beginning
The golden nine and silver ten are coming soon. Many people who are looking for a job or want to change jobs have recently improved and updated their resumes, planning to take this opportunity to change to their favorite environment.
Compared with other jobs, programmers are slightly different, the most important thing is technology. Therefore, many programmers will have a misunderstanding that they feel that they have strong skills and can naturally find a good job, and do not pay much attention to their resumes.
As a result, when the resume was sent out, there were very few interview invitations, and I only hated myself for being talented.
Share a wave of introduction interview questions
Tencent—What is symmetric encryption and what is asymmetric encryption? Do public and private keys belong to symmetric encryption?
Interviewer: What is symmetric encryption and what is asymmetric encryption? Do public and private keys belong to symmetric encryption?
Psychological analysis : Cryptography is generally studied in computer science at a university. When interviewers rely on this question, they will not go deep into the underlying content of cryptography, and the difference between symmetric and asymmetric knowledge will be tested. This question is generally not asked in depth, but will ask about https, which currently uses asymmetric encryption. But job seekers must not fall into the trap, saying that they have never heard of symmetry and asymmetry.
**Job applicants:** should start with encryption and decryption
Public key and private key are commonly known as asymmetric encryption methods, which are an improvement from the previous symmetric encryption (using username and password). Let me explain the principle by e-mail.
The purpose of using public and private keys is to achieve secure emails, and the following purposes must be achieved:
-
- The content I send to you must be encrypted and cannot be seen by others during the transmission of the email.
-
- It must be ensured that it is the mail sent by me and not someone else impersonating me.
To achieve this goal, both people who send the mail must have a public key and a private key. The public key is for everyone to use. You can publish it via email, or let others download it through the website. The public key is actually used for encryption/verification. The private key is your own and must be kept very carefully. It is best to add a password. The private key is used to decrypt/sign. First of all, as far as the ownership of the key is concerned, the private key is only owned by the individual. The function of the public key and the private key is: the content encrypted with the public key can only be decrypted with the private key, and the content encrypted with the private key can only be decrypted with the public key.
For example, I want to send you an encrypted email. First of all, I must have your public key, and you must also have my public key.
First of all, I use your public key to encrypt this email, so as to ensure that this email is not seen by others, and that this email has not been modified during transmission. After you receive the email, you can decrypt it with your private key and you can see the content.
Secondly, I use my private key to encrypt this email. After it is sent to you, you can decrypt it with my public key. Because the private key is only in my hand, this ensures that this email is sent by me.
When A->B data, A will use B's public key to encrypt, so as to ensure that only B can unlock, otherwise the general public can unlock the encrypted message, which means that the confidentiality of the data is eliminated. Verification uses the mechanism of signing and stamping. When A sends information to everyone, he will use his private key as a signature, so that all people who receive the message can use A’s public key to verify the stamp and confirm the message It was sent by A
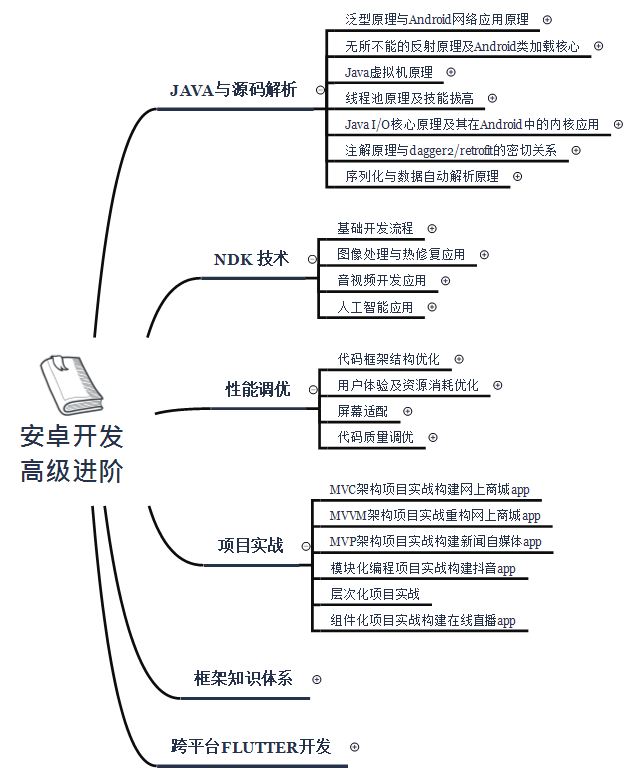
In addition to flutter, what else must be mastered in Android development?
I believe that most of the friends who are engaged in Android development are finding that finding a job is getting harder and harder and the requirements for interviews are getting higher and higher.
In addition to a solid basic knowledge of java, data structure algorithms, and design patterns, the underlying source code, NDK technology, performance tuning, and some small programs and cross-platforms, such as flutter, are shown in the figure below as a mind map;
Click on the document to get interview materials and video tutorials; [Ali P7 level Android architect technical mind map + full set of videos]
**
[External link image is being transferred...(img-FgfwBYY0-1611300953737)]