1. What is single sign-on
Single sign-on ( Single Sign the On ), referred to as SSO , is one of the more popular enterprise business integration solutions. The definition of SSO is that in multiple application systems, users only need to log in once to access all mutually trusted application systems. When there are many subsystems in our system, and these subsystems are deployed in different servers, then the traditional way of session cannot be solved, we need to use related single sign-on technology to solve it.
2. What is CAS
CAS is Yale a university-sponsored open source project, aimed at Web to provide a reliable method of single sign-on applications, CAS in 2004 Nian 12 officially became months JA-SIG project. CAS has the following characteristics:
[ 1 ] Open source enterprise-level single sign-on solution.
[ 2 ] CAS Server is a web application that needs to be deployed independently .
[ 3 ] CAS Client supports a lot of clients ( here refers to the web applications in the single sign-on system ) , including Java, .Net, PHP, Perl, Apache, uPortal, Ruby, etc.
From the structural point of view, CAS consists of two parts: CAS Server and CAS Client . CAS Server needs to be deployed independently and is mainly responsible for user authentication; CAS Client is responsible for processing access requests to the client's protected resources, and redirects to CAS Server when it needs to log in . The following figure is the most basic protocol process of CAS :

The SSO single sign-on access process mainly includes the following steps:
- Access service: The SSO client sends a request to access the service resources provided by the application system.
- Directed authentication: The SSO client will redirect user requests to the SSO server.
- User authentication: user identity authentication.
- Issuing tickets: The SSO server will generate a random Service Ticket .
- Ticket verification: The SSO server verifies the legitimacy of the ticket Service Ticket , and after the verification is passed, the client is allowed to access the service.
- Transmit user information: After the SSO server verifies the ticket, it transmits the user authentication result information to the client.
3. CAS server deployment
1. Download a pure Tomcat server, download address: https://pan.baidu.com/s/1YY3o6qno1DuR7oxwgMkdEQ
2. Download cas.war server, download address: https://pan.baidu.com/s/1w7Y1d3Tr0P0MBlGvRcLVTg
3. Unzip the downloaded Tomcat server to a file directory with no Chinese and no spaces, then cut the downloaded cas.war server to Tomcat's webapps directory, start Tomcat in the bin directory, ![]() and cas will be automatically extracted . the WAR package.
and cas will be automatically extracted . the WAR package.
4. Enter http://localhost:8080/cas/login in the browser to enter the following page:

4. CAS server configuration
1. Modify the port number
A. Modify the port number of Tomcat
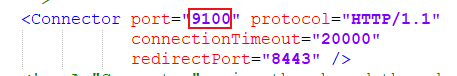
Open the Tomcat directory conf\server.xml and find the following configuration (Tomcat's initial port number is 8080, modify it to another port number, such as 9100)
B. Modify the cas configuration file
Modify the WEB-INF/cas.properties of cas after decompression :
![]()
2. Remove https certification
CAS is used by default HTTPS protocol, if you use HTTPS protocol requires SSL security certificate (to be specific to the institutions to apply and purchase) . If the security requirements are not high or in the development and testing phase, the HTTP protocol can be used . We are here to explain that by modifying the configuration, let CAS use the HTTP protocol.
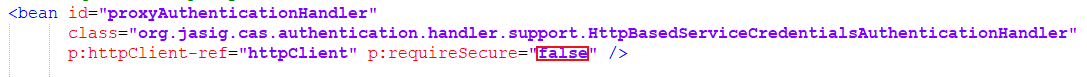
A. Modify the WEB-INF/deployerConfigContext.xml of cas
Here you need to modify the parameter p:requireSecure="false" , the default is true, the requireSecure attribute means whether security verification is required, that is, HTTPS , false means not to use
B. Modify the WEB- INF/spring-configuration /ticketGrantingTicketCookieGenerator.xml of cas

Default parameters P: = cookieSecure "to true" , the same way as HTTPS authentication related, TRUE is using HTTPS authentication, FALSE is not used https authentication.
The parameter default is p:cookieMaxAge="-1" , which is the maximum life cycle of COOKIE , and -1 is no life cycle, that is, it is valid only in the currently opened window. If you close or reopen other windows, authentication will still be required. It can be modified to a number greater than 0 as needed , such as 3600 , which means that within 3600 seconds, open any window without verification. Here we change cookieSecure to false and cookieMaxAge to 3600.
C. Modify the cas of the WEB-INF / spring-configuration / warnCookieGenerator.xml:
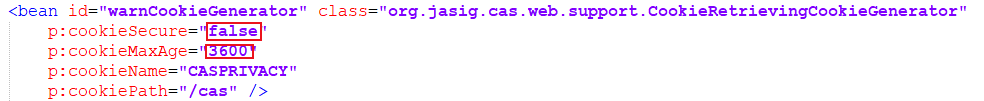
We change cookieSecure to false and cookieMaxAge to 3600 here.
5. Username login
In the deployerConfigContext.xml file under web-inf in the cas server :
<!-- 选择登录用户数据源 -->
<constructor-arg>
<map>
<entry key-ref="proxyAuthenticationHandler" value-ref="proxyPrincipalResolver" />
<entry key-ref="primaryAuthenticationHandler" value-ref="primaryPrincipalResolver" />
</map>
</constructor-arg>The above key-ref="primaryAuthenticationHandler" means to log in with a static username and password configuration. If you want to log in with the username and password in the database, change the value to "dbAuthHandler"
<!-- 静态用户名密码配置 -->
<bean id="primaryAuthenticationHandler" class="org.jasig.cas.authentication.AcceptUsersAuthenticationHandler">
<property name="users">
<map>
<entry key="admin" value="admin"/>
</map>
</property>
</bean>
<!-- 数据库登录用户数据源配置 -->
<bean id="dataSource" class="com.mchange.v2.c3p0.ComboPooledDataSource"
p:driverClass="com.mysql.jdbc.Driver"
p:jdbcUrl="jdbc:mysql://127.0.0.1:3306/登录用户表所在的数据库名?characterEncoding=utf8"
p:user="root"
p:password="root" />
<bean id="passwordEncoder" class="org.jasig.cas.authentication.handler.DefaultPasswordEncoder"
c:encodingAlgorithm="MD5"
p:characterEncoding="UTF-8" />
<bean id="dbAuthHandler" class="org.jasig.cas.adaptors.jdbc.QueryDatabaseAuthenticationHandler"
p:dataSource-ref="dataSource"
p:sql="select 密码 from 表名 where 用户名 = ?"
p:passwordEncoder-ref="passwordEncoder"/>Import the database connection pool dependency package, download address: https://pan.baidu.com/s/13diIxLe9shgliXF-TQfynQ
Cut the decompressed three dependency packages to cas's webapps\cas\WEB-INF\lib .
After selecting the user login data source, log in with the new port number again to log in to the success page:

VI. Logged-in user logout
Browser address bar input: http://localhost:9100/cas/logout
You can see the prompt page after exiting:
