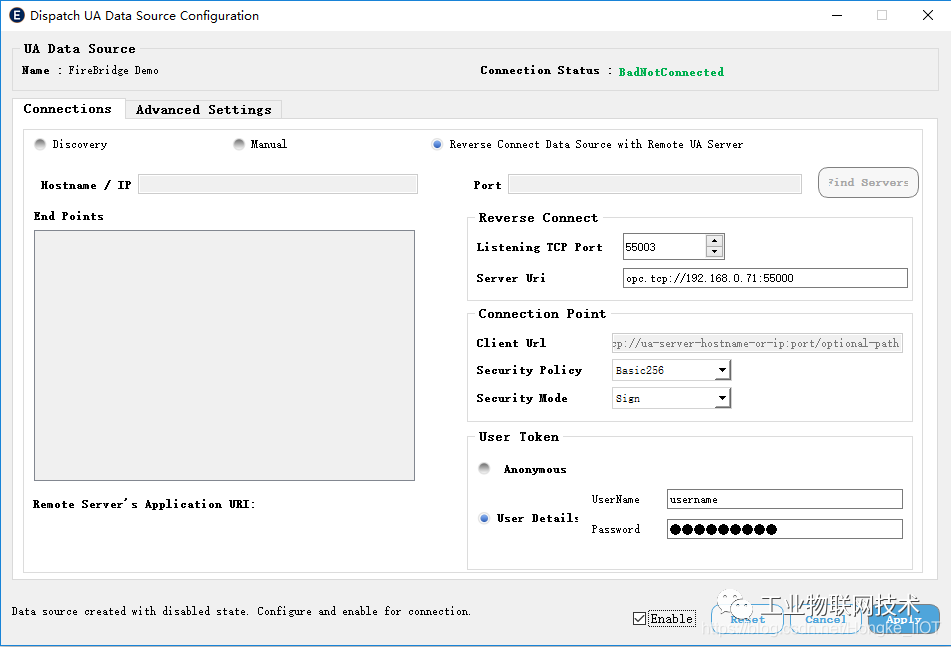
In the Dispatch FireBridge Reverse Connections tab of the Dispatch Configuration view, click the plus sign to add a new FireBridge reverse connection, and then fill in the client's Url in the Client Endpoint Url column. The format of the Url is:
opc.tcp:// <Client IP address>:<FireBridge communication port number>
Then, check the Enable option box and click Apply. At this point, the server is ready.
c) Client part:
Similarly, first connect to the FLEX Dispatch server located on the local machine, add the real OPC UA data source in the Dispatch Federator Data Sources tab of the Dispatch Configuration view, select the Reverse Connect Data Source with Remote UA Server type in the settings, and click the Server Url Fill in the Url of the server FLEX Dispatch (in this example, the port number is 55000), and fill in the FireBridge communication port in Listening TCP Port (in this example, the port number is 55003). Then select the matching security policy, enter the account password, check Enable and click Apply. At this time, the client has been configured, and you can wait for the software to automatically configure it.
✔ The first connection may prompt that the certificate is not trusted. At this time, you need to cut all the certificates in:
C:\ProgramData\Matrikon\FLEXDispatch<your FLEX Dispatch instance name>
\pki\DefaultApplicationGroup\rejected\certs
to
C:\ C:\ProgramData\Matrikon\FLEXDispatch<your FLEX Dispatch instance name>
\pki\DefaultApplicationGroup\trusted\certs
folder.
Back in the data view, you can find the server data source in the file tree Root>Objects>DispatchConfiguration>DataSources>FireBridge Demo>Data>Objects>DispatchConfiguration>DataSources folder.
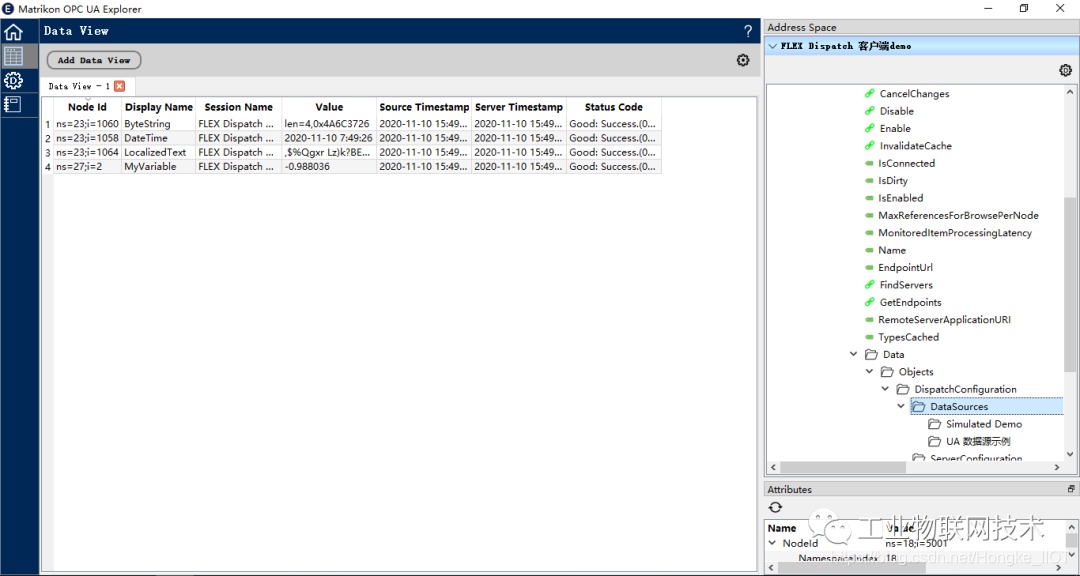
At this time, other computers in the LAN where the client host is located, or other OPC UA clients on the client host connecting to the FLEX Dispatch server, can also access the same results.
Conclusion
With the help of FLEX Dispatch's firewall traversal function (FireBridge), we can make OPC UA have the ability to penetrate firewalls, without setting up a firewall whitelist for OPC UA software or leaving open ports on the firewall.
In this way, the integrity of the firewall can be preserved, which helps to improve the security of the entire communication system. Security and stability are the foundation on which various applications of the Industrial Internet of Things can be established.