Remote access and control (detailed)-SSH remote management and TCP Wrappers access control
1. SSH remote management
1. Definition
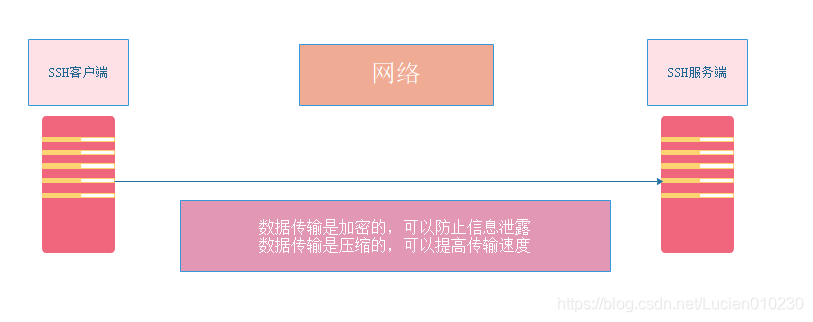
SSH (Secure Shell) is a secure channel protocol, which is mainly used to realize remote login and remote copy functions of the character interface.
The SSH protocol encrypts the data transmission between the communicating parties, including the user password entered when the user logs in. Therefore, the SSH protocol has good security.
2. Advantages
3. Client and server
- Client: Putty, Xshell, CRT
- Server: OpenSSH
-OpenSSH is an open source software project that implements the SSH protocol and is suitable for various UNIX and Linux operating systems.
-CentOS 7 system has installed openssh related software packages by default, and has added the sshd service as a boot-up.
4. SSH service opening, port number and configuration file
- Start the SSH service
-execute the "systemctl start sshd" command to start the sshd service - Port number of the SSH service-The
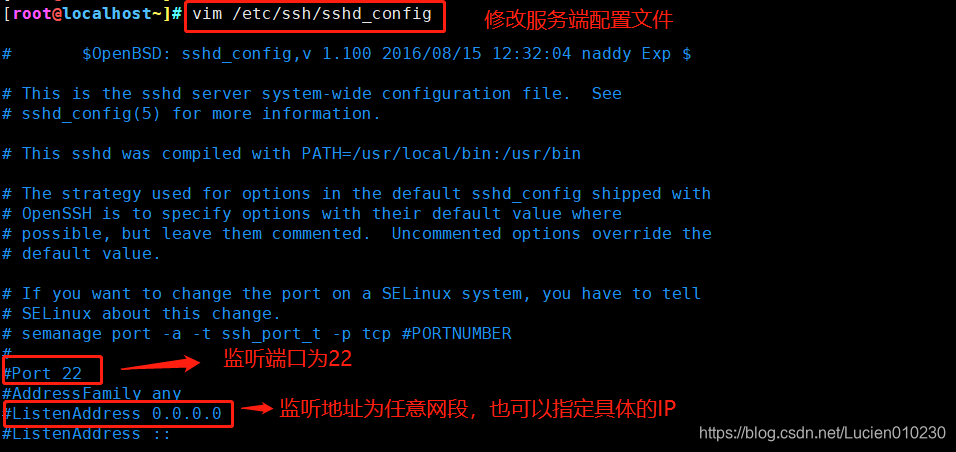
default port number used by the sshd service is 22 - SSH service configuration file
-sshd_config is the configuration file for the server
-ssh_config is the configuration file for the client
2. Configure the OpenSSH server
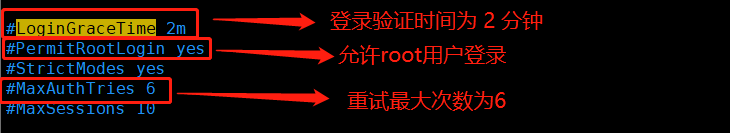
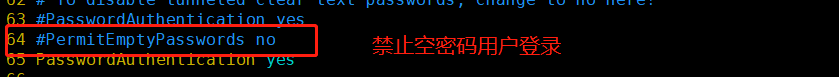
1. Commonly used setting options for configuration files
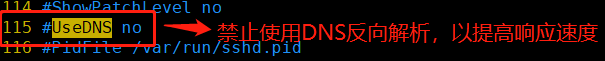
2、AllowUsers和DenyUsers

Three, use the SSH client program
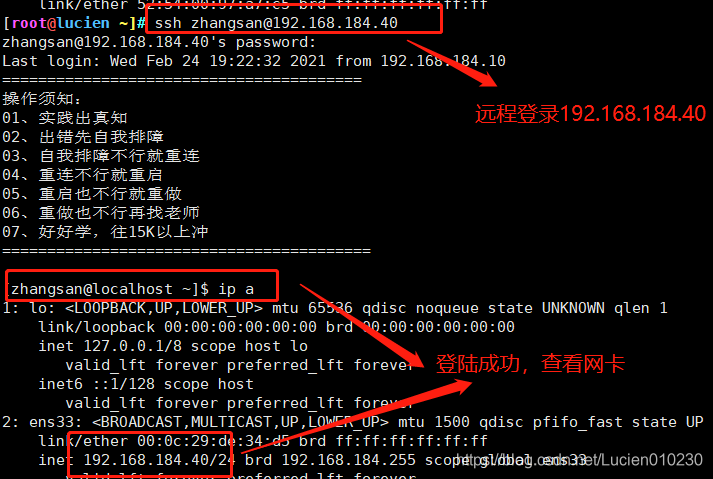
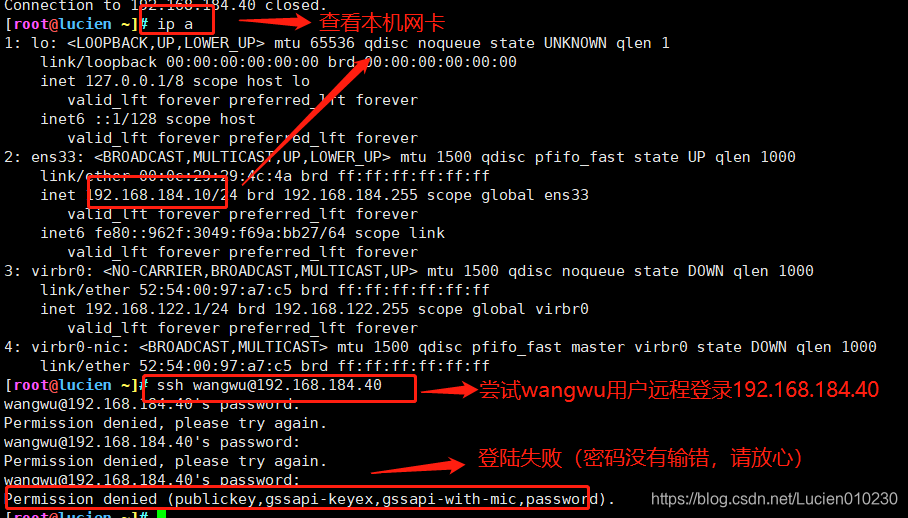
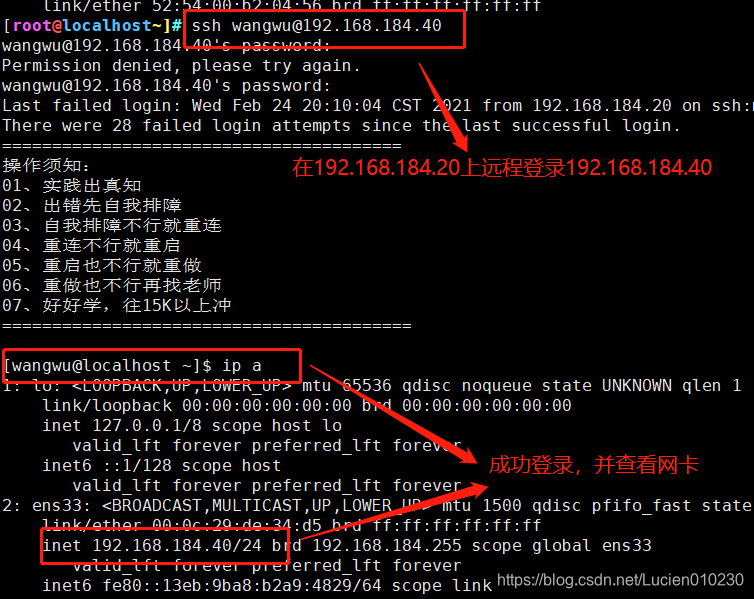
1. SSH remote login

When the user logs in to the SSH server for the first time, he must accept the ECDSA key sent by the server (enter "yes" as prompted) before proceeding with the verification. The received secret key information will be saved in the ~/.ssh/known_hosts file. After the password verification is successful, you can log in to the command environment of the target server.
| Options | Description |
|---|---|
| -1 | Mandatory use of ssh protocol version 1 |
| -2 | Mandatory use of ssh protocol version 2 |
| -4 | Mandatory use of IPv4 addresses |
| -6 | Mandatory use of IPv6 addresses |
| -A | Enable authentication proxy connection forwarding function |
| -a | Disable the authentication proxy connection forwarding function |
| -b | Use the address specified by this machine as the source IP address of the counterpoint connection |
| -C | Request to compress all data |
| -F | Specify the configuration file of the ssh command, the default configuration file is "/etc/ssh/ssh_config" |
| -f | Execute ssh commands in the background |
| -g | Allow remote hosts to connect to the forwarding port of this machine |
| -i | Specify the identity file (that is, the private key file) |
| -l | Specify the login user name to connect to the remote server |
| -N | Do not execute remote commands |
| -The | Specify configuration options |
| -p | Specify the port on the remote server |
| -q | Silent mode, all warning and diagnostic messages are prohibited from output |
| -X | Enable X11 forwarding function |
| -x | Disable X11 forwarding function |
| -Y | Turn on the trust X11 forwarding function |
2. SCP remote replication
①, Downstream copy

② Uplink copy

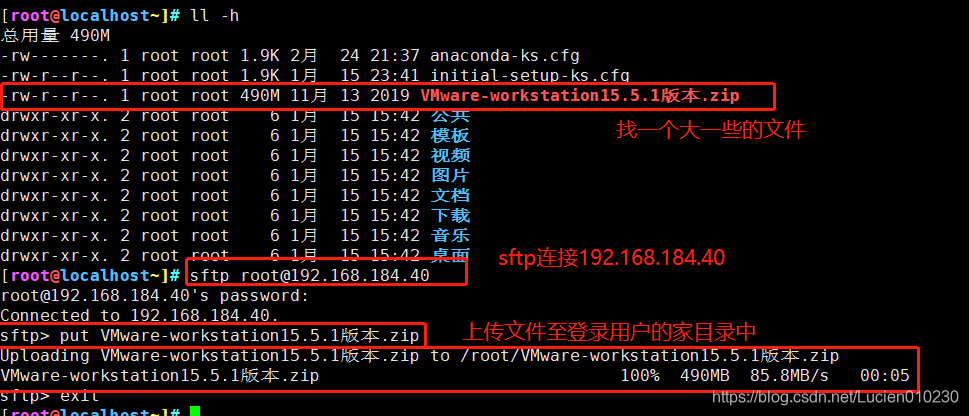
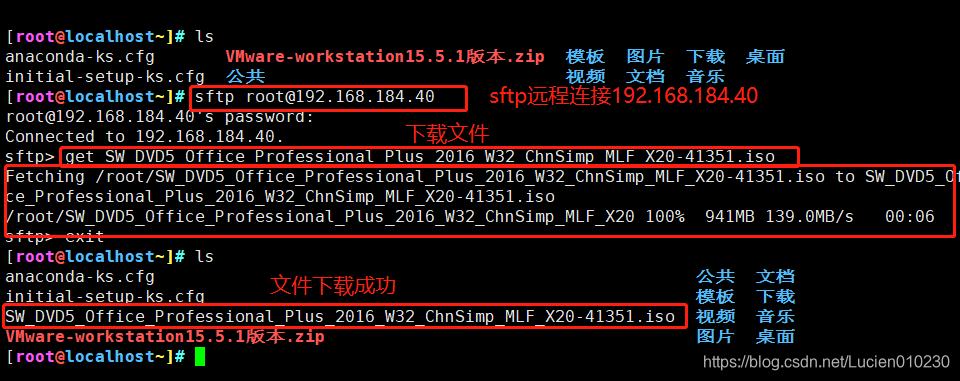
3. sftp secure FTP
Due to the use of encryption/decryption technology, the transmission efficiency is lower than ordinary FTP, but the security is higher.
sftp root@192.168.184.40
root@192.168.184.40's password:
Connected to 192.168.184.40.
sftp> ls
sftp> get 文件名 #下载文件
sftp> put 文件名 #上传文件
sftp> exit #退出
Four, sshd service supports two verification methods
1. Password verification
- Verify the login name and password of the local system user in the server. Simple, but may be brute-forced
2. Secret key pair verification
- The matching key information is required to pass the verification. Usually, a pair of key files (public key, private key) are created in the client first, and then the public key file is placed in the specified location on the server. When logging in remotely, the system will use the public key and private key to verify the encryption/decryption association. Can enhance security, and can avoid interactive login.
- When both password verification and key pair verification are enabled, the server will preferentially use key pair verification. The verification method can be set according to the actual situation.
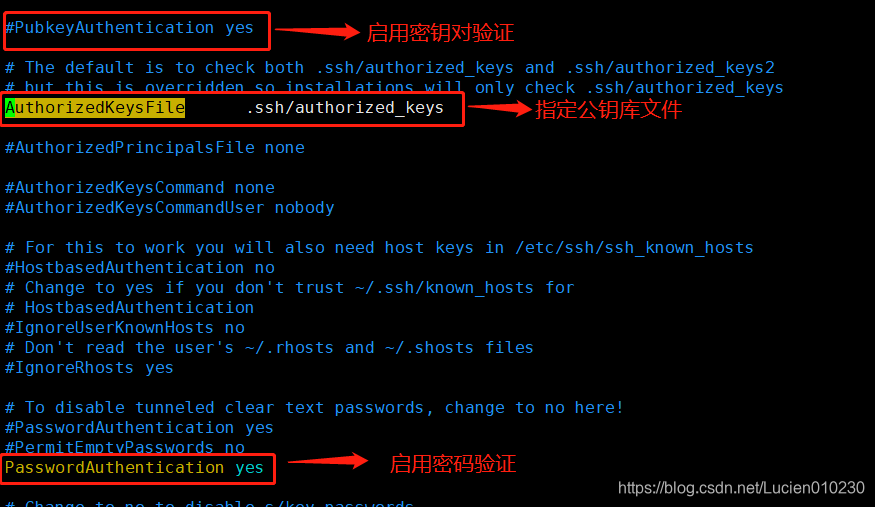
vim /etc/ssh/sshd_config
PasswordAuthentication yes #启用密码验证
PubkeyAuthentication yes #启用密钥对验证
AuthorizedKeysFile .ssh/authorized_keys #指定公钥库文件
①, create a secret key pair on the client
Create a key pair file for the current user through the ssh-keygen tool. The available encryption algorithms are RSA, ECDSA, or DSA, etc. (The "-t" option of the ssh-keygen command is used to specify the algorithm type).
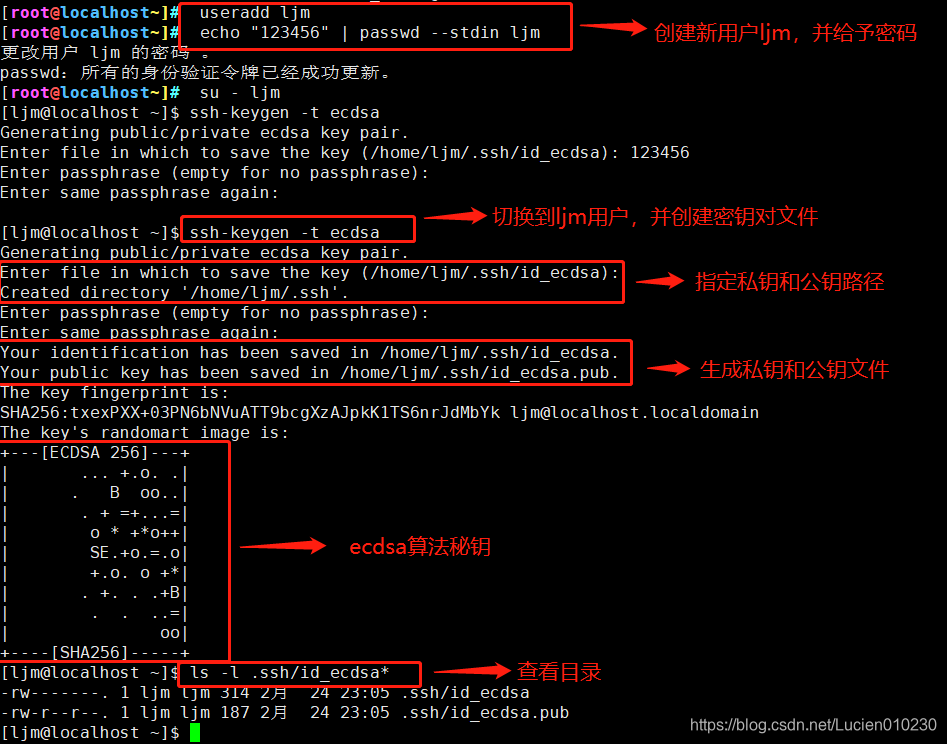
useradd ljm
echo "123456" | passwd --stdin ljm
su - ljm
ssh-keygen -t ecdsa
Generating public/private ecdsa key pair.
Enter file in which to save the key (/home/ljm/.ssh/id_ecdsa): #指定私钥位置,直接回车使用默认位置
Created directory '/home/ljm/.ssh'. #生成的私钥、公钥文件默认存放在宿主目录中的隐藏目录.ssh/下
Enter passphrase (empty for no passphrase): #设置私钥的密码
Enter same passphrase again: #确认输入
ls -l .ssh/id_ecdsa* #id_ecdsa是私钥文件,权限默认为600;id_ecdsa.pub是公钥文件,用来提供给 SSH 服务器
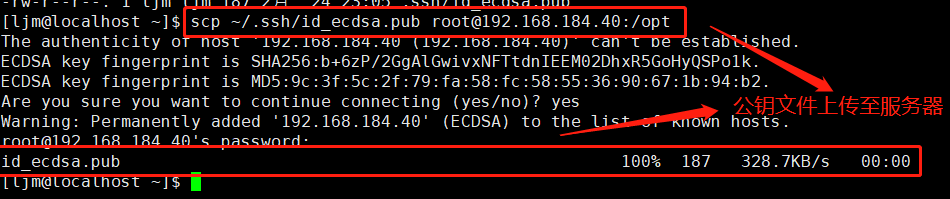
② Upload the public key file to the server
scp ~/.ssh/id_ecdsa.pub root@192.168.184.20:/opt
或
#此方法可直接在服务器的/home/ljm/.ssh/目录中导入公钥文本
cd ~/.ssh/
ssh-copy-id -i id_ecdsa.pub zhangsan@192.168.184.20
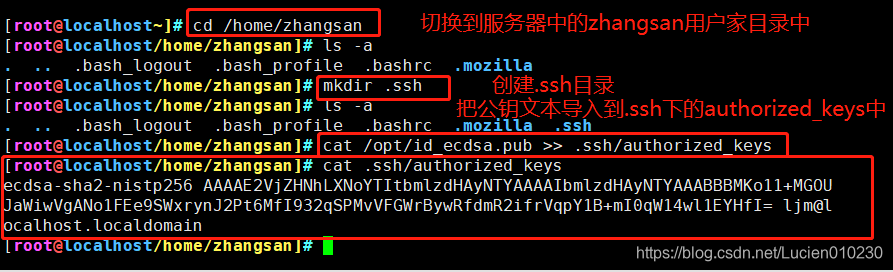
③. Import the public key text in the server
mkdir /home/zhangsan/.ssh/
cat /tmp/id_ecdsa.pub >> /home/zhangsan/.ssh/authorized_keys
cat /home/zhangsan/.ssh/authorized_keys
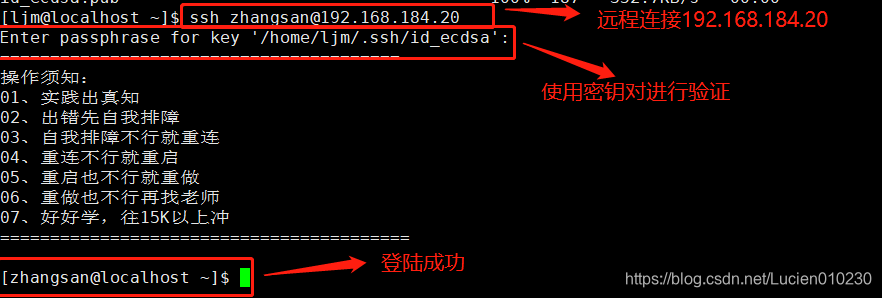
④, use the secret key pair to verify on the client
ssh zhangsan@192.168.184.20
lucien@192.168.184.20's password: #输入私钥的密码
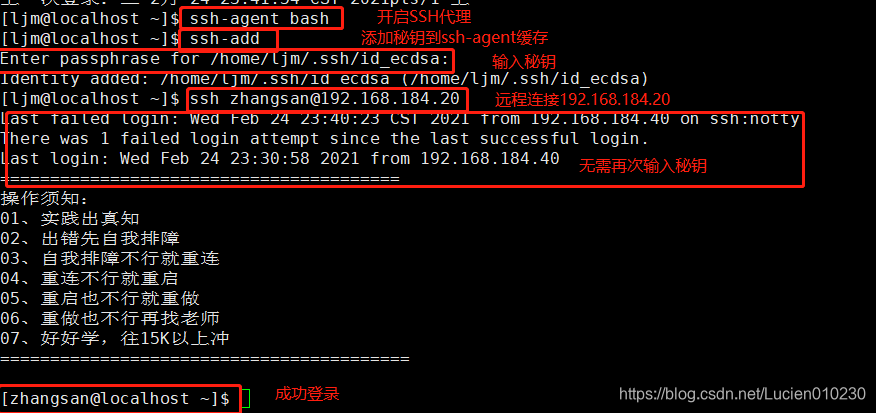
⑤, set the ssh proxy function on the client to realize interactive login
ssh-agent bash
ssh-add
Enter passphrass for /home/zhangsan/.ssh/id_ecdsa: #输入私钥的密码
ssh zhangsan@192.168.184.20
Five, TCP Wrappers access control
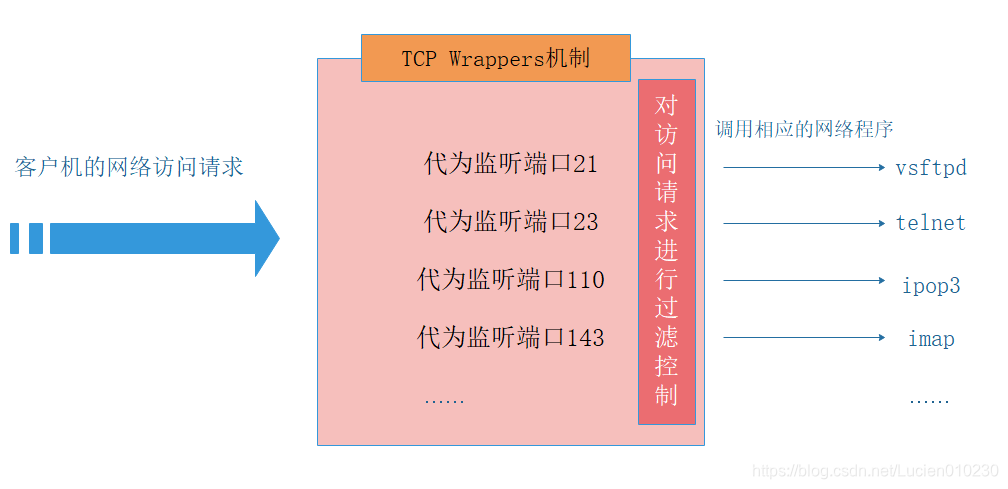
- TCP Wrappers "wraps" the TCP service program, and monitors the port of the TCP service program on behalf of it, adding a security detection process. The external connection request must pass this layer of security detection first, and then the real service program can be accessed after obtaining permission.
- In most Linux distributions, TCP Wrappers is a feature provided by default.

1. Two ways to realize the protection mechanism
- To directly use the tcpd program to protect other service programs, you need to run the tcpd program.
- The libwrap.so.* link library is called by other network service programs without running the tcpd program. This method is more widely used and more efficient.
①, view the program's libwrap.so.* link library-ldd command

| Common parameters | Description |
|---|---|
| -v | Detailed information mode, print all relevant information |
| -u | Print unused direct dependencies |
| -d | Perform relocation and report any missing objects |
| -r | Perform relocation of data objects and functions, and report any missing objects and functions |
| – -help | Display help information |
- The file needs to write the absolute path
- When we are not very clear about the absolute path of the file, we can use the which command to query
- You can also use two commands together: ldd $(which sshd)
2. The access strategy of TCP Wrappers
- The protection objects of the TCP Wrappers mechanism are various network service programs, and access control is performed on the client address of the access service.
- The corresponding two policy files are /etc/hosts.allow and /etc/hosts.deny, which are used to set allow and deny policies respectively.

| Service program list | ALL | Represents all services |
|---|---|---|
| Single service program | Such as "vsftpd" | |
| List of multiple service programs | Such as "vsftpd,sshd" | |
| Client address list | ALL | Represents any client address |
| LOCAL | Represents the local address | |
| Multiple addresses are separated by commas | ||
| Wildcards allowed | * | Represents characters of any length |
| ? | Only represents one character | |
3. Basic principles of TCP Wrappers mechanism
-
First check the /etc/hosts.allow file, if a matching policy is found, then access is allowed;
-
Otherwise, continue to check the /etc/hosts.deny file, if a matching policy is found, access is denied;
-
If no matching policy is found after checking the above two files, then access is allowed.
-
Allow all, deny individual,
just add the corresponding deny policy in the /etc/hosts.deny file -
Allow individual, deny all
In addition to adding an allow policy in /etc/hosts.allow, you also need to set an "ALL:ALL" deny policy in the /etc/hosts.deny file.
4. Example
You only want to access the sshd service from a host with an IP address of 12.0.0.1 or a host on the 192.168.80.0/24 network segment, and other addresses are rejected.
vi /etc/hosts.allow
sshd:12.0.0.1,192.168.80.*
vi /etc/hosts.deny
sshd:ALL