You may have seen a similar article I wrote before, why do you have to repeat it? I just want to better help beginners understand virus reverse analysis and system security, and be more systematic without destroying the previous series. Therefore, I reopened this column to prepare systematically and in-depth study of system security, reverse analysis and malicious code detection. The "System Security" series of articles will be more focused, more systematic, and more in-depth. It is also the author's slow growth history. It is really difficult to change majors. Reverse analysis is also a hard part, but I will also try to see how much I can learn from it in the next four years. Enjoy the process, come on together~
The author introduced the knowledge of macro virus in the previous article. It is still active in various APT attack samples. The specific content includes the basic principles of macro virus, defense measures, spontaneous emails and APT28 sample analysis. This article will introduce in detail what is a digital signature, and use Signtool to sign EXE files, and then in-depth analysis of the digital signature format and PE virus content. This basic knowledge is not only related to system security, but also closely related to the commonly used software, documents, and operating systems around us. I hope that this knowledge will be helpful to you, and I hope everyone will raise their security awareness, and that security protection has a long way to go. This article refers to the articles in the references, combined with my own experience and practice to write, I also recommend that you read the references.
Article Directory
Starting in July 2019, I came to an unfamiliar profession-cyberspace security. It is very painful and uncomfortable to enter the security field for the first time. There are too many things to learn and the coverage is too wide, but fortunately, I am struggling to move forward by sharing 100 articles in the "Network Security Self-study" series. I am grateful to the security bosses and friends who have met, acquainted, and enjoyed each other this year. If the writing is not good or insufficient, please Haihan!
Next, I will open a new security series called "System Security", which is also a free 100 articles. The author will study malicious sample analysis, reverse analysis, intranet penetration, actual network attack and defense, etc., and will also go online Sharing the form of notes and practical operations and learning with bloggers, I hope to progress with you, come on~
- Recommended previous article: Network Security Self-study Series-100
Author's github resources:
- Reverse analysis: https://github.com/eastmountyxz/SystemSecurity-ReverseAnalysis
- Network Security: https://github.com/eastmountyxz/NetworkSecuritySelf-study
Preamble analysis:
- [System Security] 1. What is reverse analysis, the basis of reverse analysis and the reverse of classic minesweeping games
- [System Security] 2. How to learn reverse analysis and Lü Buchuan game reverse case
- [System Security] III. IDA Pro disassembly tool first knowledge and reverse engineering decryption actual combat
- [System Security] 4. The basic usage of OllyDbg dynamic analysis tool and the reverse engineering of Crakeme
- [System Security] 5. OllyDbg and Cheat Engine tools reverse analysis of the Plants vs. Zombies game
- [System Security] 6. Reverse analysis of conditional statements and loop statements source code restoration and flow control
- [System Security] 7. PE virus principle of reverse analysis, C++ implementation of file encryption and decryption and OllyDbg reverse engineering
- [System Security] 8. CVE-2019-0708 Recurrence and Blue Screen Attack of Windows Vulnerability Exploitation
- [System Security] 9. Windows vulnerability exploitation of MS08-067 remote code execution vulnerability reproduction and in-depth privilege escalation
- [System Security] X. Windows vulnerability exploitation of SMBv3 service remote code execution vulnerability (CVE-2020-0796) recurrence
- [System Security] 11. Analysis of the behavior mechanism of panda burning incense and PE virus in those years
- [System Security] 12. Panda Burning Incense Virus IDA and OD Reverse Analysis (Part I) Virus Initialization
- [System Security] XIII. IDA and OD reverse analysis of panda burning incense virus (medium) virus release mechanism
- [System Security] 14. Panda Burning Incense Virus IDA and OD Reverse Analysis-Virus Release Process (Part 2)
- [System Security] 15. Chrome browser password retention function penetration analysis, blue screen vulnerability and recurrence of a music software vulnerability
- [System Security] 16. Basic knowledge of PE file reverse engineering (PE analysis, PE editing tools and PE modification)
- [System Security] 17. Windows PE virus concept, classification and infection method detailed
- [System Security] 18. Virus attack and defense mechanism and WinRAR malicious hijacking vulnerabilities (script virus, self-starting, scheduled shutdown, blue screen attack)
- [System Security] 19. The basics of macro virus entry, defense measures, spontaneous emails and analysis of APT28 macro samples
- [System Security] 20. PE Digital Signature (Part 1) What is a digital signature and a detailed explanation of Signtool signature tool
Statement: I firmly oppose the use of teaching methods to commit crimes. All crimes will be severely punished. We need to maintain the green network together. It is recommended that you understand the principles behind them and better protect them. The sample will not be shared with everyone, the analysis tool will. (See the references below)
1. Digital signature of PE file
1. Concept popularization
(1) PE file
The full name of PE file is Portable Executable, which means portable executable file. Common EXE, DLL, OCX, SYS, and COM are all PE files. PE files are program files on Microsoft Windows operating system (maybe indirectly Execution, such as DLL). A follow-up article will analyze the PE file format in detail.
(2) Why do we need to digitally sign PE files?
- Anti-tampering : Through the verification of the digital signature, it is ensured that the file has not been illegally tampered with.
- Reduce false positives : Security software reduces false positives by verifying whether the file has a digital signature from a regular manufacturer.
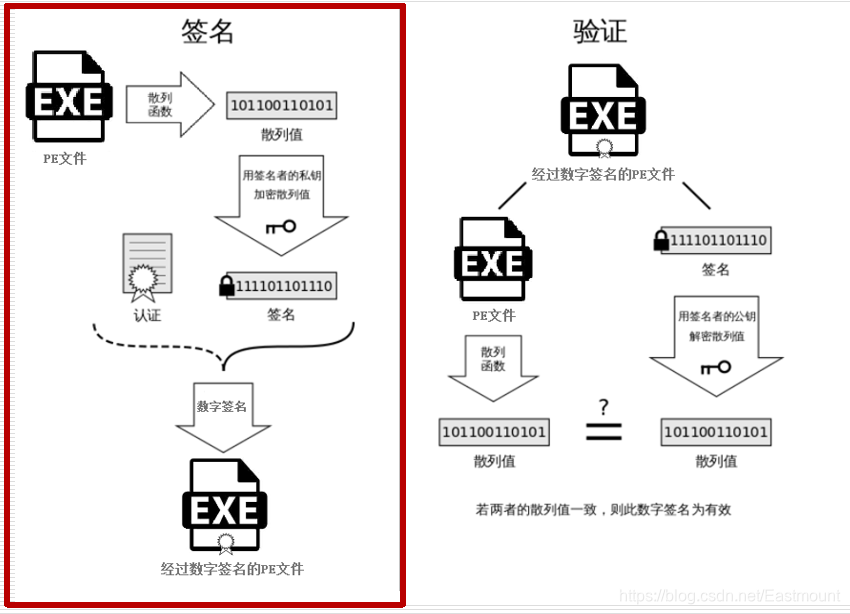
(3) PE file digital signature and verification process
signature:
- The software publisher uses a hash algorithm (such as MD5 or SHA) to calculate the hash value of the PE file.
- The software publisher uses the private key to sign the hash value to obtain the signature data.
- The public key and signature data corresponding to the signed private key are attached to the PE file in the form of a certificate to form a digitally signed PE file.
- The software publisher will publish the digitally signed PE file.
verification:
- Extract the public key of the software publisher, the hash algorithm used, the signature algorithm, and the signature data of the original hash value from the PE file certificate.
- Use the extracted public key and the corresponding signature verification algorithm to restore the signature data to the original hash value of the original PE file.
- Use the same hash algorithm for the existing PE file to calculate the corresponding hash value.
- Compare whether the two hash values are consistent to determine whether the data has been destroyed or tampered with.
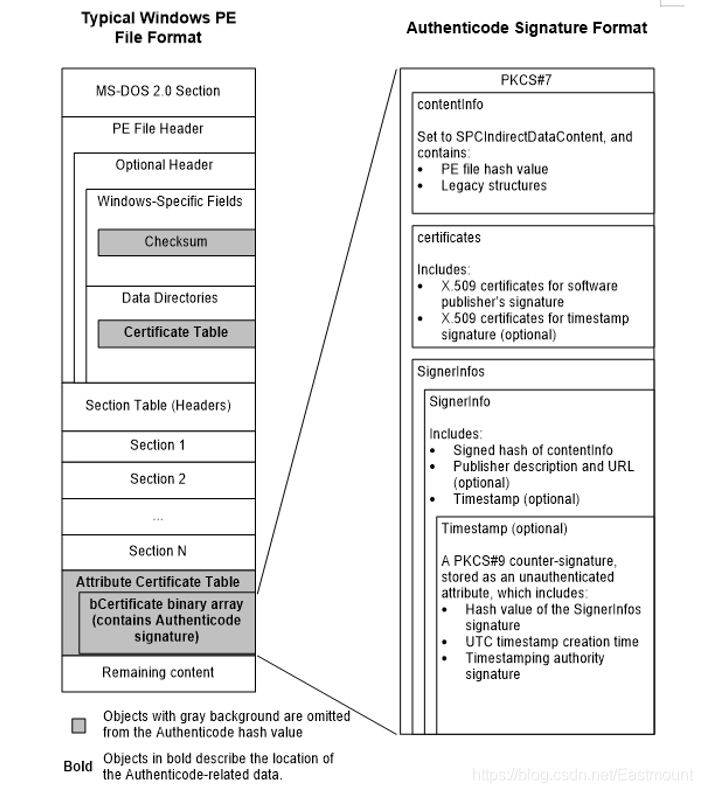
(4) The overall structure of the digital signature of the PE file
The digital signature information of the PE file is stored in the Certificate Table location, and the fifth item of the optional file header DataDirecotry of the PE file records the file offset and size.
The author of the next article attempts to explain in detail the structure of the PE file and signature analysis.
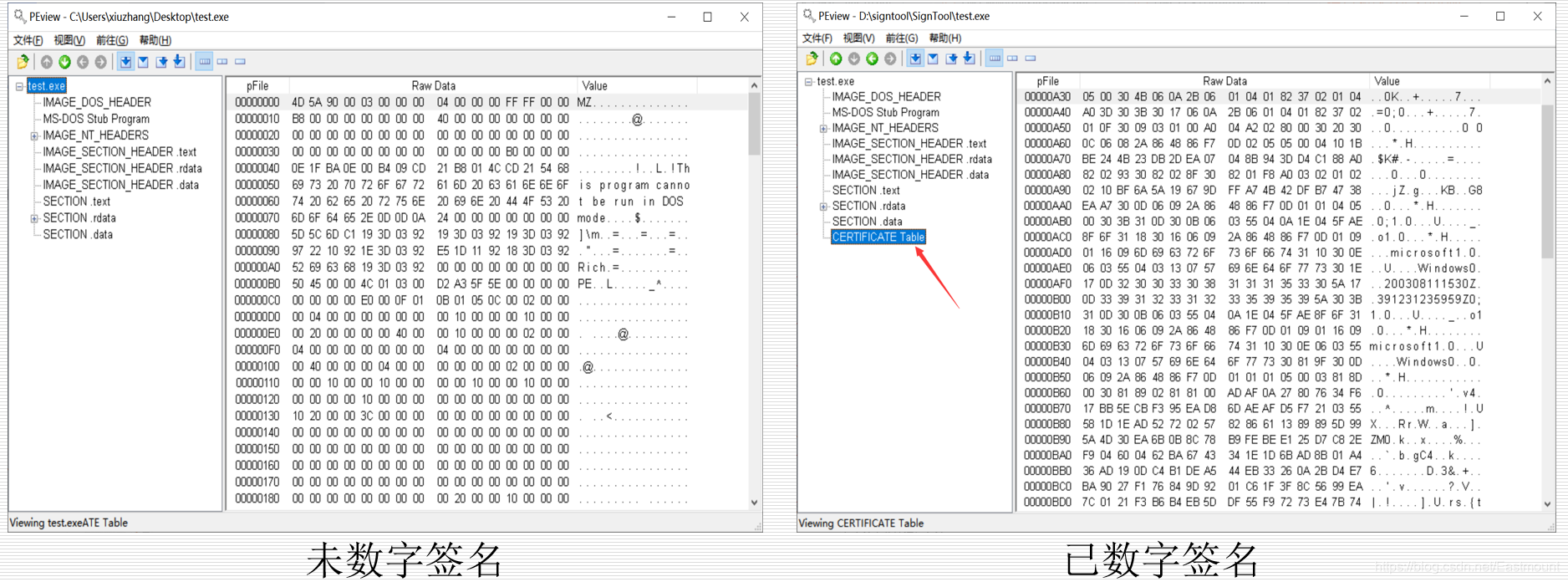
Use PEView to view the comparison chart before and after the signature, and you can see that the Certificate Table stores related signature information.
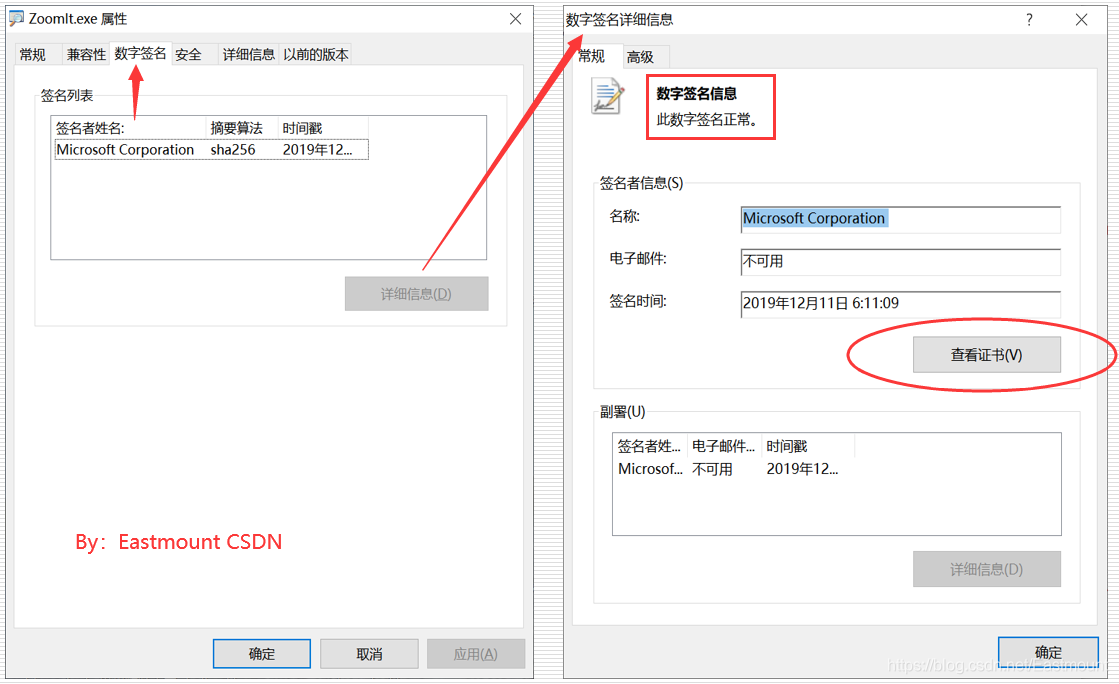
(5) PE file digital signature view
Taking the Zoomit.exe program as an example, we can see that the digitally signed PE file will have an additional "digital signature" attribute. Click on the detailed information to view the corresponding certificate.
The corresponding certificate information and certificate path are shown in the figure below, including signature algorithm, hash algorithm, validity period, issuer information, etc.

(6) View of Microsoft digital signature certificate
Next, I will show you the Windows certificate. Enter "certmgr.msc" during operation, and you can see that there are 5 system default ECC signed root certificates, as shown in the figure below.
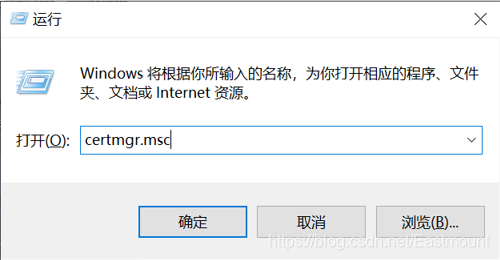
We export one of the root certificates at will, and export it directly and choose the Base64 encoding one.
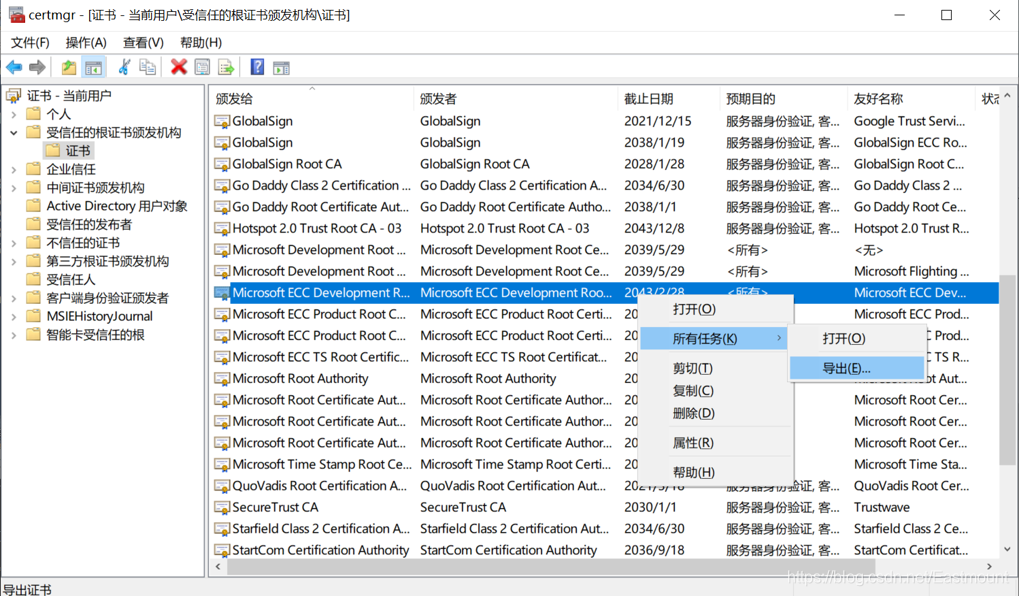
You can see the exported ECC key certificate as shown in the figure below, including information such as the validity period of the certificate. This is the digital certificate that Microsoft is implementing the Elliptic Curve Encryption (ECC) algorithm, located in the CryptoAPI.dll file, which is also a signature vulnerability that we use to forge trusted sources.

(7) Common algorithms and application areas of digital signatures
Commonly used algorithms for digital signatures include:
- RSA digital signature algorithm
based on big integer factorization problem, MD5, SHA - DSA digital signature algorithm
based on discrete logarithm problem - ECDSA elliptic curve digital signature algorithm
ECC+DSA, elliptic encryption algorithm, belongs to a variant of DSA, based on the discrete logarithm problem on elliptic curve
Its application areas include:
- PE file digital signature
- HTTPS digital signature
- Email digital signature
- Office document digital signature
- Code digital signature
2. Github website certificate verification process
Then look at the process of Microsoft certificate verification on the Github website.
- When a website (such as Github.com) is accessed on a Windows system, the website will send a website certificate signed by a third-party authority (CA) to the Windows system.
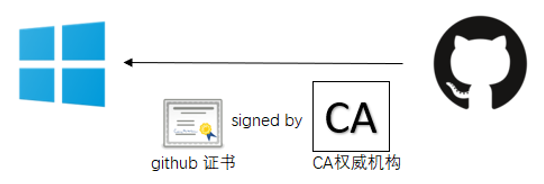
- The Windows system will verify whether the certificate is issued by the CA. If the verification is passed, the Windows system and the website will successfully establish a TLS link.
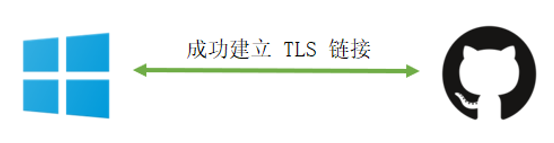
- In order to facilitate the next faster access, Windows puts the successfully verified certificate into a Certificate Cache (certificate cache) in memory. In the next verification, if the certificate exists in the cache, the value in the cache is directly taken for verification. CVE-2020-0601 is used here.
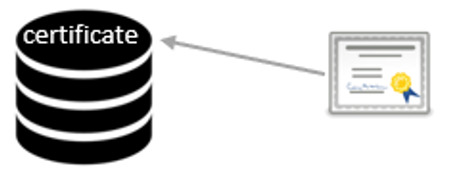
- After successfully caching the certificate data, according to the Windows certificate caching mechanism described below, a malicious website can forge a fake website (such as github.com) certificate and pass Windows verification, disguising itself as a legitimate website.
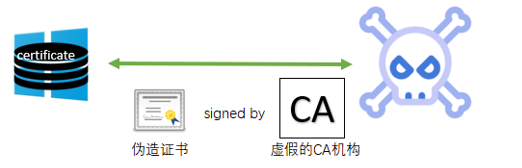
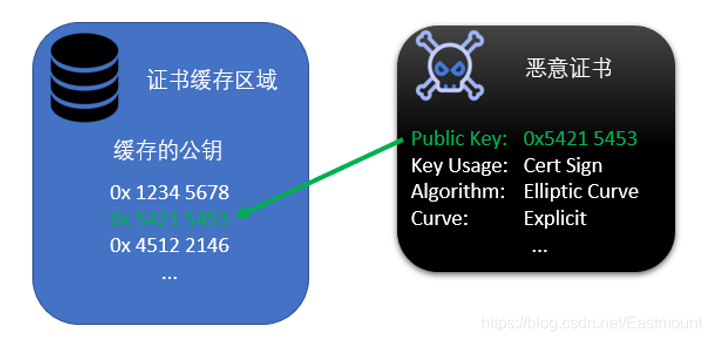
- When Windows receives a new certificate, Windows traverses and compares the public key of the newly received certificate and the certificate of the cached certificate to find a matching value.
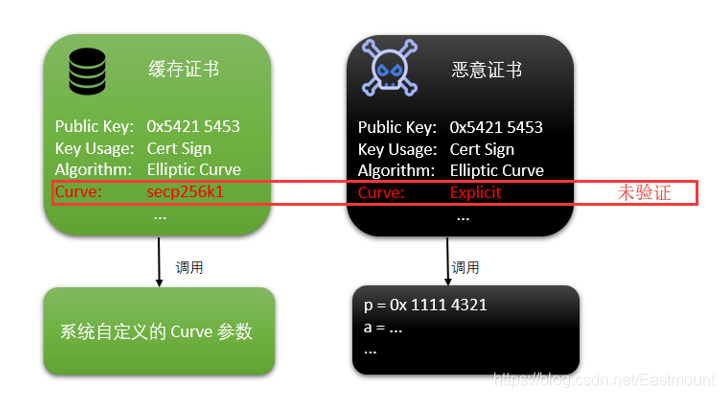
- The forged malicious certificate has the same public key as the cached certificate in the Windows system, but the Curve item is not within the verification range, so the certificate can be forged by constructing a custom Curve. The certificate verification process is still established, but the certificate that passes the verification is no longer the security certificate that was successfully verified before.
In the 23rd article, we will reproduce the Microsoft certificate CVE-2020-0601 vulnerability in detail.
2. Teacher Ruan Yifeng tells everyone what a digital signature is
Reference article:
What is a digital signature? -Ruan Yifeng What is a Digital Signature? -Original
website
At this point, you may still be wondering "What is a digital signature"? Next, I will explain through the blog of Teacher Ruan Yifeng. Personally, I think this is a more clear principle article, and it also contains the knowledge of encryption and decryption, information transmission in network security.
(1) Suppose Bob has two keys, one is a public key and the other is a private key.

(2) Bob gave the public key to his friends-Patty, Doug, Susan-each one.

(3) Susan wants to write a confidential letter to Bob. After she finishes writing, encrypt it with Bob's public key to achieve confidentiality.

(4) After receiving the letter, Bob decrypts it with the private key, and then he sees the content of the letter. What I want to emphasize here is that as long as Bob's private key is not leaked, this letter is safe and cannot be decrypted even if it falls into the hands of others.

(5) Bob wrote back to Susan and decided to use a "digital signature". After he finishes writing, he uses the Hash function to generate a digest of the letter.

(6) Then, Bob uses the private key to encrypt the digest to generate a "digital signature" (signature).

(7) Bob attached this signature to the letter and sent it to Susan.

(8) After receiving the letter, Susan removes the digital signature and decrypts it with Bob's public key to get the abstract of the letter. This proves that this letter was indeed sent by Bob.

(9) Susan then uses the Hash function on the letter itself, and compares the result with the summary obtained in the previous step. If the two are consistent, it proves that the letter has not been revised.

(10) A complicated situation has emerged. Doug wanted to deceive Susan. He secretly used Susan's computer and exchanged his own public key for Bob's public key. At this time, Susan actually possessed Doug's public key, but thought it was Bob's public key. Therefore, Doug can pretend to be Bob, make a "digital signature" with his private key, write to Susan, and let Susan use the fake Bob public key to decrypt.

(11) Later, Susan felt something wrong and found that she could not determine whether the public key really belonged to Bob. She thought of a way and asked Bob to find a "certificate authority" (CA) to certify the public key. The certificate authority uses its own private key to encrypt Bob's public key and some related information to generate a "digital certificate" (Digital Certificate).

(12) After Bob gets the digital certificate, he can rest assured. To write to Susan in the future, as long as the signature is accompanied by a digital certificate.

(13) After receiving the letter, Susan uses the CA's public key to unlock the digital certificate, and you can get Bob's real public key, and then you can prove whether the "digital signature" is really signed by Bob.

(14) Next, let's look at an example of using "digital certificate": https protocol. This protocol is mainly used for web page encryption. First, the client sends an encryption request to the server.

(15) After the server encrypts the web page with its own private key, it sends it to the client together with its own digital certificate.

(16) The "Certificate Manager" of the client (browser) has a list of "Trusted Root Certification Authorities". According to this list, the client will check whether the public key to unlock the digital certificate is in the list.

(17) If the web address recorded in the digital certificate is inconsistent with the web address you are browsing, it means that the certificate may be fraudulently used and the browser will issue a warning.

(18) If this digital certificate is not issued by a trusted organization, the browser will issue another warning. If the digital certificate is reliable, the client can use the server public key in the certificate to encrypt the information, and then exchange encrypted information with the server.


Digital signature is to ensure data integrity. It can be used to judge whether the data has been tampered with, and all the data encrypted by the private key can be decrypted by knowing the public key, which is not safe. The function of private key encryption is to confirm the identity, and decrypt the digest with the corresponding public key to prove who the digest comes from and play the role of signature.
3. Signtool signs PE files
- Reverse analysis: https://github.com/eastmountyxz/SystemSecurity-ReverseAnalysis
- Software security: https://github.com/eastmountyxz/Software-Security-Course
Follow-up articles of the test.exe program will also be shared and uploaded to Github.
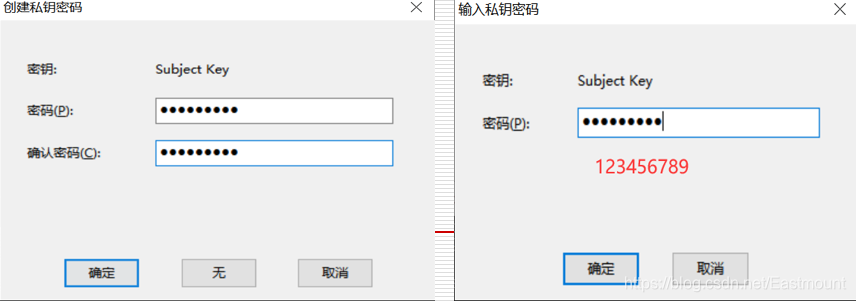
The first step is to generate the required certificate through makecert.exe, and generate two files, test.cer and test.PVK.
cd SignTool
makecert -$ "individual" -r /sv "test.PVK" /n "CN=Windows,E=microsoft,O=微软" test.cer

During the creation process, you need to enter the private key password, which is set to "123456789" here.
The second step is to check the certificate information, if it is not trusted, click "Install Certificate".

Install and trust the certificate.

The third step is to use the signcode.exe tool to sign the data and select the "test.exe" program that needs to be signed.
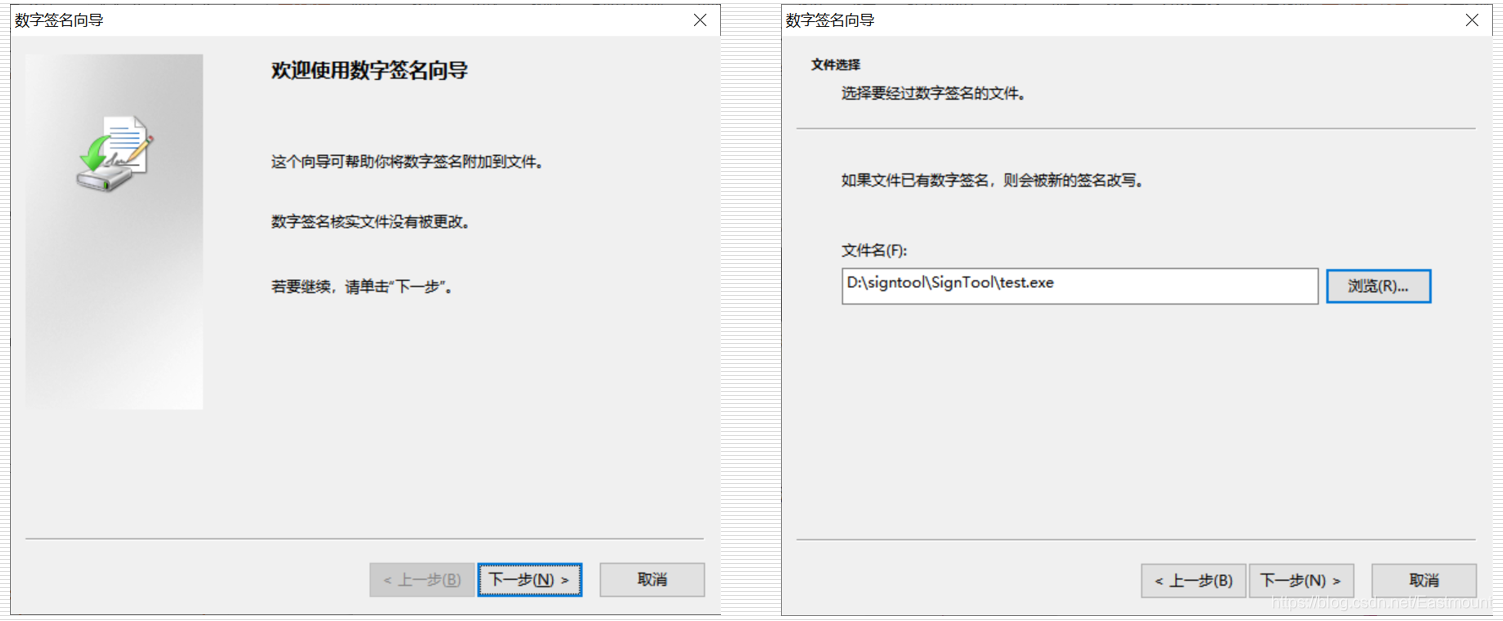
The fourth step is to automatically select the custom option, and then click to select the test.cer file from the file, the test.cer file is in the directory you generated in the first step, and then the next step.
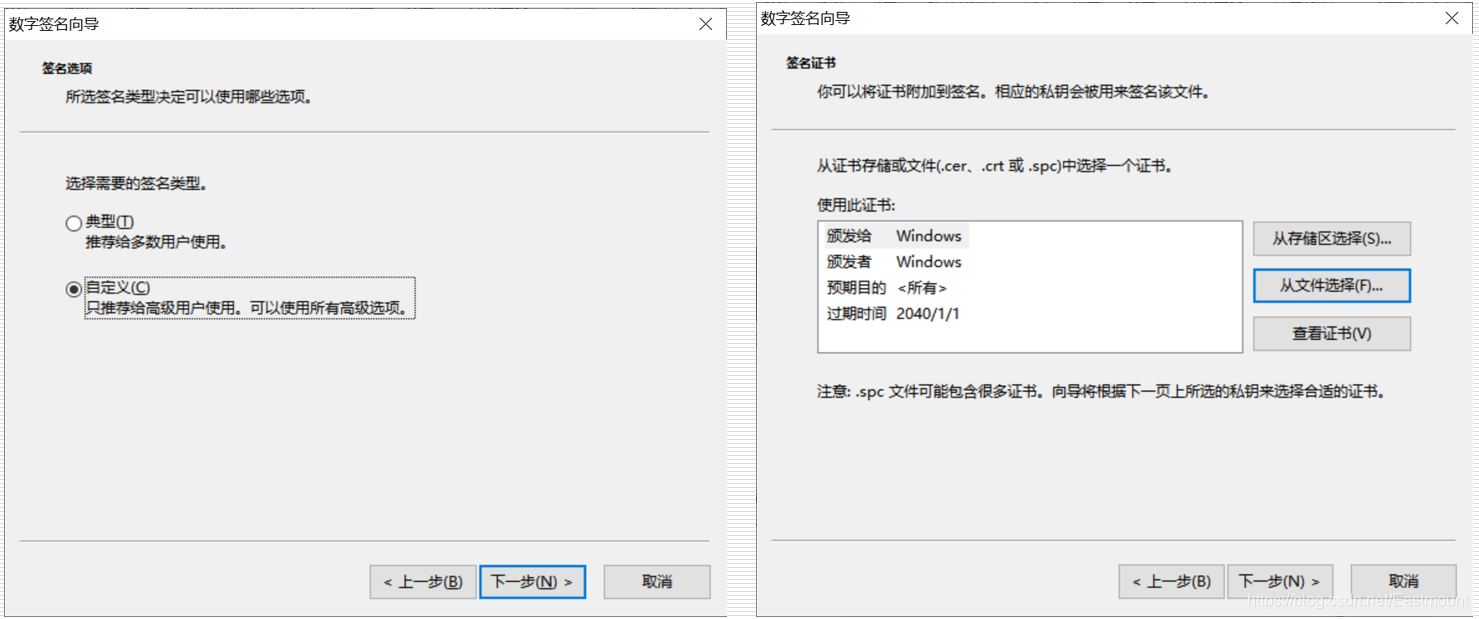
The fifth step, click the browse button, add the file test.PVK, the test.PVK file is also in the directory generated in the first step, click Next, the hash algorithm can be md5, or sha1, and click Next.

The sixth step, click Next by default, and a data description box will appear. You can fill it in or leave it blank. Click Next.

The seventh step is to fill in the URL of the timestamp server: http://timestamp.wosign.com/timestamp, or you can choose not to add a timestamp, click Next to finish, and a successful signing box will pop up.

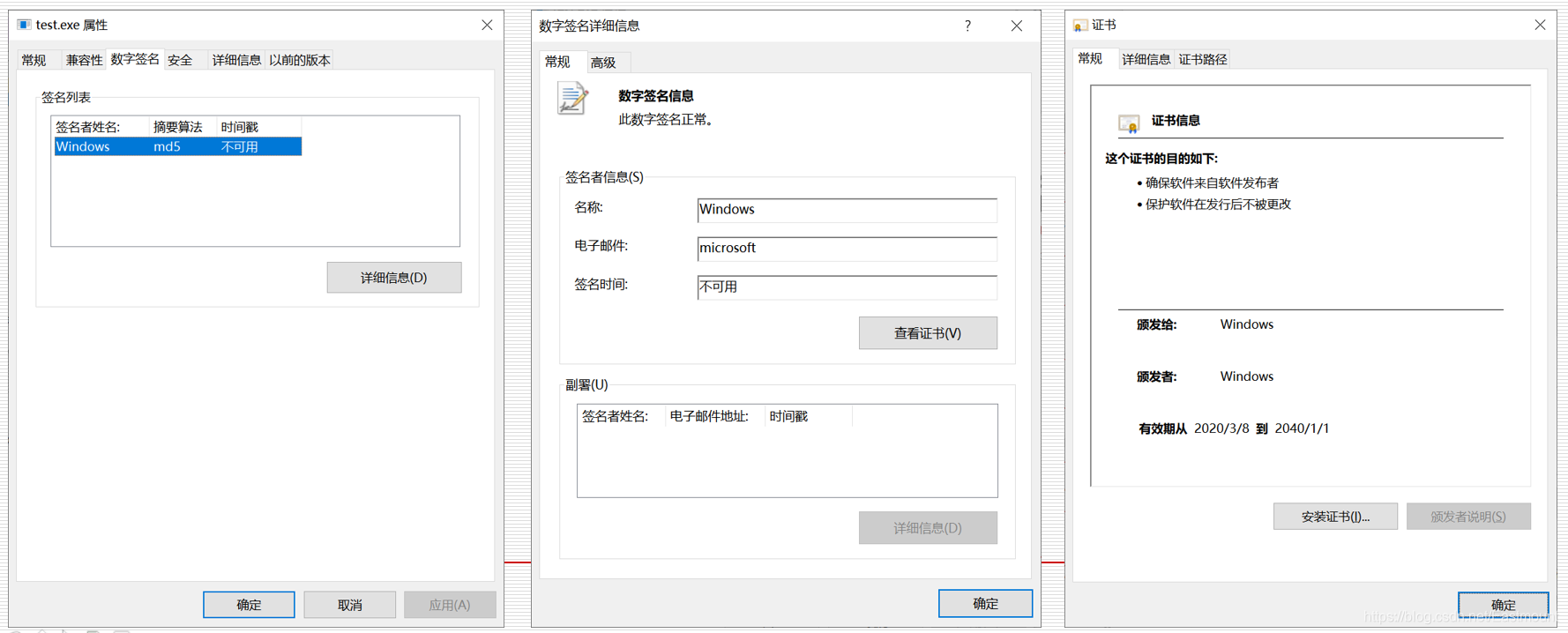
In the eighth step, the test.exe file is now digitally signed. Open the properties of the exe file, as shown in the figure below, you can see the signature related information. Note that the digital signature is normal and the issuer is Windows.
Finally, we use PEView software to open the PE file, and we can see that there is a "CERTIFICATE Table" difference between the structure before and after signing.

In the next article, we will analyze the structure of digital signatures in detail.

Four. Summary
The article is written here, the introduction is over, I hope the article is helpful to you. This article mainly explains:
- PE file digital signature
- Share teacher Ruan Yifeng’s blog and tell everyone what a digital signature is
- Sign EXE files with SignTool
The author is slowly growing up as a beginner in network security! I hope to write related articles more thoroughly in the future. At the same time, I am very grateful to the security experts in the references for sharing their articles, and thank the friends and masters for their teaching. From network security to system security, from Trojan horse virus to backdoor hijacking, from malicious code to traceability analysis, from penetration tool to binary tool, as well as Python security, top conference papers, hacker competitions and vulnerability sharing. Unknown attack and defense, life is a long way, as a beginner, I really crawl forward, thank many people for their help, continue to climb, continue to cheer!
After studying safety for a year, I have met many safety leaders and friends. I hope everyone can make progress together. If there are some shortcomings in this article, please ask Haihan. The author is slowly growing up as a beginner in network security and system security! I hope to write related articles more thoroughly in the future. At the same time, I am very grateful to the security experts in the reference for sharing their articles, and thank the masters and laboratory partners for their teaching. I know that I am very good and I have to work hard. There are no shortcuts to programming, and there are no shortcuts to reverse engineering. They are all about moving bricks. Whenever you rub the attacking opponent on the ground, you will win and you will gradually develop your own safety experience and skills. Come on, the boy hopes this route will help you and encourage each other.
Welcome everyone to discuss, do you think this series of articles help you! If there are deficiencies, please Haihan. Any suggestions can be commented to inform readers and encourage each other~
- Reverse analysis: https://github.com/eastmountyxz/SystemSecurity-ReverseAnalysis
- Network Security: https://github.com/eastmountyxz/NetworkSecuritySelf-study
The newly opened "Nazhang AI Security Home" on August 18, 2020 will mainly focus on Python big data analysis, cyberspace security, artificial intelligence, Web penetration and offensive and defensive technology, and share CCF, SCI, South and North nuclear papers The algorithm is implemented. Nazhang’s House will be more systematic, and will reconstruct all the author’s articles, explain Python and security from scratch, and have written articles for nearly ten years. I really want to share what I have learned and felt. I would also like to invite you to give me your advice and sincerely invite your attention! Thank you.

(By:Eastmount 2021-02-07 Sunday morning and evening in Guiyang http://blog.csdn.net/eastmount/ )
References:
[1] "Software Security" Course of Wuhan University
[2] (Strong push) [Network Security Self-study] 46. Microsoft Certificate Vulnerability CVE-2020-0601 (Part I) Windows verification mechanism and executable file signature reproduction
[3] (Forced push) What is a digital signature? -Ruan Yifeng
[4] (Strong push) What is a Digital Signature? -Original website
[5] (Strong push) Some research on the digital signature of PE files under Windows platform-DoveFeng
[6] (Strong push) https:// docs.microsoft.com/zh-cn/windows/win32/debug/pe-format
[7] (Strong Push) Hash Digital Signature-Phant
[8] (Strong Push) Digital Signature Verification in Malicious File Analysis System -NSFOCUS
[8] (Strong push) [Translation] Digital signature format in Windows PE files-Look at Xueyin Yanbing [
9] PE file digital signature tool-ahuo
[10] PE file analysis-exception handling table and Digital Signature-zhyulo
[11] Authenticode Signature Forgery-Signature Forgery and Signature Verification Hijacking of PE Files-RoarTalk
[12] Digital Signature-CTF Wiki
[13] Introduction and difference of digital signature algorithms-infiniSign
[14] [Help] About the digital signature of PE files -Kanxue Forum
[15] Blockchain : What is a digital signature? -ChinaKingKong
[16] Verify the legality of a file's digital signature (VerifyPE)-ahuo
[17] Digital signature-Shinymood
[18] Digital signature verification in a malicious file analysis system-Baidu Library
[19] How to determine whether a file already exists Digital Signature-CSDN Forum