table of Contents
1. Knowledge supplement
1. APP operation process after reinforcement
1. -->APP启动
2. -->壳dex先加载起来
3. -->壳负责把源dex文件读出来
4. -->壳把源dex文件解密
5. -->把解密后的dex加载进内存 源dex运行起来
2. The principle of shelling
After the hardened APP is started, the final source dex file will be loaded into the memory for execution. At this time, the dex file is the dex after the hardening program is decrypted, which is the source code of the app.
The purpose of Android unpacking is to dump the decrypted application dex file from the memory. In order to achieve this purpose, we need to know the dex address and the dex file size of the dex file in the memory. The libart.so library file of the Android system provides an exported OpenMemory function to load the dex file.
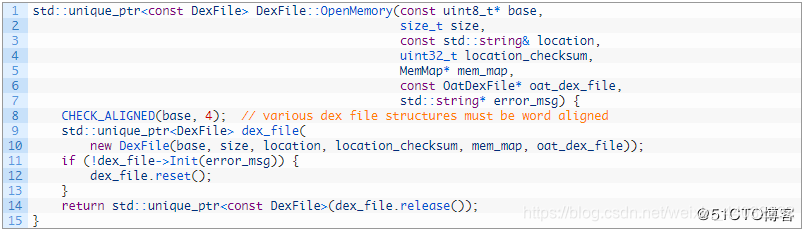
The first parameter of this function points to the dex file in the memory. If we can Hook this function, we can get the starting address of the dex file when it is loaded into the memory, and then calculate the dex file saved in the file header according to the dex file format Length fileSize.
Understand the dex file format: https://www.jianshu.com/p/f7f0a712ddfe
dex starting position: the first parameter of OpenMemory
8个字节 magin ---> dex 035
4个字节 校验位
20个字节 签名
-----从32个字节开始------
4个字节 dex文件大小
Information available:
- dex starting position (the first parameter of OpenMemory)
- dex file size (dex starting position + 32 bytes)
So we can read the data in the memory and write it locally
// 把内存里的数据读出来,从begin(dex在内存中的起始位置)开始读,取length长度(dex_size文件的大小)
file.write(Memory.readByteArray(begin, dex_size))
// 将这段读取出来的数据写入本地
var file = new File("/data/data/%s/" + dex_size + ".dex", "wb")
2. Operation process demonstration
Before writing the Frida script, we need to find the export function name of OpenMemory in the libart.so file. This function name will vary slightly depending on the android version or architecture.
What is the name of this exported function?
It is equivalent to the interface provided by the method in the so file to the outside OpenMemory. The calling form of the method in the so file in the Java code is:
javaCode.OpenMemory的导出函数名
OpenMemory导出函数名与so文件中的OpenMemory方法存在映射关系
java代码中想要调用so库中的OpenMemory方法就以它的导出函数名调用
Different librat.so can be exported according to whether the 64-bit libart.so or 32-bit is used during the application operation.
adb pull /system/lib/libart.so C:\Users\v_mcsong\Desktop
adb pull /system/lib64/libart.so C:\Users\v_mcsong\Desktop
Use 32/64-bit IDA to open the librat.so file to view OpenMemorythe export method name. The export method name may be different for different Android versions.

That is, the call _ZN3art7DexFile10OpenMemoryEPKhjRKNSt3__112basic_stringIcNS3_11char_traitsIcEENS3_9allocatorIcEEEEjPNS_6MemMapEPKNS_10OatDexFileEPS9_is in the so libraryOpenMemory
Shelling script:
Reference open source project: https://github.com/dstmath/frida-unpack/blob/master/frida_unpack.py
#-*- coding:utf-8 -*-
# coding=utf-8
import frida
import sys
def on_message(message, data):
base = message['payload']['base']
size = int(message['payload']['size'])
print(hex(base),size)
# print session
# dex_bytes = session.read_bytes(base, size)
# f = open("1.dex","wb")
# f.write(dex_bytes)
# f.close()
### libart.so
# 9.0 arm 需要拦截 _ZN3art13DexFileLoader10OpenCommonEPKhjS2_jRKNSt3__112basic_stringIcNS3_11char_traitsIcEENS3_9allocatorIcEEEEjPKNS_10OatDexFileEbbPS9_NS3_10unique_ptrINS_16DexFileContainerENS3_14default_deleteISH_EEEEPNS0_12VerifyResultE
# 7.0 arm:_ZN3art7DexFile10OpenMemoryEPKhjRKNSt3__112basic_stringIcNS3_11char_traitsIcEENS3_9allocatorIcEEEEjPNS_6MemMapEPKNS_10OatDexFileEPS9_
# android 10: libdexfile.so
# #_ZN3art13DexFileLoader10OpenCommonEPKhjS2_jRKNSt3__112basic_stringIcNS3_11char_traitsIcEENS3_9allocatorIcEEEEjPKNS_10OatDexFileEbbPS9_NS3_10unique_ptrINS_16DexFileContainerENS3_14default_deleteISH_EEEEPNS0_12VerifyResultE
# 获取包名
package = sys.argv[1]
print("dex 导出目录为: /data/data/%s"%(package))
device = frida.get_usb_device()
pid = device.spawn(package)
session = device.attach(pid)
src = """
Interceptor.attach(Module.findExportByName("libart.so", "_ZN3art7DexFile10OpenMemoryEPKhjRKNSt3__112basic_stringIcNS3_11char_traitsIcEENS3_9allocatorIcEEEEjPNS_6MemMapEPKNS_10OatDexFileEPS9_"), {
onEnter: function (args) {
//dex文件的起始位置
var begin = args[1]
//dex文件的前8个字节是magic字段 看dex的文件格式说明
//打印magic(会显示 "dex 035") 三个字符 可以验证是否为dex文件
console.log("magic : " + Memory.readUtf8String(begin))
//把地址转换成整型 再加32
//因为dex文件的第32个字节处存放的是 dex文件的大小
var address = parseInt(begin,16) + 0x20
//把address地址指向的内存值读出来 该值就是dex的文件大小
//ptr(address)转换的原因是 frida只接受 NativePointer类型指针
var dex_size = Memory.readInt(ptr(address))
console.log("dex_size :" + dex_size)
//frida写文件 把内存中的数据 写到本地
var file = new File("/data/data/%s/" + dex_size + ".dex", "wb")
//Memory.readByteArray(begin, length)
//把内存里的数据读出来,从begin开始读,取length长度(dex_size文件的大小)
file.write(Memory.readByteArray(begin, dex_size))
file.flush()
file.close()
var send_data = {}
send_data.base = parseInt(begin,16)
send_data.size = dex_size
send(send_data)
},
onLeave: function (retval) {
if (retval.toInt32() > 0) {
}
}
});
"""%(package)
script = session.create_script(src)
script.on("message" , on_message)
script.load()
device.resume(pid)
sys.stdin.read()


Use jadx to open one by one to see which dex file is the source code of the app.
Reference article: https://blog.51cto.com/yeshaochen/2496524